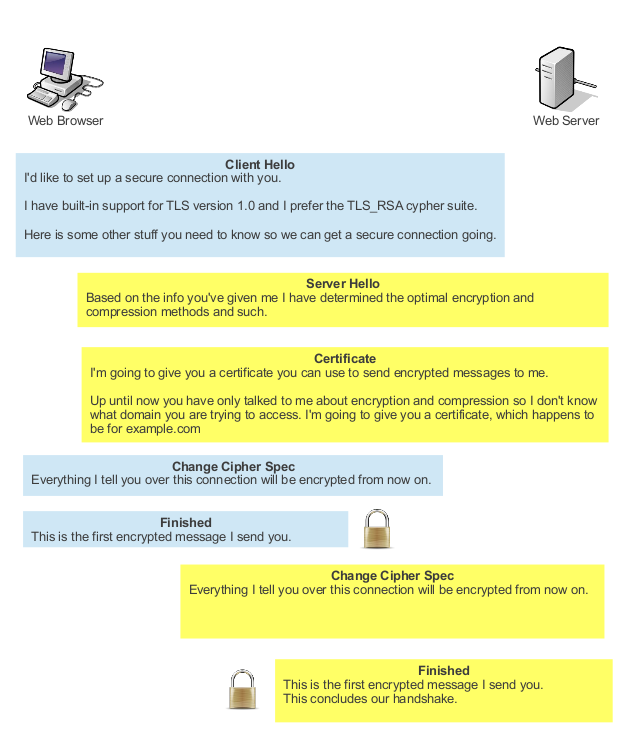
In the recent past it was impossible to add multiple different SSL .crt / .pem bundle certificates on Apache Webserver but each one of it was supposed to run under a separate domain or subdomain, preconfigured with a separate IP address, this has changed with the introduction of Apache SNI (Server Name Indication). What SNI does is it sends, the site visitor initiating connections on encrypted SSL port (443) or whatever configured a certificate that matches, the client requested server name.
Note that SNI is Apache HTTPD supported only and pitily can't be used on other services such as Mail Servers (SMTPS), (POP3S), (IMAPS) etc.
Older browsers did not have support for proper communication with WebServers supporting SNI communication, so for Websites whose aim is interoperatibility and large audience of Web clients still the preferrable way is to set up each VirtualHost under a separate IP, just like the good old days.
However Small and MidSized businesses could save some cash by not having to buy separate IPs for each Virtualhost, but just use SNI.
Besides that the people are relatively rarely using old browsers without SNI, so having clients with browsers not supporting SNI would certiainly be too rare. To recognize where a browser is having support for TLS or not is to check whether the Browser has support for TLS extension.
One requirement in order for SNI to work properly is to have registered domain because SNI works based on the requested ServerName by client.
On Debian GNU / Linux based distributions, you need to have Apache Webserver installed with enabled mod_ssl module:
linux:~# apt-get install –yes apache2
…linux:~# a2enmod ssl
…linux:~# /etc/init.d/apache2 restart
…
If you're not planning to get a trusted source certificate, especially if you're just a start-up business which is in process of testing the environment (you still did not ordered certificate via some domain registrar you might want to generate self signed certificate with openssl command and use that temporary:
linux:~# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/your-domain.com/apache.key –out /etc/apache2/ssl/your-domain.com/apache.crt
Here among the prompted questions you need the a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank.
For some fields leave the default value,
If you enter '.', or press enter the field will be left blank.
—–
Country Name (2 letter code) [AU]:BG
State or Province Name (full name) [Some-State]: Sofia
Locality Name (eg, city) []:SOF
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Pc-Freak.NET
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:your-domain.com
Email Address []:webmaster@your-domain.com
(by the way it might be interesting to mention here the list of cheapest domain name registrars on the Internet as of January 2017 – source site here
Below order is given as estimated by price / quality and provided service approximate
1. BlueHost.com – Domains $6.95
2. NameCheap.Com – Annual fee $10.69
3. GoDaddy.com – Annual fee $8.99 for first year, $14.99$ for each additional year
4. HostGator.com – Annual fee $15.00
5. 1and1.com – Annual fee $0.99 for first year ($14.99 for each additional year)
6. Network Solutions – This was historically one of the first domain registrar companies, but the brand is pricy $34.99
7. Register.com – Not sure
8. Hostway.com – $9.95 (first year and $9.95 renewals)
9. Moniker.com – Annual fee $11.99
10. Netfirms.ca – Annual fee $9.95 first year, Renewal fee is $11.99 per year
Note that domain pricing could value depending on the type of domain name country extension and many of the domain registrars would give you discount if you purchase domain name / SSL for 2 / 3+ years.
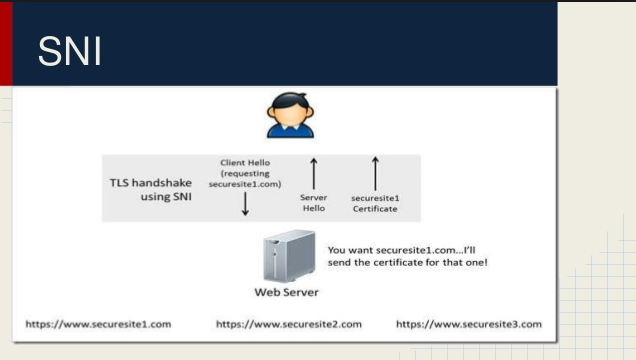
Next step in order to use SNI is to configure the WebServer Virtualhosts file:
linux:~# vim /etc/apache2/sites-available/domain-names.com
# Instruct Apache to listen for connections on port 443
Listen 443
# Listen for virtual host requests on all IP addresses
NameVirtualHost *:443# Go ahead and accept connections for these vhosts
# from non-SNI clients
SSLStrictSNIVHostCheck off<VirtualHost *:80>
ServerAdmin webmaster@your-domain.com
ServerName your-domain.com
DocumentRoot /var/www# More directives comes here
</VirtualHost>
<VirtualHost *:443>ServerAdmin webmaster@localhost
ServerName your-domain.com
DocumentRoot /var/www# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
SSLEngine on# A self-signed (snakeoil) certificate can be created by installing
# the ssl-cert package. See
# /usr/share/doc/apache2.2-common/README.Debian.gz for more info.
# If both key and certificate are stored in the same file, only the
# SSLCertificateFile directive is needed.
SSLCertificateFile /etc/apache2/ssl/your-domain.com/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/your-domain.com/apache.key# More Apache directives could be inserted here
</VirtualHost>
<VirtualHost *:443>
DocumentRoot /var/www/sites/your-domain2
ServerName www.your-domain2.com# Other directives here
</VirtualHost>
Add as many of the SNI enabled VirtualHosts following the example below, or if you prefer seperate the vhosts into separate domains.
I also recommend to check out Apache's official documentation on SNI for NameBasedSSLVhostsWithSNI etc.
Hope this article was not too boring 🙂
Enjoy life




