Bulgarian icon of Saint Demetrius
Every 26 of October in the Bulgarian Orthodox Church and whole Bulgarian nation we honor deeply the memory of martyrdom of Saint Demetrius the Myroblyte (meaning 'the Myrrh-Gusher' or 'Myrrh-Streamer'; a term that stemmed from 3rd century – 306 y. the year of Maryrdom of this great saint. Saint Demetrius over the century has been one of the most venerated saints in the Eastern Orthodox Church and since the Christianization of Bulgaria his glory also spread quickly throughout the Bulgarian Empire lands.
![]()
During the Middle Ages, he came to be revered as one of the most important Orthodox military saints, often paired with Saint George of Lydda and for that in many of the Orthodox Churches worldwide there are icons of the two saints painted together holding their warrior equipment spear, shield and sward .
![]()
St. Demetrius (Dimitar in Bulgarian) feast day is 26 October for Eastern Orthodox Christians, which falls on 8 November for those following the old calendar. In the Roman Catholic church he is most commonly called "Demetrius of Sermium" and his memorial falls on 8 October, which seem to coincide with my Birthday 🙂
Demetrius was born to pious Christian parents in Thessaloniki, the Eastern Roman Empire region Macedonia in 270 (Macedonia has been part of the Bulgarian kingdom and Empire for many centuries).
According to the hagiographies, Demetrius was a young man of senatorial family who became proconsul of the Thessalonica district. He was run through with spears in around 306 AD in Thessaloniki, during the Christian persecutions of Galerian, which matches his depiction in the 7th century mosaics.
Most historical scholars follow the hypothesis put forward by Bollandist Hippolyte Delehaye (1859–1941), that his veneration was transferred from Sirmium when Thessaloniki replaced it as the main military base in the area in 441/442 AD. His very large church in Thessaloniki, the Hagios Demetrios, dates from the mid-5th century. Thessaloniki remained a centre of his veneration, and he is the patron saint of the city.
After the growth of his veneration as saint, the city of Thessaloniki suffered repeated attacks and sieges from the Slavic peoples who moved into the Balkans, and Demetrius was credited with many miraculous interventions to defend the city. Hence later traditions about Demetrius regard him as a soldier in the Roman army, and he came to be regarded as an important military martyr. Unsurprisingly, he was extremely popular in the Middle Ages. Disputes between Bohemond I of Antioch and Alexios I Komnenos appear to have resulted in Demetrius being appropriated as patron saint of crusading.
![]()
Saint Demetrius Russian Icon
Demetrius was also venerated as patron of agriculture, peasants and shepherds in the Greek countryside during the Middle Ages.
Most scholars still believe that for four centuries after his death, Demetrius had no physical relics, and in their place an unusual empty shrine called the "ciborium" was built inside Hagios Demetrios. What were purported to be his remains subsequently appeared in Thessaloniki, but the local archbishop John, who compiled the first book of the Miracles ca. 610, was publicly dismissive of their authenticity. The relics were assumed to be genuine after they started emitting a liquid and strong-scented myrrh. This gave Demeterius the epithet Myroblyte.
Saint Demetrius used to be a mayor of Thessaloniki and had been very educated for his time, the Roman empire ordered him to find and imprison, torture and eventually kill all Christians in the city who refuse to follow the paganic Roman religion. Being a brave in heart and a being a Christian himself, he refused to follow the unrighteous emperor decree and even on the contrary started to put special efforts for the raising of the Christian faith in the city.
Despite this position in the still-pagan empire, he remained fervent in faith and works for Christ, encouraging many Christians to endure persecution and even bringing many pagans to the faith.
When Maximian returned from one of his campaigns to Thessaloniki, which he had made his capital, he had pagan games and sacrifices celebrated for his triumph. Demetrios was denounced by pagans who were envious of his success, and he was thrown into prison. While in prison he was visited by a young Christian named Nestor, who asked him for a blessing to engage in single combat with the giant Lyaios (or Lyaeus), who was posing as the champion of paganism. Demetrios gave his blessing and Nestor, against all odds. Nestor succeded to slew his opponent in the arena contrary to any expectations as Lyaios used to kill many, many christians on the circus arena, as David had once defeated Goliath. Saint Demetrius blesses Nestor but warned him he will have to endure a martyrdom after his defeat of Nestor which occured shortly after the defeath of Lyaios, Nestor was captured and martyred for Christ. Being raged out by the killing of Lyaios, the Romans send trooops and killed with spears saint Demetrius while he was praying in the prison.
According to some (Greek) hagiographic legend, as retold by Dimitry of Rostov in particular, Demetrius appeared in 1207 in the camp of tsar Kaloyan of with a lance and so killing him. This scene, known as Чудо о погибели царя Калояна ("the miracle of the destruction of tsar Kaloyan") became a popular element in the iconography of Demetrius. He is shown on horseback piercing the king with his spear, paralleling the iconography (and often shown alongside) of Saint George and the Dragon.
The reason of High veneration of Saint Demetrius in Bulgaria today ?
The godly life he led, together with his military virtues and martyrdom, led the people of Thessaloniki to declare him their saint-warrior and patron. According to the beliefs of the local centuries, the saint defended Thessaloniki, performing miracle after miracle, but in August 1185 something unheard of happened. The second richest and most important city in the empire after Constantinople was captured by the Normans and subjected to unprecedented looting. The Church of St. Dimitar was burned and the relics of the saint were scattered. The medieval Greek, who was inclined to seek God's intervention everywhere, was spiritually broken. The Romans saw the fall of Dimitrov as a punishment for their sinfulness. It is clear to them that St. Dimitar left them.
Meanwhile, in the north, the memories of the old Bulgarian kingdom were more than alive, and it became increasingly difficult for the Bulgarians to tolerate the Roman rule. The moment for a mass uprising was ripe. According to Nikita Honiat, there were three key events at the beginning of the uprising. The first concerned the desire of the brothers Peter and Assen (prominent Bulgarian boyars) to be included in the proniat lists of the empire and to receive a small landed estate at the foot of the Balkan Mountains. To this end, most likely in the autumn of 1185, they appeared in person before Emperor Isaac II Angel in Kipsela, just as he was preparing to march against the Normans who had conquered Thessaloniki. The refusal to comply with their demands provoked sharp resentment in the younger brother Assen, who personally threatened the emperor with rebellion. This unheard of behavior of the young boyar was punished with a slap.

King Ivan Assen I (Tsar of Bulgaria 1187/1188–1196)
The second important event was the imposition of additional taxes on the livestock of the population on the occasion of the emperor's wedding to the Hungarian Princess Margaret. This led to the outbreak of strong and mass discontent among the population of Moesia. The two brothers knew very well what they were doing and used the mass discontent to make their threat a reality. However, the insults, material hardship and the presence of two brilliant leaders in the face of Assenevtsi were not enough for a revolt.
![]()
Bulgarian Medieval Icon of Saint Demetrius the Myrrh-Bringer
The Bulgarians also had to receive a "divine" guarantee for their work. They believed that the Lord should show them that they were chosen and worthy of their freedom, that they not only could, but should take up arms against the Byzantine Vasilevs. And the sign was not late. On October 26, 1185, Assenevtsi, together with a large crowd, gathered in Tarnovo to consecrate the newly built church "St. Dimitar. Meanwhile, a miraculous icon of the saint appeared in the city. It was alleged that she had left Thessaloniki, conquered by the Normans, and found her home in the new temple of the Bulgarians.
The religious consciousness of the medieval Bulgarian interpreted this as a refusal of St. Dimitar to defend the Romans and a sacred guarantee that the saint will protect the Bulgarians in their cause for freedom. And indeed the old church in Thessaloniki had collapsed and plundered, the Romans were punished, the Empire was humiliated.
Those gathered in the church began to shout and call for the rejection of the yoke and for the restoration of the glory of the old kings. In this atmosphere of patriotic enthusiasm, the older brother, Todor (named Peter), placed a golden tiara on his head, put on a red cloak, and put on the purple shoes that only the Byzantine Vasilevs could wear. Thus, after 167 years of interruption of the throne of the Bulgarian kings, a Bulgarian ascended again. The coronation of Peter as king and the beginning of the great uprising of the Bulgarians was one of those moments in history when all accounts end and only faith gives the people the courage to take the hand outstretched by the uncertainty of the future and follow the path indicated by her, not knowing where he was taking her.
Niketa Choniates writes: “With such (divine) prophecies the whole nation was won for the cause and all raised their swords. And because their rebellion was successful from the very beginning, the Bulgarians believed even more that God had approved their freedom. "
At first, Isaac II Angel was unable to respond to the uprising, as he had to deal with the Normans and the usurper of Cyprus, Isaac I Komnenos. It was not until December 1185 that Vasilevs sent his uncle Sevastocrator John against the rebels. However, no battle took place because the Sevastocrator was recalled on suspicion of rebellion. At the head of the second army was Caesar John VI Kantakouzenos, who went to Hemus, but was defeated in a night attack by Assen-evtsi. The Bulgarians took the lives of most of the Roman army, and its commander managed to escape by abandoning the entire convoy. A third army of the great Byzantine general Alexy Branas was also sent, but it turned against the emperor and marched to Constantinople instead of Tarnovo.
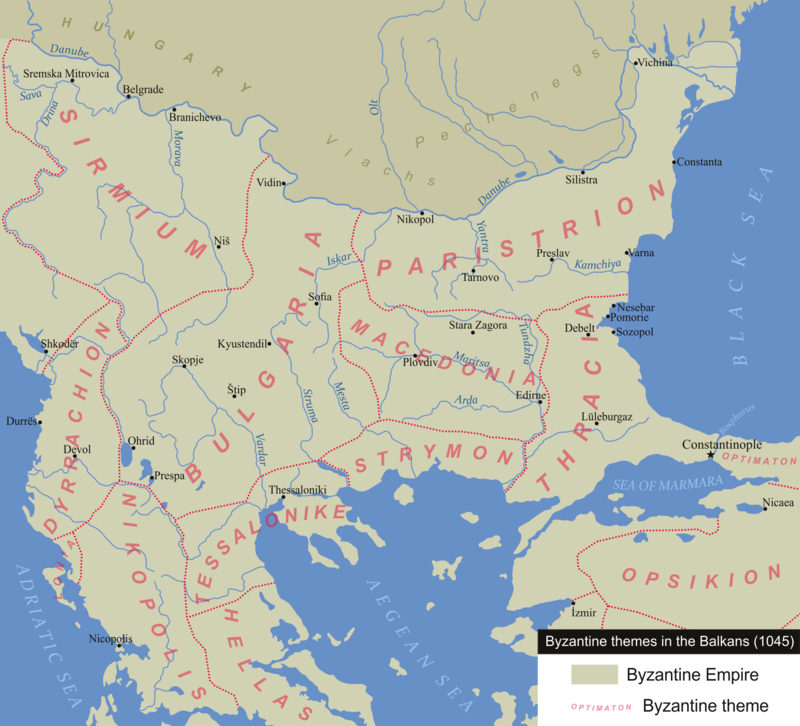
The Byzantine themes (or districts) of Bulgaria and Paristrion
Paristrion – (Greek: Παρίστριον, lit. 'beside the Ister'), or Paradounabon/Paradounabis (αραδούναβον / Παραδούναβις), which is preferred in official documents, was a Byzantine province covering the southern bank of the Lower Danube (Moesia Inferior) in the 11th and 12th centuries.
It was not until 1186 that the emperor personally led a large army and decided to deal with the Bulgarians once and for all. His campaign forced the brothers to retreat across the Danube to their Kuman allies, and Isaac II Angel plundered Moesia and returned to Constantinople. According to the story of Nikita Honiat, the emperor was so arrogant of his success that he met with ridicule the reminder of Vasily II the Bulgarian assassin that the Bulgarians would revolt and that one day they would be liberated.
At that time, Assen's personality became more and more prominent, and he became the real leader of the rebellion. In the summer of 1186, the Assenevs crossed the Danube again, conquered the plain and set their goal to bring the endeavor to a successful conclusion. Niketa Choniates says:
"And then they returned to their homeland Moesia; finding the land abandoned by the Roman armies, they took on even greater confidence, leading their Cuman auxiliary detachments as if they were legions of demons. They did not simply want to secure their possessions and establish control over Moesia; They wanted to devastate the Roman territories and unite the political power of Moesia and Bulgaria in one empire as before. "
Isaac Angel's second campaign was not long in coming. In the autumn of 1186 he set out again against the two brothers, passing through the fortress of Beroe and heading for Serdica (today's Sofia), from where he intended to cross Hemus and attack Tarnovo. The winter of 1186, however, blocked the passages and forced the emperor to abandon his endeavor for another year. With the arrival of the spring of 1187, the Romans crossed the mountain and besieged the Lovech fortress. However, the Bulgarian troops offered unprecedented resistance and after a three-month siege Isaac II Angel had to ask for peace.

The Church Saint Demetrius built by King Asen I in memoriam of great Miracles of Bulgarians victories over Byzantines
Church is located near the Tarnovo Fortress of Trapezica
The Church slavonic written sources tells how the brothers spread the word a patron saint of Thessaloniki – St. Demetrius, came to Tarnovo to help the Bulgarian people to be liberated…
Thus, most probably, the Lovech armistice was signed in front of the city walls, which de jure recognized the Bulgarian power north of the Balkans. The long road to freedom began on that distant St. Dimitrov's Day in 1185. he was finally walked away. St. Dimitar became the patron of the Asenevtsi dynasty and one of the most beloved Bulgarian saints, and the Bulgarians proved to the world that their pursuit of freedom is nothing but a great national feat, in which with a true understanding of the necessary and possible, with steady faith and unwavering energy in the design and implementation, the political and spiritual resurrection of the Second Bulgarian Kingdom was reached.
![]()
Saint Demetrius Bulgarian icon year 1824
St. Demetrius is depicted on horseback spearing a man, not because he ever a killed a man but because he blessed Nestor to win over the Gladiator Lyaeus. The Church decided to commemory the memory and bravery of Saint Nestor who also confessed Christ in his martyrdom every on the next day after the memory of st. Demetrius is celebrated. Saint Nestor even today is celebrated in the Church calendar on 27-th of October.
In Bulgaria the veneration of saint Demetrius was of high esteem especially in the Second Bulgarian Empire and many churches and monasteries has been built around the country (counting at few hundred temples and monasteries) with him being their patron.

Saint Demetrius Holy Relics in the St. Demetrius Church in Thessaloniki Greece (the white papers are names of people who ask for help from the saint)
Saint Demetrius is famous in Thessaloniki and highly venerated every year during his feast as he has been summoned by the Church to protect the city on multiple occasions which he did so far during pandemics such as the Black Death and during invasion of alien (non-Christian) nations.
It is mostly remarkable that every year during his feast day, a great miracle happens from the exact place where he was martyred (situated in the Church named after him), a myrrh with heavenly odor is streaming which is taken by believers for oilment and as a blessing carefully kept until the next year feast of the saint.
Because of the high amount of myrrh outflow a special pool was kept to keep the oilment sparring out of his holy relics.
As Saint Demetrius has helped multiple times to many of their saints as we know from history, especially in times of epidemies and pandemies like it is now let by his holy prayers those who venerate him and the people worldwide finds Healing and relief and an Enlightment and blessing from the light of Christ, just like Nestor found in his blessing !
Holy Martyr Demetrius of Thessaloniki pray the Lord for us the sinners !!!