1. Short Intro to Screen command and what is Shared Screen Session
Do you have friends who want to learn some GNU / Linux or BSD basics remotely? Do you have people willing to share a terminal session together for educational purposes within a different network? Do you just want to have some fun and show off yourself between two or more users?
If the answer to the questions is yes, then continue on reading, otherwise if you're already aware how this is being done, just ignore this article and do something more joyful.
So let me start.
Some long time ago when I was starting to be a Free Software user and dedicated enthusiast, I've been given by a friend an interesting freeshell hosting access and I stumbled upon / observed an interesting phenomenon, multiple users like 5 or 10 were connected simultaneously to the same shell sharing their command line.
I can't remember what kind of shell I happen to be sharing with the other logged in users with the same account, was that bash / csh / zsh or another one but it doesn't matter, it was really cool to find out multiple users could be standing together on GNU / Linux and *BSD with the same account and use the regular shell for chatting or teaching each others new Linux / Unix commands e.g. being able to type in shell simultaneously.
The multiple shared shell session was possible thanks to the screen command
For those who hear about screen for a first time, here is the package description:
# apt-cache show screen|grep -i desc -A 1
Description-en: terminal multiplexer with VT100/ANSI terminal emulation
GNU Screen is a terminal multiplexer that runs several separate "screens" on
—
Description-md5: 2d86b86ed6058a04c540802e49312f40
Homepage: https://savannah.gnu.org/projects/screen
root@jericho:/usr/local/src/pure-python-otr# apt-cache show screen|grep -i desc -A 2
Description-en: terminal multiplexer with VT100/ANSI terminal emulation
GNU Screen is a terminal multiplexer that runs several separate "screens" on
a single physical character-based terminal. Each virtual terminal emulates a
—
Description-md5: 2d86b86ed6058a04c540802e49312f40
Homepage: https://savannah.gnu.org/projects/screen
Tag: hardware::input:keyboard, implemented-in::c, interface::text-mode,
There is plenty of things to use screen for as it provides you a way to open Virtual Terminals into a single ssh or physical console TTY login session and I've been in love with screen command since day 1 I found out about it.
To start using screen just invoke it into a shell and enter a screen command combinations that make various stuff for you.
2. Some of the most useful Daily Screen Key Combinations for the Sys Admin
To do use the various screen options, use the escape sequence (CTRL + Some Word), following by the command. For a full list of all of the available commands, run man screen, however
for the sake of interest below short listing shows some of most useful screen key combination invoked commands:
| Ctrl-a a | Passes a Ctrl-a through to the terminal session running within screen. |
|---|---|
| Ctrl-a c | Create a new Virtual shell screen session within screen |
| Ctrl-a d | Detaches from a screen session. |
| Ctrl-a f | Toggle flow control mode (enable/disable Ctrl-Q and Ctrl-S pass through). |
| Ctrl-a k | Detaches from and kills (terminates) the screen session. |
| Ctrl-a q | Passes a Ctrl-q through to the terminal session running within screen (or use Ctrl-a f to toggle whether screen captures flow control characters). |
| Ctrl-a s | Passes a Ctrl-s through to the terminal session running within screen (or use Ctrl-a f to toggle whether screen captures flow control characters). |
| Ctrl-a :kill | Also detaches from and kills (terminates) the screen session. |
| Ctrl-a :multiuser on | Make the screen session a multi-user session (so other users can attach). |
| Ctrl-a :acladd USER | Allow the user specified (USER) to connect to a multi-user screen session. |
| Ctrl-a p | Move around multiple opened Virtual terminals in screen (Move to previous) |
| Ctrl-a n | Move backwards in multiple opened screen sessions under single shell connection |
I have to underline strongly for me personally, I'm using the most
CTRL + A + D (to detach session),
CTRL + A + C to open new session within screen (I tend to open multiple sessions for multiple ssh connections with this),
CTRL + A + P, CTRL + A + N – I use this twoto move around all my open screen Virtual sessions.
3. HOW TO ACTUALLY SHARE TERMINAL SESSION BETWEEN MULTIPLE USERS?
3.1 Configuring Shared Sessions so other users can connect
You need to have a single user account on a Linux or Unix like server lets say that might be the /etc/passwd, /etc/shadow, /etc/group account screen and you have to give the password to all users to be participating into the shared screen shell session.
E.g. create new system account screen
root@jericho:~# adduser screen
Adding user `screen' …
Adding new group `screen' (1001) …
Adding new user `screen' (1001) with group `screen' …
The home directory `/home/screen' already exists. Not copying from `/etc/skel'.
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for screen
Enter the new value, or press ENTER for the default
Full Name []: Screen user to give users shared access to /bin/bash
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] Y
Now distribute the user / pass pair around all users who are to be sharing the same virtual bash session via screen and instruct each of them to run:
hipo@jericho:~$ screen -d -m -S shared-session
hipo@jericho:~$
hipo@jericho:~$ screen -list
There is a screen on:
4095.shared-session (10.10.2017 20:22:22) (Detached)
1 Socket in /run/screen/S-hipo.
3.2. Attaching to just created session
Simply login with as many users you need with SSH to the remote server and instruct them to run the following command to re-attach to the just created new session by you:
hipo@jericho:~$ screeen -x
That's all folks now everyone can type in simultaneously and enjoy the joys of the screen shared session.
If for some reasons more than one session is created by the simultaneously logged in users either as an exercise or by mistake i.e.:
hipo@jericho:~$ screen -list
There are screens on:
4880.screen-session (10.10.2017 20:30:09) (Detached)
4865.another-session (10.10.2017 20:29:58) (Detached)
4847.hey-man (10.10.2017 20:29:49) (Detached)
4831.another-session1 (10.10.2017 20:29:45) (Detached)
4 Sockets in /run/screen/S-hipo.
You have to instruct everyone to connect actually to the exact session we need, as screen -x will ask them to what session they like to connect.
In that case to connect to screen-session, each user has to run with their account:
hipo@jericho:~$ screen -x shared-session
If under some circumstances it happened that there is more than one opened shared screen virtual session, for example screen -list returns:
hipo@jericho:~$ screen -list
There are screens on:
5065.screen-session (10.10.2017 20:33:20) (Detached)
4095.screen-session (10.10.2017 20:30:08) (Detached)
All users have to connect to the exact screen-session created name and ID, like so:
hipo@jericho:~$ screen -x 4095.screen-session
Here is the meaning of used options
-d option instructs screen to detach,
-m makes it multiuser session so other users can attach
-S argument is just to give the screen session a name
-list Sesssion gives the screen-session ID
Once you're over with screen session (e.g. all users that are learning and you show them stuff and ask them to test by themselves and have completed, scheduled tasks), to kill it just press CTRL + A + K
4. Share screen /bin/bash shell session with another user
Sharing screen session between different users is even more useful to the shared session of one user as you might have a *nix server with many users who might attach to your opened session directly, instead of being beforehand instructed to connect with a single user.
That's perfect also for educational purposes if you want to learn some Linux to a class of people, as you can use their ordinary accounts and show them stuff on a Linux / BSD machine.
Assuming that you follow and created already screen-session with screen cmd
hipo@jericho:~$ screen -list
There is a screen on:
5560.screen-session (10.10.2017 20:41:06) (Multi, attached)
1 Socket in /run/screen/S-hipo.
hipo@jericho:~$
Next attach to the session
bunny@jericho:~$ screen -r shared-session
bunny@jericho:~$ Ctrl-a :multiuser on
bunny@jericho:~$ Ctrl-a :acladd user2
bunny@jericho:~$ screen -x UserNameHere/shared-session
Here are 2 screenshots on what should happen if you had done above command combinations correctly:
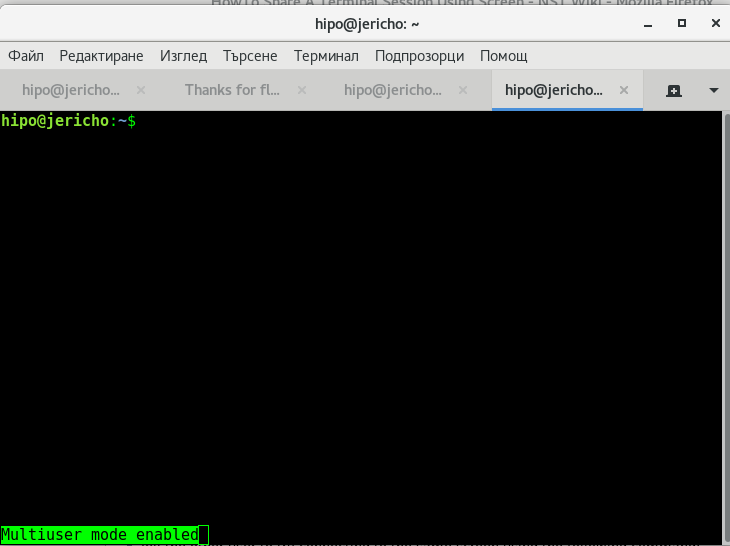
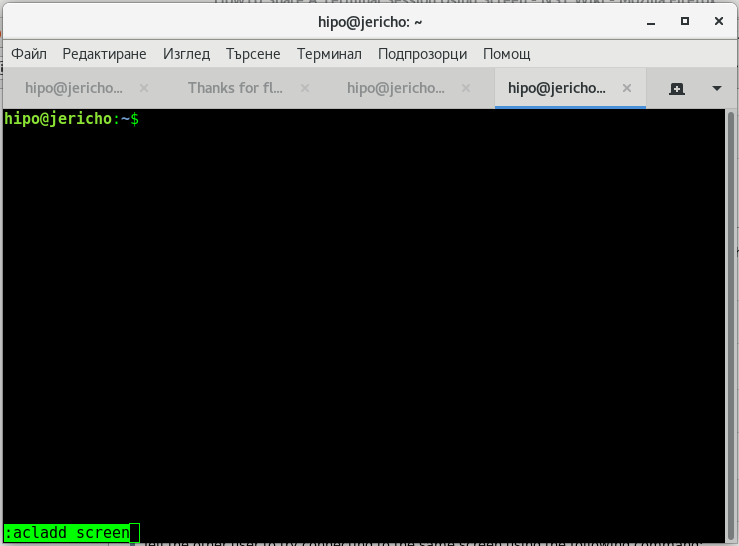
In order to be able to share screen Virtual terminal ( VTY ) sessions between separate (different) logged in users, you have to have screen command be suid (SUID bit for screen is disabled in most Linux distributions for security reasons).
Without making SUID the screen binary file, you are to get the error:
hipo@jericho:/home/hipo$ screen -x hipo/shared
Must run suid root for multiuser support.
If you are absolutely sure you know what you're doing here is how to make screen command sticky bit:
root@jericho:/home/hipo# which screen
root@jericho:/home/hipo# /usr/bin/screen
root@jericho:/home/hipo# root@jericho:/home/hipo# root@jericho:/home/hipo# chmod u+s $(which screen)
chmod 755 /var/run/screen
root@jericho:/home/hipo# rm -fr /var/run/screen/*
exit