Posts Tagged ‘Protocol’
Friday, December 9th, 2011 I have few servers, which have automatically enabled IPv6 protocols (IPv6 gets automatically enabled on Debian), as well as on most latest Linux distribituions nowdays.
Disabling IPv6 network protocol on Linux if not used has 2 reasons:
1. Security (It’s well known security practice to disable anything not used on a server)
Besides that IPv6 has been known for few criticil security vulnerabilities, which has historically affected the Linux kernel.
2. Performance (Sometimes disabling IPv6 could have positive impact on IPv4 especially on heavy traffic network servers).
I’ve red people claiming disabling IPv6 improves the DNS performance, however since this is not rumors and did not check it personally I cannot positively confirm this.
Disabling IPv6 on all GNU / Linuces can be achieved by changing the kernel sysctl settings net.ipv6.conf.all.disable_ipv6 by default net.ipv6.conf.all.disable_ipv6 equals 1 which means IPv6 is enabled, hence to disable IPv6 I issued:
server:~# sysctl net.ipv6.conf.all.disable_ipv6=0
To set it permanently on system boot I put the setting also in /etc/sysctl.conf :
server:~# echo 'net.ipv6.conf.all.disable = 1 >> /etc/sysctl.conf
The aforedescribed methods should be working on most Linux kernels version > 2.6.27 in that number it should work 100% on recent versions of Fedora, CentOS, Debian and Ubuntu.
To disable IPv6 protocol on Debian Lenny its necessery to blackist the ipv6 module in /etc/modprobe.d/blacklist by issuing:
echo 'blacklist ipv6' >> /etc/modprobe.d/blacklist
On Fedora / CentOS there is a another universal “Redhat” way disable IPv6.
On them disabling IPv6 is done by editting /etc/sysconfig/network and adding:
NETWORKING_IPV6=no
IPV6INIT=no
I would be happy to hear how people achieved disabling the IPv6, since on earlier and (various by distro) Linuxes the way to disable the IPv6 is probably different.
Alto to stop Iptables IPV6 on CentOS / Fedora and RHEL issue:
# service ip6tables stop
# service ip6tables off
Tags: blackist, boot, Cannot, CentOS, conf, Debian, Disabling, distro, DNS, echo, fedora, gnu linux, heavy traffic, How to, impact, ipv, ipv4, ipv6, kernel, kernel 2, Linux, linux kernel, linux kernels, methodology, modprobe, Module, necessery, net, network, network protocol, network servers, Networking, number, performance, Protocol, protocols, quot, Redhat, security, security practice, security vulnerabilities, sysconfig, sysctl, system boot, traffic network, Ubuntu, version, way, working
Posted in Computer Security, Linux, System Administration, Various | No Comments »
Monday, July 8th, 2013 
I just configured new dedicated server. One of requirement was dedicated server to support connections via FTP transfer protocol and few users to have access via it.
I added users with required permissions to directory structure and went on to test it with Linux ftp command, i.e.:
hipo@pcfreak:~$ ftp remote-host-name
Connected to remote-host-name.com
220 ProFTPD 1.3.3a Server (Matusala) [xx.xxx.xxx.xxx.xx]
Name (Matusala:hipo): testing-user
331 Password required for testing-user
Password:
230 User testing-user logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful
425 Unable to build data connection: No route to host
ftp> exit
221 Goodbye.
As you see from above FTP paste even simple commands like "ls" failed to work with error:
425 Unable to build data connection: No route to host
I thought somehow I have configured on server some paranoid firewall, so tested same connection with iptables rules flushed, e.g.:
matusala:~# iptables -F
matusala:~# iptables -t nat -F
Even after flushing firewall message persisted, so I googled around to see the what causes the error. The same error was hit by many users, and as I read, understand what causes is FTP server host is located behind some DMZ or firewall (as it was not my firewall I suppose, the dedicated provider has some firewall rules which are blocking FTP traffic on standard FTP TCP / UDP ports, port 20 and 21 ).
Fix is to enable in Linux kernel ip_nat_ftp or in newer Linux kernels module nf_nat_ftp:
matusala:~# modprobe ip_nat_ftp
matusala:~# modprobe nf_nat_ftp
or
To make ip_nat_ftp load permanently on Debian and Ubuntu servers:
matusala:~# echo 'ip_nat_ftp' >> /etc/modules
matusala:~# echo 'nf_nat_ftp' >> /etc/modules
One important note to make here is if you're testing the connection between two Linux servers it is possible the server from which you're running the client to have missing nf_nat_ftp loaded, so if error persist and you're testing remote FTP server from local ftp client on linux load same modules on localhost and you're done 🙂
Tags: binary mode, client error, dedicated server, directory structure, firewall rules, ftp command, host name, kernel, Linux, linux ftp, matus, modprobe, Protocol, server host, udp ports
Posted in Linux, System Administration | No Comments »
Wednesday, June 12th, 2013 
Here in my job, there is one internet (TV) around which can only read video formats in Mp4. Henceforth I needed a way to convert a number of JPEG / PNG format Picture files to Mp4. In my situation I needed to make video out of pictures and script it as this was required to be later pushed via FTP protocol to the Internet TV. Ater doing some research I figured out this is possible to build video out of pictures by using together ImageMagick and avconv.
First thing is to send pictures in certain resolution. There is a tool from imagemagick package called mogrify (which can do that). To convert a number of different dimension pictures to lets say 1024×768, used:
noah:~# mogrify -resize 1024×768 *.png
In earlier Linux distributions to create a movie from pictures ffmpeg was used like so:
# ffmpeg -qscale 5 -r 20 -b 9600 -i SDC%04d.png movie.mp4
However in newer version of ffmpeg support for this is removed, and to make video from images, there is other tool avconv. On most Linux distributions avconv is part of libav-tools package.
To install on avconv Debian and Ubuntu;
noah:~# apt-get install –yes libav-tools
…
Once installed to create single mp4 video from JPEG or PNG pictures:
noah:~# avconv -i SDC106001.JPG SDC10595.JPG SDC13611.JPG SDC13612.JPG SDC13614.JPG movie-from-pictures.mp4
I found there is also a nice GUI,software Open Movie Editor, which can create video out of number of pictuers stored in a directory.
Open Movie Editor is available in most Linux distributions (unfortunately as of time of writting on Debian Wheeze there is no install candidate of openmovieeditor), there is however substitute package doing the same job called openshot);
On latest Debian stable to install Openshot:
noah:~# apt-get install –yes openshot
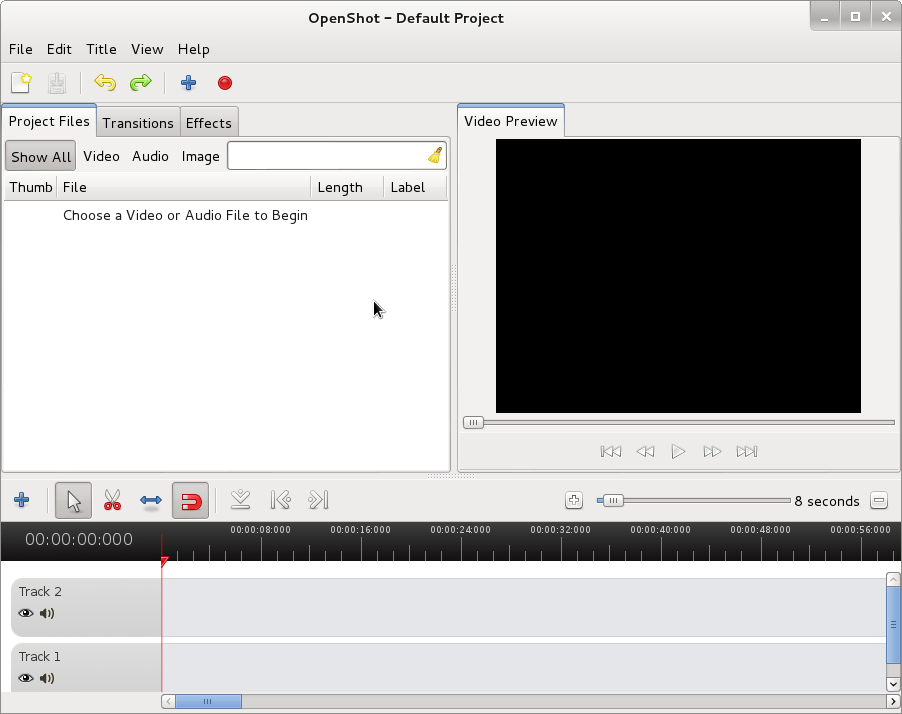
Openshot has an option (Import Image Sequence) from File -> Import Image Sequence. Using this option you can select a directory with fles with common prefix name lets say IMG*.png and create Video based on the photos inside.
On Ubuntu Linux or other distro where openmovieeditor is avialable install it with:
ubuntu:~# apt-get install –yes openmovieeditor
…
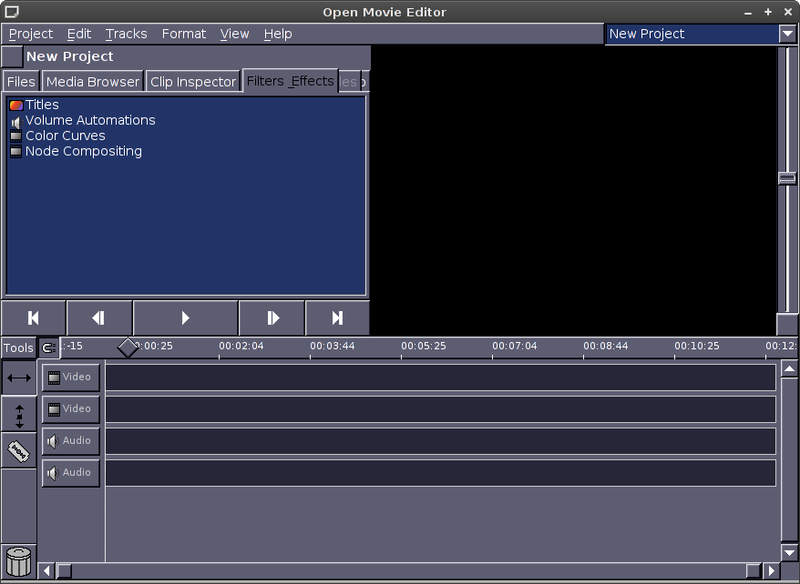
To create a video out of pictures click on Media Browser tab. Choose the Folder with pictures from which video will be generated and drag them to the Video bar
(window).
To save produced video navigate to menus:
Project -> Render
and select format to save it as. One good codec to save output is Quicktime's. To convert later Quicktime MOV Video to MP4 video,
there is the Pytube Media Converter script.
Well that's all enjoy your new videos from pictures 🙂
Tags: ffmpeg, images, internet tv, jpeg images, Linux, mogrify, most linux distributions, pictuers, png format, Protocol, ubuntu linux, video formats, wheeze, writting
Posted in Everyday Life, Linux, Linux and FreeBSD Desktop, Various | No Comments »
Monday, May 27th, 2013 
If you just configured new Qmail Mail server installation following some of the many Qmail install tutorials available online (i.e. – Life with Qmail, QmailRocks etc.) andall seemed configured fine, but still sending mails via mail server is not working in Thunderbird or Outlook with an error message like:
An error occurred while sending mail. The mail server responded: sorry, that domain isn't in my list of allowed rcpthosts (#5.7.1).
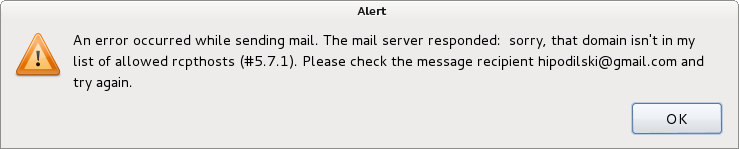
You should know the err:
The mail server responded: sorry, that domain isn't in my list of allowed rcpthosts (#5.7.1).
Is caused often by SMTP Server "incorrect" SMTP setting in Thunderbird.
To navigate to view configuration causing the weird error in Debian (Thunderbird / IceDove 10.0.12) follow to menus:
Edit -> Account Settings -> Outgoing Server (SMTP) -> (Edit on default SMTP server)
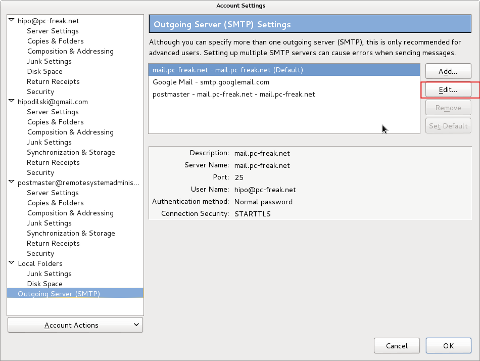
Below are screenshot of my Thunderbird (Icedove), SMPT (Mail server) settings, causing the cryptic error message.
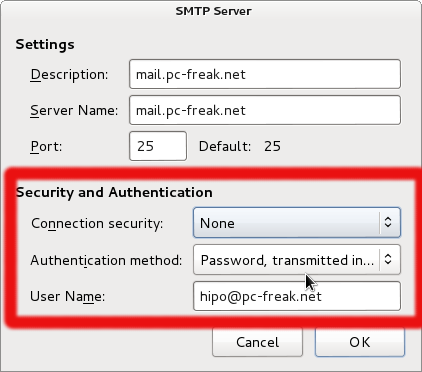
As you can see as of time of getting Error, connection security is set to None, however the Qmail SMTP Mail server is configured to not support Transmissions of Passoword (in plain text) insecurely, hence whenever Thunderbird tries to authenticate sending my Mailbox password via SMTP Auth protocol in plain text, authentication fails with the ugly archaic error:
The mail server responded: sorry, that domain isn't in my list of allowed rcpthosts (#5.7.1).
Solution to problem is as simple as changing,
Connection Security: to STARTTLS
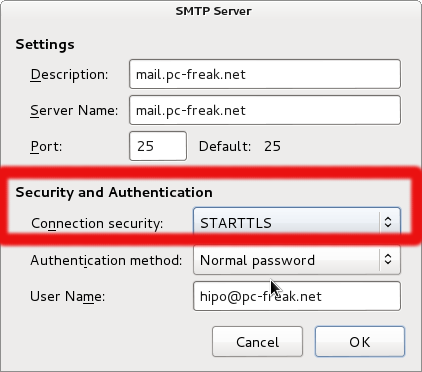
To finalize and, restarting Thunderbird is necessary. After that sending mail via Mail server works like a charm.
Note that the meaning of;'
sorry, that domain isn't in my list of allowed rcpthosts (#5.7.1).
Sending mail client or user is not authorized to deliver to mailbox to whose delivery is attempted (in my case to Gmail.com). This message pops-up because the SMTP Mail server is configured properly and not Open Relay host.
Hope this helps someone. In case it worked for you drop a comment with version of Mail Client and Mail server and a thank you message 😉
Tags: account settings, authentication, cryptic error message, life with qmail, list of allowed rcpthosts, mail server, mailbox password, outgoing server, Protocol, qmail installation, sending mail, smpt, Thunderbird, transmissions
Posted in Linux and FreeBSD Desktop, Qmail, Various | No Comments »
Sunday, July 29th, 2012 A friend of mine (Dido) who is learning C programming, has written a tiny chat server / client (peer to peer) program in C. His program is a very good learning curve for anyone desiring to learn basic C socket programming.
The program is writen in a way so it can be easily modified to work over UDP protocol with code:
struct sockaddr_in a;
a_sin_family=AF_INET;
a_sin_socktype=SOCK_DGRAM;
Here are links to the code of the Chat server/client progs:
Tiny C Chat Server Client source code
Tiny C Chat Client source code
To Use the client/server compile on the server host tiny-chat-serer-client.c with:
$ cc -o tiny-chat-server tiny-chat-server.c
Then on the client host compile the client;
$ cc -o tiny-chat-client tiny-chat-client.c
On the server host tiny-chat-server should be ran with port as argument, e.g. ;
$ ./tiny-chat-server 8888
To chat with the person running tiny-chat-server the compiled server should be invoked with:
$ ./tiny-chat-client 123.123.123.123 8888
123.123.123.123 is the IP address of the host, where tiny-chat-server is executed.
The chat/server C programs are actually a primitive very raw version of talk.
The programs are in a very basic stage, there are no condition checks for incorrectly passed arguments and with wrongly passed arguments it segfaults. Still for C beginners its useful …
Tags: Auto, c programming, c programs, c socket programming, chat client, chat server, checks, client, client host, client server, client source code, codeTo, cThen, curve, dido, Draft, family, ip address, learning c, learning curve, mine, minimalistic, peer to peer program, person, port, program, programming, Protocol, raw version, server c, server client, server host, sockaddr, Socket, socktype, stage, struct, struct sockaddr, Tiny, tiny c, UDP, version, way, writen
Posted in Programming | No Comments »
Thursday, May 3rd, 2012 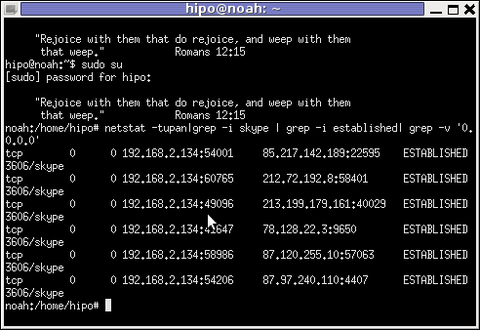
Before I explain how netstat and whois commands can be used to check information about a remote skype user – e.g. (skype msg is send or receved) in Skype. I will say in a a few words ( abstract level ), how skype P2P protocol is designed.
Many hard core hackers, certainly know how skype operates, so if this is the case just skip the boring few lines of explanation on how skype proto works.
In short skype transfers its message data as most people know in Peer-to-Peer "mode" (P2P) – p2p is unique with this that it doesn't require a a server to transfer data from one peer to another. Most classical use of p2p networks in the free software realm are the bittorrents.
Skype way of connecting to peer client to other peer client is done via a so called "transport points". To make a P-to-P connection skype wents through a number of middle point destinations. This transport points (peers) are actually other users logged in Skype and the data between point A and point B is transferred via this other logged users in encrypted form. If a skype messages has to be transferred from Peer A (point A) to Peer B (Point B) or (the other way around), the data flows in a way similar to:
A -> D -> F -> B
or
B -> F -> D -> A
(where D and F are simply other people running skype on their PCs).
The communication from a person A to person B chat in Skype hence, always passes by at least few other IP addresses which are owned by some skype users who happen to be located in the middle geographically between the real geographic location of A (the skype peer sender) and B (The skype peer receiver)..
The exact way skypes communicate is way more complex, this basics however should be enough to grasp the basic skype proto concept for most ppl …
In order to find the IP address to a certain skype contact – one needs to check all ESTABLISHED connections of type skype protocol with netsat within the kernel network stack (connection) queue.
netstat displays few IPs, when skype proto established connections are grepped:
noah:~# netstat -tupan|grep -i skype | grep -i established| grep -v '0.0.0.0'
tcp 0 0 192.168.2.134:59677 212.72.192.8:58401 ESTABLISHED 3606/skype
tcp 0 0 192.168.2.134:49096 213.199.179.161:40029 ESTABLISHED 3606/skype
tcp 0 0 192.168.2.134:57896 87.120.255.10:57063 ESTABLISHED 3606/skype
Now, as few IPs are displayed, one needs to find out which exactly from the list of the ESTABLISHED IPs is the the Skype Contact from whom are received or to whom are sent the messages in question.
The blue colored IP address:port is the local IP address of my host running the Skype client. The red one is the IP address of the remote skype host (Skype Name) to which messages are transferred (in the the exact time the netstat command was ran.
The easiest way to find exactly which, from all the listed IP is the IP address of the remote person is to send multiple messages in a low time interval (let's say 10 secs / 10 messages to the remote Skype contact).
It is a hard task to write 10 msgs for 10 seconds and run 10 times a netstat in separate terminal (simultaneously). Therefore it is a good practice instead of trying your reflex, to run a tiny loop to delay 1 sec its execution and run the prior netstat cmd.
To do so open a new terminal window and type:
noah:~# for i in $(seq 1 10); do \
sleep 1; echo '-------'; \
netstat -tupan|grep -i skype | grep -i established| grep -v '0.0.0.0'; \
done
-------
tcp 0 0 192.168.2.134:55119 87.126.71.94:26309 ESTABLISHED 3606/skype
-------
tcp 0 0 192.168.2.134:49096 213.199.179.161:40029 ESTABLISHED 3606/skype
tcp 0 0 192.168.2.134:55119 87.126.71.94:26309 ESTABLISHED 3606/skype
-------
tcp 0 0 192.168.2.134:49096 213.199.179.161:40029 ESTABLISHED 3606/skype
tcp 0 0 192.168.2.134:55119 87.126.71.94:26309 ESTABLISHED 3606/skype
...
You see on the first netstat (sequence) exec, there is only 1 IP address to which a skype connection is established, once I sent some new messages to my remote skype friend, another IP immediatelly appeared. This other IP is actually the IP of the person to whom, I'm sending the "probe" skype messages.
Hence, its most likely the skype chat at hand is with a person who has an IP address of the newly appeared 213.199.179.161
Later to get exact information on who owns 213.199.179.161 and administrative contact info as well as address of the ISP or person owning the IP, do a RIPE whois
noah:~# whois 213.199.179.161
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '87.126.0.0 - 87.126.127.255'
inetnum: 87.126.0.0 - 87.126.127.255
netname: BTC-BROADBAND-NET-2
descr: BTC Broadband Service
country: BG
admin-c: LG700-RIPE
tech-c: LG700-RIPE
tech-c: SS4127-RIPE
status: ASSIGNED PA
mnt-by: BT95-ADM
mnt-domains: BT95-ADM
mnt-lower: BT95-ADM
source: RIPE # Filteredperson: Lyubomir Georgiev
.....
Note that this method of finding out the remote Skype Name IP to whom a skype chat is running is not always precise.
If for instance you tend to chat to many people simultaneously in skype, finding the exact IPs of each of the multiple Skype contacts will be a very hard not to say impossible task.
Often also by using netstat to capture a Skype Name you're in chat with, there might be plenty of "false positive" IPs..
For instance, Skype might show a remote Skype contact IP correct but still this might not be the IP from which the remote skype user is chatting, as the remote skype side might not have a unique assigned internet IP address but might use his NET connection over a NAT or DMZ.
The remote skype user might be hard or impossible to track also if skype client is run over skype tor proxy for the sake of anonymity
Though it can't be taken as granted that the IP address obtained would be 100% correct with the netstat + whois method, in most cases it is enough to give (at least approximate) info on a Country and City origin of the person you're skyping with.
Tags: Auto, client, connection, Draft, ESTABLISHED, explanation, few words, form, free software, geographic location, gnu linux, hackers, hard core, host, information, ip address, ip addresses, ips, level, Linux, location, message data, middle, netstat, noah, p2p, p2p networks, p2p protocol, peers, person, ppl, proto, Protocol, receiver, RIPEtech-c, sender, Skype, terminal, time, to, tupan, type, whois commands
Posted in Computer Security, Skype on Linux, System Administration | No Comments »
Friday, August 13th, 2010 
If you want to imrpove your internet privacy through tor-rifing your network traffic of ICQ and MSN networks.
Do the following:
1. Install tor server
debian:~# apt-get install tor
2. Install the polipo caching proxy
debian:~# apt-get install polipo
3. Download and overwrite default polipo configuration with the one from torproject.org
This is necessary to configure in order to have polipo adapted to work with tor, so issue the following commands:
debian:~# cd /etc/polipo
debian:~# wget https://svn.torproject.org/svn/torbrowser/trunk/build-scripts/config/polipo.conf
debian:~# mv config config.bak
debian:~# mv polipo.conf config
4. Restart polipo for the new config settings to take affect
debian:~# /etc/init.d/polipo restart
Make sure in your /etc/tor/torrc you have existing the following two torrc directives:
debian:~# vim /etc/tor/torrc
SocksPort 9050 # what port to open for local application connections
SocksListenAddress 127.0.0.1 # accept connections only from localhost
5. Start up tor server if it’s not already started
debian:~# /etc/init.d/tor retart
6. Install pidgin if you haven’t got it installed already
debian:~# apt-get install pidgin
8. Start up the recent installed pidgin multi-protocol instant messanger
hipo@debian:~$ pidgin &
If you already previously properly installed and configured version of pidgin.
9. In pidgin messanger do the following changes to configure it to proxy traffic via tor
In your either your existing ICQ / MSN pidgin account navigate to:
- Accounts -> Manage Accounts
- Under Protocol ICQ
-
click Modify..
- Now go to Proxy
The default Proxy setting in Debian Sid/Squeeze would Use GNOME Proxy Settings however in other Linux distributions or *BSD it could be either No Proxy or some other setting.
- Now substitute whatever options is choosen with SOCKS 5
- In the below data input field with a name Host: type 127.0.0.1
- For the Port: field box type the port 9050
You specify for a local proxy port 9050 because this is the default port where we have previosly configured polipo to proxify traffic to tor’s anonymity network
The settings tor tunneling of traffic for Protocol MSN are analogous like for the ICQ Protocol so I won’t repeat myself on that.
This described tor tunneling for ICQ and MSN traffic should be applicable to other IM protocols under the same logic.
Here is the time to nota that the above instructions should be also applicable for Gain with minor changes or even without any.
Of course because tunneling traffic via Poplipo and it’s handling over to a tor node which will pass traffic randomly through different geographical locations whether tor servers reside will be more time consuming, so login account login time to your Messanger protocol of choice will vary and would be a bit longer.
The use of tor for your MSN and ICQ traffic is twofold:
1. Using tor anonymizing traffic network will keep your anonymity on the net private
2. Using the tor anonimity online services will let you access IM servers despite firewall blocking applied by administrators on certain places for instance (in your School or Your work env) and will therefore let you still use your favourite IM in spite of the applied firewall restrictions.
Anyways as we all know life is not perfect 🙂
Despite the slower logins and the bit slower message transmission, at least you won’t be easily tracable by third party prying eyes,
administrators or any other messanger spying sniffer traffic logger installed somewhere in between yourself and the end side of an IM server.
Hope this article helps somebody out there and will be a step further in the battle for securying your privacy online.
Tags: amp, Anonymising ICQ and MSN and other messangers via Tor on Linux, bak, config, config settings, configure, debian sid, Gnome, hipo, icq, init, Install, instant messanger, internet privacy, linux distributions, localhost, login, Manage, messangers, MSN, mv, nbsp, network traffic, overwrite, pidgin, polipo, Privacy, Protocol, proxy settings, Restart, retart, scripts, squeeze, time, tor, torproject, type, vim, wget
Posted in Computer Security, FreeBSD, Linux, Linux and FreeBSD Desktop | 3 Comments »
Wednesday, August 17th, 2011 One server recently installed with Qmail + Vpopmail and Squirrelmail had just been reported to me that the webmail is failing to properly login existent users on the server via the IMAP protocol.
I’ve checked on port 143 to see if couriertpcd process is properly listening with netstat -tlnp as well as used telnet to check if I can normally connect with telnet to the imap port and it seemed there is no issue with IMAP
Further on I checked /var/log/mail.log and there I found the following error message popping up:
Aug 17 08:56:27 mail-serv imapd: LOGIN FAILED, user=hipo@mail-serv.com, ip=[::ffff:127.0.0.1]
Aug 17 08:56:27 mail-serv imapd: authentication error: Connection refused
Aug 17 08:56:29 mail-serv imapd: Connection, ip=[::ffff:127.0.0.1]
Aug 17 08:56:29 mail-serv imapd: authdaemon: s_connect() failed: Connection refused
Aug 17 08:56:29 mail-serv imapd: [Hint: perhaps authdaemond is not running?]
The error was shown each time I do get a failure in Squirrelmail in my browser to connect to IMAP with the error:
ERROR: Connection dropped by IMAP server.
As the log revealed the courier-authdaemond was not up and running on the system. I thus launched it :
qmail:~# /usr/local/sbin/authdaemond stop
qmail:~# /usr/local/sbin/authdaemond start
qmail:~# /etc/init.d/imap start
I’ve later on figured out the strange, was caused because of a server reboot, during boot process authdaemond did not properly load up, therefore to prevent future problems like this one, I’ve put authdaemond and /etc/init.d/imap scripts to load up via /etc/rc.local :
qmail:~# echo '/usr/local/sbin/authdaemond stop' >> /etc/rc.local
qmail:~# echo '/usr/local/sbin/authdaemond start' >> /etc/rc.local
qmail:~# echo '/etc/init.d/imap start' >> /etc/rc.local
Tags: authdaemon, authentication error, boot, boot process, browser, com, connection, connection ip, ERROR, error error, error message, failure, ffff, imap port, imap protocol, IMAPFurther, issue, localqmail, login, mail, mail log, nbsp, port, port 143, Protocol, Qmail, Reboot, sbin, scripts, squirrelmail, startI, startqmail, Stop, time, usr, var, vpopmail
Posted in Linux, Qmail, System Administration | No Comments »
Thursday, February 2nd, 2012 I'm managing few wordpress installations which requires me to type in:
Hostname , FTP Username and FTP Password , every single time a plugin update is issued and I want to upgrade to the new version.
Below is a screenshot of this annoying behaviour:
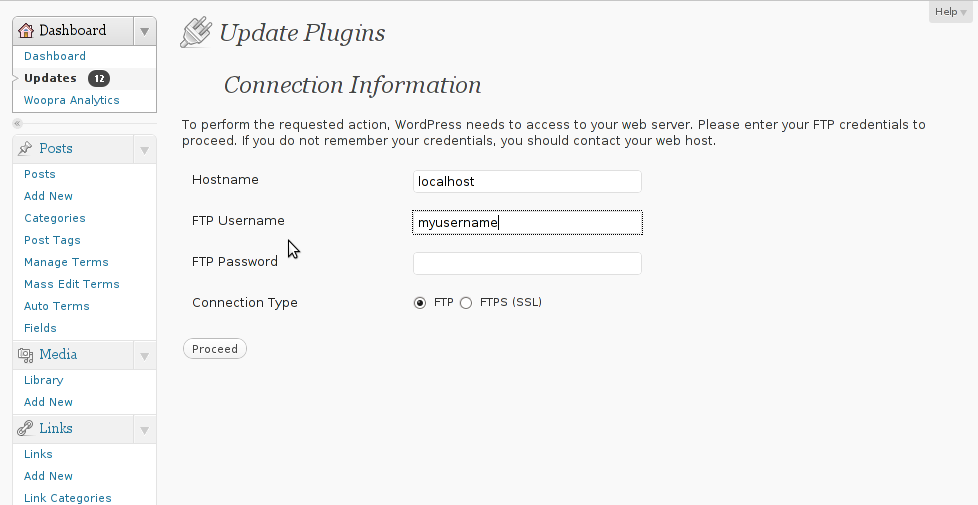
As you can see in the above screenshot, there is no way through Update Plugins web interface to store the password permanently. Hence the only option to store it permanently is to manually edit wp-config.php (file located in wordpress docroot, e.g. /path/to/wordpress/wp-config.php , inside the file find the line:
define ('WPLANG', '');
Right after it put a code similar to:
define('FS_METHOD', 'ftpsockets');
define('FTP_BASE', '/path/to/wordpress/');
define('FTP_CONTENT_DIR', '/path/to/wordpress/wp-content/');
define('FTP_PLUGIN_DIR ', '/path/to/wordpress/wp-content/plugins/');
define('FTP_USER', 'Username');
define('FTP_PASS', 'Password');
define('FTP_HOST', 'localhost');
Change the above defines:
path/to/wordpress/ – with your wordpress location directory.
Username and Password – with your respective FTP username and password. The localhost
That's all, from now onwards the User/Password prompt will not appear anymore. Consider there is a security downside of storing the FTP User/Pass in wp-config.php , if someone is able to intrude the wordpress install and access the documentroot of the wordpress install he we'll be able to obtain the ftp user/pass and log in the server directly via FTP protocol.
Tags: Auto, base path, behaviour, config, content, documentroot, downside, Draft, file, g path, host, line, localhost, location, location directory, password, Path, php, plugin, Protocol, screenshot, security, someone, time, type, update, User, version, way, web interface
Posted in System Administration, Web and CMS, Wordpress | 1 Comment »
Sunday, February 12th, 2012 
Lately I've been researching on ntpd and wrote a two articles on how to install ntpd on CentOS, Fedora and how to install ntpd on FreeBSD and during my research on ntpd, I've come across OpenNTPD and decided to give it a go on my FreeBSD home router.
OpenBSD project is well known for it is high security standards and historically has passed the test of time for being a extraordinary secure UNIX like free operating system.
OpenBSD is developed in parallel with FreeBSD, however the development model of the two free operating systems are way different.
As a part of the OpenBSD to be independant in its basis of software from other free operating systems like GNU / Linux and FreeBSD. They develop the all around free software realm known OpenSSH. Along with OpenSSH, one interesting project developed for the main purpose of OpenBSD is OpenNTPD.
Here is how openntpd.org describes OpenNTPD:
"a FREE, easy to use implementation of the Network Time Protocol. It provides the ability to sync the local clock to remote NTP servers and can act as NTP server itself, redistributing the local clock."
OpenNTPD's accent just like OpenBSD's accent is security and hence for FreeBSD installs which targets security openntpd might be a good choice. Besides that the so popular classical ntpd has been well known for being historically "insecure", remote exploits for it has been released already at numerous times.
Another reason for someone to choose run openntpd instead of ntpd is its great simplicity. openntpd configuration is super simple.
Here are the steps I followed to have openntpd time server synchronize clock on my system using other public accessible openntpd servers on the internet.
1. Install openntpd through pkg_add -vr openntpd or via ports tree
a) For binar install with pkg_add issue:
freebsd# pkg_add -vr openntpd
...
b) if you prefer to compile it from source
freebsd# cd /usr/ports/net/openntpd
freebsd# make install clean
...
2. Enable OpenNTPD to start on system boot:
freebsd# echo 'openntpd_enable="YES"' >> /etc/rc.conf
3. Create openntpd ntpd.conf configuration file
There is a default sample ntpd.conf configuration which can be straight use as a conf basis:
freebsd# cp -rpf /usr/local/share/examples/openntpd/ntpd.conf /usr/local/etc/ntpd.conf
Default ntpd.conf works just fine without any modifications, if however there is a requirement the openntpd server to listen and accept time synchronization requests from only certain hosts add to conf something like:
listen on 192.168.1.2
listen on 192.168.1.3
listen on 2607:f0d0:3001:0009:0000:0000:0000:0001
listen on 127.0.0.1
This configuration will enable only 192.168.1.2 and 192.168.1.3 IPv4 addresses as well as the IPv6 2607:f0d0:3001:0009:0000:0000:0000:0001 IP to communicate with openntpd.
4. Start OpenNTPD service
freebsd# /usr/local/etc/rc.d/openntpd
5. Verify if openntpd is up and running
freebsd# ps axuww|grep -i ntp
root 31695 0.0 0.1 3188 1060 ?? Ss 11:26PM 0:00.00 ntpd: [priv] (ntpd)
_ntp 31696 0.0 0.1 3188 1140 ?? S 11:26PM 0:00.00 ntpd: ntp engine (ntpd)
_ntp 31697 0.0 0.1 3188 1088 ?? S 11:26PM 0:00.00 ntpd: dns engine (ntpd)
root 31700 0.0 0.1 3336 1192 p2 S+ 11:26PM 0:00.00 grep -i ntp
Its also good idea to check if openntpd has succesfully established connection with its peer remote openntpd time servers. This is necessery to make sure pf / ipfw firewall rules are not preventing connection to remote 123 UDP port:
freebsd# sockstat -4 -p 123
USER COMMAND PID FD PROTO LOCAL ADDRESS FOREIGN ADDRESS
_ntp ntpd 31696 4 udp4 83.228.93.76:54555 212.70.148.15:123
_ntp ntpd 31696 6 udp4 83.228.93.76:56666 195.69.120.36:123
_ntp ntpd 31696 8 udp4 83.228.93.76:49976 217.75.140.188:123
By default openntpd is also listening to IPv6 if IPv6 support is enabled in freebsd kernel.
6. Resolve openntpd firewall filtering issues
If there is a pf firewall blocking UDP requests to in/out port 123 within /etc/pf.conf rule like:
block in log on $EXT_NIC proto udp all
Before the blocking rule you will have to add pf rules:
# Ipv4 Open outgoing port TCP 123 (NTP)
pass out on $EXT_NIC proto tcp to any port ntp
# Ipv6 Open outgoing port TCP 123 (NTP)
pass out on $EXT_NIC inet6 proto tcp to any port ntp
# Ipv4 Open outgoing port UDP 123 (NTP)
pass out on $EXT_NIC proto udp to any port ntp
# Ipv6 Open outgoing port UDP 123 (NTP)
pass out on $EXT_NIC inet6 proto udp to any port ntp
where $EXT_NIC is defined to be equal to the external lan NIC interface, for example:
EXT_NIC="ml0"
Afterwards to load the new pf.conf rules firewall has to be flushed and reloaded:
freebsd# /sbin/pfctl -f /etc/pf.conf -d
...
freebsd# /sbin/pfctl -f /etc/pf.conf -e
...
In conclusion openntpd should be more secure than regular ntpd and in many cases is probably a better choice.
Anyhow bear in mind on FreeBSD openntpd is not part of the freebsd world and therefore security updates will not be issued directly by the freebsd dev team, but you will have to regularly update with the latest version provided from the bsd ports to make sure openntpd is 100% secure.
For anyone looking for more precise system clock synchronization and not so focused on security ntpd might be still a better choice. The OpenNTPD's official page states it is designed to reach reasonable time accuracy, but is not after the last microseconds.
Tags: Auto, basis, better security, CentOS, connection, development model, Draft, Engine, exploits, fedora, Free, free operating system, free operating systems, freebsd, GNU, gnu linux, high security, Linux, network time protocol, ntp server, ntp servers, ntpd, Open, OpenBSD, OpenNTPD, pkg, ports, project, Protocol, quot, realm, reason, root, secure unix, security standards, simplicity, software, system, system clock, test, test of time, time, time server
Posted in FreeBSD, System Administration | No Comments »


















