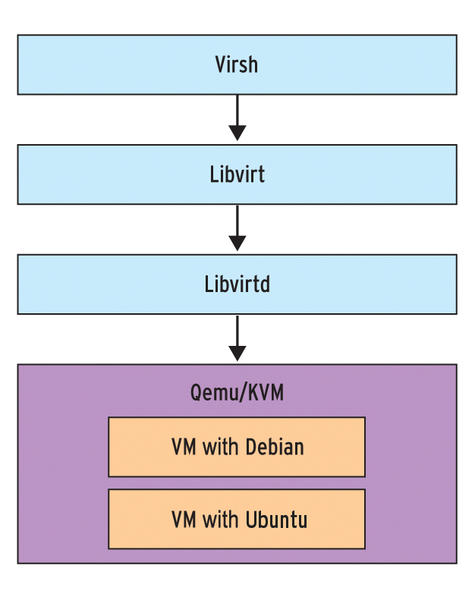
Doing everything in Linux console / terminal is a question perhaps every Linux / BSD hacker wants to do as Graphical user interface and using web search or using Graphical Environment plugins is an unneded complexity + googling or duckduckgoing for weather to check your next vacation destination city has been more and more of a terrible experience (for me) as I'm not a big fan of using the OS in a GUI.
In that manner of thoughts, as a Linux console geek and hard core ASCII art fan. I was recently happy to find that possible to check weather forecast in tty console or Linux terminal in a beautiful ascii art way easily through a Web wttr.in service – a web application weather forecast service that supports displaying the current and few days in future, weather forecast either in browser as a plain text or from the command line by simply accessing it with your favourite web access / transfer tool such as;
wget / curl or any of your favourite text browser elinks / lynx / w3m or if on *BSDs use fetch command.
Install Curl data transfer tool if it is not already
Wget is installed by default across most Linux distributions and fetch is present by default on BSDs, displaying it in text browser would perhaps be never used but if you decide to give it a try maybe try with elinks (to get colorful output), w3m and lynx will display a black and white results.
In case if you miss curl, install it:
On Debian distro
aptitude install -y curl
or Fedora
yum install -y curl
…
Of course to use wttr.in as it is Internet based Weather Forecast service the minimum you need to have is to have Internet connection to your Linux / BSD desktop computer.
Text based Weather Forecast Web App currently supports:
display the current weather as well as a 3-day weather forecast, split into morning, noon, evening and night
- Temperature is displayed for morning, noon, evening and night (includes temperature range, wind speed and direction, viewing distance, precipitation amount and probability)
- Provide results for Weather based on City / town / village location
- Supports display of Moon Phases Forecast in calendar days
- Supports multilingual names (Bulgarian Phonetic cyrillic / Russian and other exotic UTF-8 encodings such as Chineese and Japanese), 50+ languages are currently supported
- Has ability for prognosis for hostname (domain) location based on an its IP GeoIP location on the Globe
- Geographical locations / landmarks such as Lakes / Mountains etc. can be easily queried
- Query results metrics could be configured, e.g. USCS units or EU and rest of world accepted ones (SI) metric
- Displayed result could be either in ANSI (if from terminal / console / HTML if queried from browser or in PNG – if needed)
Where wttr.in could be useful ?
The best applications use, I can think of are for server (shell) / perl scripting automation purposes, it could be useful especially in TOO HOT, TOO, COLD, TOO WET location in Small and Middle sized Data Centers Green Energy (Sun Panel) Parks / Wind Energy situated Linux monitoring hosts to track possible problems of overheats or overcolding of servers due to abnormal excessive temperatures such as the ones we experienced this summer here All across in Europe or in too Cold DC locations such as heat locations Deserts in African Countries, Saudi Arabia or Chukotka or Siberia in Russia.
Other application is as a backup option to other normal Weather report services by PHP or Python scripts that fetch data, from multiple places.
Of course since this is a third party controlled service, the downtime is due to excessive connection requests, the service could get flooded and stopped working, but I guess for any Commercial use, wttr.in creator Igor Chubin would be happy to sell a specific crafted service for any end user candidates.
Here is few examples of the beautiful returned ASCII art formatted output of wttr.in.
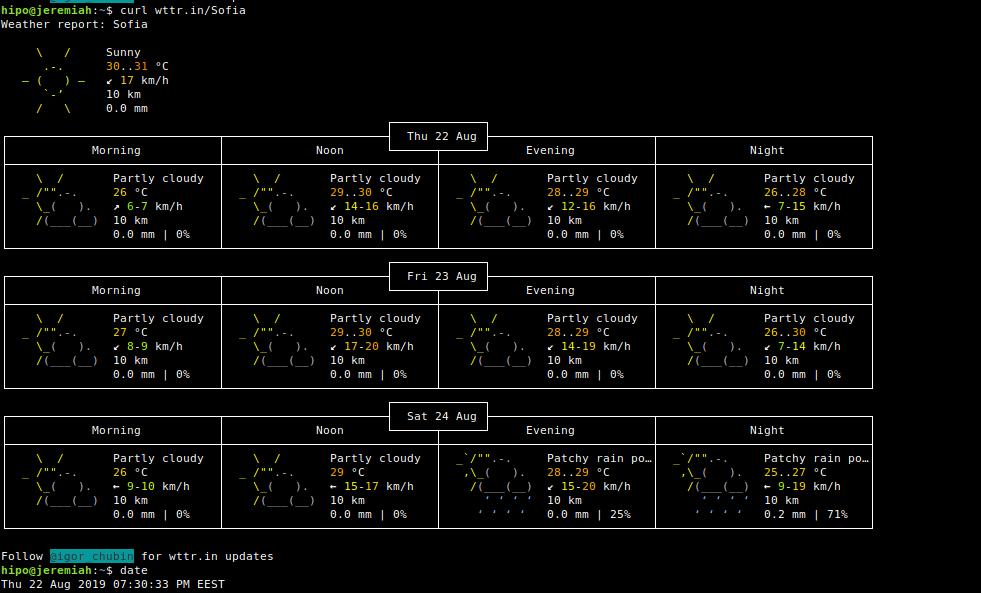
1. Getting a three days Weather Forecast prognosis for city / town location
To get what is current weather in my current city of Living, Sofia Bulgaria just pass the city to the URL address
curl http://wttr.in/Sofia
links http://wttr.in/Dobrich
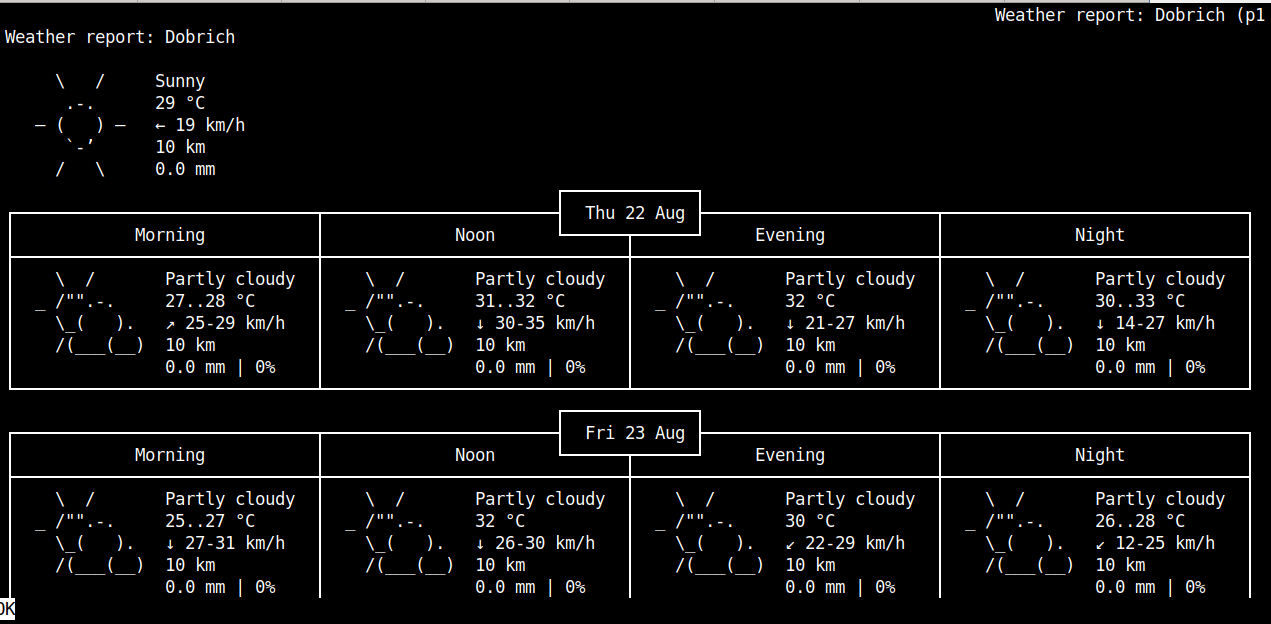
Default links (Linux) www text browser produces ugly black and white
2. Displaying Weather forecast with wget
wget -O- -q http://wttr.in
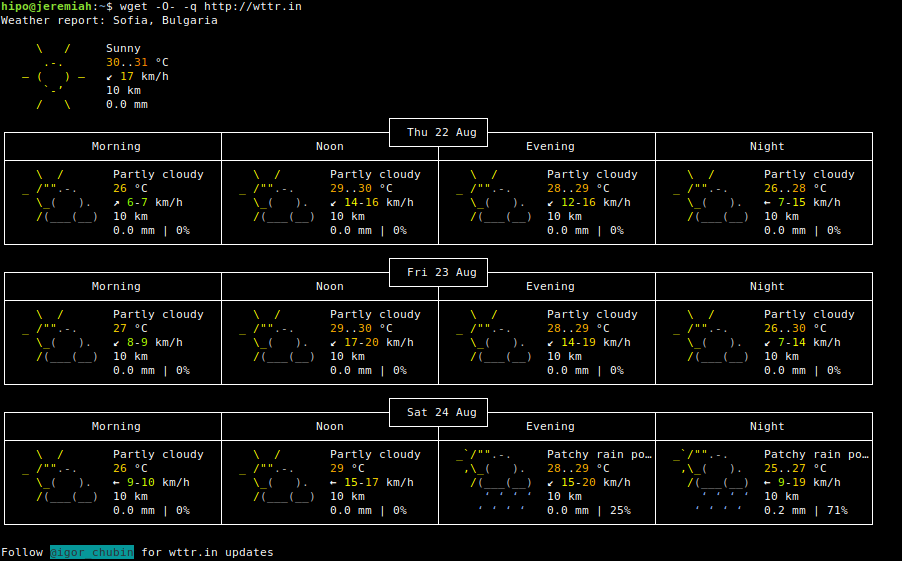
If you're lazy you can even omit the http:// as wget will look for HyperText Transmission Protocol by itself
wget -O- -q wttr.in
3. Getting Forecast results for a Tourist Destination
Lets get the weather forecast for the popular tourist Bulgarian destination of the Seven Rila Lakes (near Rila Monastery), situated in the Rila Mountain BG.
curl http://wttr.in/Seven+Rila+Lakes
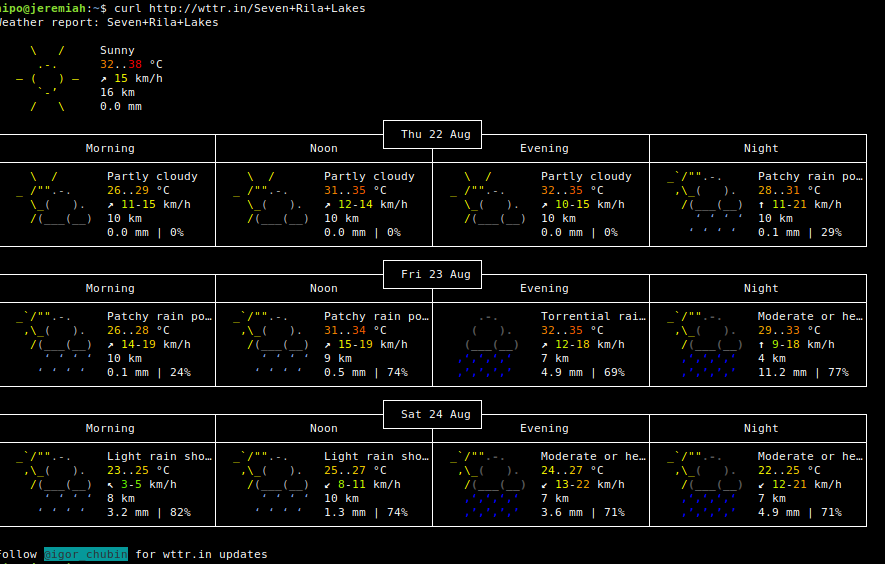
4. Display Forecast for a specific server IP
Displaying information on specific server IP address current situated in GeoIP database, of course could be not really true, as the IP could be just a Load Balancer a router that does NAT to some internal DMZ-ed location server, but anyways it is a cool feature.
Lets get information on what is the weather on Google Global's Public DNS server IP 8.8.8.8 so commonly used to guarantee a Windows and Linux Desktop client machines Internet connectivity.
curl wttr.in/@8.8.8.8
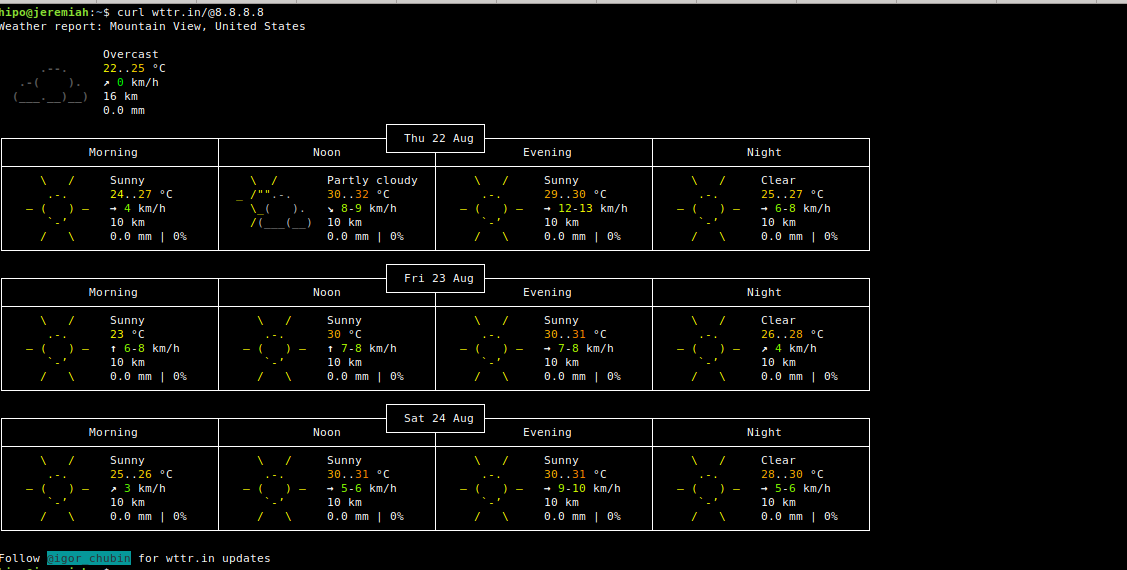
5. Download PNG image picture from wttr.in service
Lets say you want to get a 3 days standard Weather forecast for the popular Black Sea Resort town in Bulgaria Pomorie (a beautiful sea city which has even a functioning 5 Monks Monastery Pomorie Monastery situated near sea coast)
curl http://wttr.in/Pomorie.png
–2019-08-22 20:15:51– http://wttr.in/Pomorie.png
Resolving wttr.in (wttr.in)… 5.9.243.187
Connecting to wttr.in (wttr.in)|5.9.243.187|:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 42617 (42K) [image/png]
Saving to: ‘Pomorie.png’
Pomorie.png 100%[=======================================================================================================>] 41.62K –.-KB/s in 0.07s
2019-08-22 20:15:52 (586 KB/s) – ‘Pomorie.png’ saved [42617/42617]
Note: The generated .png is again the ASCII art produced by a direct text fetch bug in pic format
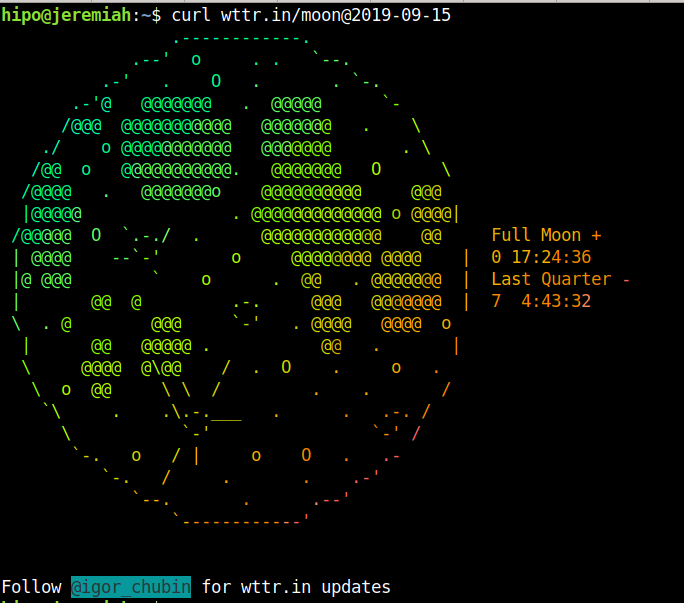
6. Displaying Current Moon Phase
If you want to enjoy a text based Moon phase picture through wttr.in 🙂
wget -O- -q wttr.in/Moon
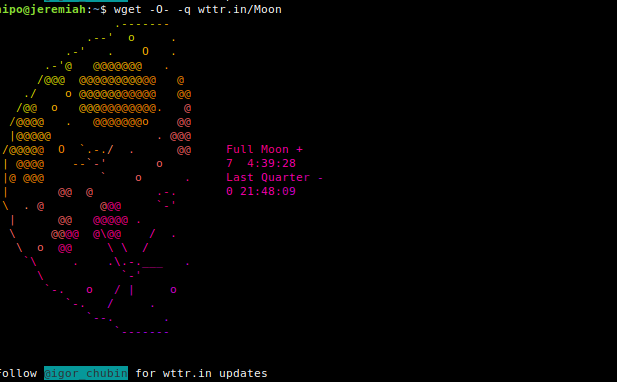
You can also get a Moon Phase prognosis for a current future date or get a previous date phase
curl wttr.in/moon@2019-09-15

Full Moon Madness !! – Vampires are out beaware and Enjoy the ultra kewl ASCII Colorful Art 🙂
7. Getting help for wttr.in terminal Waether Forecast results
$ curl wttr.in/:help
Usage:
$ curl wttr.in # current location
$ curl wttr.in/muc # weather in the Munich airport
Supported location types:
/paris # city name
/~Eiffel+tower # any location
/Москва # Unicode name of any location in any language
/muc # airport code (3 letters)
/@stackoverflow.com # domain name
/94107 # area codes
/-78.46,106.79 # GPS coordinates
Special locations:
/moon # Moon phase (add ,+US or ,+France for these cities)
/moon@2016-10-25 # Moon phase for the date (@2016-10-25)
Units:
m # metric (SI) (used by default everywhere except US)
u # USCS (used by default in US)
M # show wind speed in m/s
View options:
0 # only current weather
1 # current weather + 1 day
2 # current weather + 2 days
A # ignore User-Agent and force ANSI output format (terminal)
F # do not show the "Follow" line
n # narrow version (only day and night)
q # quiet version (no "Weather report" text)
Q # superquiet version (no "Weather report", no city name)
T # switch terminal sequences off (no colors)
PNG options:
/paris.png # generate a PNG file
p # add frame around the output
t # transparency 150
transparency=… # transparency from 0 to 255 (255 = not transparent)
Options can be combined:
/Paris?0pq
/Paris?0pq&lang=fr
/Paris_0pq.png # in PNG the file mode are specified after _
/Rome_0pq_lang=it.png # long options are separated with underscore
Localization:
$ curl fr.wttr.in/Paris
$ curl wttr.in/paris?lang=fr
$ curl -H "Accept-Language: fr" wttr.in/paris
Supported languages:
af da de el et fr fa hu id it nb nl pl pt-br ro ru tr uk vi (supported)
az be bg bs ca cy cs eo es fi ga hi hr hy is ja jv ka kk ko ky lt lv mk ml nl fy nn pt pt-br sk sl sr sr-lat sv sw th te uz zh zu he (in progress)
Special URLs:
/:help # show this page
/:bash.function # show recommended bash function wttr()
/:translation # show the information about the translators
8. Comparing two cities weather from command line
One useful use of wttr.in if you plan to travel from Location city A to Location city B is to compare the temperatures with a simple bash one liner script:
diff -Naur <(curl -s http://wttr.in/Sofia ) <(curl -s http://wttr.in/Beograd )
9. Using ansiweather command to get Weather Temperature / Wind / Humidity in one line beuatiful text
If you go and install answeather Linux package
apt-get install –yes ansiweather
You will get a shell script wrapper with ANSI colors and Unicode symbols support. Weather data comes from OpenWeatherMap, this is useful if wttr.in is not working due to some URL malfunction (due to service is DoS-ed) etc.
ansiweather -l Atina

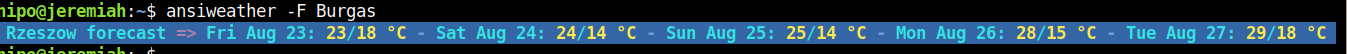
Lets use ansiweather to print the weather prognosis for upcoming 5 days for near port of Burgas, BG
ansiweather -F -l Burgas
10. Get all Weather current forecast for each Capital in the world
You can download and use this simple plain text file list of All Country Capitals in the World (country-capitals-all-world.txt) with ansiweather and a bash loop to get displayed each and every current day Weather Forecast in the World, here is how:
while read line; do ansiweather -l $line; sleep 3; done < country-capitals-all-world.txt
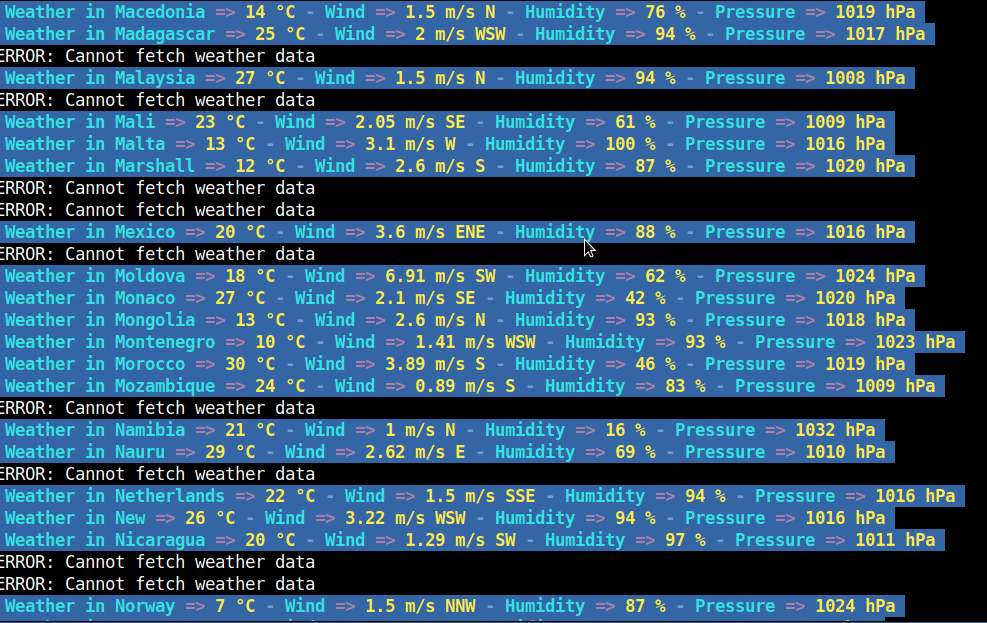
As you can see some of the very exotic third world capitals does not return data so 'ERROR: Cannot fetch weather data' is returned.
You can also substitute ansiweather with curl wttr.in/$line to do get the beautiful ASCII art 3 days weather forecast via wttr.in
while read line; do curl http://wttr.in/$line; sleep 3; done < country-capitals-all-world.txt
I'll be happy to know other nice ASCII Art supporting Web service to enjoy from text terminal on Linux (nomatter useful or) just funny joyful prank maniacal pranks such as Watching text ASCII version remake of Star Wars Classic Movie by simply telnetting to towel.blinkenlights.nl (if you haven't so just telnet and enjoy the streamed ASCIIs ! 🙂
telnet towel.blinkenlights.nl
Talking about fun and ASCII, its worthy to mention hollywood Linux package
hipo@jeremiah:~/Desktop$ apt-cache show hollywood|grep -i desc -A 3
Description-en: fill your console with Hollywood melodrama technobabble
This utility will split your console into a multiple panes of genuine
technobabble, perfectly suitable for any Hollywood geek melodrama.
It is particularly suitable on any number of computer consoles in the
—
Description-md5: 768f44c76220ea2b35f855ea34c8bc35
Homepage: http://launchpad.net/hollywood
Section: games
Priority: optional
Once installed on Debian with:
aptitude install -y hollywood
…
You can get in a rapid manner plenty of tmux (screen like – virtual console emulator) split screen statistics about your notebook / workstation / server CPU usage, mlocate.db status, info about plugged in machine voltage, Speedometer (statistics about Network bandwidth usage), System load avarage (CPU Count, Memory Utilization) and some other random info coming out of dmesg kernel log and more. The information displayed in splitted windows changes rapidly and (assuming you run it at home Desktop with a soundblaster) and not remotely, a james bond Agent 007 soundtrack is played on the back, that brings up one's adrenaline and makes it look even cooler.
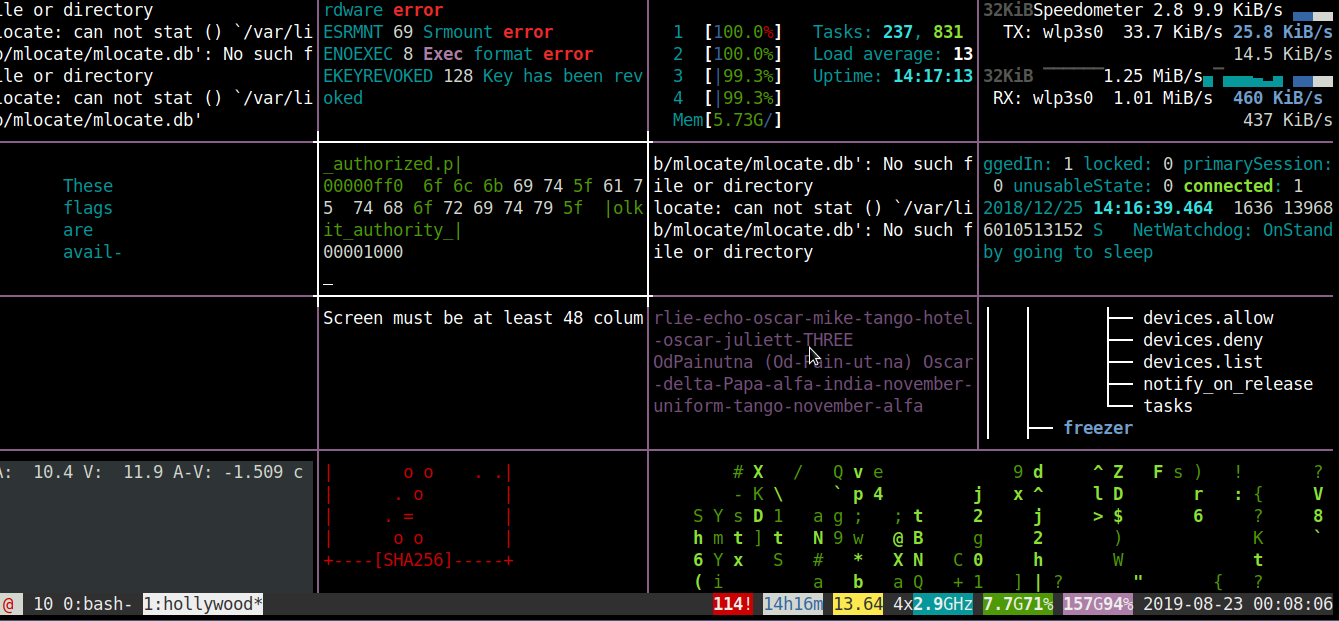
To give you an idea what to expect, here is shot of /usr/games/hollywood (the program start binary location) on Debian GNU / Linux running, Enjoy! 🙂