Earlier I've written a an article MobaXTerm: A good gnome-terminal like tabbed SSH client for Windows / Windows Putty Tabs Alternative in which I've introduced the best in my opinion SSH / Telnet / VNC / RDP / Xserver in one Terminal client emulator for Windows operating systems.
The client has been around for quite some time and it has been improving rapidly over the last 10 years, where it now more looks like a separate Operating System than a single terminal client. It's size is quite compact as well and my opinion and every self respectiving developer, system administrator, IT geek or a hacker would definitely
use the mobaxterm at home or at work place on a daily. I guess some of my readers, who have already migrated SuperPutty / SecureCRT or Putty / XMing or whatever kind of exotic Remote SSH Console terminal is used could validate this 🙂
Therefore as I've set up Mobaxterm on a multiple computers all around, I've found it useful to write a small article with some post-install hints (tune ups) one can do immediately once he has installed the Desktop or Portable Apps version of mobaxterm on desktop PC / notebook.
1. Set up your bashrc server / command aliases
Lets say you need to setup some rules for connectivity via a socks proxy to dig holes over a harsh company firewalls or add
custom options to every ssh client attempt to remote server, or simply alias some of your servers with custom connectivity options and so on simply open vi / vim text editor from mobaxterm local terminal and place inside your rules, for example that could be anything like:
alias ssh='ssh -o stricthostkeychecking=no -o passwordauthentication=yes -o PreferredAuthentications=password -v'
alias sftp='sftp -o stricthostkeychecking=no -o passwordauthentication=yes -o PreferredAuthentications=password'
alias work-server='ssh UserName@work-server -v -o passwordauthentication=yes -o PreferredAuthentications=password'alias proxy='ssh -D 3128 UserName@proxyIP-host1 -o ConnectTimeout=80'
alias proxy1='ssh -D 3128 UserName@proxy-host2 -p 443 -o ConnectTimeout=60'
alias proxy3='ssh -D 3128 Username@proxy-host3 -p 443 -o ConnectTimeout=60'Simply open the terminal and setup whatever you require
export ftp_proxy="http://proxy-host:8080"
export https_proxy="https://proxy-host:8080"
export http_proxy="http://proxy-host:8080"
export HTTP_PROXY="http://proxy-host:8080"
export HTTPS_PROXY="http://proxy-host:8080"
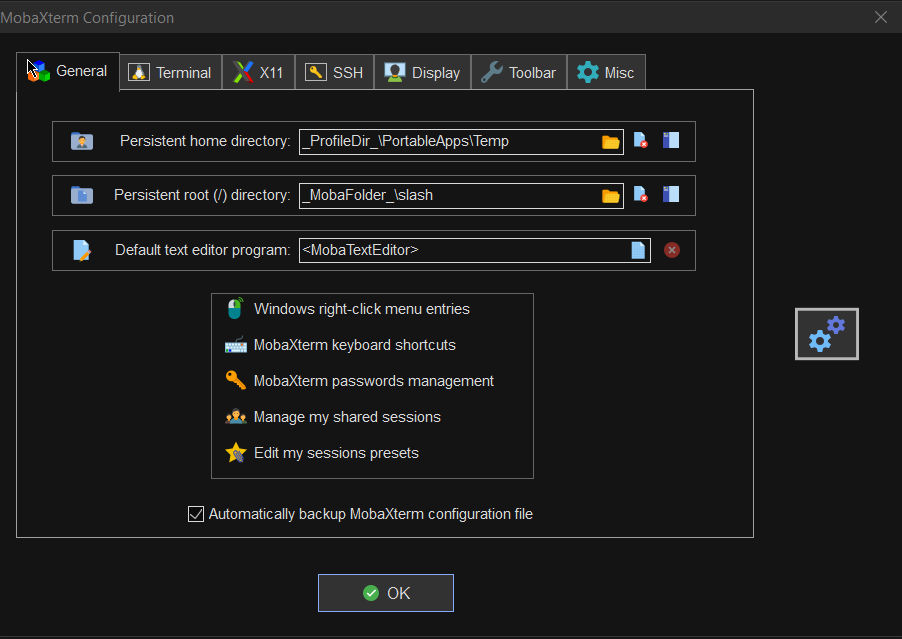
2. Set mobaxterm presistent directory / persistent root directory and default text editor
Make sure you have properly defined at least Persistent directory / Persistent directory if you want to keep the files under your /home/mobaxterm and root directory be able to save your data from local mobaxterm terminal work you have done.
To do so o to Configuration -> General
3. Change default settings for Opening / Closing Terminal tabs just like in gnome-terminal
MobaXterm is really awesome as the developer, followed pretty much the logic of some common GNU / Linux Terminal clients like Gnome-Terminal and KDE's default Konsole terminal.
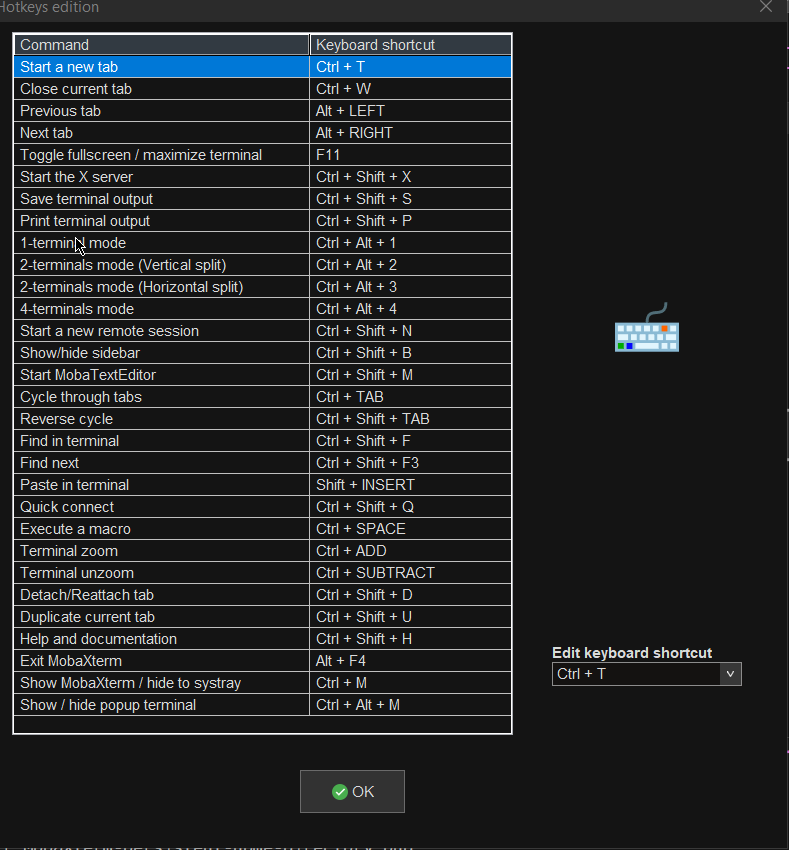
One of the first things to do once Mobaxterm is installed on the PC is to set up nice key binds as default onces might be heard to learn at the beginning or you might have already the habit to use the certain set of key combinations on your Linux desktop:
Common once are:
1. Open tab / Close tab common once I bind to are (CTRL + T / CTRL + W)
2. Previous tab move / Next tab move keys common one I use are (ALT + LEFT / ALT + RIGHT)
3. Find in terminal (CTRL + F)
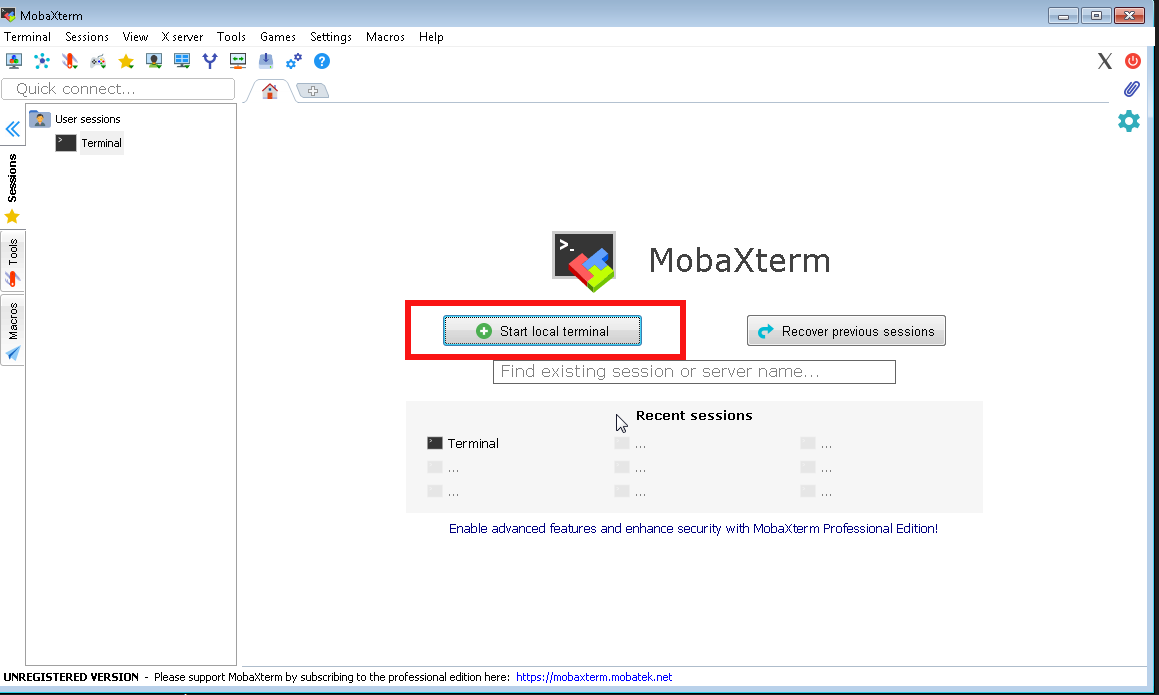
4. Make MobaXterm to automatically open a terminal to not Start local terminal every time
By default mobaxterm it is really annoying cause every time you run it after system reboot you have to select
Start local terminal
Once you run the terminal you get this prompt and you have to press on Start local terminal
How to make Mobaxterm automatically open local Terminal Tab on every boot?
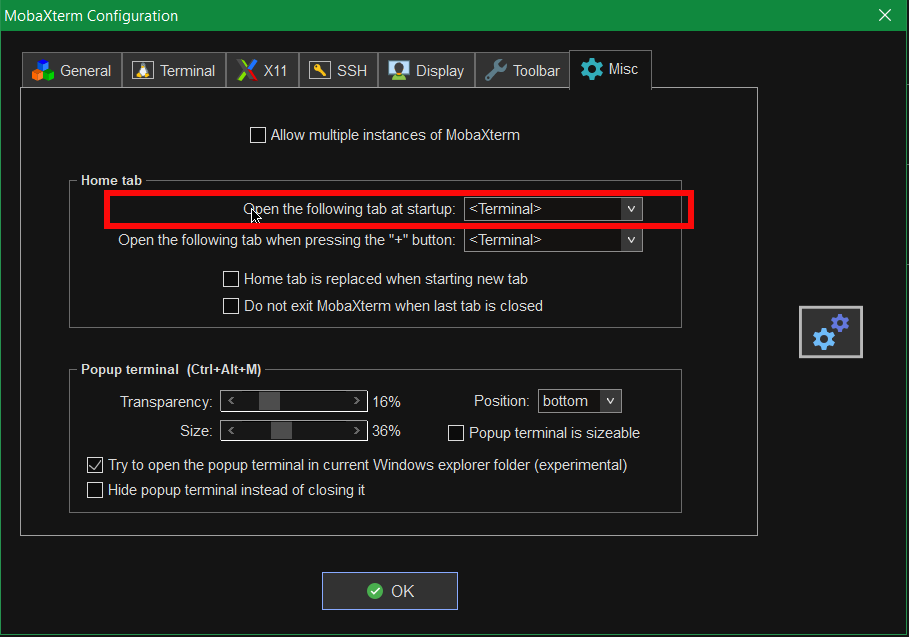
To fix this so every time a local terminal is spawn on MobaXterm you have get to:
Settings -> Configuration -> Misc
Open the Following tab at startup by default it will be
<Home (Pinned)>
Change it to:
<Terminal>
That's it on next login your Local Terminal with /bin/bash.exe will auto load !
[hipo.WINDOWS-PC] ➤ env|grep -i SHELL
SHELL=/bin/bash.exe
PATH=/bin:/drives/c/Users/hipo/DOCUME~1
/MobaXterm/slash/bin:/drives/c/Windows:/drives/c/Windows/system32:/drives/c/Windows/system32:/drives/c/Windows:/drives/c/Windows/System32/Wbem:
/drives/c/Windows/System32/WindowsPowerShell/v1.0:/drives/c/Windows/sysnative
PSModulePath=C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
CMDPATH=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;
C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\sysnative\;
C:\Users\hipo\DOCUME~1\MobaXterm\slash\bin
WINPATH=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\sysnative\
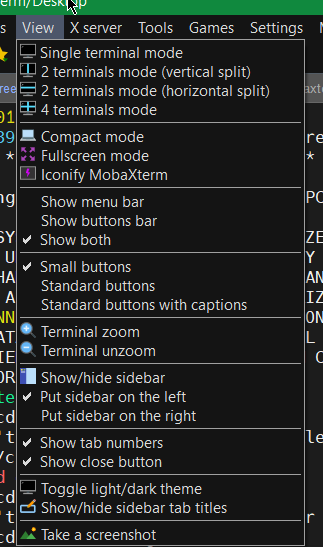
5. Make menu buttons to appear smaller
Go to menu and select
View -> (Small Buttons)
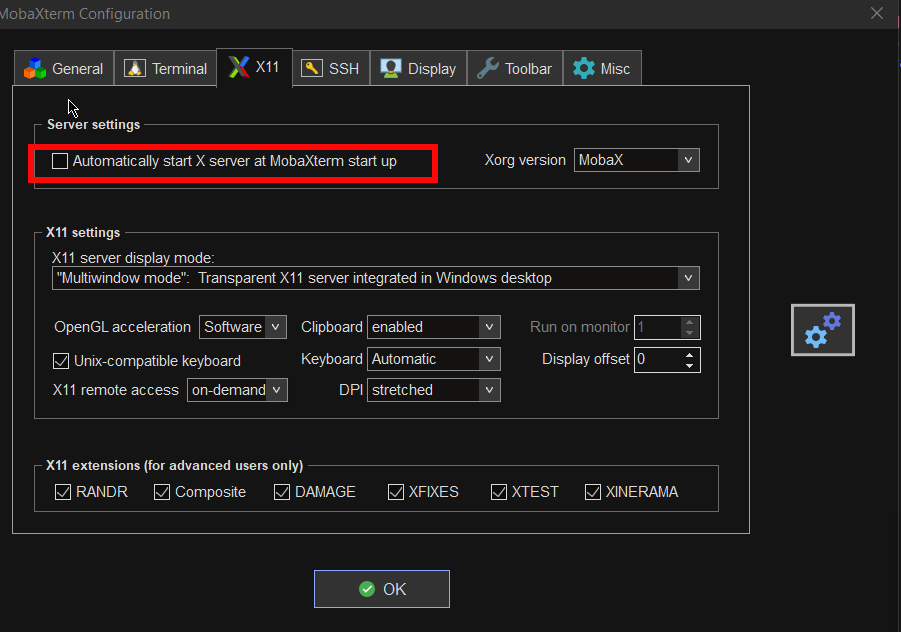
6. Disable auto start of XServer to prevent a port listener on the machine on TCP port
By default mobaxterm opens XServer listener, so you can immediately connect from a remote SSH servers missing Xserver and install software requiring an XServer, for example software such as Oracle Database or some MiddleWare WebLogig or IBM's Web Sphere. This is useful but if you want to have a good security only allow this server on a purpose. Otherwise the XServer will run in parallel with rest of your Moba and just load up your PC and eat up some RAM memory. To disable it go to:
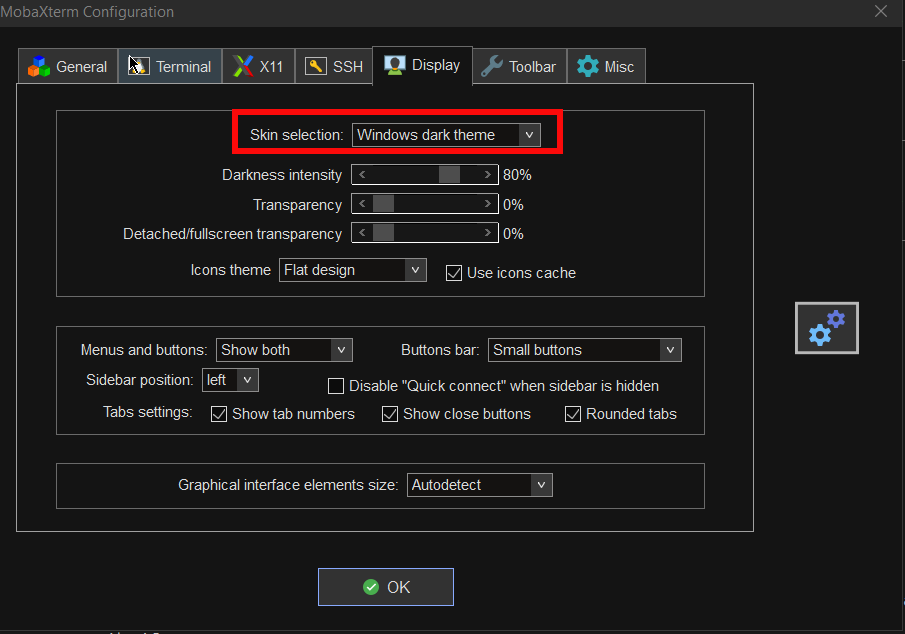
7. Change the mobaxterm Default theme to Dark
This is optional I like to set the Theme to Dark, also as a Theme for Windows as well as for MobaxTerm, the aim of that is simply to not put extra stress on my eye sight. Being on the PC around 8 to 10 hours and spending some 6 to 8 hours on console work is enough. If you want to do as well.
8. Install additional set of common Linux tools to mobaxterm to use on Windows
Tools such as:
1. Midnight Commander (mc)
2. Wget
3. Curl
4. Vim
5. Screen
6. Rsync
7. Perl
8. W3m
9. dosunix
10. unix2dos
11. gnupg
12. diffutils
13. mysql
14. mpg123
15. whois
If you want to have a set of packages pre-installed that are including above as well as the rest of mine, here is a dump of my installed mobapt manager packages:
For more simply use the experimental Mobaxterm Graphical Package installer
[hipo.WINDOWS-PC] ➤ for i in $(cat Downloads/installed-packages-mobaxterm.txt ); do apt-cyg install $i; done
Found package GeoIP-database
Installing GeoIP-database
Downloading GeoIP-database-20180505-1.tar.xz…
Unpacking GeoIP-database-20180505-1.tar.xz…
Running postinstall scripts
Package GeoIP-database installed.Rebasing new libraries
Found package adwaita-icon-theme
Installing adwaita-icon-theme
Downloading adwaita-icon-theme-3.26.1-1.tar.xz……
You will be prompted for a single Yes for the respository
MobApt Packages Manager
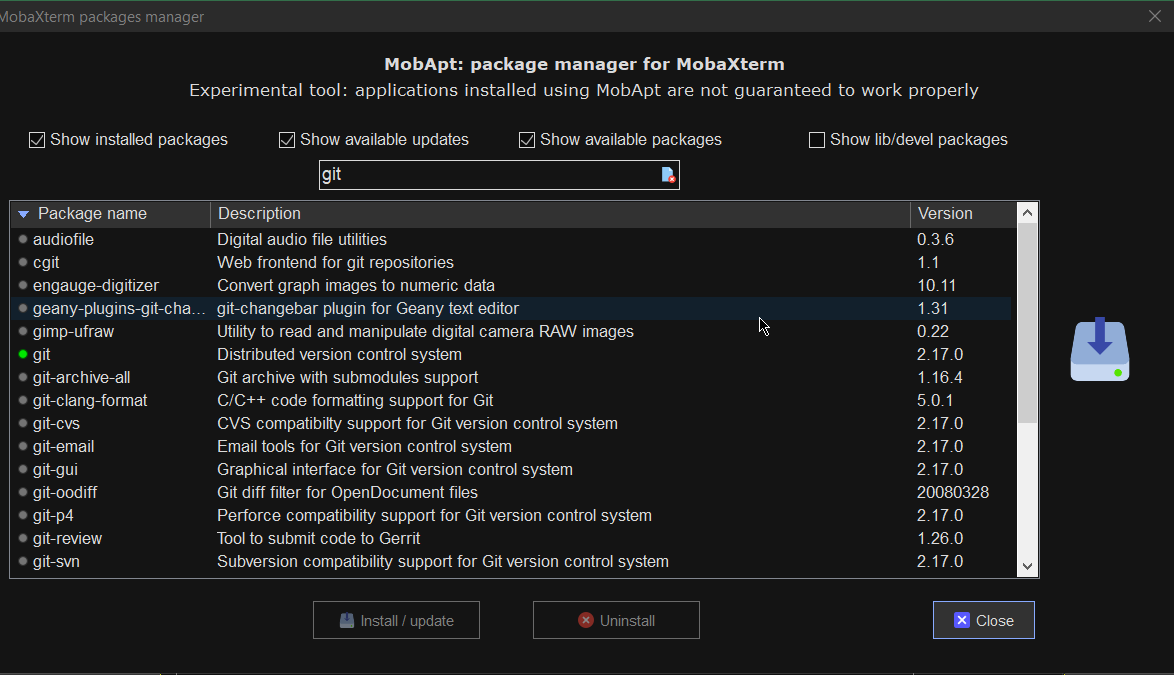
Though it is said it is experimental, I have to say the MobApt Apt Manager works quite good, I never had any issues with it so far.
9. Mobaxterm.ini the settings storage file that can help you move your configurations
If you have to prepeare new MobaXterm on multiple PCs frequently perhaps it is best to just copy the Mobaxterm.ini file.
Here is an example of my mobaxterm.ini for download.
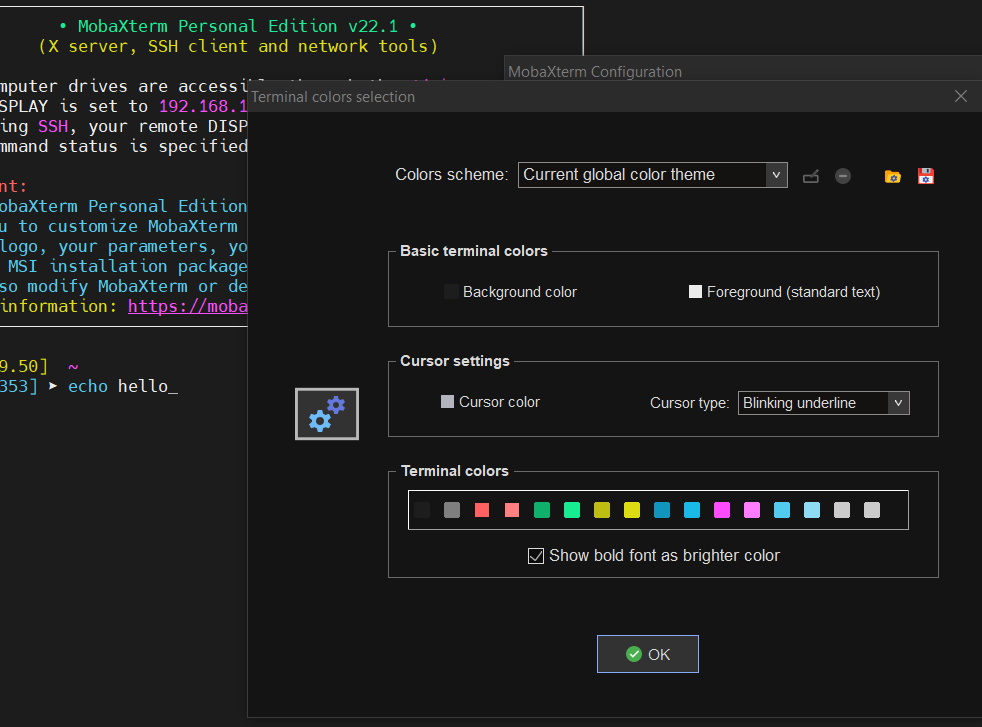
10. Change terminal colors and curor type and enable blinking (customizations)
Settings -> Configuration -> Terminal -> (Default Terminal Color Settings)
11. Use very useful moba Tools
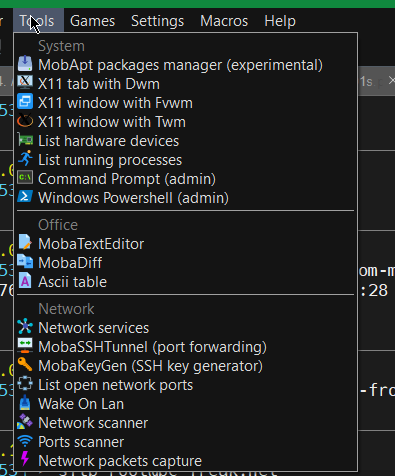
For sysadmins Moba has plenty of other jems such as:
-
Network Port scanner such as Nmap with GUI
-
list open network ports (GUI interface to netmap)
-
SSH tunnel tool
-
Moba Diff
-
Wake on Lan
-
Network Packet capturer (such as tcpdump)
-
List running processes (such as taskmgr in simple form)
-
List machine hardware devices (such as Windows Device manager)
12. Remote monitoring of opened ssh session
To enable remote monitoring for a Saved session simply use the "Remote monitoring" button on the down left corner of the terminal.
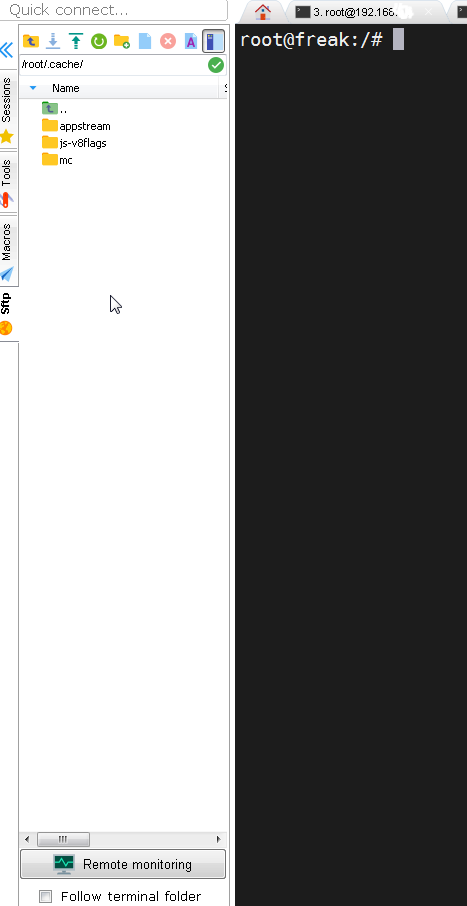
Or to enable it for a new host, open:
1. "Saved sessions"
2. Click over "User sessions"
3. New Session -> (SSH)
4. Basic SSH Settings (Remote host) -> OK
5. Click over the new created session
6. Click on Remote monitoring for the opened session
13. Play some mobaxterm console games
As you might have pissed off of configuring go on and enjoy some of the great console games, some of which are also present on a normal Linux new distribution installation. 🙂
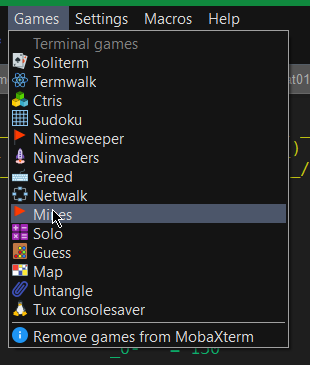
List of Moba Games
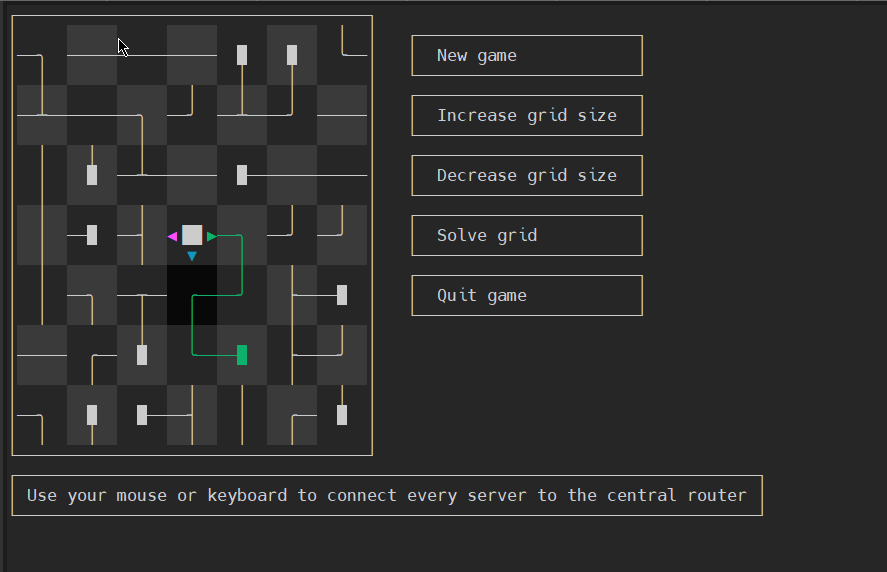
TeamWalk (Use your mouse or keyboard to connect every server to the central router)
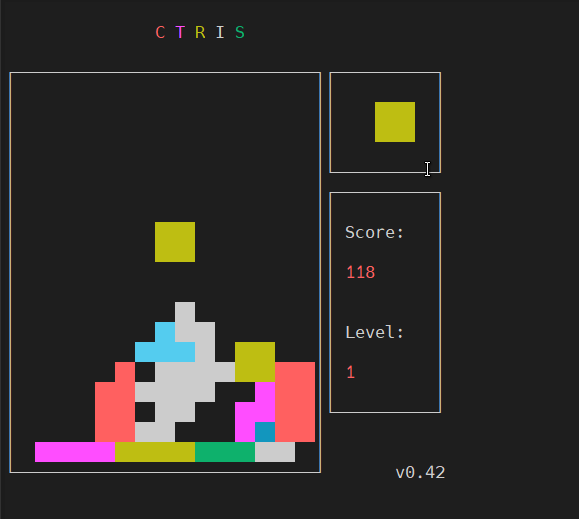
Ctris Console tetris from Mobaxterm
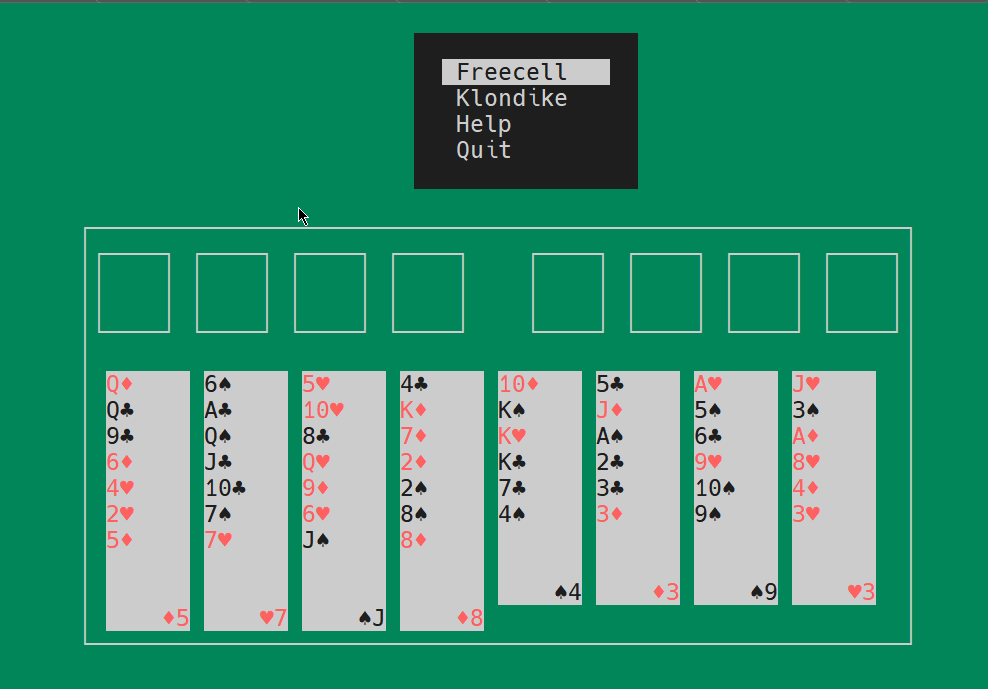
Text console Solitaire from Moba
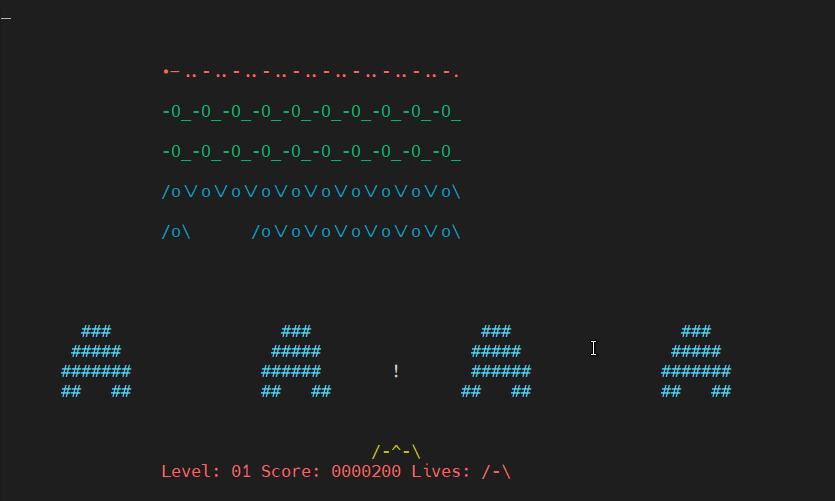
Here is NinVaders (Text Version of Space Invaders Arcade Classic)
Enjoy ! 🙂