Posts Tagged ‘deb package’
Wednesday, March 6th, 2013 On Debian based GNU / Linux distros, there are some critical packages which need to be disabled to update during the common routine apt-get update && apt-get upgrade which is a almost daily part of Debian sysadmin living. Example for packages which are good to mark not to upgrade are for example; linux kernel, java virtual machine, adobe flash plugin, etc.
Setting a package to omit upgrade on system package update for adobe flash plugin for example is with:
# echo adobe-flashplugin hold | dpkg –set-selections
debian:~# echo adobe-flash-properties-gtk hold | dpkg --set-selections
debian:~# echo flashplugin-nonfree-extrasound hold | dpkg --set-selections
To do deb package update on hold for kernel;
debian:~# echo linux-image-generic hold | dpkg --set-selections
debian:~# echo linux-image-3.2.0-38-generic | dpkg --set-selections
Do the same for as many packages which seem to break up on updates and when, you explicitly want remove the hold/s run:
debian:~# echo adobe-flashplugin install | dpkg --set-selections
....
debian:~# echo linux-image-generic install | dpkg --set-selections
Tags: adobe flash plugin, critical packages, deb package, java virtual machine, Linux, linux distros, linux kernel, sysadmin, system updates, Ubuntu
Posted in Linux, System Administration | No Comments »
Tuesday, March 5th, 2013 I just had to configure a Matrox Graphics MGA G200 AGP on a very old computer installed with Xubuntu 12.04. The Graphic card is not automatically detected and Xorg Linux server automatically runs X without generating any config in /etc/X11/xorg.conf after Xubuntu install. By default Linux uses the VESA driver for running X, the problem with VESA is it is very slow in videos and is only good for text reading and simple browsing. For watching video and Youtube, one needs to install the custom Video card driver on this host the Video card was identifying in lpsci as:
user@oldhost:~$ lspci |grep -i matrox
01:00.0 VGA compatible controller: Matrox Graphics, Inc. MGA G200 AGP (rev 03)
In deb package repositories, there is a special xorg MGA driver suited to run MGA cards, thus to use it I had to first install it with:
user@oldhost:~# apt-get install --yes xserver-xorg-video-mga
....
For allowing card to normally watch movies – you have to have installed a special video driver which is to be lated built from source:
user@oldhost:~# apt-get -b source mga-vid-source
user@oldhost:~# dpkg -i /usr/src/modules/mga-vid/debian/mga-vid-source_2.6.32-1_i386.deb
....
There is also special program to test if MGA video driver is installed and work correctly mga_vid_test. To have it installed and use it you have to be running on 2.6.x Linux kernel cause it is a bit of old software plus it is necessary to have installed mga-vid-common i.e.:
user@oldhost:~# apt-get install --yes mga-vid-common
.....
I did a quick research online for other people who faced similar problem and found in Ubuntu Forums the following MGA G200 recommended xorg.conf
Below config was little modified by me as by default it was configured to run in 1280×1024 in 24 bit depth color. Usually 24 bit color is high for old cards, plus the resolution of 1280 seemed quite high for this piece of old iron, so I decided to use the better suiting old computers 1024×768 in 16 bit color depth.
Tags: bit depth, deb package, graphic card, lspci, matrox graphics, old computer, old computers, old iron, old software, text reading, vesa driver, video card driver, video driver, youtube
Posted in Linux and FreeBSD Desktop, Linux Audio & Video | 1 Comment »
Saturday, March 17th, 2012 Default XFce picture viewer on Slackware Linux is GIMP (GNU Image Manipulation Program). Though GIMP is great for picture editting, it is rather strange why Patrick Volkerding compiled XFCE to use GIMP as a default picture viewer? The downsides of GIMP being default picture viewing program for Slackware's XFCE are the same like Xubuntu's XFCE risterroro, you can't switch easily pictures back and forward with some keyboard keys (left, right arrow keys, backspace or space etc.). Besides that another disadvantage of using GIMP are;
a) picture opening time in GIMP loading is significantly higher if compared to a simple picture viewer program like Gnome's default, eye of the gnome – eog.
b) GIMP is more CPU intensive and puts high load on each picture opening
A default Slackware install comes with two good picture viewing programs substitute for GIMP:
- Gwenview
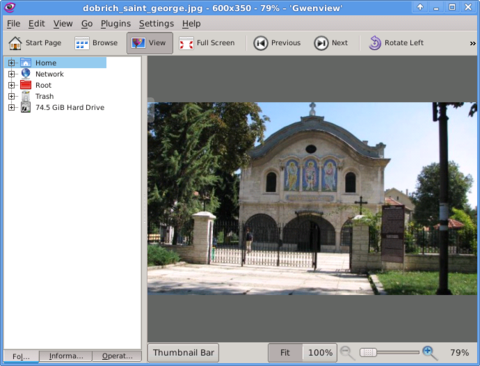
-
- Geeqie
-
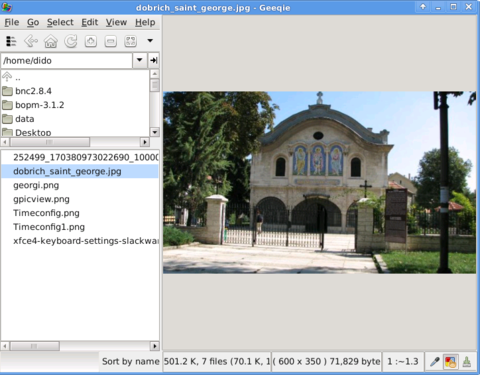
Both of the programs support picture changing, so if you open a picture you can switch to the other ones in the same directory as the first opened one.
I personally liked more Gwenview because it has more intutive picture switching controls. With it you can switch with keyboard keys space and backspace
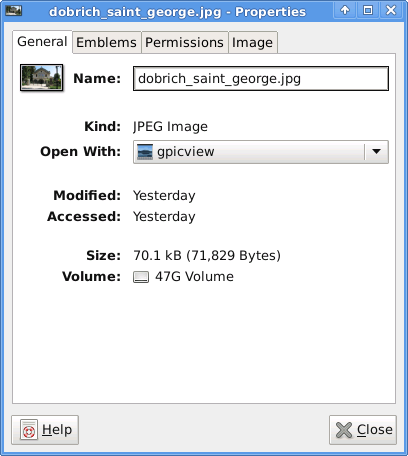
To change GIMP's default PNG, JPEG opening I had with mouse right button over a pic and in properties change, Open With: program.
If you're curious about the picture on on all screenshots, this is Church – Saint George (situated in the city center of Dobrich, Bulgaria).
St. Georgi / St. George Church is built in 1842 and is the oldest Orthodox Church in Dobrich.
In the Crimean War (1853-1856) the church was burned down and was restored to its present form in 1864.
gpicview is another cool picture viewing program, I like. Unfortunately on Slackware, there is no prebuild package and the only option is either to convert it with alien from deb package or to download source and compile as usual with ./configure && make && make install .
Downloading and compiling from source went just fine on Slackware Linux 13.37gpicview has more modern looking interface, than gwenview and geeqie. and is great for people who want to be in pace with desktop fashion 🙂
Tags: arrow, arrow keys, Auto, backspace, Button, center, change, city, configure, crimean war 1853, deb package, Desktop, desktop environment, dobrich bulgaria, download, Draft, eye, georgi, GIMP, Gnome, gnu image manipulation, gnu image manipulation program, image manipulation program, keyboard keys, manipulation, nbsp, Open, opening time, option, orthodox church, other ones, package, picture editting, png, program, Risterroro, st george church, substitute, time, XFCE, Xubuntu
Posted in Linux and FreeBSD Desktop, System Administration | No Comments »
Thursday, June 30th, 2011 
Recently has become publicly known for the serious hole found in all Apache webserver versions 1.3.x and 2.0.x and 2.2.x. The info is to be found inside the security CVE-2011-3192 – https://issues.apache.org/bugzilla/show_bug.cgi?id=51714
Apache remote denial of service is already publicly cirtuculating, since about a week and is probably to be used even more heavily in the 3 months to come. The exploit can be obtained from exploit-db.com a mirror copy of #Apache httpd Remote Denial of Service (memory exhaustion) is for download here
The DoS script is known in the wild under the name killapache.pl
killapache.pl PoC depends on perl ForkManager and thus in order to be properly run on FreeBSD, its necessery to install p5-Parallel-ForkManager bsd port :
freebsd# cd /usr/ports/devel/p5-Parallel-ForkManager
freebsd# make install && make install clean
...
Here is an example of the exploit running against an Apache webserver host.
freebsd# perl httpd_dos.pl www.targethost.com 50
host seems vuln
ATTACKING www.targethost.com [using 50 forks]
:pPpPpppPpPPppPpppPp
ATTACKING www.targethost.com [using 50 forks]
:pPpPpppPpPPppPpppPp
...
In about 30 seconds to 1 minute time the DoS attack with only 50 simultaneous connections is capable of overloading any vulnerable Apache server.
It causes the webserver to consume all the machine memory and memory swap and consequently makes the server to crash in most cases.
During the Denial of Service attack is in action access the websites hosted on the webserver becomes either hell slow or completely absent.
The DoS attack is quite a shock as it is based on an Apache range problem which started in year 2007.
Today, Debian has issued a new versions of Apache deb package for Debian 5 Lenny and Debian 6, the new packages are said to have fixed the issue.
I assume that Ubuntu and most of the rest Debian distrubtions will have the apache's range header DoS patched versions either today or in the coming few days.
Therefore work around the issue on debian based servers can easily be done with the usual apt-get update && apt-get upgrade
On other Linux systems as well as FreeBSD there are work arounds pointed out, which can be implemented to close temporary the Apache DoS hole.
1. Limiting large number of range requests
The first suggested solution is to limit the lenght of range header requests Apache can serve. To implement this work raround its necessery to put at the end of httpd.conf config:
# Drop the Range header when more than 5 ranges.
# CVE-2011-3192
SetEnvIf Range (?:,.*?){5,5} bad-range=1
RequestHeader unset Range env=bad-range
# We always drop Request-Range; as this is a legacy
# dating back to MSIE3 and Netscape 2 and 3.
RequestHeader unset Request-Range
# optional logging.
CustomLog logs/range-CVE-2011-3192.log common env=bad-range
CustomLog logs/range-CVE-2011-3192.log common env=bad-req-range
2. Reject Range requests for more than 5 ranges in Range: header
Once again to implement this work around paste in Apache config file:
This DoS solution is not recommended (in my view), as it uses mod_rewrite to implement th efix and might be additionally another open window for DoS attack as mod_rewrite is generally CPU consuming.
# Reject request when more than 5 ranges in the Range: header.
# CVE-2011-3192
#
RewriteEngine on
RewriteCond %{HTTP:range} !(bytes=[^,]+(,[^,]+){0,4}$|^$)
# RewriteCond %{HTTP:request-range} !(bytes=[^,]+(?:,[^,]+){0,4}$|^$)
RewriteRule .* - [F]
# We always drop Request-Range; as this is a legacy
# dating back to MSIE3 and Netscape 2 and 3.
RequestHeader unset Request-Range
3. Limit the size of Range request fields to few hundreds
To do so put in httpd.conf:
LimitRequestFieldSize 200
4. Dis-allow completely Range headers: via mod_headers Apache module
In httpd.conf put:
RequestHeader unset Range
RequestHeader unset Request-Range
This work around could create problems on some websites, which are made in a way that the Request-Range is used.
5. Deploy a tiny Apache module to count the number of Range Requests and drop connections in case of high number of Range: requests
This solution in my view is the best one, I've tested it and I can confirm on FreeBSD works like a charm.
To secure FreeBSD host Apache, against the Range Request: DoS using mod_rangecnt, one can literally follow the methodology explained in mod_rangecnt.c header:
freebsd# wget http://people.apache.org/~dirkx/mod_rangecnt.c
..
# compile the mod_rangecnt modulefreebsd# /usr/local/sbin/apxs -c mod_rangecnt.c
...
# install mod_rangecnt module to Apachefreebsd# /usr/local/sbin/apxs -i -a mod_rangecnt.la
...
Finally to load the newly installed mod_rangecnt, Apache restart is required:
freebsd# /usr/local/etc/rc.d/apache2 restart
...
I've tested the module on i386 FreeBSD install, so I can't confirm this steps works fine on 64 bit FreeBSD install, I would be glad if I can hear from someone if mod_rangecnt is properly compiled and installed fine also on 6 bit BSD arch.
Deploying the mod_rangecnt.c Range: Header to prevent against the Apache DoS on 64 bit x86_amd64 CentOS 5.6 Final is also done without any pitfalls.
[root@centos ~]# uname -a;
Linux centos 2.6.18-194.11.3.el5 #1 SMP Mon Aug 30 16:19:16 EDT 2010 x86_64 x86_64 x86_64 GNU/Linux
[root@centos ~]# /usr/sbin/apxs -c mod_rangecnt.c
...
/usr/lib64/apr-1/build/libtool --silent --mode=link gcc -o mod_rangecnt.la -rpath /usr/lib64/httpd/modules -module -avoid-version mod_rangecnt.lo
[root@centos ~]# /usr/sbin/apxs -i -a mod_rangecnt.la
...
Libraries have been installed in: /usr/lib64/httpd/modules
...
[root@centos ~]# /etc/init.d/httpd configtest
Syntax OK
[root@centos ~]# /etc/init.d/httpd restart
Stopping httpd: [ OK ]
Starting httpd: [ OK ]
After applying the mod_rangecnt patch if all is fine the memory exhaustion perl DoS script's output should be like so:
freebsd# perl httpd_dos.pl www.patched-apache-host.com 50
Host does not seem vulnerable
All of the above pointed work-arounds are only a temporary solution to these Grave Apache DoS byterange vulnerability , a few days after the original vulnerability emerged and some of the up-pointed work arounds were pointed. There was information, that still, there are ways that the vulnerability can be exploited.
Hopefully in the coming few weeks Apache dev team should be ready with rock solid work around to the severe problem.
In 2 years duration these is the second serious Apache Denial of Service vulnerability after before a one and a half year the so called Slowloris Denial of Service attack was capable to DoS most of the Apache installations on the Net.
Slowloris, has never received the publicity of the Range Header DoS as it was not that critical as the mod_range, however this is a good indicator that the code quality of Apache is slowly decreasing and might need a serious security evaluation.
Tags: apache httpd, apache server, apache webserver, ATTACKING, bugzilla, CentOS, com, config, copy, CustomLog, deb package, denial of service, denial of service attack, dos attack, dos script, download, exploit, freebsd, host, HTTP, info, machine memory, memory exhaustion, minute time, mirror copy, mod, necessery, Netscape, number, perl httpd, poc, pPpPpppPpPPppPpppPp, REJECT, Remote, RewriteCond, script, simultaneous connections, work
Posted in Computer Security, Linux, System Administration | No Comments »
Sunday, February 26th, 2012 In my last article, I've explained How to create PNG, JPG, GIF pictures from one single PDF document
Convertion of PDF to images is useful, however as PNG and JPEG graphic formats are raster graphics the image quality gets crappy if the picture is zoomed to lets say 300%.
This means convertion to PNG / GIF etc. is not a good practice especially if image quality is targetted.
I myself am not a quality freak but it was interesting to find out if it is possible to convert the PDF pages to SVG (Scalable Vector Graphics) graphics format.
Converting PDF to SVG is very easy as for GNU / Linux there is a command line tool called pdf2svg
pdf2svg's official page is here
The traditional source way compile and install is described on the homepage. For Debian users pdf2svg has already existing a deb package.
To install pdf2svg on Debian use:
debian:~# apt-get install --yes pdf2svg
...
Once installed usage of pdf2svg to convert PDF to multiple SVG files is analogous to imagemagick's convert .
To convert the 44 pages Projects.pdf to multiple SVG pages – (each PDF page to a separate SVG file) issue:
debian:~/project-pdf-to-images$ for i in $(seq 1 44); do \
pdf2svg Projects.pdf Projects-$i.SVG $i; \
done
This little loop tells each page number from the 44 PDF document to be stored in separate SVG vector graphics file:
debian:~/project-pdf-to-images$ ls -1 *.svg|wc -l
44
For BSD users and in particular FreeBSD ones png2svg has a bsd port in:
/usr/ports/graphics/pdf2svg
Installing on BSD is possible directly via the port and convertion of PDF to SVG on FreeBSD, should be working in the same manner. The only requirement is that bash shell is used for the above little bash loop, as by default FreeBSD runs the csh.
On FreeBSD launch /usr/local/bin/bash, before following the Linux instructions if you're not already in bash.
Now the output SVG files are perfect for editting with Inkscape or Scribus and the picture quality is way superior to old rasterized (JPEG, PNG) images
Tags: Auto, bash shell, bsd users, command line tool, Convert, Converting, convertion, crappy, deb, deb package, debian project, debian users, document, documentConvertion, Draft, editting, format, freak, GIF, gnu linux, graphic formats, Graphics, graphics format, graphics graphics, homepage, Image, image quality, ImageMagick, inkscape, issue, JPG, jpg gif, line, Linux, nbsp, number, package, page, pdf document, picture, png, png images, Projects, raster graphics, rasterized, Scalable, scalable vector graphics, Scribus, Shell, svg file, svg files, tool, traditional source, use, vector, way
Posted in Linux, Linux and FreeBSD Desktop, System Administration | No Comments »
Saturday, January 28th, 2012 I've earlier blogged on playing Apogee's Raptor Shadows of Death arcade on GNU / Linux with dosbox
All the old school raptor addicts will be interested to hear Kazzmir (Jon Rafkind) a free software devotee developer has created a small game resembling many aspects of the original Raptor arcade game.
The game is called Rafkill and is aimed to be a sort of Raptor like fork/clone.
Originally the game was also named Raptor like the DOS game, however in year 2006 it was changed to current Rafkill in order to avoid legal issues with Apogee's Raptor.
The game is not anymore in active development, the latest Rafkill release is from January 2007, anyhow even for the 2012 it is pretty entertaining. The sound and music are on a good level for a Linux / BSD shoot'em'up free software game . The graphics are not of a top quality and are too childish, but this is normal, since the game is just one man masterpiece.

Rafkill is developed in C/C++ programming language, the game music engine it uses is called DUMB (Dynamic Universal Bibliotheque). By the way DUMB library is used for music engine in many Linux arcade games. DUMB allows the Linux game developer to develop his game and play a music files within different game levels in "tracked" formats like mod, s3m, xm etc.
The game is available in compiled form for almost all existent GNU/Linux distributions, as well as one can easily port it as it is open source.
To install Rafkill on Debian, Ubuntu, Xubuntu and Linux Mint en other Debian based distros
root@debian:~# apt-get install rafkill
Installing on Fedora and other rpm based is with yum
debian:~# apt-get install rafkill
...
Once rafkill is installed, in order to start it on Debian the only way is using the rafkill (/usr/bin/rafkill) command. It appears the deb package maintainer did not wrote a gnome launcher file like for example /usr/share/applications/rafkill.desktop
Just to explain for all the GNOME noobs, the .desktop files are a description file GNOME reads in order to understand where exactly to place certain application in the (Gnome Applications, Places, System …) menu panel.
Even though it miss the .desktop, it is launchable via Applications menu under the Debian section e.g. to open it from the GNOME menus you will have to navigate to:
Applications -> Debian -> Games -> Action -> Rafkill
This "shortcut" to launch the game is quite long and hard to remember thus it is handy to directly launch it via xterm:
hipo@debian:~$ rafkill
or by pressing ALT+F2 and typing rafkill :

Starting the game I got some really ugly choppy music / sound issues.
My guess was the fizzling sounds were caused by some bug with the sound portions streamed through pulseaudio sound system.
To test if my presume is correct, stopped pulseaudio and launched rafkill once again:
hipo@debian:~$ pulseaudio -k
hipo@debian:~$ rafkill
This way the game was counting on ALSA to process sound en the sound was playing perfectly fine.
I solved this problem through small wrapper shell script. The script did kill pulseaudio before launching rafkill and that way solve gchoppy sound issues, once the game execution is over the script starts pulseaudio again in order to prevent all other applications working with pulseaudio.
Finally, I've placed the executable script in /usr/bin/rafkill :
Here is the script:
#!/bin/bash
pulseaudio --kill
/usr/games/rafkill
pulseaudio --start
You can download rafkill.wrapper.sh here
Or write in root terminal:
debian:~# cd /usr/bin
debian:/usr/bin:# wget https://www.pc-freak.net/bshscr/rafkill.wrapper.sh
debian:/usr/bin:# mv https://www.pc-freak.net/bshscr/rafkill.wrapper.sh rafkill
debian:/usr/bin:# chmod +x rafkill
Interesting in Ubuntu Linux, rafkill music is okay and I suppose the bug is also solved in newer Linux distributions based on Ubuntu. Probably the Debian Squeeze pulseaudio (0.9.21-4) package version has a bug or smth..
After the change the game music will be playing fine and the game experience is cooler. The game is hard to play. Its really nice the game has game Saves, so once you die you don't have to start from level 1.
I've seen rafkill rolling around on freebsd.org ftps under the ubuntu packages pool, which means rafkill could probably be played easily on FreeBSD and other BSDs.
Enjoy the cool game 😉
Tags: active development, arcade game, arcade games, Auto, BSD, c c programming language, c programming language, clone, deb package, Desktop, desktop files, different game, dos game, Draft, Engine, file, form, Free, game developer, game levels, game music, Gnome, hipo, level, Linux, linux distributions, linux game, menu, mod, music engine, Open, open source clone, package, package maintainer, pulseaudio, quot, script, shadows of death, share applications, small game, software, software game, software open source, Ubuntu, Universal, wrapper, year
Posted in Games Linux, Linux, Linux and FreeBSD Desktop | 1 Comment »
Thursday, December 8th, 2011 The usual way that one is supposed to check a certain partition let’s say /dev/sda1 disk UUID (Universal Unique Identifier) label is through a command:
vol_id /dev/sda1
For reason however Debian does not include vol_id command. To check the UUID assigned disk labels on Debian one should use another command called blkid (part of util-linux deb package).
blkid will list all block device attributes so it doesn’t specifically, passing any partition as argument.
Here is an example output of blkid :
server:/root# blkid
/dev/sda1: UUID="cdb1836e-b7a2-4cc7-b666-8d2aa31b2da4" SEC_TYPE="ext2" TYPE="ext3"
/dev/sda5: UUID="c67d6d43-a48f-43ff-9d65-7c707a57dfe6" TYPE="swap"
/dev/sdb1: UUID="e324ec28-cf04-4e2e-8953-b6a8e6482425" TYPE="ext2"
/dev/sdb5: UUID="1DWe0F-Of9d-Sl1J-8pXW-PLpy-Wf9s-SsyZfQ" TYPE="LVM2_member"
/dev/mapper/computer-root: UUID="fbdfc19e-6ec8-4000-af8a-cde62926e395" TYPE="ext3"
/dev/mapper/computer-swap_1: UUID="e69100ab-9ef4-45df-a6aa-886a981e5f26" TYPE="swap"
/dev/mapper/computer-home: UUID="2fe446da-242d-4cca-8b2c-d23c76fa27ec" TYPE="ext3"
Tags: cca, command, computer swap, deb, deb package, debian gnu, dev, Disk, disk labels, doesn, DWe, ext, ff, gnu linux, Linux, linux deb, LVM, mapper, package, partition, partition disk, quot dev, reason, root, sda, sdb, sec type, server root, Unique, UUID, vol, way
Posted in Linux, System Administration, Various | No Comments »
Saturday, December 3rd, 2011 
I’m currently reading Free as in Freedom (2.0) R. Stallman and the Free Software Revolution
The book includes a reference to Eric S. Raymond ‘s famous The Cathedral and the Bazaar which does makes a point about the important of Open Source . I’ve read the The Cathedral and the Bazaar paper some very long time ago (in my young days so to say) and hence I couldn’t resemble much of the document so I jumped in after the footnote in the FAIF book and decided to take a quick look on The Cathedral and the Bazaar once again to bring up some memories. I was stunned to find the paper is available in many formats but officially not included in PDF . Since i’m a GNU / Linux user I’ve never managed to get into the habit to read postscript documents which from modern day stand point are also already a bit of obsolete and therefore I found it as a wise idea to convert and mirror the POSTSCRIPT (PS) version of the document to PDF on www.pc-freak.net
Happily the ps2pdf command to convert the ps to pdf on my debian gnu / linux is really easy:
ps2pdf cathedral-and-the-bazaar-Eric_Raymond.ps Cathedral-and-the-bazaar-Eric_Raymond.pdf
ps2pdf is part of the ghostscript deb package, so if you can’t find the program you will need to have it installed with apt-get first.
By the way the Postscript file is easily readable using my default gnome PDF reader evince , but anyways I converted and mirrored the paper for all those windows users who might like to take a look at the document in PDF.
I’ve also made a mirror of the original Cathedral and the Bazaaar postscript document here , for all those who want to check out The PDF version of the Cathedral and the Bazaaar is for download here
Even though the “open source” movement is an interesting idea and it had some major impact on the development of some free software the idiology of open source which was very much influenced by this document is very weak compared to the philosophy Richard Stallman indcuded as of the great need of the software to be free.
To be honest looking back in time for a long time being a Linux user I did not make any distinguishment between “Free Software” concept and “Open Source”, even worser I considered to evangelize on Open Source not realizing that initially what attracted me to free software was the idiology of open source and not the real values on which ground free software is built.
This kind of miss understanding between perception of “open source” and “free software” I got and spread for years now I fully realize and I seem like when I red back then The Cathedral and the Bazaar document I didn’t looked any critical at the document but it had a major, I would say “bad” impact on my idiology on software for a long time. So for all those who had not checked it it’s worthy checking but only in case if one fully understands Richard Stallman’s concept of Free Software, without this understanding one can easily slip into the wrong believe (just like me back in thme) that open source is the same as free software. Even though open source can be free software it is not presumably that an open source is free software and that it guarantees that the published source will be free. But I’ll stop now as I slept away from my goal of the article to just log here how a convertion of postscript to pdf on gnu / linux is done.
Just to close up this article I warmly recommend on all people interested into hacking and the history of Free operating systems and Free software as FreeBSD and GNU / Linux the Free as in Freedom (2.0) book ! Its truly a remarkable and great inspirational reading for all people like me involved into free software realm of ICT.
Tags: bazaar, bit, Cathedral, Cathedral-and-the-bazaar, deb package, debian gnu, download, eric s raymond, evangelize, evince, file, Free, free as in freedom, free software revolution, freedom 2, ghostscript, GNU, gnu linux, impact, Linux, linux user, movement, need, Open, open source movement, package, philosophy, Postscript, postscript document, postscript documents, postscript files, postscript ps, ps version, ps2pdf, quot, reading, software, Source, stallman, time, windows users, wise idea
Posted in Everyday Life, FreeBSD, Linux, Various | 1 Comment »
Tuesday, August 30th, 2011 
Recently has become publicly known for the serious hole found in all Apache webserver versions 1.3.x and 2.0.x and 2.2.x. The info is to be found inside the security CVE-2011-3192 – https://issues.apache.org/bugzilla/show_bug.cgi?id=51714
Apache remote denial of service is already publicly cirtuculating, since about a week and is probably to be used even more heavily in the 3 months to come. The exploit can be obtained from exploit-db.com a mirror copy of #Apache httpd Remote Denial of Service (memory exhaustion) is for download here
The DoS script is known in the wild under the name killapache.pl
killapache.pl PoC depends on perl ForkManager and thus in order to be properly run on FreeBSD, its necessery to install p5-Parallel-ForkManager bsd port :
freebsd# cd /usr/ports/devel/p5-Parallel-ForkManager
freebsd# make install && make install clean
...
Here is an example of the exploit running against an Apache webserver host.
freebsd# perl httpd_dos.pl www.targethost.com 50
host seems vuln
ATTACKING www.targethost.com [using 50 forks]
:pPpPpppPpPPppPpppPp
ATTACKING www.targethost.com [using 50 forks]
:pPpPpppPpPPppPpppPp
...
In about 30 seconds to 1 minute time the DoS attack with only 50 simultaneous connections is capable of overloading any vulnerable Apache server.
It causes the webserver to consume all the machine memory and memory swap and consequently makes the server to crash in most cases.
During the Denial of Service attack is in action access the websites hosted on the webserver becomes either hell slow or completely absent.
The DoS attack is quite a shock as it is based on an Apache range problem which started in year 2007.
Today, Debian has issued a new versions of Apache deb package for Debian 5 Lenny and Debian 6, the new packages are said to have fixed the issue.
I assume that Ubuntu and most of the rest Debian distrubtions will have the apache’s range header DoS patched versions either today or in the coming few days.
Therefore work around the issue on debian based servers can easily be done with the usual apt-get update && apt-get upgrade
On other Linux systems as well as FreeBSD there are work arounds pointed out, which can be implemented to close temporary the Apache DoS hole.
1. Limiting large number of range requests
The first suggested solution is to limit the lenght of range header requests Apache can serve. To implement this work raround its necessery to put at the end of httpd.conf config:
# Drop the Range header when more than 5 ranges.
# CVE-2011-3192
SetEnvIf Range (?:,.*?){5,5} bad-range=1
RequestHeader unset Range env=bad-range
# We always drop Request-Range; as this is a legacy
# dating back to MSIE3 and Netscape 2 and 3.
RequestHeader unset Request-Range
# optional logging.
CustomLog logs/range-CVE-2011-3192.log common env=bad-range
CustomLog logs/range-CVE-2011-3192.log common env=bad-req-range
2. Reject Range requests for more than 5 ranges in Range: header
Once again to implement this work around paste in Apache config file:
This DoS solution is not recommended (in my view), as it uses mod_rewrite to implement th efix and might be additionally another open window for DoS attack as mod_rewrite is generally CPU consuming.
# Reject request when more than 5 ranges in the Range: header.
# CVE-2011-3192
#
RewriteEngine on
RewriteCond %{HTTP:range} !(bytes=[^,]+(,[^,]+){0,4}$|^$)
# RewriteCond %{HTTP:request-range} !(bytes=[^,]+(?:,[^,]+){0,4}$|^$)
RewriteRule .* - [F]
# We always drop Request-Range; as this is a legacy
# dating back to MSIE3 and Netscape 2 and 3.
RequestHeader unset Request-Range
3. Limit the size of Range request fields to few hundreds
To do so put in httpd.conf:
LimitRequestFieldSize 200
4. Dis-allow completely Range headers: via mod_headers Apache module
In httpd.conf put:
RequestHeader unset Range
RequestHeader unset Request-Range
This work around could create problems on some websites, which are made in a way that the Request-Range is used.
5. Deploy a tiny Apache module to count the number of Range Requests and drop connections in case of high number of Range: requests
This solution in my view is the best one, I’ve tested it and I can confirm on FreeBSD works like a charm.
To secure FreeBSD host Apache, against the Range Request: DoS using mod_rangecnt, one can literally follow the methodology explained in mod_rangecnt.c header:
freebsd# wget http://people.apache.org/~dirkx/mod_rangecnt.c
..
# compile the mod_rangecnt module
freebsd# /usr/local/sbin/apxs -c mod_rangecnt.c
...
# install mod_rangecnt module to Apache
freebsd# /usr/local/sbin/apxs -i -a mod_rangecnt.la
...
Finally to load the newly installed mod_rangecnt, Apache restart is required:
freebsd# /usr/local/etc/rc.d/apache2 restart
...
I’ve tested the module on i386 FreeBSD install, so I can’t confirm this steps works fine on 64 bit FreeBSD install, I would be glad if I can hear from someone if mod_rangecnt is properly compiled and installed fine also on 6 bit BSD arch.
Deploying the mod_rangecnt.c Range: Header to prevent against the Apache DoS on 64 bit x86_amd64 CentOS 5.6 Final is also done without any pitfalls.
[root@centos ~]# uname -a;
Linux centos 2.6.18-194.11.3.el5 #1 SMP Mon Aug 30 16:19:16 EDT 2010 x86_64 x86_64 x86_64 GNU/Linux
[root@centos ~]# /usr/sbin/apxs -c mod_rangecnt.c
...
/usr/lib64/apr-1/build/libtool --silent --mode=link gcc -o mod_rangecnt.la -rpath /usr/lib64/httpd/modules -module -avoid-version mod_rangecnt.lo
[root@centos ~]# /usr/sbin/apxs -i -a mod_rangecnt.la
...
Libraries have been installed in:
/usr/lib64/httpd/modules
...
[root@centos ~]# /etc/init.d/httpd configtest
Syntax OK
[root@centos ~]# /etc/init.d/httpd restart
Stopping httpd: [ OK ]
Starting httpd: [ OK ]
After applying the mod_rangecnt patch if all is fine the memory exhaustion perl DoS script‘s output should be like so:
freebsd# perl httpd_dos.pl www.patched-apache-host.com 50
Host does not seem vulnerable
All of the above pointed work-arounds are only a temporary solution to these Grave Apache DoS byterange vulnerability , a few days after the original vulnerability emerged and some of the up-pointed work arounds were pointed. There was information, that still, there are ways that the vulnerability can be exploited.
Hopefully in the coming few weeks Apache dev team should be ready with rock solid work around to the severe problem.
In 2 years duration these is the second serious Apache Denial of Service vulnerability after before a one and a half year the so called Slowloris Denial of Service attack was capable to DoS most of the Apache installations on the Net.
Slowloris, has never received the publicity of the Range Header DoS as it was not that critical as the mod_range, however this is a good indicator that the code quality of Apache is slowly decreasing and might need a serious security evaluation.
Tags: apache httpd, apache server, apache webserver, ATTACKING, Auto, bugzilla, com, config, copy, CustomLog, deb package, denial of service, denial of service attack, dos attack, dos script, dos vulnerability, download, Draft, exploit, freebsd, header, host, HTTP, info, machine memory, memory exhaustion, minute time, mirror copy, mod, necessery, Netscape, number, perl httpd, poc, pPpPpppPpPPppPpppPp, REJECT, Remote, RewriteCond, script, simultaneous connections, work
Posted in Computer Security, FreeBSD, Linux, System Administration, Web and CMS | No Comments »
Wednesday, August 24th, 2011 While I was deploying a new Nagios install to Monitor some Windows hosts I’ve came across the following error in Nagios’s web interface:
Sorry, but Nagios is currently not checking for external commands, so your command will not be committed!
Read the documentation for information on how to enable external commands...
This error is caused by an option configuration for /etc/nagios/nrpe.cfg (part of the nrpe-nagios-server Debian package.
The config variable in nrpe.cfg causing the error is check_external_command=0 , the fix comes to changing the variable to:
check_external_command=1
As well as restart the /etc/init.d/nagios-nrpe-server and /etc/init.d/nagios3 services:
debian:~# /etc/init.d/nagios3 restart
...
debian:~# /etc/init.d/nagios-nrpe-server
...
This changes has work out the error Sorry, but Nagios is currently not checking for external commands, so your command will not be committed! , however immediately after another kind of error appared in Nagios web interface when I tried to use the send Nagios commands button. The error was:
Error: Could not stat() command file '/var/lib/nagios3/rw/nagios.cmd'!
This error is due to a deb package, which seems to be affecting the current deb versions of Nagios shipped with Debian 6 Squeeze stable, as well as the Latest Ubuntu release 11.04.
Thanksfully there is a work around to the problem I found online, to fix it up I had to execute the commands:
debian:~# /etc/init.d/nagios3 stop debian:~# dpkg-statoverride --update --add nagios www-data 2710 /var/lib/nagios3/rw
debian:~# dpkg-statoverride --update --add nagios nagios 751 /var/lib/nagios3
debian:~# /etc/init.d/nagios3 start
And hooray Thanks God the error is gone 😉
Tags: Button, check, checking, command, config, deb, deb package, dpkg, ERROR, file, god, hooray, information, kind, lib, monitor, nagios, online, option, package, squeeze, Stable, stat, Thanksfully, Ubuntu, var, web interface, work, www data
Posted in Linux, System Administration | 8 Comments »














