In the office, some of my colleagues has started receiving error messages, while trying to send mail with Thunderbird and Outlook Express
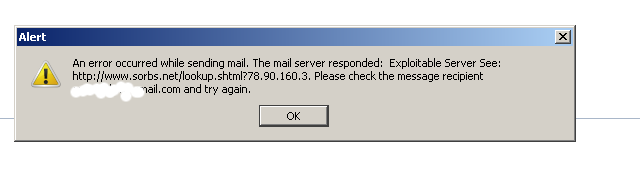
The exact error they handed to me reads like this:
An error occured while sending mail. The mail server responded: Exploitable Server See:
http://www.sorbs.net/lookup?xx.xx.xx.xx. Please check the message recipient
Here is also a screenshot, I’ve been sent via Skype with the error poping up on a Thunderbird installed on Windows host.
Typing the url http://www.sorbs.net/lookup?xx.xx.xx.xx lead me to sorbs.net to a page saying that the IP address of the mail client which is trying to send mail is blacklisted . This is not strange at all condireng that many of the office computers are running Windows and periodically get infected with Viruses and Spyware which does sent a number of Unsolicated Mail (SPAM).
The sorbs.net record for the IP seems to be an old one, since at the present time the office network was reported to be clear from malicious SMTP traffic.
The error sorbs.net disallowing the mail clients to send from the office continued for already 3 days, so something had to be done.
We asked the ISP to change the blacklisted IP address of xx.xx.xx.xx , to another one but they said it will take some time and they can’t do it in a good timely matter, hence to make mail sending work again with POP3 and IMAP protocols from the blacklisted IPs I had to set in the Qmail install to not check the xx.xx.xx.xx IP against mail blacklisting databases.
On qmail install disabling an IP check in RBLSMTPD is done through editting /etc/tcp.smtp and following recreate of /etc/tcp.smtp.cdb – red by qmailctl script start.
The exact line I put in the end of /etc/tcp.smtp to disable the RBLSMTPD check is:
xx.xx.xx.xx:allow,RBLSMTPD="",RELAYCLIENT="",QS_SPAMASSASSIN="0"
Further on to recreate /etc/tcp.smtp.cdb and reload the new cdb db records:
qmail:~# qmailctl cdb
qmail:~# qmailctl restart
...
Onwards, the sorbs.net IP blacklist issue was solved and all office computers from xx.xx.xx.xx succeeded in sending mails via SMTP.