August 2010 Archives
Tue Aug 31 19:59:54 EEST 2010
Periodically relax your eyes to reduce computer generated strain and help up your nerves
While I was looking for information
about how to relax when you spend a lot of time in front of pc
screen I came across two interesting article, that might concern
your interest. Link to the article named
Rlex your eye quickly but soothing way during a busy time can
be red here
In the article you will find few eyes relaxing exercises which are said to improve the overall experience infront of pc screen as well as calm down the computer generated stress by some nice eyes massages.
Some more precious info on the results in daily life caused by life strain like for instance headaches, increase in stress for the visual nervous system, overall body fatigue are to be found here and is under the name Compuster Eye Strain: How to relieve it with free eye exercises, nutrition and lifestyle.
This two ones are a really interesting articles, so big thanks to the post authors !
In the article you will find few eyes relaxing exercises which are said to improve the overall experience infront of pc screen as well as calm down the computer generated stress by some nice eyes massages.
Some more precious info on the results in daily life caused by life strain like for instance headaches, increase in stress for the visual nervous system, overall body fatigue are to be found here and is under the name Compuster Eye Strain: How to relieve it with free eye exercises, nutrition and lifestyle.
This two ones are a really interesting articles, so big thanks to the post authors !
Mon Aug 30 14:49:56 EEST 2010
Cults to Saint Elijah in Heterodox Islam and their relation to Hebrew faith and Christianity
Christians and Jews, are quite aware
of the glorious earthly living of
Saint Elijah also known under the name (Elias).
In the Hebrew Bible (Old Testament) as a basis of our Christian scriptures as well as in our Christian faith, St. Elijah is one of the most honored saints lived on earth grounded in the same saints line the new testamental Saint John the Baptist and the old times God holy man Enoch
Both of the saints Elihjah and Enoch are known to be the only God prophets who were taken to heaven alive. The two saints are well known to be referred in Both the Old Testament and The New Testament in the Holy Bible.
An interesting not well known fact about the name Elijah is the name meaning literally translated from Hebrew the name means "My God is Yahweh" or Jehovah as we know one of God's names referred within the Holy Bible.
In the Qu'ran as a later book compared to Old Testament (Hebrew Bible) and The Holy Bible we Christians have.
It appears there are two references in the Holy Quran referring to the Old Testament Holy man Elias this are the verses number "37:123–132" and "6:85"
The two verses as directly translated from Arabic to English says the following:
Qur'an 37:123–132
Qur'an 6:85
As we see in the Qu'ran Eliajah is considered a high estate prophet in a similar fashion as we honour him as a great Saint in Christianity.
We see the quick reference to the Holy Bible chapter 1st and 2nd Kings , however the verses doesn't gave us a good account on who Elijah was.
As many muslims consider the Old Testament from the Holy Bible as one of their Holy Books along with some muslims considering the New Testament though under a very wild Islamic interpretation, St. Elijah has a reference in Islamic seems to appear in Islamic faith under a lot of "hoods".
Therefore Islamic interpretation on the Prophet living and deeds are varying quite wildly.
There are plenty of places in Turkey as well as in the Arabic World and even the Balkans that are said as a sacral places where it's beeing said the prophet has abode or has done a numeous miracles like for instance under his will some miraculously healing water has emerged and all kind of mystic stuff alike.
This kind of legends being spread along muslims are quite known and mostly derive from (heterodox) muslim (Sufi's - see Sufism for a refence) tradition.
Most of the Holy places indicated by the Islamic Heterodox beliefs as a place where the saint is said to have either appeared, did miracles, lived or appeared are the so called (Tekkes) see my post referring about my going to one of the Tekkes here in Bulgaria in Obrotishte
It's an interesting fact that the Islamic understanding of the Prophet and the thousand places around the world that are said the prophet has appeared at most cases used to be a holy places for local Christians or used to contain a Church, a chapel, or some hermit saint that used to inhabit the place during his earhly life time.
This kind of Christian gathering places were often places with a name under our Christian Orthodox Saint - St. Nicholas
It's rather strange that the islamic Sufi cults somehow mistakenly identified St. Nicholas (the wondermaker) with St. Elijah, therefore from a Christian Monasteries or a Church (ecclesias) at a certain time of Christian desolation on that places the past Christian Holy places has slowly become a places to be honoured by the muslims.
Often from a Prophet islamic saint Elijah has been known to be a BABA (most probably this word derives it's meaning from the Christian ABBAs [ Fathers ] which are considered the first Christian hermits and saints who lived in the time interval of 1st to 5th or 6th century after A.D.
Therefore in a similar manner that we Christians ask the saints to have a prayer intercession to our saints, muslims go to venerate the BABA Prophet Elijah and believe whatever they ask him he will do for them.
Even in this days it's a common thing here in Bulgaria that the veneration to the Elijah BABA turns to be a festival, where people gather to a spring that is believed to be miraculous or to a local Tekke and start looking Prophet Elijah's protection or blessing.
The things with Islam especially with a Heterodox one (which means non main stream) Islam are quite entangled, therein myths and legends from various faiths has been implicated in a real odd manner and a various cult believes has emerged.
Since many of Islam practicing people this days are not quite religion literate they tend to believe everything they hear, same thing is also quite true for other faiths like Christian.
In Turkey situation is a bit better since all the Tekkes (Khanqh) in Turkey were prohibited from the first Turkish president Mustafa Kemal Ataturk
However in many other places where muslim population is present like in the balkanies things are quite chaotic, many Tekkes still exist until very day.
Almost each one of the Khanqah's is belied to have a burried body of a BABA or a saint most commonly, saying that it's St. Elijah's body buried there.
Thus believing muslims often go to this sacral places which used to be in between the 16th to the 18th century a sacral places for Sufists.
Sufists used the Tekkes to have their religious believes and ritual practices.
For more about Sufism check out here
There is plenty much I can say about the cults that emerged in almost inexplainable way to Elijah the Tekkes sufism and the Heterodox Islam inverted faith beliefs, however I think I've said the most essential.
If somebody has a special interest on the topic I guess he can read plenty of information online and get a good idea of the many cults to the Prophet Elijah and the other baba's (Saints) thought to be Allah's servants in Islam.
This kind of topic was really interesting one since it gives us a better glimpse on religion and modern religion cults. Hope it was an interesting one for you as well.
In the Hebrew Bible (Old Testament) as a basis of our Christian scriptures as well as in our Christian faith, St. Elijah is one of the most honored saints lived on earth grounded in the same saints line the new testamental Saint John the Baptist and the old times God holy man Enoch
Both of the saints Elihjah and Enoch are known to be the only God prophets who were taken to heaven alive. The two saints are well known to be referred in Both the Old Testament and The New Testament in the Holy Bible.
An interesting not well known fact about the name Elijah is the name meaning literally translated from Hebrew the name means "My God is Yahweh" or Jehovah as we know one of God's names referred within the Holy Bible.
In the Qu'ran as a later book compared to Old Testament (Hebrew Bible) and The Holy Bible we Christians have.
It appears there are two references in the Holy Quran referring to the Old Testament Holy man Elias this are the verses number "37:123–132" and "6:85"
The two verses as directly translated from Arabic to English says the following:
Qur'an 37:123–132
Elijah too was one of the Envoys;
When he said to his people, 'Will you not be Godfearing?
Do you call on Baal, and abandon the Best of creators?
God, your Lord, and the Lord of your fathers, the ancients?'
But they cried him lies;
so they will be among the arraigned, except for God's sincere
servants.
And We left for him among the later folk.
'Peace be upon Elijah!'
Even so we recompense the good-doers;
he was among Our believing servants.
Qur'an 6:85
And Zechariah and John and Jesus and Elijah, all in the ranks
of the righteous.
As we see in the Qu'ran Eliajah is considered a high estate prophet in a similar fashion as we honour him as a great Saint in Christianity.
We see the quick reference to the Holy Bible chapter 1st and 2nd Kings , however the verses doesn't gave us a good account on who Elijah was.
As many muslims consider the Old Testament from the Holy Bible as one of their Holy Books along with some muslims considering the New Testament though under a very wild Islamic interpretation, St. Elijah has a reference in Islamic seems to appear in Islamic faith under a lot of "hoods".
Therefore Islamic interpretation on the Prophet living and deeds are varying quite wildly.
There are plenty of places in Turkey as well as in the Arabic World and even the Balkans that are said as a sacral places where it's beeing said the prophet has abode or has done a numeous miracles like for instance under his will some miraculously healing water has emerged and all kind of mystic stuff alike.
This kind of legends being spread along muslims are quite known and mostly derive from (heterodox) muslim (Sufi's - see Sufism for a refence) tradition.
Most of the Holy places indicated by the Islamic Heterodox beliefs as a place where the saint is said to have either appeared, did miracles, lived or appeared are the so called (Tekkes) see my post referring about my going to one of the Tekkes here in Bulgaria in Obrotishte
It's an interesting fact that the Islamic understanding of the Prophet and the thousand places around the world that are said the prophet has appeared at most cases used to be a holy places for local Christians or used to contain a Church, a chapel, or some hermit saint that used to inhabit the place during his earhly life time.
This kind of Christian gathering places were often places with a name under our Christian Orthodox Saint - St. Nicholas
It's rather strange that the islamic Sufi cults somehow mistakenly identified St. Nicholas (the wondermaker) with St. Elijah, therefore from a Christian Monasteries or a Church (ecclesias) at a certain time of Christian desolation on that places the past Christian Holy places has slowly become a places to be honoured by the muslims.
Often from a Prophet islamic saint Elijah has been known to be a BABA (most probably this word derives it's meaning from the Christian ABBAs [ Fathers ] which are considered the first Christian hermits and saints who lived in the time interval of 1st to 5th or 6th century after A.D.
Therefore in a similar manner that we Christians ask the saints to have a prayer intercession to our saints, muslims go to venerate the BABA Prophet Elijah and believe whatever they ask him he will do for them.
Even in this days it's a common thing here in Bulgaria that the veneration to the Elijah BABA turns to be a festival, where people gather to a spring that is believed to be miraculous or to a local Tekke and start looking Prophet Elijah's protection or blessing.
The things with Islam especially with a Heterodox one (which means non main stream) Islam are quite entangled, therein myths and legends from various faiths has been implicated in a real odd manner and a various cult believes has emerged.
Since many of Islam practicing people this days are not quite religion literate they tend to believe everything they hear, same thing is also quite true for other faiths like Christian.
In Turkey situation is a bit better since all the Tekkes (Khanqh) in Turkey were prohibited from the first Turkish president Mustafa Kemal Ataturk
However in many other places where muslim population is present like in the balkanies things are quite chaotic, many Tekkes still exist until very day.
Almost each one of the Khanqah's is belied to have a burried body of a BABA or a saint most commonly, saying that it's St. Elijah's body buried there.
Thus believing muslims often go to this sacral places which used to be in between the 16th to the 18th century a sacral places for Sufists.
Sufists used the Tekkes to have their religious believes and ritual practices.
For more about Sufism check out here
There is plenty much I can say about the cults that emerged in almost inexplainable way to Elijah the Tekkes sufism and the Heterodox Islam inverted faith beliefs, however I think I've said the most essential.
If somebody has a special interest on the topic I guess he can read plenty of information online and get a good idea of the many cults to the Prophet Elijah and the other baba's (Saints) thought to be Allah's servants in Islam.
This kind of topic was really interesting one since it gives us a better glimpse on religion and modern religion cults. Hope it was an interesting one for you as well.
Sat Aug 28 16:55:45 EEST 2010
Torus Trooper, Tumiki Fighters and Starfighter one of the best Arcade native Linux games made ever
I'm not a big gamer this days,
however every now and then I do like playing some fast pace arcade
game to cheer up.
The arcade games for Linux are really lot, however most of them are too boring and has a notable bad graphic design or a game play, here is why I decided to blog about two really worthy games to be noted and placed among best arcade games produced so far.
Below you will find a quick game review of the arcade game Linux trio Torus Trooper, Tumiki Fighters and Starfighter
1.Let me begin with Torus Trooper
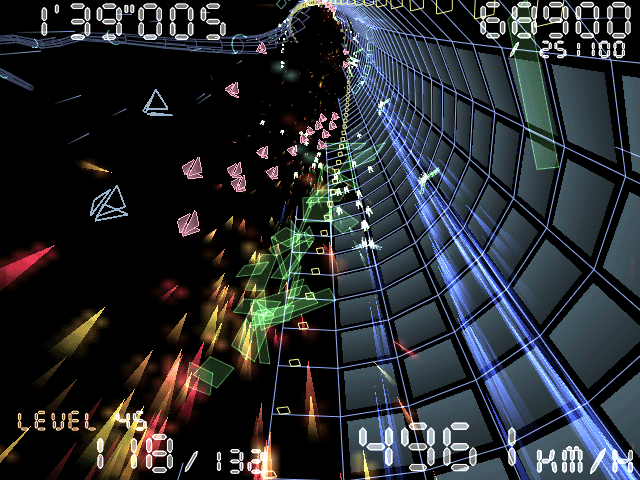
Torus trooper is an awesome fast pace japanese game a bit in the tradition of the good old Star Wars racer the graphics of course as with most Linux games are not that awesome as with Star Wars racer, however the game is a really nice one 3D tunnel shooter, especially if you'd like to play half an hour to relax from a heavy strained day. In the game you have a spaceship and you have to navigate through a rotating tunnels and kill the enemy's spaceship, there is quite a lot of action involved and this makes the game really wonderful to lift up your adrenaline :)
While navigating though the tunnels and killing enemies you can switch up and down your spaceship acceleration,
you have a limited time for which you have to complete each of the game levels, whether killing a series of enemies
would win you some bonus seconds usually if you get a bonus time an extra +15 seconds is added to your time limit you're supposed to complete the level.
On certain scores also can grant you extra time bonus of (+15) seconds. If you get killed then a (-15 seconds) are deducted from your level completion time limit.
As every arcade in the game each level has a boss (a base) you have to destroy dependantly the time interval in which you succeed in destroying the end level boss would add up either (+30) or (+45) seconds to your overall game time limit.
The enemy will show up after you kill a previously game defined number of enemy's spaceship, the remaining enemy's spaceship to be destroyed is (displayed at the right up corner) of the game.
Below I present you with the screenshot taken from Torus Trooper 's official website and hopefully it will give you a brief idea what to expect if you desire to give the game a go on your GNU/Linux.
The game installation on Debian is pretty straight forward is available as a debian package to install just copy paste in your root terminal the:
Now all left is to start up the game in full-screen mode by typing as a non-privileged user:
What annoyed me a bit was the fact that I couldn't find a fullscreen option in after starting up the game without the -fullscreen option. But heh, let us not forget we are on Linux, things to be a bit commandish :)
Hopefully in future releases of the game (if there are such), the fullscreen will be added as a possible option to be selected from within the game itself.
Another very notable thing about the Torus Trooper game is the addicting music and game play I belive is the real charm of arcade games.
2. TUMIKI Fighters
Is another great japanese arcade game, it's an interesting fact that both TUMIKI Fighters and Torus Trooper are created by a single Japanese man Kenta Cho
Mr. Kenta Cho has done quite a good job especially if we consider the fact that he is the only one that has developed this two wonderful games.
TUMIKI Fighters's also very dynamic, however it's more a 2D like arcade, each of the ships within the game are actually a toy like (Lego like).
What I find unique about TUMIKI Fighters as a game is the fact that whenever you kill an enemy toy ship you're able to assimilate the destoying ship before your eyes.
As described in TUMIKI Fighters official game web site ,
"Stick more enemies and become much stronger."
In other words the more ships you are able to gain to your basis ship the stronger your ship becomes.
Below I present you with a screenshot to get an idea what to expect if you consider installing and playing the game.
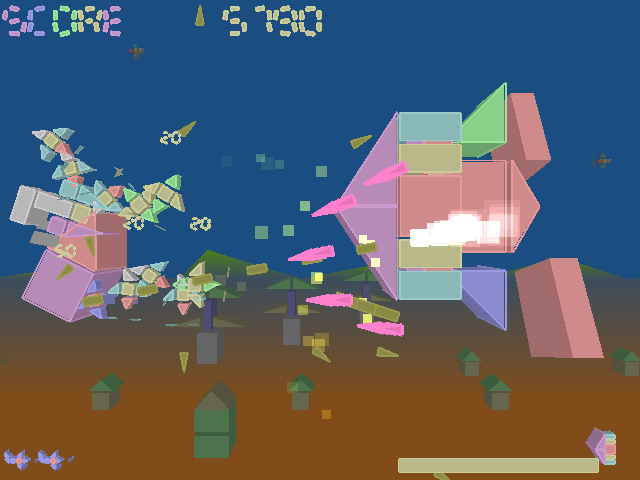
The screenshot is a bit messed and the game looks a way better in reality so I urge you to take few seconds to install and try it.
If you're on Debian just issue command:
To start up the game in fullscreen in a similar fashion to Torus Trooper you will have to pass the -fullscreen command option next to the main game binary.
So:
Will start the game in fullscreen.
3. Finally I'll tell you a few words about Project Starfighter
Project Starfighter is I a class above both Tumiki Fighters and Torus Trooper this is most probably because it was developed by a developers group called Parallel Realities
If you're a Linux game developer, it's very likely that checking their website will provide you with a number of precious articles on Game development e.g. making many of the developed Parallel Realities developed games as well as game source code.
Parallel Realities has so far developed a lot of games, they've done a great job that each of the games has Linux / Unix ports.
I find Project Starfighter a real game with a class for the Linux platform. Below I provide you with a screenshot from a battle between your own battle ship and an enemy boss:
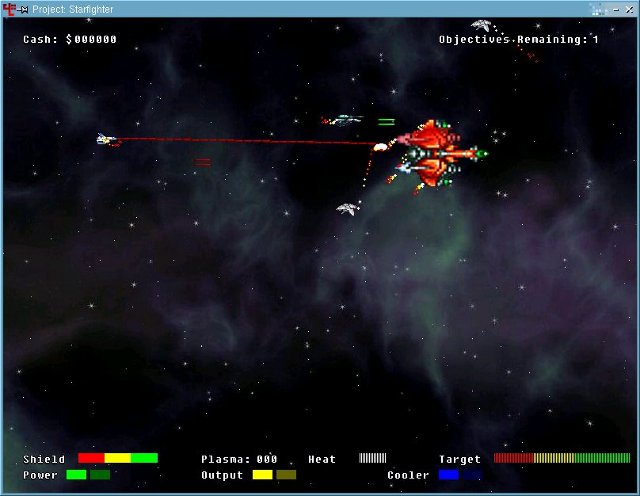 Some of the game includes features (as taken directly from the
game's website) are:
Some of the game includes features (as taken directly from the
game's website) are:
Mentioning about the game music here is the time to tell you that the game music of Project Starfighter is among the best game soundtracks I've ever heard in my life!
The music is quite much a demoscene like so I'm quite sure if you play the game you will truly enjoy the wonderful game music.
The game would require you to have a succesfully configured and running SDL library on your Linux, along with that you will have to have a properly installed video drivers otherwise the game would run up very slowly.
The game is available for a numerous computer OS platforms including even Microsoft Windows :)
Again we the Debian users are favourable because the game has been packaged in a deb for a Debian platform to install the game on Debian GNU/Linux invoke in your root terminal:
The game is started either by navigating to GNOME / KDE menus games menus or directly via a terminal by executing:
The game has one major drawback, it's difficulty level is a real killing one, you have to play at least a couple of games until you're able to pass level 1.
I've never ever passed level 2, if the developers work out the too complex game level of difficulty then I believe the game will be a way more addictive.
Anyways each of the 3 reviewed games Torus Trooper, TUMIKI Fighters and Project Starfighter are really addictive and makes the ordinary sys admin / programmer life a bit more enjoyable :)
The arcade games for Linux are really lot, however most of them are too boring and has a notable bad graphic design or a game play, here is why I decided to blog about two really worthy games to be noted and placed among best arcade games produced so far.
Below you will find a quick game review of the arcade game Linux trio Torus Trooper, Tumiki Fighters and Starfighter
1.Let me begin with Torus Trooper
Torus trooper is an awesome fast pace japanese game a bit in the tradition of the good old Star Wars racer the graphics of course as with most Linux games are not that awesome as with Star Wars racer, however the game is a really nice one 3D tunnel shooter, especially if you'd like to play half an hour to relax from a heavy strained day. In the game you have a spaceship and you have to navigate through a rotating tunnels and kill the enemy's spaceship, there is quite a lot of action involved and this makes the game really wonderful to lift up your adrenaline :)
While navigating though the tunnels and killing enemies you can switch up and down your spaceship acceleration,
you have a limited time for which you have to complete each of the game levels, whether killing a series of enemies
would win you some bonus seconds usually if you get a bonus time an extra +15 seconds is added to your time limit you're supposed to complete the level.
On certain scores also can grant you extra time bonus of (+15) seconds. If you get killed then a (-15 seconds) are deducted from your level completion time limit.
As every arcade in the game each level has a boss (a base) you have to destroy dependantly the time interval in which you succeed in destroying the end level boss would add up either (+30) or (+45) seconds to your overall game time limit.
The enemy will show up after you kill a previously game defined number of enemy's spaceship, the remaining enemy's spaceship to be destroyed is (displayed at the right up corner) of the game.
Below I present you with the screenshot taken from Torus Trooper 's official website and hopefully it will give you a brief idea what to expect if you desire to give the game a go on your GNU/Linux.

The game installation on Debian is pretty straight forward is available as a debian package to install just copy paste in your root terminal the:
debian:~# apt-get install torus-trooper
Now all left is to start up the game in full-screen mode by typing as a non-privileged user:
debian:~$ torus-trooper -fullscreen
What annoyed me a bit was the fact that I couldn't find a fullscreen option in after starting up the game without the -fullscreen option. But heh, let us not forget we are on Linux, things to be a bit commandish :)
Hopefully in future releases of the game (if there are such), the fullscreen will be added as a possible option to be selected from within the game itself.
Another very notable thing about the Torus Trooper game is the addicting music and game play I belive is the real charm of arcade games.
2. TUMIKI Fighters
Is another great japanese arcade game, it's an interesting fact that both TUMIKI Fighters and Torus Trooper are created by a single Japanese man Kenta Cho
Mr. Kenta Cho has done quite a good job especially if we consider the fact that he is the only one that has developed this two wonderful games.
TUMIKI Fighters's also very dynamic, however it's more a 2D like arcade, each of the ships within the game are actually a toy like (Lego like).
What I find unique about TUMIKI Fighters as a game is the fact that whenever you kill an enemy toy ship you're able to assimilate the destoying ship before your eyes.
As described in TUMIKI Fighters official game web site ,
"Stick more enemies and become much stronger."
In other words the more ships you are able to gain to your basis ship the stronger your ship becomes.
Below I present you with a screenshot to get an idea what to expect if you consider installing and playing the game.

The screenshot is a bit messed and the game looks a way better in reality so I urge you to take few seconds to install and try it.
If you're on Debian just issue command:
debian:~# apt-get install tumiki-fighters
To start up the game in fullscreen in a similar fashion to Torus Trooper you will have to pass the -fullscreen command option next to the main game binary.
So:
debian:~$ tumiki-fighters -fullscreen
Will start the game in fullscreen.
3. Finally I'll tell you a few words about Project Starfighter
Project Starfighter is I a class above both Tumiki Fighters and Torus Trooper this is most probably because it was developed by a developers group called Parallel Realities
If you're a Linux game developer, it's very likely that checking their website will provide you with a number of precious articles on Game development e.g. making many of the developed Parallel Realities developed games as well as game source code.
Parallel Realities has so far developed a lot of games, they've done a great job that each of the games has Linux / Unix ports.
I find Project Starfighter a real game with a class for the Linux platform. Below I provide you with a screenshot from a battle between your own battle ship and an enemy boss:
 Some of the game includes features (as taken directly from the
game's website) are:
Some of the game includes features (as taken directly from the
game's website) are:- 26 missions over 4 star systems
- Primary and Secondary Weapons (including a laser cannon and a charge weapon)
- A weapon powerup system
- Missions with Primary and Secondary Objectives
- A Variety of Missions (Protect, Destroy, etc)
- 13 different music tracks
- Boss battles
Mentioning about the game music here is the time to tell you that the game music of Project Starfighter is among the best game soundtracks I've ever heard in my life!
The music is quite much a demoscene like so I'm quite sure if you play the game you will truly enjoy the wonderful game music.
The game would require you to have a succesfully configured and running SDL library on your Linux, along with that you will have to have a properly installed video drivers otherwise the game would run up very slowly.
The game is available for a numerous computer OS platforms including even Microsoft Windows :)
Again we the Debian users are favourable because the game has been packaged in a deb for a Debian platform to install the game on Debian GNU/Linux invoke in your root terminal:
debian:~# apt-get install starfighter
The game is started either by navigating to GNOME / KDE menus games menus or directly via a terminal by executing:
debian:~$ starfither
The game has one major drawback, it's difficulty level is a real killing one, you have to play at least a couple of games until you're able to pass level 1.
I've never ever passed level 2, if the developers work out the too complex game level of difficulty then I believe the game will be a way more addictive.
Anyways each of the 3 reviewed games Torus Trooper, TUMIKI Fighters and Project Starfighter are really addictive and makes the ordinary sys admin / programmer life a bit more enjoyable :)
Fri Aug 27 17:10:27 EEST 2010
Code snippet to check if form typed email is present in Database with Zend Framework / substitute for Db_NoRecordExists (Db_RecordExists)
I'm writting a registration form and
in Zend Framework (ZF) and I came to the point where the input
email form address had to be stored in database if it's not already
there.
Thus I needed a way to complete the task. Firstly I tried using Db_NoRecordExists and Db_RecordExists which is the "proper" way to complete this task in Zend Framework.
I tried to apply a code to my Zend Form similar to:
Nevertheless I couldn't make the above code to work out, thus I eventually ended up writting my own function in order to check if the form input email is not already stored in database and if it's stored to render again my Zend Registration input form.
Herein I present the code with a hope that somebody else that is a juniour with PHP Zend Framework just I am will benefit out of it.
1. First here is what is in my form controller application/controller/RegistrationForm.php:
In order to be able to use the above code you will also have to have existing application/models/DbTable/Registration.php or whatever name you'd like to choose.
Within that file place code like:
Of course change the database.my_table_name with whatever your database and table name is, also assure $email_address which is defined by the above code $this->email_address = $email_address = $formData['email']['email']; has to be properly tuned in your application/controller/RegistrationController.php or whatever it is called. In my case I use the $formData data array to store my email variable earlier taken by the Zend Form I use the following code to check if my request is properly posted by the Zend_Form:
As you can see I use $formData to get Zend_Form posted conteny, if you use another modify the above code to math up with it.
Hope that's helpful to somebody out there!
Feedback as always is very welcome.
}
Thus I needed a way to complete the task. Firstly I tried using Db_NoRecordExists and Db_RecordExists which is the "proper" way to complete this task in Zend Framework.
I tried to apply a code to my Zend Form similar to:
$email = new Zend_Form_SubForm();
$email->addElements(array(
$email_addr = new Zend_Form_Element_Text('email'),
));
$email_addr->setRequired(true)
->setLabel('Email:')
->setValue('email (Gmail, Yahoo, etc.)')
->addFilter('StringTrim')
->addFilter('StripTags')
->addValidator('EmailAddress', false)
->addValidator('Db_NoRecordExists', false, array('table' =>
'my_table_name','field' => 'email'))
->setAttribs(array('minlength' => '5', 'maxlength' =>
'40'));
Nevertheless I couldn't make the above code to work out, thus I eventually ended up writting my own function in order to check if the form input email is not already stored in database and if it's stored to render again my Zend Registration input form.
Herein I present the code with a hope that somebody else that is a juniour with PHP Zend Framework just I am will benefit out of it.
1. First here is what is in my form controller application/controller/RegistrationForm.php:
// pick up the email entered earlier from Zend Form
$this->email_address = $email_address =
$formData['email']['email'];
// if query_result = 1 then registrar has already an existant email
in db
$check_if_email_in_db = new Model_DbTable_Registration();
$query_result =
$check_if_email_in_db->checkUserisNotRegistered($this->email_address);
if($query_result == '1') {
$this-view->errorMsg =' Your email address is
already taken! Please type another one. ';
$this->form;
return;
}
In order to be able to use the above code you will also have to have existing application/models/DbTable/Registration.php or whatever name you'd like to choose.
Within that file place code like:
class Model_DbTable_Registration extends
Zend_Db_Table_Abstract
{
// set database name
protected $_name = 'database.my_table_name';
public function checkUserisNotRegistered($email_address) {
if(empty($email_address))
throw new Exception('empty parameter passed.');
$where = $this->_db->quoteIdentifier('email') . ' =
"'.$email_address.'"';
$this->fetchAll($this->select()->where($where));
$result = $this->fetchAll($this->select()
->where($where));
$query_result = $result['0']['email'];
if($query_result == NULL) {
$query_result = '0';
} else {
$query_result = '1';
}
return $query_result;
}
}
Of course change the database.my_table_name with whatever your database and table name is, also assure $email_address which is defined by the above code $this->email_address = $email_address = $formData['email']['email']; has to be properly tuned in your application/controller/RegistrationController.php or whatever it is called. In my case I use the $formData data array to store my email variable earlier taken by the Zend Form I use the following code to check if my request is properly posted by the Zend_Form:
if ($this->getRequest()->isPost()) {
$formData = $this->_request->getPost();
....
}
As you can see I use $formData to get Zend_Form posted conteny, if you use another modify the above code to math up with it.
Hope that's helpful to somebody out there!
Feedback as always is very welcome.
}
Thu Aug 26 15:48:02 EEST 2010
Uploading multiple files from a form with Zend Framework (ZF) / Storing uploaded zf files with unique name
Here is the code basis I used to
implement a form file uploader in Zend Framework (ZF).
I tried to write the code as self explanatory as possible, hope I achieved my goal. If you have to solve the task I believe my code can help you out. Check out the code:
In the above code example the getExtension function is prepared in order to extract the file extension, this is necessary to build up the uploaded file name.
In this code sample, the foreach loop will get through all the defined file names earlier on and will iterate through them setting each file a unique name in the format similar to file_0_UVicsNlBcH.your_file.txt .
As you can see the generated file has few parts "file" is a static one 0 is generated because the file to be saved is the first uploaded file from a defined Zend_Form. . The UVicsNlBcH within the file name is an unique key by which you can later recognize the file name, this is especially handy if you also store the string somewhere in database.
The code:
is responsible for renaming each of the uploaded files to the custom generated file name. I believe the rest of the code is very easy to understand.
It took me a while until I come up with this code and I do not guarantee that this way of doing things is secure or anything it just seems to work for me for now so I decided to share it in an attempt to help to somebody developing a file uploader in Zend Framework.
The feedback or code improvement suggestions are very welcome!
I tried to write the code as self explanatory as possible, hope I achieved my goal. If you have to solve the task I believe my code can help you out. Check out the code:
// open Zend Http file transfer stream
$file_upload = new Zend_File_Transfer_Adapter_Http();
// Returns all known internal file information
$files = $file_upload->getFileInfo();
$file['unique_key0'] =
My_General_Functions::gen_random_string(10);
$file['unique_key1'] =
My_General_Functions::gen_random_string(10);
$file_upload->setDestination(Zend_Registry::get('Config')->file_uploads->destination_dir);
$i = 0;
foreach($file_upload->getFileInfo() as $info) {
// get uploaded files extensions
$file_ext = $this->getExtension($info['name']);
// generate file names for the ones to be stored on server
$fileName =
'file'.'_'.$i.'_'.$file["unique_key$i"].'.'.$file_ext;
$filename[$i] = $info['name'];
$i++;
// rename each of the uploaded files with random name based on
unique_key0 and unique_key1 array vars
$file_upload->addFilter('Rename', array(
'target' =>
Zend_Registry::get('Config')->file_uploads->destination_dir .
'/' . $fileName,
'overwrite' => 'yes'
));
if(!$file_upload->receive($info['name'])) {
$this->view->msg = $file_upload->getMessages();
return;
}
}
public function getExtension ($name)
{
if($name){
$exts = preg_split("[/\\.]", $name);
$n = count($exts)-1;
$exts = $exts[$n];
return $exts;
}
In the above code example the getExtension function is prepared in order to extract the file extension, this is necessary to build up the uploaded file name.
In this code sample, the foreach loop will get through all the defined file names earlier on and will iterate through them setting each file a unique name in the format similar to file_0_UVicsNlBcH.your_file.txt .
As you can see the generated file has few parts "file" is a static one 0 is generated because the file to be saved is the first uploaded file from a defined Zend_Form. . The UVicsNlBcH within the file name is an unique key by which you can later recognize the file name, this is especially handy if you also store the string somewhere in database.
The code:
$file_upload->addFilter('Rename', array(
'target' =>
Zend_Registry::get('Config')->file_uploads->destination_dir .
'/' . $fileName,
'overwrite' => 'yes'
));
is responsible for renaming each of the uploaded files to the custom generated file name. I believe the rest of the code is very easy to understand.
It took me a while until I come up with this code and I do not guarantee that this way of doing things is secure or anything it just seems to work for me for now so I decided to share it in an attempt to help to somebody developing a file uploader in Zend Framework.
The feedback or code improvement suggestions are very welcome!
Wed Aug 25 16:57:57 EEST 2010
VIM Project (VI Improvied IDE Editor extension to facilitate web development with vi enhanced editor
I use VIM as an editor of choice for many years
already.
Yet it's until recently I use it for a PHP ZF (Zend Framework) web development.
Few days ago I've blogged How to configure vimrc for a php syntax highlightning (A Nicely pre-configured vimrc to imrpove the daily text editing experience
This enhancements significantly improves the overall PHP code editing with VIM. However I felt something is yet missing because I didn't have the power and functunality of a complete IDE like for instance The Eclipse IDE
I was pretty sure that VIM has to have a way to be used in a similar fashion to a fully functional IDE and looked around the net to find for any VIM plugins that will add vim an IDE like coding interface.
I then come accross a vim plugin called VIM Prokject : Organize/Navigate projects of files (like IDE/buffer explorer)
The latest VIM Project as of time of writting is 1.4.1 and I've mirrored it here
The installation of the VIM Project VIM extension is pretty straight forward to install it and start using it on your PC issue commands:
1. Install the project VIM add-on
2. Load the plugin
Launch your vim editor and type :Project
You will further see a screen like:
3. You will have to press \C within the Project window to load a new project
Then you will have to type a directory to use to load a project sources files from:
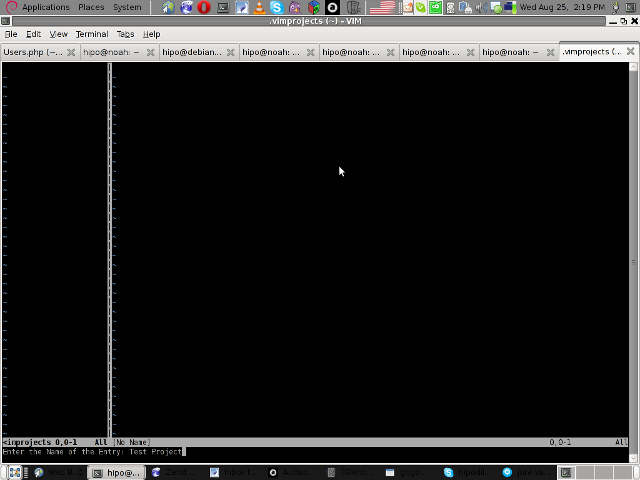
You will be prompted with to type a project name like in the screenshot below:
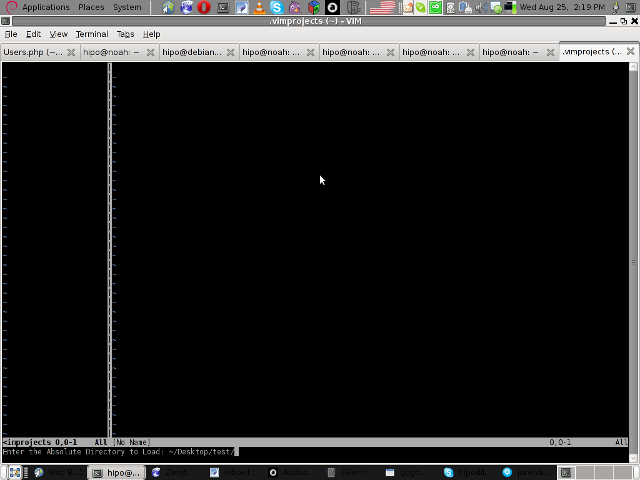
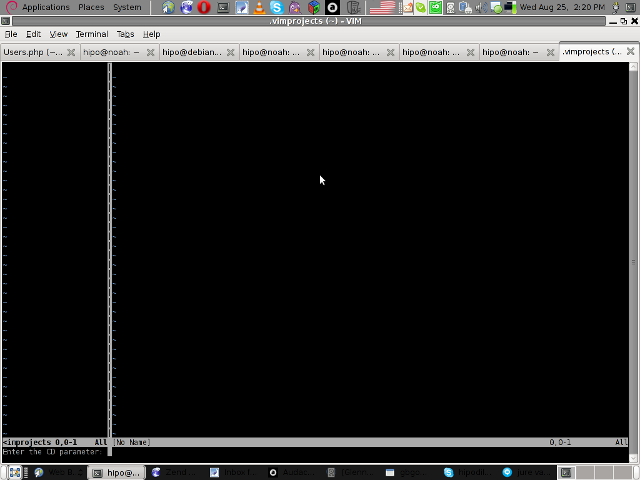
4. Next you will have to type a CD (Current Dir) parameter
To see more about the CD parameter consult vim project documentation by typing in main vim pane :help project
The appearing screen will be something like:
5. Thereafter you will have to type a file filter
File filter is necessary and will instruct the vim project plugin to load all files with the specified extension within vim project pane window
You will experience a screen like:
 alt="vim
project plugin file filter screen" />
alt="vim
project plugin file filter screen" />
Following will be a short interval in which all specified files by the filter type will get loaded in VIM project pane and your Zend Framework, PHP or any other source files will be listed in a directory tree structure like in the picture shown below:
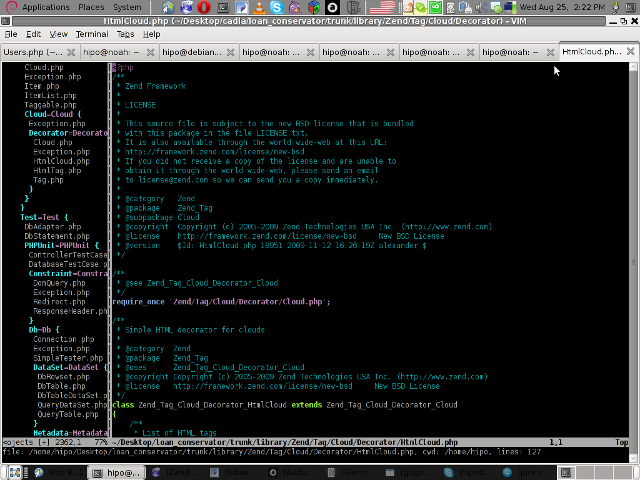
6. Saving loaded project hierarchy state
In order to save a state of a loaded project within the VIM project window pane you will have to type in vim, let's say:
:saveas .projects/someproject
Later on to load back the saved project state you will have to type in vim :r .projects/someproject
You will now have almost fully functional development IDE on top of your simple vim text editor.
You can navigate within the Project files loaded with the Project extension pane easily and select a file you would like to open up, whenever a source file is opened and you work on it to switch in between the Project file listing pane and the opened source code file you will have to type twice CTRL+w or in vim language C-w
To even further sophisticate your web development in PHP with vim you can add within your ~/.vimrc file the following two lines:
In the above vim configuration directovies the " character is a comment line and the autocmd is actually vim declarations.
The first :autocmd ... declaration will instruct vim to execute your current opened php source file with the php cli interpreter whenever a key press of CTRL+M (C-m) occurs.
The second :autocmd ... will add to your vim a shortcut, so whenever a CTRL+L (C-l) key combination is pressed VIM editor will check your current edited source file for syntax errors.
Therefore this will enable you to very easily periodically check if your file syntax is correct.
Well this things were really helpful to me, so I hope they will be profitable for you as well.
Cheers :)
Yet it's until recently I use it for a PHP ZF (Zend Framework) web development.
Few days ago I've blogged How to configure vimrc for a php syntax highlightning (A Nicely pre-configured vimrc to imrpove the daily text editing experience
This enhancements significantly improves the overall PHP code editing with VIM. However I felt something is yet missing because I didn't have the power and functunality of a complete IDE like for instance The Eclipse IDE
I was pretty sure that VIM has to have a way to be used in a similar fashion to a fully functional IDE and looked around the net to find for any VIM plugins that will add vim an IDE like coding interface.
I then come accross a vim plugin called VIM Prokject : Organize/Navigate projects of files (like IDE/buffer explorer)
The latest VIM Project as of time of writting is 1.4.1 and I've mirrored it here
The installation of the VIM Project VIM extension is pretty straight forward to install it and start using it on your PC issue commands:
1. Install the project VIM add-on
debian:~$ wget
http://pc-freak.net/files/project-1.4.1.tar.gz
debian:~$ mv project-1.4.1.tar.gz ~/.vim/
debian:~$ cd ~/.vim/
debian:~$ tar -zxvvf project-1.4.1.tar.gz
2. Load the plugin
Launch your vim editor and type :Project
You will further see a screen like:

3. You will have to press \C within the Project window to load a new project
Then you will have to type a directory to use to load a project sources files from:

You will be prompted with to type a project name like in the screenshot below:

4. Next you will have to type a CD (Current Dir) parameter
To see more about the CD parameter consult vim project documentation by typing in main vim pane :help project
The appearing screen will be something like:

5. Thereafter you will have to type a file filter
File filter is necessary and will instruct the vim project plugin to load all files with the specified extension within vim project pane window
You will experience a screen like:
 alt="vim
project plugin file filter screen" />
alt="vim
project plugin file filter screen" />Following will be a short interval in which all specified files by the filter type will get loaded in VIM project pane and your Zend Framework, PHP or any other source files will be listed in a directory tree structure like in the picture shown below:

6. Saving loaded project hierarchy state
In order to save a state of a loaded project within the VIM project window pane you will have to type in vim, let's say:
:saveas .projects/someproject
Later on to load back the saved project state you will have to type in vim :r .projects/someproject
You will now have almost fully functional development IDE on top of your simple vim text editor.
You can navigate within the Project files loaded with the Project extension pane easily and select a file you would like to open up, whenever a source file is opened and you work on it to switch in between the Project file listing pane and the opened source code file you will have to type twice CTRL+w or in vim language C-w
To even further sophisticate your web development in PHP with vim you can add within your ~/.vimrc file the following two lines:
" run file with PHP CLI (CTRL-M)
:autocmd FileType php noremap <C-M>
:w!<CR>:!/usr/bin/php %<CR>
" PHP parser check (CTRL-L)
:autocmd FileType php noremap <C-L> :!/usr/bin/php -l
%>CR>
In the above vim configuration directovies the " character is a comment line and the autocmd is actually vim declarations.
The first :autocmd ... declaration will instruct vim to execute your current opened php source file with the php cli interpreter whenever a key press of CTRL+M (C-m) occurs.
The second :autocmd ... will add to your vim a shortcut, so whenever a CTRL+L (C-l) key combination is pressed VIM editor will check your current edited source file for syntax errors.
Therefore this will enable you to very easily periodically check if your file syntax is correct.
Well this things were really helpful to me, so I hope they will be profitable for you as well.
Cheers :)
Tue Aug 24 11:32:52 EEST 2010
Free Software in Balkans 2010 (A free software conference on the Balkanies is approaching)

Today when I was reviewing my daily visited websites I come across an interesting news.
This kind of meeting is quite a news because it is the first in line where Free software users and developmers from all around the balkanies will meet to discuss,test,share and continue the free software code and ideals.
The first Free Software conference in the Balkanies is about to be hosted in Vlora University Albania .
The conference Free Software in Balkans (FreeSB2010) is an annual meeting of the free software users, developpers and supporters in the Balkan countries. It will travel from country to country, year to year to different locations. The Conference will gather professionals, academics and enthusiasts who share the vision that software should be free and open for the community to develop and customize to its needs, and that knowledge is a communal property and free and open to everyone.
This kind of event will build up the social network between free software fans and developers and will further help in the general spread of free software on the balkanies.
This kind of meeting are already for a long time a tradition in many states in America, so having it in the balkanies is quite a development.
You can read a bit more about the exact focus of Free Software in Balkans 2010 conference here
Pitily right now there is no published scheduled list of presentations which are about to be given in the conference, but I guess the conference schedule would be out in a few days time.
I'm not yet sure if I'll have the time and opportunity to attend the conference, however I do hope that somebody of my balkan readers will got interested into the "fabulous" Free Software event and will support the event's initiative by visiting it :)
Mon Aug 23 15:17:14 EEST 2010
Last day after the great Christian Orthodox feast The Dormition of the Thetokost (sending the feast away the feast)

On 15th of August we celebrated in the Bulgarian Orthodox Church, as well as the other Orthodox Churches around the world, the celebration of the Great Feast commemorating the "falling asleep" e.g. physical death of the Theotokos (Virgin Mary)
We believe in the Orthodox Church that on this date the Mother of God Virgin Mary has passed away. The church tradition says that on that date it's our Lord and Saviour Jesus Christ himself that come from heaven to gather her soul.
We use to say that Virgin Mary has fall asleep because her physical death happened without any pain or suffering.
God bestowed Our Lady with such a death because of her humility and sinless life she choose to left while being on Earth.
The Church tradition also teaches that her bodily resurrection occured in a close similarity to Christs by Christ himself and she resurrected in the body was taken up to heaven after her death. The two weeks before dormition of the Theotokos occurs are being preceded by a two weeks fasting period. The dormition fast is one of the strictest fasts in the Church life, it's one of the 4 major fasts periods that occur within the Church life every the year. It's an interesting fast that a little while before Virgin's Mary "fall asleep", she has prayed to her son and our God Jesus Christ to let her see the Holy Apostles once again.
The Lord heard her prayer as she is the most venerable among the ones who lived in this earth and in a miraculous way transported the St. Apostles in the house of St. apostol John where the Theotokos was living. All the apostles were transported to see Virgin Mary except st. Apostol Thomas whose transport has been delayed a bit. He is been said to have arrived three days after her death, when he asked the other apostoles to see her grave so that he could bid her good bye, when all the 12 apostles went to Mother of God's grave they found no body and a sweet fragrance was filling the tomb air. As I said earlier Christ has taken her body to reunite it with the soul he had accepted 3 days earlier. Therefore theology teaches that Virgin Mary has undergone the second resurrection already, a resurrection that is about to come for all who currently abide at this earth with the Second Coming of Christ
An spiritual elder and a brother and Christ has mentioned to me that it is the sending away of the feast which apparently which's commemoration lasts for 8 days, quite an interesting fact I decided to share herein
A good account about the Dormition of the Holy Theotokos is found here and I suggest you read it up if you have some time.
There is another reason that the feast is so venerated it's being said by many people that Virgin Mary the mother of God blesses abundantly and protects everybody who keeps the fast before the feast of her Dormition.
Another practice within the Church is that flowers are being blessed on the date of the Dormition of Virgin Mary. In some Churches even there is a special shroud depicting the Theotokos's sleeping body after her death.
I've been to an interesting Liturgy where the Shroud or (Plashtenica) as better known in the Slavonic Eastern Orthodox world is being placed and is exhibited for a veneration of the layman and Church clergy. On the third day similarly to the resurrection of Our Lord and Saviour Jesus Christ this Plashtenica is being put away by the priest in order to show off that the body of the Mother of God was taken to heaven and has miraculously been resurrected and taken to heaven by God.
In Bulgaria the feast is known under the name Uspenie Bogorodichno - "The Dormition of the Theotokos". Uspenie derives from old slavonic and literally translated means "falling asleep".
Let the Holy Mother of God pray her son and our God Jesus Christ to have mercy on us the sinners.
Sun Aug 22 21:12:02 EEST 2010
Back from a nice tent camping on Krapets Beach
I've just returned from a nice
camping night spend in Krapets beach if we don't count the
unjustified outburst because some irritation all went peaceful.
Earlier on I've blogged about
The nice July Morning spend on Krapets beach For a second time
this year I have the blessing to come to this wild beach thanks to
Cvetomir (Ceco) an orthodox Christian broter in Christ as well as a
close friend.
The other friends that came with us was Stelio and Adriana.
I do recommend Krapets as a tourist destination to everybody who is commited to really have a good rest from daily stress as nowadays we experience in the cities.
Unfortunately we couldn't much swim because of the heavy high waves, but even the black sea air has a body and soul healing effect on health.
I always feel myself charged with new energy to go on with the strained daily wife when I spend such a wonderful time on such an magnifient places with such a nice people.
On our way back from Krapets beach, we went through Spasovo village (Saviour's) as it literal translation meaning from English says).
I just found out today that Spasovo appears to be one of the big villages in terms of population here in Bulgaria.
We sat to have a lunch in pub in the village.
We met there English couple family and took a conversation with them. It appeared that many English people and probably many westeners are crazy about Bulgaria and do feel it as a growing country and as a place where life is different and a way more interesting than England.
That was quite an interesting view for a English folks. It seems according to their story that paying bills in England and also the general normal life as we know it there is quite expensive even for English people.
They told us that a normal house in England costs like 30 000 to 40 000 pounds and this is a hell a lot of money to gather and that food expenses and taxes are really a killing ones there.
Anyways I'm gonna close the post with a picture view of Krapets just to give you an idea what to expect if you decide to visit it someday.

The other friends that came with us was Stelio and Adriana.
I do recommend Krapets as a tourist destination to everybody who is commited to really have a good rest from daily stress as nowadays we experience in the cities.
Unfortunately we couldn't much swim because of the heavy high waves, but even the black sea air has a body and soul healing effect on health.
I always feel myself charged with new energy to go on with the strained daily wife when I spend such a wonderful time on such an magnifient places with such a nice people.
On our way back from Krapets beach, we went through Spasovo village (Saviour's) as it literal translation meaning from English says).
I just found out today that Spasovo appears to be one of the big villages in terms of population here in Bulgaria.
We sat to have a lunch in pub in the village.
We met there English couple family and took a conversation with them. It appeared that many English people and probably many westeners are crazy about Bulgaria and do feel it as a growing country and as a place where life is different and a way more interesting than England.
That was quite an interesting view for a English folks. It seems according to their story that paying bills in England and also the general normal life as we know it there is quite expensive even for English people.
They told us that a normal house in England costs like 30 000 to 40 000 pounds and this is a hell a lot of money to gather and that food expenses and taxes are really a killing ones there.
Anyways I'm gonna close the post with a picture view of Krapets just to give you an idea what to expect if you decide to visit it someday.

Sat Aug 21 11:46:35 EEST 2010
How to add/create user accounts to be used with Trac (issue tracking system) on Linux
In my previous post I've blogged
how to install and configure Trac on Debian
The next logical question for me was how to use trac with multiple user accounts.
Thanksfully this happened to be very easy. All I had to do to setup different trac users was to add different Apache htaccess authentication accounts.
Consequently you will be logged in in Trac's interface after you login with your Apache htaccess user and password with the same user as provided in the Apache authentication dialog.
Of course to create the required Trac login accounts, you need to first have setup an Apache AuthType Basic declaration.
For example you will have to add something similar to:
your Apache virtualhost or domain configuration file.
In order to add the two users user1 and user2 then I simply had to add the users with the htpasswd Apache password tool.
Thanks God this was easy :)
The next logical question for me was how to use trac with multiple user accounts.
Thanksfully this happened to be very easy. All I had to do to setup different trac users was to add different Apache htaccess authentication accounts.
Consequently you will be logged in in Trac's interface after you login with your Apache htaccess user and password with the same user as provided in the Apache authentication dialog.
Of course to create the required Trac login accounts, you need to first have setup an Apache AuthType Basic declaration.
For example you will have to add something similar to:
<Location "/">
AuthType Basic
AuthName "Trac - projects"
AuthUserFile /etc/apache2/trac.passwd
Require valid-user
</Location>
your Apache virtualhost or domain configuration file.
In order to add the two users user1 and user2 then I simply had to add the users with the htpasswd Apache password tool.
debian:~# htpasswd /etc/apache2/trac.passwd user1
debian:~# htpasswd /etc/apache2/trac.passwd
user2
Thanks God this was easy :)
Fri Aug 20 16:21:04 EEST 2010
How to install and configure Trac on Debian GNU/Linux to track your software development
1. Install trac debian
package
2. Create trac project directories in /var/www/
If you have more than one repositories in Subversion then add as many /var/www/trac/project1, /var/www/trac/project2 as you like.
3. Initialize the base environment for a new track project and set proper permissions
When you type the trac-admin command you will have to fill in some very basic data concerning the new track project.
You will be prompted for things like project name , project sql type , repository type etc.
The most vital thing to enter here is the repository type and path to your repository.
Thanksfully by default trac uses svn so you just press enter when you're prompted for repo type.
Afterwards you will have to fill in the path to your svn repository in my case it was /var/svn-repos/project
4. Deploy the track cgi scripts with trac-admin
5. Install trac-spamfilter package to prevent spam on your Trac tickets
6. Install support for MySQL as a default Trac data storage If you're about to go with MySQL in favour of the default sqlite, (though I personally choose not to use it) issue command:
Edit and add to your /etc/apache2/sites-available/default the following variables:
It's a good idea also to add authentication to your trac to prevent any unwanted visitors to download your project source.
Again in your /etc/apache2/sites-enabled/default add something similar to:
7. Edit your /var/www/trac/project/conf/trac.ini
Some of the values I changed here and you might find it handy as well are:
By default attachment max_size was pretty low max_size = 262144 I decided to incrase it to max_size = 2621440
I've also changed src = site/logo.png to the exact path of my project logo. Changing this will make your project logo appear in the head of your new trac installment.
Something else I changed was the footer var which by default had a link pointing to trac's webpage I changed it to point to my project website, so you might consider doing same too.
I believe this is all I did to have a running installation of trac.
Few things to mention is that this installation uses the slower trac.cgi instead of the way faster and recommended trac.fcgi, however lest my many attempts to make the trac.fcgi as explained in Trac Guide I did not succeeded in starting apache to serve trac via trac.fcgi script.
It's really odd that the default steps explained in Trac On Debian as followed literally as described in the documnetation wouldn't get you anywhere and you will end up with an installation that is not really working, for some strange reason the documentation misses the trac cgi deploy step as I explain in above.
We also need to create the /etc/apache2/trac.htpasswd .htaccess file. To do so issue:
Place your password of choice
Be sure to also comment any existing declarations that say something like:
Any user feedback is very welcome, any suggestions or problems with the described install are about to be fixed asap as I have a user feedback.
debian:~# apt-get install trac
2. Create trac project directories in /var/www/
debian:~# mkdir /var/www/trac
debian:~# mkdir /var/www/trac/project
...If you have more than one repositories in Subversion then add as many /var/www/trac/project1, /var/www/trac/project2 as you like.
3. Initialize the base environment for a new track project and set proper permissions
debian:~# trac-admin /var/www/trac/project initenv
debian:~# find /var/www/trac/project -type f -exec chmod 660 {}
\;
debian:~# find /var/www/trac/project -type d -exec chmod 2770 {}
\;
When you type the trac-admin command you will have to fill in some very basic data concerning the new track project.
You will be prompted for things like project name , project sql type , repository type etc.
The most vital thing to enter here is the repository type and path to your repository.
Thanksfully by default trac uses svn so you just press enter when you're prompted for repo type.
Afterwards you will have to fill in the path to your svn repository in my case it was /var/svn-repos/project
4. Deploy the track cgi scripts with trac-admin
debian~:# trac-admin /var/www/trac/project /tmp/deploy
debian:~# mv /tmp/deploy/* /var/www/trac
debian:~# rm -rf /tmp/deploy
5. Install trac-spamfilter package to prevent spam on your Trac tickets
debian:~# apt-get install trac-spamfilter
6. Install support for MySQL as a default Trac data storage If you're about to go with MySQL in favour of the default sqlite, (though I personally choose not to use it) issue command:
debian:~# apt-get install python-mysqldb
Edit and add to your /etc/apache2/sites-available/default the following variables:
Alias /trac "/usr/share/trac/htdocs"
ScriptAlias /trac/project /usr/share/trac/cgi-bin/trac.cgi
<Location "/trac/project">
SetEnv TRAC_ENV "/var/www/trac/project"
</Location>It's a good idea also to add authentication to your trac to prevent any unwanted visitors to download your project source.
Again in your /etc/apache2/sites-enabled/default add something similar to:
<Location "/trac">
AuthType Basic
AuthName "Trac project"
AuthUserFile /etc/apache2/trac.htpasswd
Require valid-user
</Location>
7. Edit your /var/www/trac/project/conf/trac.ini
Some of the values I changed here and you might find it handy as well are:
By default attachment max_size was pretty low max_size = 262144 I decided to incrase it to max_size = 2621440
I've also changed src = site/logo.png to the exact path of my project logo. Changing this will make your project logo appear in the head of your new trac installment.
Something else I changed was the footer var which by default had a link pointing to trac's webpage I changed it to point to my project website, so you might consider doing same too.
I believe this is all I did to have a running installation of trac.
Few things to mention is that this installation uses the slower trac.cgi instead of the way faster and recommended trac.fcgi, however lest my many attempts to make the trac.fcgi as explained in Trac Guide I did not succeeded in starting apache to serve trac via trac.fcgi script.
It's really odd that the default steps explained in Trac On Debian as followed literally as described in the documnetation wouldn't get you anywhere and you will end up with an installation that is not really working, for some strange reason the documentation misses the trac cgi deploy step as I explain in above.
We also need to create the /etc/apache2/trac.htpasswd .htaccess file. To do so issue:
debian:~# htpasswd -c /etc/apache2/trac.htpasswd passwd
password:
Place your password of choice
Be sure to also comment any existing declarations that say something like:
ScriptAlias
or <Directory "/usr/lib/cgi-bin">
Any user feedback is very welcome, any suggestions or problems with the described install are about to be fixed asap as I have a user feedback.
Thu Aug 19 14:45:40 EEST 2010
How to configure .vimrc for PHP syntax highlighting - Download nicely configured .vimrc that can improve your daily vim text edit experience
The latest php.vim as of time of
writting is from 2008 and is two years newer than the php.vim that
comes with the latest vim package for Debian
Testing/Unstable.
To install the newer version of php.vim on my Debian desktop I issued the following commands:
1. Download newest version of vim.php from vim.org
This will have installed newest php.vim syntax highlighting rules. Now we will also need to copy a nicely configured .vimrc ready to be used for PHP highlighting, along with the PHP highlighting the .vimrc we are about to install is well configured for all kind of vim edits, so you will certainly benefit out if it if you're a vim user just like me.
2. Download a properly nicely configured .vimrc for all kind of syntax highlighting including php editing and many other vim capabilities enabled
To install the newer version of php.vim on my Debian desktop I issued the following commands:
1. Download newest version of vim.php from vim.org
noah:~# cd /usr/share/vim/vim72/
noah:/usr/share/vim/vim72 # mv /usr/share/vim/vim72/syntax/vim.php
/usr/share/vim/vim72/syntax/vim.php.orig
noah:/usr/share/vim/vim72 # lynx
http://www.vim.org/scripts/download_script.php?src_id=8651
# Now press D and Choose save to Disk in Lynx
noah:/usr/share/vim/vim72 # tar -zxvf php.tar.gz
-rw-r--r-- peter/peter 278277 2008-05-07 00:44
syntax/php.vimThis will have installed newest php.vim syntax highlighting rules. Now we will also need to copy a nicely configured .vimrc ready to be used for PHP highlighting, along with the PHP highlighting the .vimrc we are about to install is well configured for all kind of vim edits, so you will certainly benefit out if it if you're a vim user just like me.
2. Download a properly nicely configured .vimrc for all kind of syntax highlighting including php editing and many other vim capabilities enabled
noah:~/usr/share/vim/vim72 # cd ~
noah:~# wget http://pc-freak.net/files/.vimrc
You might also want to set the same .vimrc for all other users
except root, I'll leave this up to you.
Posted by hip0 |
Permanent link
Wed Aug 18 17:29:21 EEST 2010
How to validate a form email address with
PHP / PHP Validate Email address
I'm writting a small contact
form from scratch and I needed a quick and dirty way to validate
an email address with PHP
I've googled to find some examples and I found many examples for
completing the task, however in order to validate the email address
I eventually I ended up with the following PHP code:
if ( preg_match( "/^[-\w.]+@([A-z0-9][-A-z0-9]+\.)+[A-z]{2,4}$/", $email ) )
{
# Do some processing here - input if valid
$valid_email = '1';
}
else
{
print "" . ' ' . '
' . '
Bad e-mail address.
Please correct it '. 'and resubmit the
form
'; exit (1); }
Now just pass the input $email variable from your form to
the if condition and modify according to your
needs.
Posted by hip0 |
Permanent link
Tue Aug 17 19:11:41 EEST 2010
Speeding up your Apache hosted website
through mod_deflate on Debian / How to compress css and (js)
javascript
People who run websites which
aim at top responce times, are quite familiar with mod gzip
and mod deflate .
Both Apache modules mod deflate and mod gzip are used
for the very same purpose. They add a standard gzip compression to
the files that Apache transfer to your Webserver clients.
Its said mod_gzip is the more powerful and more configurable
module, however most people nowadays stick to the more straigh
forward and easier to set up mod_deflate
I personally also adhere to mod_deflate since it's documentation on
Apache's website is quite
complete.
In this article I'm gonna explain you how I quickly added support
for mod_deflate gzip compression to a Webserver I've recently had
to configure for a website.
Doing so reduced the access time to the website from 6-7 seconds as
reported by Yahoo's
Yslow to 3-4 secs.
These days people are constantly looking for a ways to improve
their web site opening times in order to improve the end user
experience, so the reduce to about 3 seconds in a website access
time is quite a good achievement.
Some time ago I've
blogged about How to enable http gzip compression on CentOS 5.x to
speed up Apache
However I've realized I haven't blogged how the same thing is
achieved on a Debian Linux so therefore I decided it might be
interesting to somebody out there to explore how same thing is
achieved on Apache server running on top of Debian.
Anyways enough jabberish, here is the exact steps I took on a
Debian Lenny server to configure properly an Apache 2.x webserver
gzip compression through the mod_deflate module.
1. Open up /etc/apache2/mods-available/deflate.conf and place
the following configuration directives within the file:
<IfModule mod_deflate.c>
# AddOutputFilterByType DEFLATE text/html text/plain text/xml
AddOutputFilterByType DEFLATE text/html text/plain text/xml
application/xml application/xhtml+xml application/rss+xml
application/json text/css text/javascript application/javascript
application/x-javascript
# Insert filter
#SetOutputFilter DEFLATE
# Netscape 4.x has some problems
BrowserMatch ^Mozilla/4 gzip-only-text/html
# Netscape 4.06-4.08 have some more problems
BrowserMatch ^Mozilla/4.0[678] no-gzip
# MSIE masquerades as Netscape, but it is fine
BrowserMatch bMSIE !no-gzip !gzip-only-text/html
# Don't compress images
SetEnvIfNoCase Request_URI .(?:gif|jpe?g|png)$ no-gzip
dont-vary
# Don't compress already compressed stuff !
SetEnvIfNoCase Request_URI .(?:exe|t?gz|zip|bz2|sit|rar)$ no-gzip
dont-vary
SetEnvIfNoCase Request_URI .pdf$ no-gzip dont-vary
# Make sure proxies don't deliver the wrong content
Header append Vary User-Agent env=!dont-vary
</IfModule>
Note that above configuration has an extra configuration directives
to AddOutputFilterByType DEFLATE which are gonna instruct it
to also gzip compress content of the CSS and Javascript (js)
files as well.
2. Shut off Etags in /etc/apache2/apache2.conf the quickest way
to do it would be:
debian-server:~# echo "FileEtag none" >>
/etc/apache2/apache2.conf
3. Enable mod_deflate in your Apache server
debian-server:~# ln -sf
/etc/apache2/mods-available/deflate.conf
/etc/apache2/mods-enabled/deflate.conf
debian-server:~# ln -sf /etc/apache2/mods-available/deflate.load
/etc/apache2/mods-enabled/deflate.load
Now you need to restart your Apache server for the changes to take
affect.
debian-server:~# /etc/init.d/apache2
restart
This changes are also about to include the common suggestion by
Yahoo Yslow that warns about the following message:
Grade D on Compress components with
gzip
There are x plain text components that should be
sent compressed
Thus the aforementioned changes to your Apache would guarantee you
also a good compression status in Yslow web site slowness
test.
After the changes the returned message by Yslow would be:
Grade A on Compress components with
gzip
By the way it took me quite a lot of time to search for a solution
to the annoying yslow issue where the .css and .js scripts
failed to be compressed with gzip nevertheless the mod_deflate
module was active.
I therefore hope this post will help somebody else issuing the
Yslow css and javascript not being compressed issues to get
solved.
Mon Aug 16 15:45:59 EEST 2010
How to anonymize Skype on Linux / Use anonymous skype through tor
I've recently worked on anonymizing
as many of my applications as I could in that spirit.
I looked for a practical way to anonymize my Skype. Skype communication is so essential this days,
it's very likely that a huge part of skype communication is being monitored by skype corp, it's not impossible that some malicious installed trojan in skype would report about which IP address you're using to connect to Skype.
Therefore proxifying skype could be a step further to at least prevent for following your skype traffic route.
Of course passing Skype traffic via tor is not a guarantee for anonimity since it's probably very easy for Skype owner company to keep record of Skype users, where do they people originate from, full log of people comminication via skype based on their user login.
As skype is a closed software and we have no access neither to the protocol specs neither to program source code, it's almost impossible to know if communication via skype is secure in sense of privacy.
It appeared that proxifying skype is a piece of cake and comes just to a proper instalating of Tor + polipo caching proxy and further installing proxychains
Proxychains is a rather interesting software, it's able to carry any application TCP and DNS traffic through a proxy server (http and socks).
Therefore proxychains is able to run any program through proxy server and hence hide your real IP.
Interesting fact is that proxychains is the Unix equivalent for Window's Freecap - "Program based on universal DLL injection in alien process (works on all Windows from Win95 to Longhorn), which hooks Winsock API, redirecting connect requests to the SOCKS server.
So if you intend to proxify your Skype application on a Windows host you will have to use Wincap.
Back to the main topic of "what is the way to proxify" skype on Linux, so here is how I did it:
1. Install proxychains (available on a Debian host directly as a deb package)
2. Install skype from source on Debian Testing/Unstable (Lenny / Squeeze / Sid). I personally use skype_static-2.0.0.72.tar.bz2
I looked for a practical way to anonymize my Skype. Skype communication is so essential this days,
it's very likely that a huge part of skype communication is being monitored by skype corp, it's not impossible that some malicious installed trojan in skype would report about which IP address you're using to connect to Skype.
Therefore proxifying skype could be a step further to at least prevent for following your skype traffic route.
Of course passing Skype traffic via tor is not a guarantee for anonimity since it's probably very easy for Skype owner company to keep record of Skype users, where do they people originate from, full log of people comminication via skype based on their user login.
As skype is a closed software and we have no access neither to the protocol specs neither to program source code, it's almost impossible to know if communication via skype is secure in sense of privacy.
It appeared that proxifying skype is a piece of cake and comes just to a proper instalating of Tor + polipo caching proxy and further installing proxychains
Proxychains is a rather interesting software, it's able to carry any application TCP and DNS traffic through a proxy server (http and socks).
Therefore proxychains is able to run any program through proxy server and hence hide your real IP.
Interesting fact is that proxychains is the Unix equivalent for Window's Freecap - "Program based on universal DLL injection in alien process (works on all Windows from Win95 to Longhorn), which hooks Winsock API, redirecting connect requests to the SOCKS server.
So if you intend to proxify your Skype application on a Windows host you will have to use Wincap.
Back to the main topic of "what is the way to proxify" skype on Linux, so here is how I did it:
1. Install proxychains (available on a Debian host directly as a deb package)
debian:~# apt-get install proxychains
2. Install skype from source on Debian Testing/Unstable (Lenny / Squeeze / Sid). I personally use skype_static-2.0.0.72.tar.bz2
debian:~# cd /root
debian:/root# wget
http://pc-freak.net/files/skype_static-2.0.0.72.tar.bz2
debian:/root# tar -jxvf skype_static-2.0.0.72.tar.bz2
debian:/root# mkdir /opt/Skype/
debian:/root# mv skype_static-2.0.0.72 /opt/Skype/
Also place a skype startup script to instruct skype that it will
have to use the pulseaudio for a sound server.
Crete the /usr/local/bin/skype file.
It should contain the following
#!/bin/sh export SDL_AUDIODRIVER=pulse; /usr/bin/proxychains
/usr/bin/linux32 /opt/Skype/skype_static-2.0.0.72/skype
#/usr/bin/torify /usr/bin/linux32
/opt/Skype/skype_static-2.0.0.72/skype
Now simply startup skype by either typing
/usr/local/bin/skype from a terminal or either create a
shortcut towards skype or edit the existing shortcut added in
either GNOME or KDE menus and set it to use /usr/local/bin/skype as
a skype starter.
Even better proxychains can be used to proxify via a tsocks proxy
any other application on your BSD or Linux.
I've also noticed that tor deb is also equipped with a program
called torify - torify - wrapper for tsocks and
tor
I'm not quite sure if torify is also able to torify skype along
with the other applications for which it can be used to torify
traffic, so if any of the readers of this article can give some
feedback if they have tried that would be really nice :)
Sun Aug 15 18:21:42 EEST 2010
The terrible impuldent Google Chrome Linux package default behaviour (Chrome overwritting default configurations without even asking)
Recently I issued some kind of
upgrade and have noticed Google Chrome is spit off the message you
read below:
I think this kind of insolent behaviour from Google's Linux Chrome version is notable.
How come that the browser indulges itself to tamper with my default gnome-www-browser?
For the KDE users I feel indebted to mention that by default gnome-www-browser is linked to Epiphany
which itself is cross linked from /etc/alternatives/gnome-browser to /usr/bin/epiphany
I'm pretty happy with Epipahy most of the time so I decided to switch back my default gnome-www-browser by issuing the cmds:
This will reverse back your default Gnome browser to Epiphany
Anyways this kind of behaviour of Google packaging their Google Chrome version to overwrite default configurations without even poping up a prompt or something is really passive agressiveness.
Guess the passive agressiveness is an overall politics adopted by Google nowadays.
update-alternatives: warning: forcing reinstallation of
alternative /usr/bin/google-chrome because link group
gnome-www-browser is broken.I think this kind of insolent behaviour from Google's Linux Chrome version is notable.
How come that the browser indulges itself to tamper with my default gnome-www-browser?
For the KDE users I feel indebted to mention that by default gnome-www-browser is linked to Epiphany
which itself is cross linked from /etc/alternatives/gnome-browser to /usr/bin/epiphany
I'm pretty happy with Epipahy most of the time so I decided to switch back my default gnome-www-browser by issuing the cmds:
debian:~# rm -f /etc/alternatives/gnome-www-browser
debian:~# ls -sf ln -sf /usr/bin/epiphany
/etc/alternatives/gnome-www-browserThis will reverse back your default Gnome browser to Epiphany
Anyways this kind of behaviour of Google packaging their Google Chrome version to overwrite default configurations without even poping up a prompt or something is really passive agressiveness.
Guess the passive agressiveness is an overall politics adopted by Google nowadays.
Sat Aug 14 06:50:16 EEST 2010
How to revoke user global privileges in MySQL
I've recently realized one of the
users I have added to one of the MySQL servers I do manage has
actually some included a list of some of the global
privileges.
This extra privileges the user had was actually something that was to be removed since the user is not supposed to be able to list all existent databases on the MySQL server and things alike:
You can see below the excact SQL queries I had to issue to revoke the granted global privileges for the username.
Note to change the username before you execute the below queries:
This extra privileges the user had was actually something that was to be removed since the user is not supposed to be able to list all existent databases on the MySQL server and things alike:
You can see below the excact SQL queries I had to issue to revoke the granted global privileges for the username.
Note to change the username before you execute the below queries:
REVOKE ALL PRIVILEGES ON * . * FROM
'username'@'localhost';
REVOKE GRANT OPTION ON * . * FROM 'username'@'localhost';
GRANT USAGE ON * . * TO 'username'@'localhost' WITH
MAX_QUERIES_PER_HOUR 0 MAX_CONNECTIONS_PER_HOUR 0
MAX_UPDATES_PER_HOUR 0 MAX_USER_CONNECTIOFri Aug 13 17:42:41 EEST 2010
Anonymising ICQ and MSN and other messangers via Tor on Linux

If you want to imrpove your internet privacy through tor-rifing your network traffic of ICQ and MSN networks.
Do the following:
1. Install tor server
debian:~# apt-get install tor
2. Install the polipo caching proxy
debian:~# apt-get install polipo
3. Download and overwrite default polipo configuration with the one from torproject.org
This is necessary to configure in order to have polipo adapted to work with tor, so issue the following commands:
debian:~# cd /etc/polipo
debian:~# wget
https://svn.torproject.org/svn/torbrowser/trunk/build-scripts/config/polipo.conf
debian:~# mv config config.bak
debian:~# mv polipo.conf config
4. Restart polipo for the new config settings to take affect
debian:~# /etc/init.d/polipo restart
Make sure in your /etc/tor/torrc you have existing the following two torrc directives:
debian:~# vim /etc/tor/torrc
SocksPort 9050 # what port to open for local application
connections
SocksListenAddress 127.0.0.1 # accept connections only from
localhost
5. Start up tor server if it's not already started
debian:~# /etc/init.d/tor retart
6. Install pidgin if you haven't got it installed already
debian:~# apt-get install pidgin
8. Start up the recent installed pidgin multi-protocol instant messanger
hipo@debian:~$ pidgin &
If you already previously properly installed and configured version of pidgin.
9. In pidgin messanger do the following changes to configure it to proxy traffic via tor
In your either your existing ICQ / MSN pidgin account navigate to:
- Accounts -> Manage Accounts
- Under Protocol ICQ
- click Modify..
- Now go to Proxy
The default Proxy setting in Debian Sid/Squeeze would Use GNOME Proxy Settings however in other Linux distributions or *BSD it could be either No Proxy or some other setting.
- Now substitute whatever options is choosen with SOCKS 5
- In the below data input field with a name Host: type 127.0.0.1
- For the Port: field box type the port 9050
You specify for a local proxy port 9050 because this is the default port where we have previosly configured polipo to proxify traffic to tor's anonymity network
The settings tor tunneling of traffic for Protocol MSN are analogous like for the ICQ Protocol so I won't repeat myself on that.
This described tor tunneling for ICQ and MSN traffic should be applicable to other IM protocols under the same logic.
Here is the time to nota that the above instructions should be also applicable for Gain with minor changes or even without any.
Of course because tunneling traffic via Poplipo and it's handling over to a tor node which will pass traffic randomly through different geographical locations whether tor servers reside will be more time consuming, so login account login time to your Messanger protocol of choice will vary and would be a bit longer.
The use of tor for your MSN and ICQ traffic is twofold:
1. Using tor anonymizing traffic network will keep your anonymity on the net private
2. Using the tor anonimity online services will let you access IM servers despite firewall blocking applied by administrators on certain places for instance (in your School or Your work env) and will therefore let you still use your favourite IM in spite of the applied firewall restrictions.
Anyways as we all know life is not perfect :)
Despite the slower logins and the bit slower message transmission, at least you won't be easily tracable by third party prying eyes,
administrators or any other messanger spying sniffer traffic logger installed somewhere in between yourself and the end side of an IM server.
Hope this article helps somebody out there and will be a step further in the battle for securying your privacy online.
Thu Aug 12 13:54:39 EEST 2010
How to skip annoying waiting times before download links appear in RapidShare and Megaupload
I've accidently found Skip screen a firefox plugin that
is able to get rid of annoying waiting times before you can manage
to your downloads for rapidshare, megaupload etc.
Maybe the plugin description from their website is the best to describe skipscreen
SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more! Never download music without it. Click here to install skipscreen to your firefox
That's all no more annoying waitings before you can proceed and download a rare file.
Maybe the plugin description from their website is the best to describe skipscreen
SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more! Never download music without it. Click here to install skipscreen to your firefox
That's all no more annoying waitings before you can proceed and download a rare file.
Wed Aug 11 15:41:59 EEST 2010
How to solve errors during subversion repository check out svn (Error: URL Error: of existing directory Error: expected URL does not match)
A colleague of mine tried recently to
use tortoise because his previous work station (a Mac Book
notebook) has a problem with his charging device.
Therefore he is right now forced to use Windows as tortoisesvn is among one of the best if not the best option of a subversion client for the Windows platform naturally he decided to install tortoise and to download one of th e subversion repositories stored on our development server.
Till now all went fine for him as he conctacted me in Skype to report he cannot check out from the repo, because his check out operation has su ddenly froze up with a message:
Added: C:\Users\myuser\application\configs\My\general.php Error: URL 'svn+ssh://someuser@192.168.0.1/var/svn-repos/your_repository/trunk/application/configs/Mine' Error: of existing directory 'C:\Users\myuser\application\configs\mine' does not match Error: expected URL
This of course is a very raw version of the error and it wasn't really gave us any clue on what might be causing the desired svn check out.
After a bit research in Google, a lot of testing and many try catches we got what was causing the check out failures on his Windows XP.
The whole issues were caused by the fact that Windows's FAT16, FAT32 file system is case insensitive.
On that account when tortoise tried to download and save two directories one called Mine and the other called mine under the same folder hood in windows it failed, since already Mine directory was present and existing.
It later appeared that the mine directory contained some old garbage which doesn't have to deal with out source application stored in the repository so we completely decided to remove it.
However the issues caused and the 30 minutes lost in tracking the issues are a lot of lost time for nothing ...
I'm not sure if it's Windows file case insenstive file system (for not implementing case sensitivity by now), subversion repository software running on the server or the tortoise client fault but I'm sure this is rather ridiculous and needs a soon and timely fix by someone of the three mentioned ones.
Therefore he is right now forced to use Windows as tortoisesvn is among one of the best if not the best option of a subversion client for the Windows platform naturally he decided to install tortoise and to download one of th e subversion repositories stored on our development server.
Till now all went fine for him as he conctacted me in Skype to report he cannot check out from the repo, because his check out operation has su ddenly froze up with a message:
Added: C:\Users\myuser\application\configs\My\general.php Error: URL 'svn+ssh://someuser@192.168.0.1/var/svn-repos/your_repository/trunk/application/configs/Mine' Error: of existing directory 'C:\Users\myuser\application\configs\mine' does not match Error: expected URL
This of course is a very raw version of the error and it wasn't really gave us any clue on what might be causing the desired svn check out.
After a bit research in Google, a lot of testing and many try catches we got what was causing the check out failures on his Windows XP.
The whole issues were caused by the fact that Windows's FAT16, FAT32 file system is case insensitive.
On that account when tortoise tried to download and save two directories one called Mine and the other called mine under the same folder hood in windows it failed, since already Mine directory was present and existing.
It later appeared that the mine directory contained some old garbage which doesn't have to deal with out source application stored in the repository so we completely decided to remove it.
However the issues caused and the 30 minutes lost in tracking the issues are a lot of lost time for nothing ...
I'm not sure if it's Windows file case insenstive file system (for not implementing case sensitivity by now), subversion repository software running on the server or the tortoise client fault but I'm sure this is rather ridiculous and needs a soon and timely fix by someone of the three mentioned ones.
Tue Aug 10 13:12:34 EEST 2010
The Shepheard of Hermas an apocrypha book, used by some early Christian heresies
Heresis in Christianity, has seen long time ago been sprawling and trying to infect the correct Christian faith we shold have.
One very famous apocrypha book which was very modern around "alternative" faith seekers is The Shepherd of Hermas
The work has been well known in the west and has been widely copied in the middle ages.
The original work dating is probably either to the 2nd cenruty or to the distant 88 - 97 year after Christ.
The work is actually something similar to the Revelation of John, though it's most probably.
The book consists of five visions granted to Hermas, a former slave. This is followed by twelve mandates or commandments, and ten similitudes, or parables. It commences abruptly in the first person: "He who brought me up sold me to a certain Rhoda, who was at Rome. After many years I met her again, and began to love her as a sister." As Hermas was on the road to Cumae, he had a vision of Rhoda, who was presumably dead. She told him that she was his accuser in heaven, on account of an unchaste thought the (married) narrator had once had concerning her, though only in passing. He was to pray for forgiveness for himself and all his house. He is consoled by a vision of the Church in the form of an aged woman, weak and helpless from the sins of the faithful, who tells him to do penance and to correct the sins of his children. Subsequently he sees her made younger through penance, yet wrinkled and with white hair; then again, as quite young but still with white hair; and lastly, she shows herself as glorious as a Bride.
This allegorical language continues through the other parts of the work. In the second vision she gives Hermas a book, which she afterwards takes back in order to add to it. The fifth vision, which is represented as taking place twenty days after the fourth, introduces "the Angel of repentance" in the guise of a shepherd, from whom the whole work takes its name. He delivers to Hermas a series of precepts (mandata, entolai), which form an interesting development of early Christian ethics. One point which deserves special mention is the assertion of a husband's obligation to take back an adulterous wife on her repentance. The eleventh mandate, on humility, is concerned with false prophets who desire to occupy the first seats (that is to say, among the presbyters). Some have seen here a reference to Marcion, who came to Rome c.140 and desired to be admitted among the priests (or possibly even to become bishop of Rome).
After the mandates come ten similitudes (parabolai) in the form of visions, which are explained by the angel. The longest of these (Similitude 9) is an elaboration of the parable of the building of a tower, which had formed the matter of the third vision. The tower is the Church, and the stones of which it is built are the faithful. But in the third vision it looked as though only the holy are a part of the Church; in Similitude 9 it is clearly pointed out that all the baptized are included, though they may be cast out for grave sins, and can be readmitted only after penance.
In spite of the grave subjects, the book is written in a very optimistic and hopeful tone, like most early Christian works. Our Church the estern Orthodox Church identintifies the work nowadays as a heresy, so any man determined ot read it better do it with a blessing of his spiritual father, otherwise man is risking to have a serious harm on his spiritual state.
We should be well aware that since the book is talking against the presbyters in the early Church and does criticize the spiritual authority ok Christ's early church it has to be considered as a dangerous reading for us the comtemporary Christians.
However I thought mentioning the book here would be interesting, since it's so ancient and therefore with a high historical value, not to mention it is so similar by some things with its ideas to early Christianity.
Mon Aug 9 14:54:18 EEST 2010
Monitoring and restart server services (Apache, Mysql, Bind) with Monit to prevent server downtimes

If you're a system administrator responsible for a server running a heavy loaded high traffic website equipped with Apache, MySQL, Bind, Spamassassin .. you name the service, you have probably already faced the stressful situations whenever unexpected server services crashes occur.
You should already know by experience that whenever an Apache or Database server goes down especially on a well known respected website, then you're into real shit.
In my prefessional work experience as a system admin some time ago I found a handy small program written especially to save you the many nerves and worries, of unexpected server services failures caused by an unexpected running server software bugs.
The great program able to monitor your specified system services is called Monit
Monit is specially written with the idea in mind to track daemon, processes, files, devices and even a remote systems.
What makes monit a really superb and a desireful piece of software to install on each and every software you take care of is it's ability to trigger certain activities whenever some critical problems with monitor system files are missing, daemons are not runnign any more, some kind of critical system overload occurs and even almost everything bad you can imagine could happen could be previously foreseen and described from the monit configuration file monitrc
For instance if your MySQL server is crashing every now and then without logging any meaningful to its log file, and yet your site users have to wait before it gets restarted by you, you can easily automate that using monit.
Monit is also built with a small daemon listening on a port that is able to show you the monitored services state, it's also capable of sending altert emails in case if critical predefined occurances.
Monit is even able to be installed on a number of server nodes and be used directly from a common web interface and therefore a management of all server services from just one interface is possible.
This is especially handy if you're a system administrator responsible for 10+ servers like I used to be some time ago.
Another handy example of whenever using monit would be of a immesurable extra benefit is for instance if you have a server where you have a dying SSH server every now and then on your dedicated server located some 100 000 km away.
If you have properly installed and configure monit and this kind of emergency situation occurs monit will handle the situation and restart your SSHD daemon ASAP as it realizes the sshd daemon is not properly running on your server.
In this article I'm about to explain how to install and configure monit on a Debian GNU/Linux.
The install and configure procedure should be most likely also compatible with Ubuntu and any other Debian based distribution like Sidux, on Redhat based Linuxes the steps to be followed might be a bit different but yet easily adapted from the one I explain here.
1. Install the monit deb package on your Debian server
debian-server:~# apt-get install monit
2. Configure monit to enabled as a daemon and start up on boot
- Edit /etc/default/monit :
By default /etc/default/monit looks like so:
# Defaults for monit initscript
# sourced by /etc/init.d/monit
# installed at /etc/default/monit by maintainer scripts
# Fredrik Steen <stone@debian.org>
# You must set this variable to for monit to start
startup=0
# To change the intervals which monit should run uncomment
# and change this variable.
# CHECK_INTERVALS=180
Change in the above /etc/default/monit configuration:
startup=1
This is necessary otherwise the monit daemon won't start up.
3. Download my monitrc already configured to track and Restart MySQL, Apache and Bind
Apart from monitoring MySQL, Apache and Bind, with this configuration monit is configured to alert on an email that needs to be configured from /etc/monit/monitrc .
It also checks for free disk space availability dangerously decreasing as well as for high load avarage and critical low levels of memory usage.
You will have to modify the monitrc provided and substitute the my default domain pc-freak.net with whatever is the name of yours.
Some other minor modifations to the conf file might be necessary so review it before proceeding with running up the monit daemon.
You can either download a working copy of monitrc or directly execute on your server:
debian-server:~# cd /etc/monit
debian-server:/etc/monit # mv monitrc monitrc.orig
debian-server:/etc/monit # wget
http://pc-freak.net/files/monitrc
After a minor modifications to monitrc you should be ready to start up the monit service and it will monitor and alert whenever it matches any of the configuration prerogative.
4. Start up the monit service
debian-server:~# /etc/init.d/monit start
Having a monit on your server can assure you a better both server and services uptime as well as inform you of a possible approaching problems, the uses of monit to track and react on certain unexpected common troubles comes up to your imagination and creativity.
Sun Aug 8 20:46:18 EEST 2010
Using spriteme can improve your website view performance (Spriteme and sprites a quick look)
I've recently come across around SpriteMe a project which explains an approach in web development towards picture showing speed up with CSS.
The whole idea behind spriteme that it allows you to have a large image with a number of images and you can use some javascript to display the necessary image element part of the complete many elements image.
Using this kind of approach in displaying images in a website can save you the many dubious requests to the webserver and therefore could improve the website general access time.
The whole concept is very intesting so I suggest check it out by yourself.
Starting with sprime is a piece of cake as the guys of sprime.org has prepared a special javascript bookmark button which through which the user is able to prepare some image sprites.
A very good profound article on what is the Sprites and therein implementation called CSS Sprites: What They Are, Why They're Cool, and How To Use Them can be red here
Another good place to visit if you want to further read about Sprime and Sprites is the Css Sprites website
The whole concept behind sprime is based on an oldschool computer graphics technology called Read further about the sprite technology more in wikipedia
The css sprites are also well documented in w3cschools.com website so take a quick look therein as well.
As I'm a into computing for quite some time I even remeber that there was times that this kind of technology was a complete hype, even if I'm my memory is correct the great Heroes of Might and Magic II 's game graphic system was based around the sprite technology.
BTW Heroes of Might and Magic II is in the head in my best strategy game list.
Sprites was also heavily used earlier in games industry especially in console games for it's numerous privileges.
I haven't yet myself implemented the spritesme CSS technology in my website but I'm considering doing so ASAP I have some few hours time.
Not everything is perfect with spritesme though it can have a major impact on a website performance whenever implemented, there are still many risks as many browsers doesn't render the CSS in a proper way, not to mention that there are many people who use text mode browsers as lynx/links or some browser extensions that would not play well with CSS.
In the meantime I'll be glad to get some feedback of users who has experience with spritesme in web dev.
Sat Aug 7 12:20:32 EEST 2010
Controlling fan with Thinkfan on Lenovo Thinkpad R61 on Debian GNU/Linux (adjusting proper fan cycling)
Some time ago before I have
blogged about How to properly control your Lenovo Thinkpad R61 fan
rotation cycles on Linux with ThinkFan
In this tiny article I have explained my previous obstacles of making my Notebook CPU cooling fan to properly rotate and cool up my Central Processing Unit.
However just recently I've upgraded my Debian Unstable - Squeeze/Sid through the apt-get manager to the newest possible package updates.
The upgraded bundle of packages also updated my sid thinkfan package to:
I was unpleasently suprised when I tried to restart thinkfan using the thinkfan init.d script I have used until recently /etc/init.d/thinkfan , cause /etc/init.d/thinkfan was no longer be.
Furthermore I give a try to directly launch the thinkfan daemon from the terminal trying to backround the service, like so:
Though this started up the thinkfan daemon as you can see the note in the message below it started up with a consistent cycling cooling to keep the CPU wamrth sticked to 55 ° degrees:
WARNING: Using default temperature inputs in /proc/acpi/ibm/thermal.
WARNING: You have not provided any correction values for any sensor, and your fan will only start at 55 °C. This can be dangerous for your hard drive.
The message also indicated that the temperature values in in my recently hand crafted thinkfan.conf with custom temperature values does no longer comply to the thinkfan conf file syntax.
Therefore I had to change the obsolete thinkfan.conf file's values with a ones with which thinkfan wouldn't complain.
Thanksfully this wasn't such a hard job and in about 10 minutes time I have prepared the newer thinkfan.conf compatible with my Debian thinkfan 0.7.1-1 release.
The new working thinkfan.conf file can be obtained from here
It's necessary the old conf in /etc/thinkfan.conf is overwritten with the newer thinkfan.conf
Thereon a thinkfan daemon restart is required:
Of course afterwards the daemon has to be started again :)
The proper thinkfan daemon start up with the new conf should return an output:
I've also put on crontab that thinkfan is restarted every 30 minutes, just to make sure the daemon doesn't hang after a system restore from a hibernate state, this works generally well, if you want to follow my way add following in your root crontab.
,br />
This is it, now thinkfan will be fine again
In this tiny article I have explained my previous obstacles of making my Notebook CPU cooling fan to properly rotate and cool up my Central Processing Unit.
However just recently I've upgraded my Debian Unstable - Squeeze/Sid through the apt-get manager to the newest possible package updates.
The upgraded bundle of packages also updated my sid thinkfan package to:
hipo@noah:~$ dpkg -l |grep -i thinkfan
ii thinkfan 0.7.1-1 simple and lightweight fan control
program
I was unpleasently suprised when I tried to restart thinkfan using the thinkfan init.d script I have used until recently /etc/init.d/thinkfan , cause /etc/init.d/thinkfan was no longer be.
Furthermore I give a try to directly launch the thinkfan daemon from the terminal trying to backround the service, like so:
noah:~# thinkfan &
WARNING: Using default temperature inputs in
/proc/acpi/ibm/thermal.
WARNING: You have not provided any correction values for any
sensor, and your fan will only start at 55 °C. This can be
dangerous for your hard drive.
Though this started up the thinkfan daemon as you can see the note in the message below it started up with a consistent cycling cooling to keep the CPU wamrth sticked to 55 ° degrees:
WARNING: Using default temperature inputs in /proc/acpi/ibm/thermal.
WARNING: You have not provided any correction values for any sensor, and your fan will only start at 55 °C. This can be dangerous for your hard drive.
The message also indicated that the temperature values in in my recently hand crafted thinkfan.conf with custom temperature values does no longer comply to the thinkfan conf file syntax.
Therefore I had to change the obsolete thinkfan.conf file's values with a ones with which thinkfan wouldn't complain.
Thanksfully this wasn't such a hard job and in about 10 minutes time I have prepared the newer thinkfan.conf compatible with my Debian thinkfan 0.7.1-1 release.
The new working thinkfan.conf file can be obtained from here
It's necessary the old conf in /etc/thinkfan.conf is overwritten with the newer thinkfan.conf
Thereon a thinkfan daemon restart is required:
noah:~# killall -9 thinkfan
noah:~# rm -f /var/run/thinkfan.pid
Of course afterwards the daemon has to be started again :)
noah:~# /usr/sbin/thinkfan &
The proper thinkfan daemon start up with the new conf should return an output:
WARNING: Using default temperature inputs in
/proc/acpi/ibm/thermal.
Config as read from /etc/thinkfan.conf:
Fan level Low High
0 0 40
1 40 42
2 42 44
3 44 46
4 46 48
5 48 50
6 50 54
7 54 32767
Daemon PID: 22085
I've also put on crontab that thinkfan is restarted every 30 minutes, just to make sure the daemon doesn't hang after a system restore from a hibernate state, this works generally well, if you want to follow my way add following in your root crontab.
,br />
noah:~# crontab -u root -e
Place there:
0,30 * * * * killall -HUP thinkfan
This is it, now thinkfan will be fine again

Fri Aug 6 12:47:31 EEST 2010
Create ln symbolink or hard links with mount --bind for better filesystem read/write performance / Adding mount --bind to /etc/fstab
If you're building a website and you
need to create a link from a certain destination to another
place.
You've probably already thought about using the ln command to create a symbolic link to the questionable directory (folder).
Though this is one of the possible approaches to solve the task, it's far not the best one.
A possible alternative to the good old fashioned ln -s way would be through a bind mount - mount --bind
The mount --bind is well documented in mount's manual so it's best if you take a look at it.
You might want to check the following ln vs mount bind discussion to know more about why mount --bind is probably a better more efficient solution to link a location to another one in terms of efficiency.
fstab proper record for linking directory to another one using the --bind mount feature :
Bind mount is used to export a certain mounted directory to another one. The end result when using bind --mount it is absolutely. identical to a normal link created with ln .
However using a normal symlink is also less prone to a security leaks like filesystem directory traversal attacks etc.
Wherein ln -s command is used actually a new inode is created pointing to a certain filesystem object (let's say directory), for comparison mounting it instead of linking the directory won't have it's own inode on the filesystem created.
The above inode explanation directly means that in hard links and mount binds creation no special inode is reseverved for either the hard link or the mount --bind thus working with directories created with mount --bind is a bit faster and on a heavy loaded filesystems will have a positive decrease if used.
To permanently create a mount --bind from the /etc/fstab file in Linux, it would be necessary to place an fstab record like the one shown below:
To add the mount bind to fstab directly from terminal/console you can use a command like:
You've probably already thought about using the ln command to create a symbolic link to the questionable directory (folder).
Though this is one of the possible approaches to solve the task, it's far not the best one.
A possible alternative to the good old fashioned ln -s way would be through a bind mount - mount --bind
The mount --bind is well documented in mount's manual so it's best if you take a look at it.
You might want to check the following ln vs mount bind discussion to know more about why mount --bind is probably a better more efficient solution to link a location to another one in terms of efficiency.
fstab proper record for linking directory to another one using the --bind mount feature :
Bind mount is used to export a certain mounted directory to another one. The end result when using bind --mount it is absolutely. identical to a normal link created with ln .
However using a normal symlink is also less prone to a security leaks like filesystem directory traversal attacks etc.
Wherein ln -s command is used actually a new inode is created pointing to a certain filesystem object (let's say directory), for comparison mounting it instead of linking the directory won't have it's own inode on the filesystem created.
The above inode explanation directly means that in hard links and mount binds creation no special inode is reseverved for either the hard link or the mount --bind thus working with directories created with mount --bind is a bit faster and on a heavy loaded filesystems will have a positive decrease if used.
To permanently create a mount --bind from the /etc/fstab file in Linux, it would be necessary to place an fstab record like the one shown below:
/home/username/www/random/images
/home/username/www/unknown/images/ bind defaults,bind 0
0
To add the mount bind to fstab directly from terminal/console you can use a command like:
debian:~# echo "/home/username/www/random/images
/home/username/www/unknown/images/ bind defaults,bind 0 0" >>
/etc/fstab
Thu Aug 5 13:24:27 EEST 2010
How to install and configure torbutton on Debian / Anonymizing Iceweasel on Debian GNU/Linux

There is a quite a buzz online recently about the implications breach of personal privacy while browing online.
A week ago I've blogged On How to improve your web browser security for better personal identity
Though there is probably a plenty of more things to be done on guaranteeing your anonymous identity online, the article lacked to mention one very vital project the tor Anonymity online project The project offer the user the right to be anonymous online through a complex network expanding network of volunteers which voluntary install and grant access to the installed tor server to be used as a proxy from their computers.
A very thorough explanation on what is tor can be red here
Enabling tor on your personal computer would at least guarantee you that every now and then your traffic browser network traffic (request) would flow through a random tor servers located on a different worldly locations.
Usually the traffic to a destination host would pass through 5 tor network nodes. Where the traffic is unecrypted between last node and the 4th node, while in the other four ones it's completely crypted.
This makes your tracking almost impossible if it's based on technologies like for instance Maxmind's Geoip or Geonames's geographical data base because every now and then you'll appear to be coming to the end point referrar web server originating from a different tor node ip address
The tor server is a free software licensed under the GPL and this is also a good assurance because everybody is able to have a look on the code and this is a further guarantee that the software doesn't include a malicious ways for a middle users to sniff on your traffic.
The tor project has even built a pre-bundled browser ready to be worn by yourself on a usb stick, so you can quickly start using the tor anonymous network on any random computer anywhere.
The tor browser page is available here also Tor Browser Bundle for Windows is available here
Tor server is available for both Windows, Mac OS X, Linux and Linux/BSD Unix
Of course tor is not perfect it opens some other possible doors for attackers which are much less likely to occur if you don't use it, however in general it's better off with tor than without it.
One serious reason for not reason for not using Tor might be that it's usually many times slower than normal browser since, it routes traffic through a different tor network nodes.
So if you decide to go on and use it you better be patient and calm :)
Since I'm a Debian user and I really do value my privacy I decided to start using Tor.
In order to start using Tor it's usually necessary to configure your browser to use The TorButoon Firefox browserextension
Nevertheless on Debian GNU/Linux if you try to go the straigh way as explained on Tor's website install the TorButton and configure it to work in cooperation with the polipo caching proxy
You will be not able to browse after enabling straight the tor plugin.
If you try the up-mentioned approach you're probably about to come to errors like:
"the proxy server is refusing connections"
,
Proxy error: 502 Disconnected operation and object not in cache
or
504 Connect to superquizgames.com:80 failed: SOCKS error: host unreachable The following error occurred while trying to access http://yourwebsite.com/: 504 Connect to superquizgames.com:80 failed: SOCKS error: host unreachable
In order to properly install configure and enable the TorButton on my Debian GNU/Linux I had to get through the following steps:
1. Install the polipo caching proxy
debian:~# apt-get install polipo
2. Download and overwrite default polipo configuration with the one from torproject.org
This is necessary to configure in order to have polipo adapted to work with tor, so issue the following commands:
debian:~# cd /etc/polipo
debian:~# wget
https://svn.torproject.org/svn/torbrowser/trunk/build-scripts/config/polipo.conf
debian:~# mv config config.bak
debian:~# mv polipo.conf config
3. Restart polipo for the new config settings to take affect
debian:~# /etc/init.d/polipo restart
4. Install the iceweasel-torbutton browser extension
debian:~# apt-get install iceweasel-torbutton
>
The iceweasel-torbutton will also install you the tor package which
is evidently required for the torbutton to operate.
Now you should be ready to go, you can enable the tor use from the
tor button which should appear in your browser in the bottom right
corner of your browser.
It should look something similar to:
Tor Enable/Disable Iceweasel browser Button
To test your Tor Configuration you can use the Test Settings
button which is straight available from TorButton's
preferences
From here after it might be a good idea to play with the TorButton
security settings and configure it according to your liking, bear
in mind that you should have a solid knowledge on how browsers work
and some basic Internet protocols before you start tampering this
options.
If tou don't know what you do you better stop and don't tamper with
the torbutton security options.
The only one that you will most probably want to untick is The
Disable plugins during Tor usage , stopping this option will
allow you to have a flash video streaming display properly,
otherwise you won't be able to use , Vbox
etc.
Below you see a screenshot of the TorButton Security Settings
dialog.
To open up this dialog you need to navigate to the TorButto and
choose preferences with the right mouse buttons :)
Hope this article is informative to somebody out there.
User feedback is mostly welcome! Cheers :)
Posted by hip0 |
Permanent link
Wed Aug 4 12:43:21 EEST 2010
Enable user access only to ProFTP server /
Disable user login via ssh scp and sftp
Here is a way to enable a
system user login to a proftpd server while disable same user
system access through a bash, csh shell etc.
In the below examples I assume the system user is called
ftp-user and the running GNU/Linux is Debian. However same
instructions should be probably working on other Linux
distributions as well.
1. So let's begin creating a pseudo shell named
/bin/ftpaccess
debian:~# touch /bin/ftpaccess
debian:~# echo 'echo "This accout is for ftp access only"' >
/bin/ftpaccess
debian:~# echo 'exit 0' >> /bin/ftpaccess
debian:~# chmod +x /bin/ftpaccess
2. It's also necessary to include the just created pseudo FTP shell
/bin/ftpaccess in your /etc/shells file.echo '/bin/ftpaccess' >> /etc/shells
3. Then edit your /etc/passwd and change in the user shell, you should edit a line similar to:
ftp-user:x:1011:1005:FTP
User,,,:/home/ftp-user:/bin/bash
Afterwards the same user /etc/passwd line declaration should look like:
ftp-user:x:1011:1005:FTP
user,,,:/home/ftp-user:/bin/ftpaccess
Now the ftp-user user should have an FTP file transfer upload/download access to the server but it's SSH, SCP and SFTP access will be disabled.
Talking about disabling access of SFTP it's worthy to mention the RSSH Project .
RSS is quite cool and is able to restrict a shell access via SSH but same time allow users to use the SFTP and SCP protocols.
Other user feedback/experience for accomplishing the same task is very welcome!
Tue Aug 3 13:08:41 EEST 2010
How to configure Debian to create new added users through adduser to be secure by default
If you're about to add new users to
your Debian GNU/Linux you should have certainly noticed that the
default users created in /home directory are created with a
755 chmod permissions .
What makes it even worser is that in Debian by default the root user home directory /root has also a 755 permissons by default, you can see an example of the insecure behaviour below:
This is quite a big security leak since every user on the system can read and copy all the documents of every other one without any constraint. Users can have read access to the administrator root user !
I have no clear clue why the Debian development team has taken the decision to set such an insecure permissions by default, but anyways it's probably a good practice if you're sane person with a security in mind, should certainly realize that this kind of insecure by default permissions has to be changed for a secure one.
This is probably about to save you tons of nerves of possible security info leak among users or even, security leaks coming out of your home root directory.
Changing the default permissions for the new created users on the system using the adduser command is pretty easy and is being controlled by /etc/adduser.conf
the variable responsible for the persmissons of newly created user directories found within the file is: DIR_MODE by default in Debian this variable is set to be equal to DIR_MODE=0755 which as I've already said is insecure thus a recommandable change value would be: DIR_MODE=750
So procceed and open the vim /etc/adduser.conf and change the DIR_MODE=755 variable to DIR_MODE=0750 there is plenty of more configuration options that you might want to tamper with one worthy to mention is that through the same conf file you're able to specify the range values between which a new created user's ids and gids could borrow.
This can be done via the variables FIRST_SYSTEM_UID LAST_SYSTEM_UID and respectively for GIDS, FIRST_SYSTEM_GID and LAST_SYSTEM_GID
Another thing to do immediately is change your root's directory default set permissions during after your Debian Linux installation is complete, to do so:
If you're in a position where you have already any number of users existing with alredy created insecure user home directories permissions (755) then a simple (bash shell) one liner to change all the system users permissions to 750 and hence prohibit users to be able to read among each other's directory would be:
The default insecure behaviour that Debian Linux possess as well as the issue discussed above is well documentaed in Securing Debian Manual so check it out for a more thorough info on Debian security.
What makes it even worser is that in Debian by default the root user home directory /root has also a 755 permissons by default, you can see an example of the insecure behaviour below:
hipo@noah:/$ ls -ld root/
drwxr-xr-x 67 root root 4096 Aug 3 12:40 root/
This is quite a big security leak since every user on the system can read and copy all the documents of every other one without any constraint. Users can have read access to the administrator root user !
I have no clear clue why the Debian development team has taken the decision to set such an insecure permissions by default, but anyways it's probably a good practice if you're sane person with a security in mind, should certainly realize that this kind of insecure by default permissions has to be changed for a secure one.
This is probably about to save you tons of nerves of possible security info leak among users or even, security leaks coming out of your home root directory.
Changing the default permissions for the new created users on the system using the adduser command is pretty easy and is being controlled by /etc/adduser.conf
the variable responsible for the persmissons of newly created user directories found within the file is: DIR_MODE by default in Debian this variable is set to be equal to DIR_MODE=0755 which as I've already said is insecure thus a recommandable change value would be: DIR_MODE=750
So procceed and open the vim /etc/adduser.conf and change the DIR_MODE=755 variable to DIR_MODE=0750 there is plenty of more configuration options that you might want to tamper with one worthy to mention is that through the same conf file you're able to specify the range values between which a new created user's ids and gids could borrow.
This can be done via the variables FIRST_SYSTEM_UID LAST_SYSTEM_UID and respectively for GIDS, FIRST_SYSTEM_GID and LAST_SYSTEM_GID
Another thing to do immediately is change your root's directory default set permissions during after your Debian Linux installation is complete, to do so:
debian:~# chmod -R 755 /root
If you're in a position where you have already any number of users existing with alredy created insecure user home directories permissions (755) then a simple (bash shell) one liner to change all the system users permissions to 750 and hence prohibit users to be able to read among each other's directory would be:
debian:~# for i in /home/*; do echo chmod -R 755 $i;
done
The default insecure behaviour that Debian Linux possess as well as the issue discussed above is well documentaed in Securing Debian Manual so check it out for a more thorough info on Debian security.
Mon Aug 2 11:38:14 EEST 2010
How to improve your web browser security - Better securing your personal identity privacy on the Net
Nowadays internet privacy has become
a taboo. Many people do understand how vital is it to protect your
privacy online.
Unfortunately not much has done much in order to improve their state of security whilst on the net.
In this article you're about to find out how trusted and secure is the browsing in the Internet and next to it you will find some possible ways and thoughts how you can improve your personal privacy and the amount of information your browser reveals about your (habits, interestest, and, lifestyle) while surfing online.
There are a lot of private information that can leak through a simple web serarch, let's say you decide to search for some kind of sickness and it's treatment.. just few minutes later the paid advertisement popping up will be showing up targetting ads related to your previous sickness google search.
This is tiny bit of information your browser reveals, however there is much much more. So let me give you a few more examples:
Let's say you visit a website with an Adobe Flash browser player enabled. It's very likely that the website will have flash advertisement this popular this day. If that is the scenario it's very likely that the flash application is built to use тхе so called flash cookies supported.
You might have never heard about flash cookies but anyways this one of cookies are one of the most malicious cookies ever invented.
One of the main reason they're so dubious is the fact THEY NEVER EXPIRE!
Though as with normal cookies flash cookies are used for storing user details, let's say your profile details or settings concerning your youtube video player etc. and this sound nice, market guys use the same features to track what you do online.
Using flash cookies for instance everybody who cratefted a specific adobe flash page is able to list your flash cookies stored browser history!
To partly setup the behaviour of your Flash player and change the defailt flash player settings for good use the flashplayer settings manager
It's really odd that the only way to configure flash is to configure it via adobe's webpage this is much sneaky since, God only knows what kind of information as well probably your whole flash browser history and flash cookies is being sent Adobe for later analysis.
Moreover the flash player is a propriatary software and this makes it even more likely to have included some extra spying software and stuff alike ..
To see all the stored information by flash about a websites you have visited check out:
flashplayer settings manager
Honestly I was quite shocked when I saw many websites I have visited for the rest 1.5+ year listed.
From hence since we know how "evil" flash storage manager cookies are, one sure step to increase your browser privacy is to periodically get rid of Flash Storage (Flash Cookies).
To achieve periodical flash cookies wipe out on Linux, below I provide you with a tiny .tcsh script which is tested and is working on Debian and Ubuntu. Get rid of Local Flash Storage shell script for Linux
(Stores data of the websites you have visited using your browser flash player)
To check your general Browser security The Electronic Frontier Foundation has developed a special website to test your browser anonymity visit penoptickclick.eff.org and click the > TEST ME button
In my case all my installed browser plugins were listed as well many information related to what kind of browser I use the version on the architecture I'm running on etc. etc.
Thereafter navigate to about:config and set the variable dom.storage.enabled to false . This will completely disable the DOM cookies which by the way never expire!
DOM cookies aren't so widely used yet but still it's possible that some websites online has stareted using them, since they're completely junky and bad designed for instance DOM a cookie can contant up to (100KB) of information. then it's best that you disable them completely.
Another recommendable thing to disable on your Iceweasel / Firefox that will tighten up your security is the keyword.enabled variable click twice on it and assure yourself it reads false
Disabling it will prevent the google word suggest to appear each time you type something in Google search box, albeit not every character you type will be sent to Google.
Also a really nice worthy reading is the article explaining dom cookies
Take some time and read it to get a better idea on DOM cookies what they are and why you don't want them.
Likewise take a look at Flash Cookie Forensics for a bit more insight on the flash cookies
After reading the article about flash cookies, I came to the conclusion that maybe it's best that they're completely enabled. Anyways if they're disabled then many websites won't work properly which is something we don't want.
It's rather strange that the only available way to control your flash and disable the flash cookies is via Flashplayer Web Based Setting Manager
Since it's "Web Based Manager" and it is hosted on Adobe's web site this probably means that everything you do through it gets logged by Adobe, not so nice (neither secure) heh ..
It's recommended also to install and configure the following list of extra Firefox plugins to ensure a bit more Anonimity while surfing on the Internet.
Now configure AdBlock plus to work with EasyPrivacy+EasyList (by default it works only with EasyList).
To subscribe for ABP EasyPrivacy click here
BeeFree Mozilla Addon .
Is under the GNU GPL license and it helps you defend a bit more your privacy. It's advantage use is to prevent search engines from knowing which links from their search results is most probably for you to check. Looks like a promising and great stuff
It is said in the add-on website that as a side effect of using the plugin it will probably increase your browser speed.
This post has highly adopted information from the Bulgarian Article by Anton Zinoviev, 2010 About your web browser and the inviolability of your personal life
Big thanks to Anton Zinoviev for the time and effort taken to research on the topic of browser security and write this wonderful thoroughful article.
To configure the BeeFree Firefox security tightening browser addon you will have to type in your browser URL address bar once again
about:config
Now you will have to look up for the following browser config keys:
extensions.beefree.websites.default.header.accept-charset.action
a
Set it's value to be 2 e.g. extensions.beefree.websites.default.header.accept-charset.action = 2
Now look for the key value extensions.beefree.websites.default.header.accept-charset.value.text and set it's value to:
*/*
Changing the extensions.beefree.websites.default.header.accept-charset.action = */* will make BeeFree compatible to some securing anti spam programs.
Last thing to do to complete the BeeFree configuration create the key value extensions.beefree.website.generic.header.useragent.action
To create this one press on a random key the last mouse button and select New -> Integer
The value for the newly created extensions.beefree.website.generic.header.useragent.action should be set to 4
Creating this key will instruct beefree to protect your browser from revealing it's browser version variable.
Interesting to say each restart of the browser will make BeeFree to select a random Firefox Linux or Windows version, dependant of the OS type you use.
The AntiSocial addon will prevent your browser from revealing information to Facebook about your personal interests. It blocks the facebook elements which are being embedded to your browser by some websites.
No FB Tracking stops facebook of keeping an eye on you through the buttons "I like". Using this buttons facebook can track you even if you're not logged in or registered in the social network.
Installing all this plugins would take you time but considering the privacy is invaluable time shouldn't be a concern of you.
Also some of the plugins like NoScript make take some time until you're used to it but it's worth to learn using it.
BetterPrivacy is able and will delete all flash cookies when your browser exits, this will prevent that some sites pry on you through the shitty flash cookies technology, this type of cookies NEVER EXPIRE! Hard to swallow but a fact ...
In Linux this plugin is reported to work correctly however, in Windows there are dubious reports about it.
This is just a brief overview about how to improve your browsing privacy and therefore general personal data security, there is plenty much already red and said on topic, however I hope this could be some kind of basis for my dear reader for a later research on the topic.
Unfortunately not much has done much in order to improve their state of security whilst on the net.
In this article you're about to find out how trusted and secure is the browsing in the Internet and next to it you will find some possible ways and thoughts how you can improve your personal privacy and the amount of information your browser reveals about your (habits, interestest, and, lifestyle) while surfing online.
There are a lot of private information that can leak through a simple web serarch, let's say you decide to search for some kind of sickness and it's treatment.. just few minutes later the paid advertisement popping up will be showing up targetting ads related to your previous sickness google search.
This is tiny bit of information your browser reveals, however there is much much more. So let me give you a few more examples:
Let's say you visit a website with an Adobe Flash browser player enabled. It's very likely that the website will have flash advertisement this popular this day. If that is the scenario it's very likely that the flash application is built to use тхе so called flash cookies supported.
You might have never heard about flash cookies but anyways this one of cookies are one of the most malicious cookies ever invented.
One of the main reason they're so dubious is the fact THEY NEVER EXPIRE!
Though as with normal cookies flash cookies are used for storing user details, let's say your profile details or settings concerning your youtube video player etc. and this sound nice, market guys use the same features to track what you do online.
Using flash cookies for instance everybody who cratefted a specific adobe flash page is able to list your flash cookies stored browser history!
To partly setup the behaviour of your Flash player and change the defailt flash player settings for good use the flashplayer settings manager
It's really odd that the only way to configure flash is to configure it via adobe's webpage this is much sneaky since, God only knows what kind of information as well probably your whole flash browser history and flash cookies is being sent Adobe for later analysis.
Moreover the flash player is a propriatary software and this makes it even more likely to have included some extra spying software and stuff alike ..
To see all the stored information by flash about a websites you have visited check out:
flashplayer settings manager
Honestly I was quite shocked when I saw many websites I have visited for the rest 1.5+ year listed.
From hence since we know how "evil" flash storage manager cookies are, one sure step to increase your browser privacy is to periodically get rid of Flash Storage (Flash Cookies).
To achieve periodical flash cookies wipe out on Linux, below I provide you with a tiny .tcsh script which is tested and is working on Debian and Ubuntu. Get rid of Local Flash Storage shell script for Linux
(Stores data of the websites you have visited using your browser flash player)
To check your general Browser security The Electronic Frontier Foundation has developed a special website to test your browser anonymity visit penoptickclick.eff.org and click the > TEST ME button
In my case all my installed browser plugins were listed as well many information related to what kind of browser I use the version on the architecture I'm running on etc. etc.
Thereafter navigate to about:config and set the variable dom.storage.enabled to false . This will completely disable the DOM cookies which by the way never expire!
DOM cookies aren't so widely used yet but still it's possible that some websites online has stareted using them, since they're completely junky and bad designed for instance DOM a cookie can contant up to (100KB) of information. then it's best that you disable them completely.
Another recommendable thing to disable on your Iceweasel / Firefox that will tighten up your security is the keyword.enabled variable click twice on it and assure yourself it reads false
Disabling it will prevent the google word suggest to appear each time you type something in Google search box, albeit not every character you type will be sent to Google.
Also a really nice worthy reading is the article explaining dom cookies
Take some time and read it to get a better idea on DOM cookies what they are and why you don't want them.
Likewise take a look at Flash Cookie Forensics for a bit more insight on the flash cookies
After reading the article about flash cookies, I came to the conclusion that maybe it's best that they're completely enabled. Anyways if they're disabled then many websites won't work properly which is something we don't want.
It's rather strange that the only available way to control your flash and disable the flash cookies is via Flashplayer Web Based Setting Manager
Since it's "Web Based Manager" and it is hosted on Adobe's web site this probably means that everything you do through it gets logged by Adobe, not so nice (neither secure) heh ..
It's recommended also to install and configure the following list of extra Firefox plugins to ensure a bit more Anonimity while surfing on the Internet.
- Adblock Plus
- AntiSocial
- BeeFree
- Beef Taco
- BetterPrivacy
- DownloadHelper
- Download Statusbar
- Live HTTP Headers
- No FB Tracking
- NoScript
- RefControl
Now configure AdBlock plus to work with EasyPrivacy+EasyList (by default it works only with EasyList).
To subscribe for ABP EasyPrivacy click here
BeeFree Mozilla Addon .
Is under the GNU GPL license and it helps you defend a bit more your privacy. It's advantage use is to prevent search engines from knowing which links from their search results is most probably for you to check. Looks like a promising and great stuff
It is said in the add-on website that as a side effect of using the plugin it will probably increase your browser speed.
This post has highly adopted information from the Bulgarian Article by Anton Zinoviev, 2010 About your web browser and the inviolability of your personal life
Big thanks to Anton Zinoviev for the time and effort taken to research on the topic of browser security and write this wonderful thoroughful article.
To configure the BeeFree Firefox security tightening browser addon you will have to type in your browser URL address bar once again
about:config
Now you will have to look up for the following browser config keys:
extensions.beefree.websites.default.header.accept-charset.action
a
Set it's value to be 2 e.g. extensions.beefree.websites.default.header.accept-charset.action = 2
Now look for the key value extensions.beefree.websites.default.header.accept-charset.value.text and set it's value to:
*/*
Changing the extensions.beefree.websites.default.header.accept-charset.action = */* will make BeeFree compatible to some securing anti spam programs.
Last thing to do to complete the BeeFree configuration create the key value extensions.beefree.website.generic.header.useragent.action
To create this one press on a random key the last mouse button and select New -> Integer
The value for the newly created extensions.beefree.website.generic.header.useragent.action should be set to 4
Creating this key will instruct beefree to protect your browser from revealing it's browser version variable.
Interesting to say each restart of the browser will make BeeFree to select a random Firefox Linux or Windows version, dependant of the OS type you use.
The AntiSocial addon will prevent your browser from revealing information to Facebook about your personal interests. It blocks the facebook elements which are being embedded to your browser by some websites.
No FB Tracking stops facebook of keeping an eye on you through the buttons "I like". Using this buttons facebook can track you even if you're not logged in or registered in the social network.
Installing all this plugins would take you time but considering the privacy is invaluable time shouldn't be a concern of you.
Also some of the plugins like NoScript make take some time until you're used to it but it's worth to learn using it.
BetterPrivacy is able and will delete all flash cookies when your browser exits, this will prevent that some sites pry on you through the shitty flash cookies technology, this type of cookies NEVER EXPIRE! Hard to swallow but a fact ...
In Linux this plugin is reported to work correctly however, in Windows there are dubious reports about it.
This is just a brief overview about how to improve your browsing privacy and therefore general personal data security, there is plenty much already red and said on topic, however I hope this could be some kind of basis for my dear reader for a later research on the topic.