
As a GNU / Linux user you might end up searching for the best email client to satisfy your needs, for those who used so far Outlook Express on M$ Windows first switch to GNU / Linux the most likely one to choose is either Mozilla Thunderbird or GNOME's Evolution default Mail Clientbut what more text / console programs are there that will allow you to easily check email via POP3 and IMAP on Linux?
1. Install Fetchmail and use to collect and copy your emails from remote server to your local machine
SSL enabled POP3, APOP, IMAP mail gatherer/forwarder
fetchmail is a free, full-featured, robust, and well-documented remote mail
retrieval and forwarding utility intended to be used over on-demand TCP/IP
links (such as SLIP or PPP connections). It retrieves mail from remote mail
servers and forwards it to your local (client) machine's delivery system, so
it can then be read by normal mail user agents such as mutt, elm, pine,
(x)emacs/gnus, or mailx. The fetchmailconf package includes an interactive
GUI configurator suitable for end-users.
To install it, issue:
apt-get install –yes fetchmail procmail
To configure fetchmail to gather your mail from your POP3 / IMAP mailbox, create below
.fetchmailrc configuratoin and modify according to your account
# vim .fetchmailrc
#### .fetchmailrc
set daemon 600
set logfile fetchmail.logpoll the_mail_server_hostname proto POP3
user "Remote_Username" pass "PASSWORD=" is "local_username" preconnect "date >> fetchmail.log"
#ssl
fetchall
#no keep
no rewrite
mda "/usr/bin/procmail -f %F -d %T";
Here is also few words on each of the .fetchmailrc config options
set daemon 600 The fetchmail binary with run in the background in daemon mod and fetch mail from the server every 600 seconds or 10 minutes.
set logfile fetchmail.log This will set the directory and file name of the fetchmail user log file. Eveytime fetchmail recieves an email, checks the pop3 server or errors out you will find an entry here.
poll the_isp_mail_server proto POP3 This line tells fetchmail what mail server to contact, in theis case "the_isp_mail_server" and to use the "POP3" protocol.
user "remote_user_name" pass "PASSWORD" is "local_username" preconnect "date >> fetchmail.log The user directive tells fetchmail what the name of the user on the remote mail server is for example "remote_user_name". The pass directive is simply the password you will use for the remote user on the mail server. The "is" directive is optional. It tells fetchmail to deliver mail to a diferent user name if the user on the remote mail server and the local machine are different. For example, I may be using the name "joe.doe" on the mail server, but my local user name is "jdoe". I would use a line like user "joe.doe" pass "PASSWORD" is "jdoe". The preconnect command simply adds the current time and date to the fetchmail log file every time fetchmail checks for new mail.
ssl The "ssl" directive tells fetchmail to use encryption when connecting to the pop3 mail server. Fetchmail will use port 995 instead of port 110 for un-encypted mail communication. In order to use ssl the remote mail server must be able to use ssl. Comment out this directive if you do _not_ use pop3s.
fetchall Fetchall just means to fetch all of the mail on the mail server no matter what the "read" flag is. It is possibly to read mail through many different processes. If you use another mail client from another location, for example you could have read you mail and kept it ont he server, but marked it with the "read" flag. At this point if you did _not_ use the "fetchall" flag then only mail marked as new would be downloaded.
no keep Once the mail is downloded from the mail server fetchmail is to tell the server to remove it from the server. You may choose to comment this option out if you want to leave all mail on the server.
no rewrite Do not rewrite headers. When fetchmail recieves the mail you do not want any of the headers mangled in any way. This directive tells fetchmail to leave the headers alone.
mda "/usr/bin/procmail -f %F -d %T"; The mda is your "mail delivery agent. Procmail is the program that fetchmail will hand the mail off to once it is downloaded. The argument "-f %F" logs who the mail if from and "-d %T" turns on explicit delivery mode, delivery will be to the local user recipient.
For configuring multiple mailboxes email to be gathered to local machine through fetchmail add to above configuration, some more config similar to this:
poll mail.example.com protocol pop3:
username "admin" password "your-plain-text-password" is "username" here;
username "what-ever-user-name" password "Just-another-pass#" is "foreman" here;poll mail.example.org protocol pop3 with option sslproto '':
user "whatever-user1" password "its-my-pass" mda "/usr/bin/procmail -d %T": user "whatever-user1" password "its-my-pass" mda "/usr/bin/procmail -d %T
Because as you can see fetchmail keeps password in plaintext it is a best security practice to set some good file permissions on .fetchmailrc just to make sure some other local user on the same Linux / Unix machine will not be able to read your plaintext password, to do so issue below command.
chmod 600 ~/.fetchmailrc
For the purpose of logging as we have it into the config you will also need to create new blank file fetchmail.log
touch fetchmail.log
Once fetchmail all your emails you can use mail command to view your messages or further configure alpine or mutt to read the downloaded messages.
2. Use Alpine text based email client to check your downloaded email with fetchmail
Alpine is Text-based email client, friendly for novices but powerful
Alpine is an upgrade of the well-known PINE email client. Its name derives
from the use of the Apache License and its ties to PINE.
In other words what Alpine is it is a rewritten and improved version of the good old PINE Unix email client (for those who remember it).
To give alpine a try on Debian / Ubuntu install it with:
apt-get install –yes alpine pilot
3. Use MuTT advanced and much more colorful text email client to view your emailbox

Mutt is a sophisticated text-based Mail User Agent. Some highlights:
.
* MIME support (including RFC1522 encoding/decoding of 8-bit message
headers and UTF-8 support).
* PGP/MIME support (RFC 2015).
* Advanced IMAP client supporting SSL encryption and SASL authentication.
* POP3 support.
* ESMTP support.
* Message threading (both strict and non-strict).
* Keybindings are configurable, default keybindings are much like ELM;
Mush and PINE-like ones are provided as examples.
* Handles MMDF, MH and Maildir in addition to regular mbox format.
* Messages may be (indefinitely) postponed.
* Colour support.
* Highly configurable through easy but powerful rc file.
To install MuTT:
linux:~# apt-get install –yes mutt
Configuring mutt if you don't have priorly set-up with fetchmail to collect your remote e-mails, you might want to try out .mutt's email fetch features to do so you will need a .muttrc configuration like that:
# Automatically log in to this mailbox at startup
set spoolfile="imaps://User_Name:Your-Secret-Password@mail.example.com/"
# Define the = shortcut, and the entry point for the folder browser (c?)
set folder="imaps://mail.example.com/"
set record="=Sent"
set postponed="=Drafts"
You might also omit placing the password inside .muttrc configuration as storing the password in plaintext might be a big security hole if someone is able to read it at certain point, but the downside of that is you'll be asked by mutt to fill in your email password on every login which at a point becomes pretty annoying.
If you face problems with inability of mutt to connect to remote mail server due to TLS problems, you can also try to play with below configurations:
# activate TLS if available on the server
set ssl_starttls=yes
# always use SSL when connecting to a server
set ssl_force_tls=yes
# Don't wait to enter mailbox manually
unset imap_passive
# Automatically poll subscribed mailboxes for new mail (new in 1.5.11)
set imap_check_subscribed
# Reduce polling frequency to a sane level
set mail_check=60
# And poll the current mailbox more often (not needed with IDLE in post 1.5.11)
set timeout=10
# keep a cache of headers for faster loading (1.5.9+?)
set header_cache=~/.hcache
# Display download progress every 5K
set net_inc=5
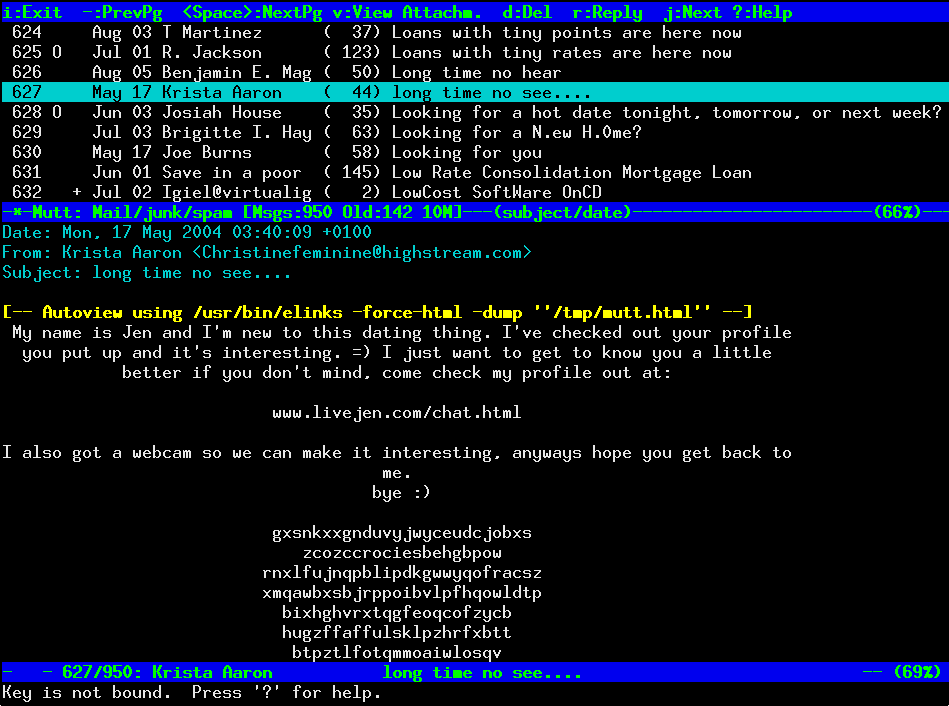
Once you have the emails downloaded with fetchmail for your mailbox mutt should be showing your email stuff like in below screenshot
linux:~$ mutt
Of course a very handy thing to have is w3m-img text browser that displays images as it might be able to open your pictures attached to email if you're on a physical console tty.
I'll be curious to hear, if you know of better and easier solutions to check mail in console, so if you know such please drop a comment explaining how you check your mail text.




