
Say you're using Tivoli TSM to manage your backups for tsm (if you don't know what is IBM TSM (Spectrum Protect) Backup solution check my previous article on how to use IBM Tivoli to list configured, scheduled, how to do restore backups with dsmc console client.
And you follow below steps to enable SSL communication with a CA-signed certificate between Spectrum Protect client and server:
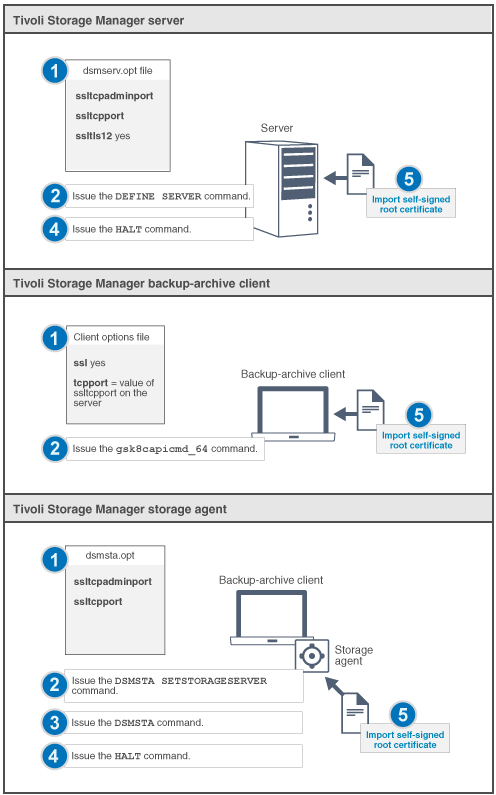
E.g. you have to
- Obtained the CA root certificate.
- Configure the clients. To use SSL, each client must import the self-signed server certificate.
Used the GSKit command-line utility (gsk8capicmd for 32-bit clients or gsk8capicmd_64 for 64-bit clients) to import the certificate.
1. The problem
This self-signed certificates has expire date which after some time might have expire date coming. If your environment has something like PCI security standards enabled and you do a Quarterly security scans with something like QualysGuard (Qaulys vulnerability management tool).
In the case of Qualys scans you may receive GSK messages in dsmerro.log if the certificate is expiring:
03/04/2021 14:35:07 ANS9959W IBM Spectrum Protect acceptor received a non-critical network error 88, IBM Spectrum Protect return code : -50.
03/05/2021 13:04:59 ANS1579E GSKit function gsk_secure_soc_init failed with 414: GSK_ERROR_BAD_CERT
03/05/2021 13:04:59 TCP/IP received rc 88 trying to accept connection from server.
03/05/2021 13:04:59 ANS9959W IBM Spectrum Protect acceptor received a non-critical network error 88, IBM Spectrum Protect return code : -50.
2. To check the situation on the host with TSM self-signed expiry
2.1 First get the FQDN and certificate name
[root@redhat: ~ ]# FQDN=$(hostname –fqdn |tr '[:lower:]’ ‘[:upper:]');
[root@redhat: ~ ]# echo "FQDN to be used is: $FQDN. Please be careful it is correct (if machine has wrong FQDN) you might have issues";
[root@redhat: ~ ]# gsk8capicmd_64 -cert -list -db /etc/adsm/Nodes/$FQDN/spclicert.kdb -stashed
The gsk8capicmd_64 is IBM's tool to view and manage SSL certificates it is perhaps a C written binary that has a compiled patched version of a normal openssl tool. Using it is the ibm recommended way to manage Tivoli certificates.
2.2 Get details using -label=CERTNAME and check for expiration date
[root@redhat: ~ ]# gsk8capicmd_64 -cert -details -label $FQDN -db /etc/adsm/Nodes/$FQDN/spclicert.kdb -stashed
Certificates found
* default, – personal, ! trusted, # secret key
– FQDN-OF-HOST.COM
3. To update the certificates
3.1 Copy the old certificates for backup
As usual do a backup in case if something goes wrong and you need to restore
[root@redhat: ~ ]# mkdir /root/certbck-tsm_$(date +"%b-%d-%Y")/
[root@redhat: ~ ]# cp -rpv /etc/adsm/Nodes/$FQDN/spclicert* /root/certbck-tsm_$(date +"%b-%d-%Y")/
3.2 Stop the dsmcad backup service
[root@redhat: ~ ]# systemctl stop dsmcad
Double check the service is stopped by checking for any remain dsm processes
[root@redhat: ~ ]# ps axf | grep dsm
3.3 Remove the expiring certificates from host
[root@redhat: ~ ]# rm -v /etc/adsm/Nodes/$FQDN/spclicert*
3.4 Generate new certificates with dsmc client
[root@redhat: ~ ]# dsmc query session -optfile="/opt/tivoli/tsm/client/ba/bin/dsm.opt"
3.5 Check if all is generated as expected
[root@redhat: ~ ]# ls -l /etc/adsm/Nodes/$FQDN/spclicert*
3.6 Start the backup service
[root@redhat: ~ ]# systemctl start dsmcad
3.7 Check /var/tsm/dsmwebcl.log for the port number of webclient
[root@redhat: ~ ]# cat /var/tsm/dsmwebcl.log
03/16/2021 13:31:41 (dsmcad) ————————————————————
03/16/2021 13:31:41 (dsmcad) Command will be executed in 11 hours and 50 minutes.
03/16/2021 15:56:01 (dsmcad) ANS9959W IBM Spectrum Protect acceptor received a non-critical network error 88, IBM Spectrum Protect return code : -50.
03/17/2021 01:21:41 (dsmcad) Executing scheduled command now.
03/17/2021 01:22:53 (dsmcad) Next operation scheduled:
03/17/2021 01:22:53 (dsmcad) ————————————————————
03/17/2021 01:22:53 (dsmcad) Schedule Name: 0120_SCHED_P
03/17/2021 01:22:53 (dsmcad) Action: Incremental
03/17/2021 01:22:53 (dsmcad) Objects:
03/17/2021 01:22:53 (dsmcad) Options: -subdir=yes
03/17/2021 01:22:53 (dsmcad) Server Window Start: 01:20:00 on 03/18/2021
03/17/2021 01:22:53 (dsmcad) ————————————————————
03/17/2021 01:22:53 (dsmcad) Command will be executed in 12 hours.
03/17/2021 13:22:53 (dsmcad) Executing scheduled command now.
03/17/2021 13:22:54 (dsmcad) Next operation scheduled:
03/17/2021 13:22:54 (dsmcad) ————————————————————
03/17/2021 13:22:54 (dsmcad) Schedule Name: 0120_SCHED_P
03/17/2021 13:22:54 (dsmcad) Action: Incremental
03/17/2021 13:22:54 (dsmcad) Objects:
03/17/2021 13:22:54 (dsmcad) Options: -subdir=yes
03/17/2021 13:22:54 (dsmcad) Server Window Start: 01:20:00 on 03/18/2021
03/17/2021 13:22:54 (dsmcad) ————————————————————…
[root@redhat: ~ ]# grep -i port /var/tsm/dsmwebcl.log
03/11/2021 16:59:19 (dsmcad) ANS3000I TCP/IP communications available on port 37506.
03/12/2021 11:35:21 (dsmcad) ANS3000I TCP/IP communications available on port 40510.
03/12/2021 14:53:03 (dsmcad) ANS3000I TCP/IP communications available on port 45005.
3.8 You can check the certificate expiery mask yourself as qualys scanner and check the new certificate
[root@redhat: ~ ]# dsmc_port=$(netstat -tulpan|grep -i dsm|awk '{ print $4 }'|cut -d":" -f2);
[root@redhat: ~ ]# echo $dsmc_port[root@redhat: ~ ]# openssl s_client -servername 127.0.0.1 -connect 127.0.0.1:$dsmc_port | openssl x509 -noout -dates
notBefore=Mar 6 14:09:55 2021 GMT
notAfter=Mar 7 14:09:55 2022 GMT
Hopefully your expiry date is fine that means you're done, you can place the steps in a single script to save time, if you have to run it in a year time.
More helpful Articles

Tags: Depedent Item, expiring, gsk8capicmd_64, ibm, Spectrum Protect, ssl certificates, Tivoli, TSM, update self-signed client







