If you work in a big company with large network infrastructure who has to deal with SSL Certificates you will sooner or later will have to learn about existence of SSL Certificate Chains.
Its worthy thus to know what is SSL Certificate Chains and how such a chain is configured in Apache?
Personal SSL certificates (certificates issued to an individual or a company) can be used by clients to uniquely identify themselves when they are involved in starting an SSL connection.
SSL Certificate file contains X.509 certificate, which, in turn, contains a public key used for encryption.
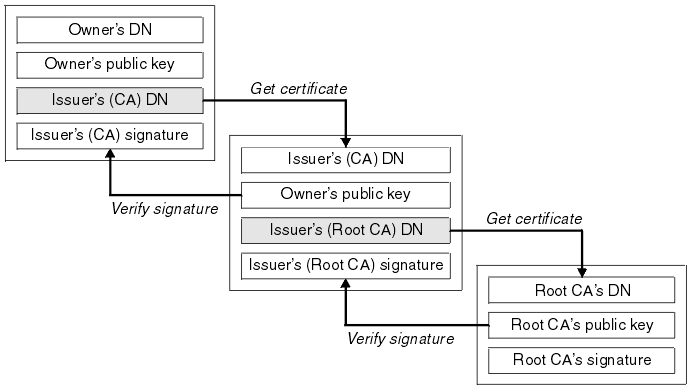
Each personal certificate has zero or more certificate chains of certification authority certificates that extend back to the root certification authority.
Certificate R (Root Certification Authority)
|
| represents issuer of
V
Certificate I1 (Intermediate Certification Authority)
|
| represents issuer of
V
Certificate I2 (A subsidiary Intermediate Certification Authority)
|
| represents issuer of
V
Certificate I3 (A further subsidiary Intermediate Certification Authority)
|
| represents issuer of
V
Certificate P (A personal certificate that is used to identify its owner
on an SSL handshake)Certificate chains are used to verify the authenticity of each certificate in that chain, including the personal certificate. Each certificate in the chain is validated using its 'parent' certificate, which in turn is validated using the next certificate up the chain, and so on, from the personal certificate up to the root certification authority certificate.
Now after explaining thoroughfully what is SSL Certificate Chain, here is how to configure a SSL Certificate in Apache Webserver.
Open apache2.conf or httpd.conf (depending on GNU / Linux distribution) and add to it;
SSLEngine On
SSLCertificateFile conf/cert/webserver-host.crt
SSLCertificateKeyFile conf/cert/webserver-host.key
SSLCertificateChainFile conf/cert/internet-v4.crt
# SSLCertificateChainFile conf/cert/intranet-v3.crt
SSLOptions +StdEnvVars +OptRenegotiate +ExportCertData
SSLCertificateChainFile conf/cert/chain-cert.crt
loads a chain of separate Personal SSL certificates each signing each other on different levels, chain is leading to top ROOT CA (Certificate Authority).
More helpful Articles

Tags: apache, apache2, cert, certificate, Certificate Chain, com, company, conf, configured, deal, existence, httpd, individual, installation, key, parent, root, signing, SSL, webserver, www








Mozilla/5.0 (Windows NT 6.1; WOW64; rv:26.0) Gecko/20100101 Firefox/26.0
Another useful SSL option is SSLVerifyDepth
Through it can be specified how many levels of the certificate chain up should be followed. For example an SSLVerifyDepth 3 means:
| depth 0: the client certificate
| depth 1: the issuer certificate
| depth 2: the issuer’s issuer certificate
| depth 3: the issuer’s issuer’s issuer certificate.
SSLVerifyDepth 0 … a self-signed client cert only is allowed
SSLVerifyDepth 1 … client cert can be signed by a CA, but this has to be the root CA.
SSLVerifyDepth 2 … client cert can be signed by a CA which itself can be
signed by a second CA.
Example of usage of SSLVerifyDepth is below Apache config:
SSLCACertificateFile conf/cert/all.crt
SSLVerifyDepth 3
# For fallback to basic authentication we need optional
SSLVerifyClient optional
ProxyPreserveHost On
View CommentView Comment