Earlier I've blogged about an encounter problem that prevented Active mode FTP connections on CentOS
As I'm working for a client building a brand new dedicated server purchased from Contabo Dedi Host provider on a freshly installed Debian 10 GNU / Linux, I've had to configure a new FTP server, since some time I prefer to use Proftpd instead of VSFTPD because in my opinion it is more lightweight and hence better choice for a small UNIX server setups. During this once again I've encounted the same ACTIVE FTP not working from FTP server to FTP client host machine. But before shortly explaining, the fix I find worthy to explain briefly what is ACTIVE / PASSIVE FTP connection.
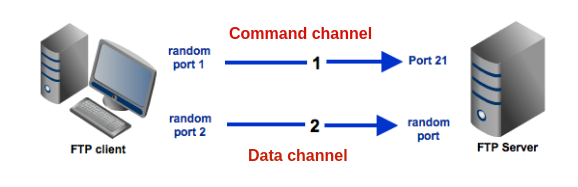
1. What is ACTIVE / PASSIVE FTP connection?
Whether in active mode, the client specifies which client-side port the data channel has been opened and the server starts the connection. Or in other words the default FTP client communication for historical reasons is in ACTIVE MODE. E.g.
Client once connected to Server tells the server to open extra port or ports locally via which the overall FTP data transfer will be occuring. In the early days of networking when FTP protocol was developed security was not of such a big concern and usually Networks did not have firewalls at all and the FTP DATA transfer host machine was running just a single FTP-server and nothing more in this, early days when FTP was not even used over the Internet and FTP DATA transfers happened on local networks, this was not a problem at all.
In passive mode, the server decides which server-side port the client should connect to. Then the client starts the connection to the specified port.
But with the ever increasing complexity of Internet / Networks and the ever tightening firewalls due to viruses and worms that are trying to own and exploit networks creating unnecessery bulk loads this has changed …
2. Installing and configure ProFTPD server Public ServerName
I've installed the server with the common cmd:
apt –yes install proftpd
And the only configuration changed in default configuration file /etc/proftpd/proftpd.conf was
ServerName "Debian"
I do this in new FTP setups for the logical reason to prevent the multiple FTP Vulnerability Scan script kiddie Crawlers to know the exact OS version of the server, so this was changed to:
ServerName "MyServerHostname"
Though this is the bad security through obscurity practice doing so is a good practice.
3. Create iptable firewall rules to allow ACTIVE FTP mode
But anyways, next step was to configure the firewall to be allowed to communicate on TCP PORT 21 and 20 to incoming source ports range 1024:65535 (to enable ACTIVE FTP) on firewal level with iptables on INPUT and OUTPUT chain rules, like this:
iptables -A INPUT -p tcp –sport 1024:65535 -d 0/0 –dport 21 -m state –state NEW,ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp -s 0/0 –sport 1024:65535 -d 0/0 –dport 20 -m state –state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp -s 0/0 –sport 21 -d 0/0 –dport 1024:65535 -m state –state ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp -s 0/0 –sport 20 -d 0/0 –dport 1024:65535 -m state –state ESTABLISHED,RELATED -j ACCEPT
Talking about Active and Passive FTP connections perhaps for novice Linux users it might be worthy to say few words on Active and Passive FTP connections
Once firewall has enabled FTP Active / Passive connections is on and FTP server is listening, to test all is properly configured check iptable rules and FTP listener:
/sbin/iptables -L INPUT |grep ftp
ACCEPT tcp — anywhere anywhere tcp spts:1024:65535 dpt:ftp state NEW,ESTABLISHED
ACCEPT tcp — anywhere anywhere tcp spts:1024:65535 dpt:ftp-data state NEW,ESTABLISHED
ACCEPT tcp — anywhere anywhere tcp dpt:ftp
ACCEPT tcp — anywhere anywhere tcp dpt:ftp-data
netstat -l | grep "ftp"
tcp6 0 0 [::]:ftp [::]:* LISTEN
4. Loading nf_nat_ftp module and net.netfilter.nf_conntrack_helper (for backward compitability)
Next step of course was to add the necessery modules nf_nat_ftp nf_conntrack_sane that makes FTP to properly forward ports with respective Firewall states on any of above source ports which are usually allowed by firewalls, note that the range of ports given 1024:65535 might be too much liberal for paranoid sysadmins and in many cases if ports are not filtered, if you are a security freak you can use some smaller range such as 60000-65535.
Here is time to say for sysadmins who haven't recently had a task to configure a new (unecrypted) File Transfer Server as today Secure FTP is almost alltime used for file transfers for the sake of security might be puzzled to find out the old Linux kernel ip_conntrack_ftp which was the standard module used to make FTP Active connections work is substituted nowadays with nf_nat_ftp and nf_conntrack_sane.
To make the 2 modules permanently loaded on next boot on Debian Linux they have to be added to /etc/modules
Here is how sample /etc/modules that loads the modules on next system boot looks like
cat /etc/modules
# /etc/modules: kernel modules to load at boot time.
#
# This file contains the names of kernel modules that should be loaded
# at boot time, one per line. Lines beginning with "#" are ignored.
softdog
nf_nat_ftp
nf_conntrack_sane
Next to say is that in newer Linux kernels 3.x / 4.x / 5.x the nf_nat_ftp and nf_conntrack-sane behaviour changed so simply loading the modules would not work and if you do the stupidity to test it with some FTP client (I used gFTP / ncftp from my Linux desktop ) you are about to get FTP No route to host errors like:
Cannot create a data connection: No route to host
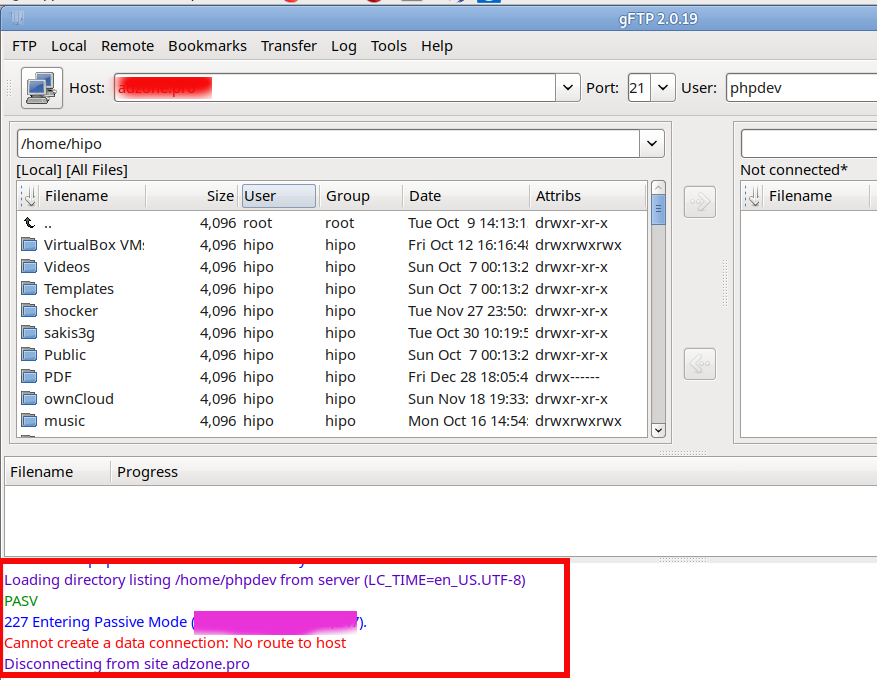
Sometimes, instead of No route to host error the error FTP client might return is:
227 entering passive mode FTP connect connection timed out error
To make the nf_nat_ftp module on newer Linux kernels hence you have to enable backwards compatibility Kernel variable
/proc/sys/net/netfilter/nf_conntrack_helper
echo 1 > /proc/sys/net/netfilter/nf_conntrack_helper
To make it permanent if you have enabled /etc/rc.local legacy one single file boot place as I do on servers – for how to enable rc.local on newer Linuxes check here
or alternatively add it to load via sysctl
sysctl -w net.netfilter.nf_conntrack_helper=1
And to make change permanent (e.g. be loaded on next boot)
echo 'net.netfilter.nf_conntrack_helper=1' >> /etc/sysctl.conf
5. Enable PassivePorts in ProFTPD or PassivePortRange in PureFTPD
Last but not least open /etc/proftpd/proftpd.conf find PassivePorts config value (commented by default) and besides it add the following line:
PassivePorts 60000 65534
Just for information if instead of ProFTPd you experience the error on PureFTPD the configuration value to set in /etc/pure-ftpd.conf is:
PassivePortRange 30000 35000
That's all folks, give the ncftp / lftp / filezilla or whatever FTP client you prefer and test it the FTP client should be able to talk as expected to remote server in ACTIVE FTP mode (and the auto passive mode) will be not triggered anymore, nor you will get a strange errors and failure to connect in FTP clients as gftp.
Cheers 🙂