I had been assigned the not easy task to make a Windows XP Pro which is located behind an ADSL modem to be remotely accessible via VNC
The Windows is connected to the Bulgarian Vivacom Intrnet provider through their ADSL service and hence there is an ADSL router modem which is configured to disallow all inbuond connections by default.
The Windows Pro PC where the VNC server was needed to be accessible did not have a real IP address (e.g. was assigned a virtual IP address by the ADSL modem.
The exact ADSL model used to connect the computer via a lan cable to the internet was Huawei SmartAX MT882
As the device is owned by Vivacom (the ex BTK tele communication company) I did not have any admin user and pass credentials for the ADSL modem to configure the ADSL router to do a port NAT forwarding of port 5800 and 5900 used by the VNC software I installed on the PC (TightVNC)
Nevertheless the missing user and password I decided to check in google if I can find some default passwords that Vivacom ADSL modems are configured to work with
After a few minutes spend in Google I already had found few passwords which were said to work fine with the Vivacom ADSL router.
Here are the passwords I found for the Vivacom ADSL Internet modems:
ZTE ZXDSL 832
username: root
password:GSrootaccess
ZTE ZXDSL 831
username:root
password:GSrootaccess
ZTE
username:root
password:831access
Huawei SmartAX MT882
username:root
password:MT882rootaccess
ZTE ZXDSL-531b
username: root
password:warmWLspot
I tried some old school brute force techniques 😉 by trying all the passwords via the ADSL web interface located on http://192.168.1.1 (I was not sure which model the Vivacom ADSL modem is as on the router there was nothing written concerning the modem type but only the Vivacom logo was present.
After a bit of time I already knew that the ADSL modem model, user and pass was:
Huawei SmartAX MT882
-------------------------------
user: root
pass: MT882rootaccess
My next step was to configure port forwarding for the SmartAX MT882 ADSL in order to achieve from modem’s web administrator I had to follow the menus:
Advanced Setup -> Virtual Servers
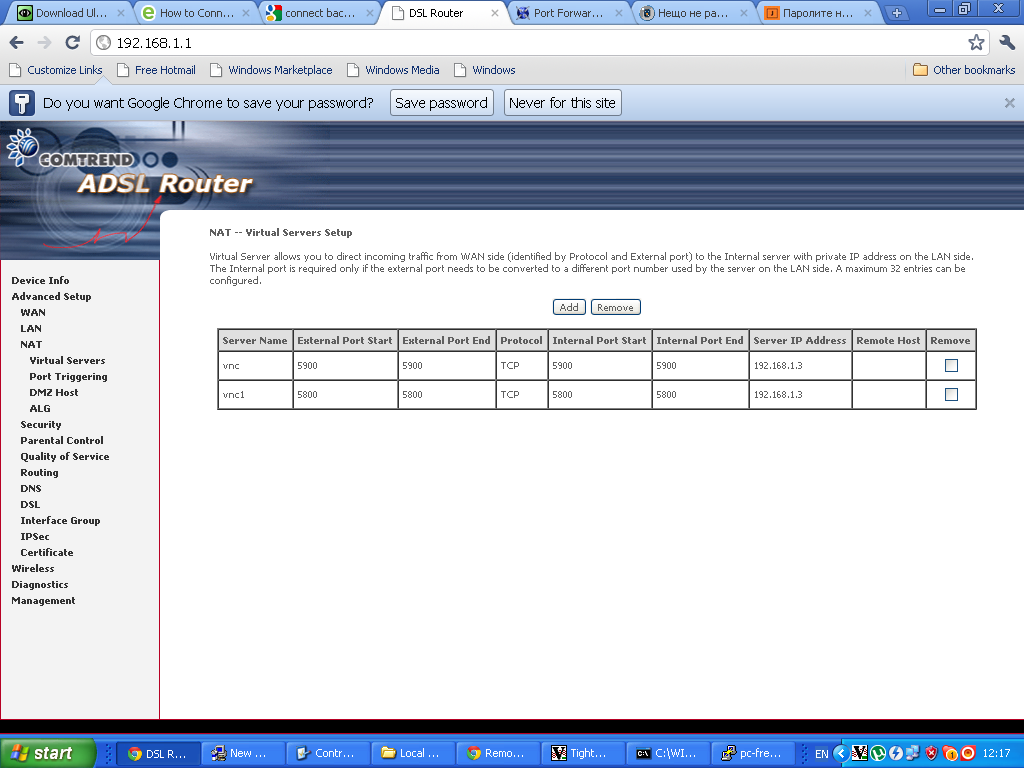
Next in the NAT — Virtual Servers section I pressed the Add button to create new automatic redirection (port forwarding) rule.
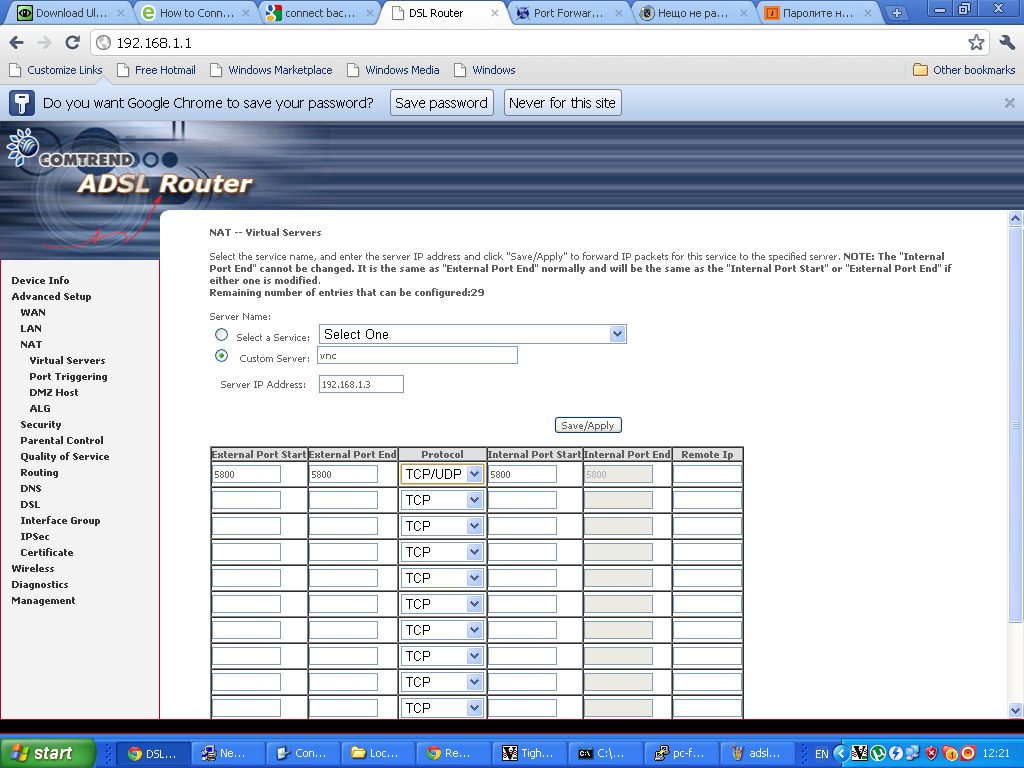 Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.
Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.
Note that the private IP address of the Windows host was assigned by the ADSL router to the ip 192.168.1.3
Further on I expected the adsl port forwarding created rule would now allow me to connect to the VNC server on the pc located behind the dsl firewall, but I was wrong… even though all seemed to be configured just fine in the ADSL router still the port unmbers 5800 and 5900 were showing up as closed during nmap scan as well as a simple telnet connection to port 5800 and 5900 failed to get established.
My logical assumption was that some configured Firewall on the Windows PC is blocking port connections to 5800 and 5900 thus I decided to check the default Windows Firewall settings as a first possible cause for the vnc ports being blocked.
I did that via the Windows menus:
Start -> Settings -> Control Panel -> Windows Firewall
However weirly enought it seemed the Windows Firewall was disabled e.g. the Off (not recommended) option was set for the firewall.
A bunch of other lookup over all the running system and services on the windows hosts I have found the PC is protected by NOD32 Antivirus – Personal Firewall
The default behaviour of NOD32’s Persnal firewall was extremely restrictive and I found it’s causing a port filter of the 5800 and 5900 vnc connection ports.
To solve the filtering nod32 did I had to open NOD32 and navigate to the following menus:
Setup -> Personal Firewall -> Configure rules and Zones
In the Zone and rule setup menu config window I had to further press on:
New button to add new personal firewall rule.
In the New rule: menu I filled in the following info:
In the General tab:
Name: vnc
Direction: Both
Action: Allow
In the tab Local
I pressed over the Add Port
Number: 5800
in the Remote tab once again I had to fill in:
Number: 5800
Then to confirm settings just pressed OK
Next on I added in the same manner an allow rule for port 5900.
After this settings I restarted the NOD32 firewall to make sure the new settings takes place by pressing over the Personal firewall button Disable filtering: allow all traffic and right after enabling the firewall once again.
Now remote tightvnc connections to the Windows XP Pro pc works like a charm once again, Thanks God 😉

 Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.
Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.




