As an administrator of few company email delivery servers, I always had to debug problems related to emails unable to drop in Yahoo’s Mail and Gmail default mail Inbox
In that reason I always need to take a close look on Email headers to try to isolate email issues.
Most often the problems with messages unable to deliver in default in Inbox are with the 3 most popular mail services:
- Gmail
- Live Hotmail
- Yahoo
Thus I decided to explain shortly here how one can check full email headers in Gmail and Yahoo public mail services in order to be able to later derive conclusions on what is wrong with his mail server outgoing messages.
1. How to view full email headers in Gmail
It’s pretty easy, though for some reason Google decided to place the button which shows the complete email message headers in a I would say not too user friendly location.
To view email headers, login to Gmail, click over some random email in Inbox or some of the other mail folders.
Once you can read the email and you see the Reply button located on the right,next to the Reply button there is the down triangle which while pressed will display a menu.
To view the full email headers one has to press over the Show original button presented in the menu. Below you see a sample screenshot on the menu with the Show Original button.
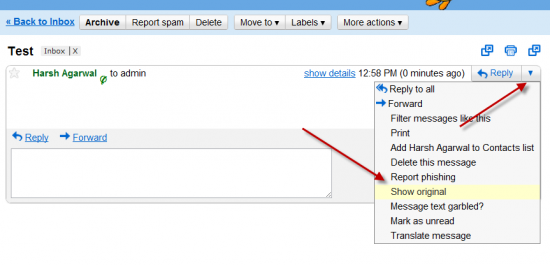
Show complete e-mail message headers and content in Gmail
2. How to view full email headers in Yahoo Mail Classic
I use Yahoo Mail Classic, as I like old stuff, Checking the full email headers there is a bit more intuitive than with Gmail.
To check email headers, just login to Yahoo mail, click over inbox, select an email message you would like to review as text.
Further on after the end of the email, you will see the Delete, Reply, Forward, Spam and Move buttons, right below this field of buttons there is the Full Headers blue text link with very small letters.
Here is a screenshot I’ve made of a sample opened mail. On the screenshot in right bottom you see the blue Full Headers button.
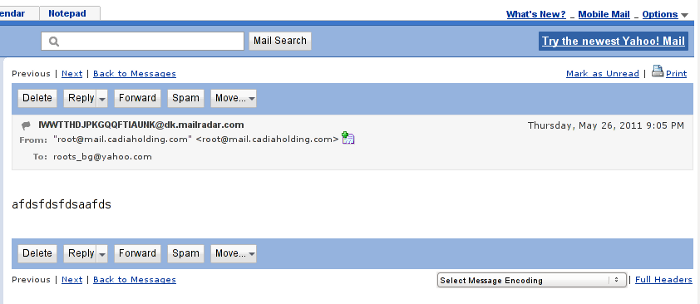
Yahoo Mail Cassic View Email Full Header
3. How to view full mail headers in Hotmail
In Hotmail checking the email, headers’s button position is very similar to Gmail’s, the only difference is the exact button which shows the Full Email header is named View Message source
In order to check Email headers in Hotmail, one has to click over a desired message, click once again on the down triangle near the Reply button and press over View Message source
Here is a screenshot showing the View Message source menu
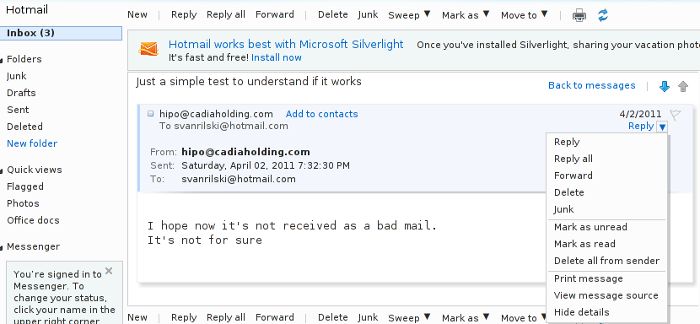
Hotmail View Full email Headers
One small note to make here is that the View source headers buttons is currently not working on Epiphany browser running on Linux.
As always Microsoft are making stuff incompatible, if it’s not used with a Microsoft product ..
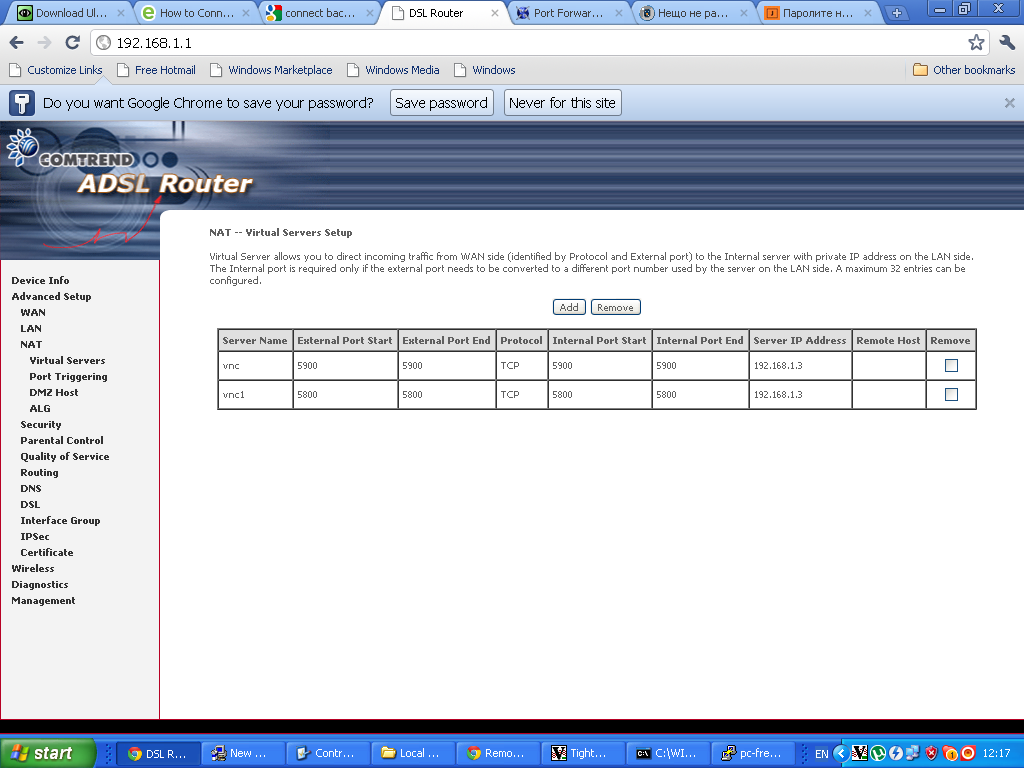
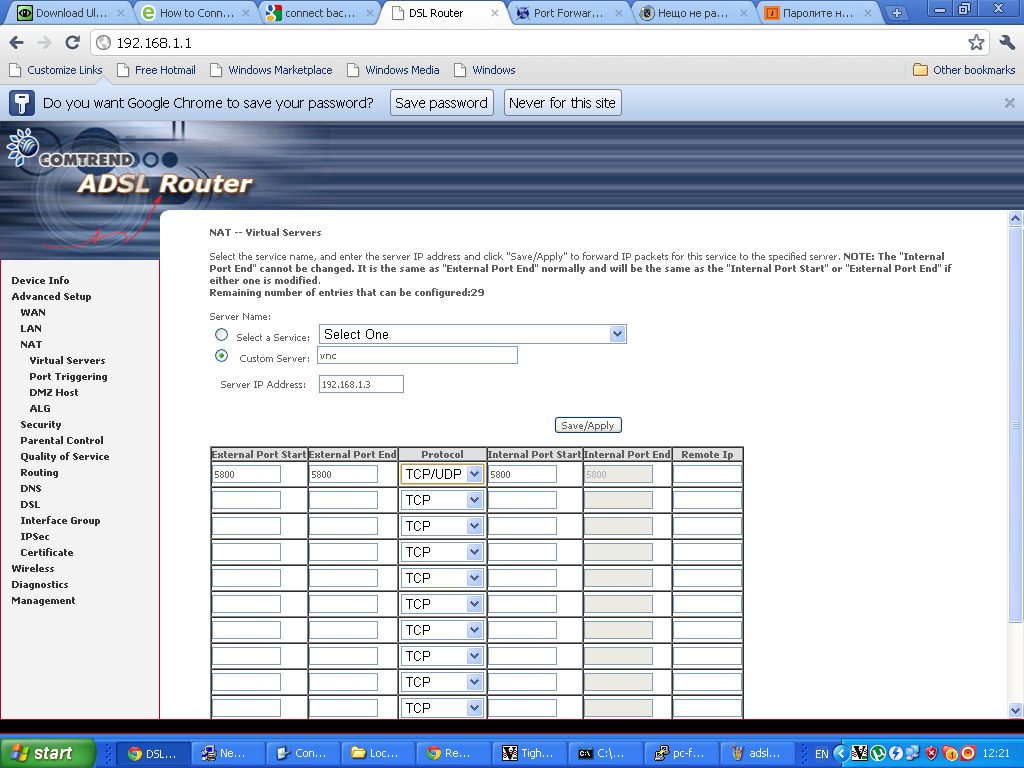 Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.
Configuring ADSL SmartAX MT882 TightVNC NAT port redirection screenTightVNC requires also NAT port redirection rule for port 5900 in order to be able to connect to the VNC server behind the dsl, so analogically I added a Virtual Server NAT rule for port 5900.