
Keeping WordPress Site / Blog and related installed plugins up-to-date is essential to prevent an attacker to hack into your Site / Database and deface your site, however if you're a company providing shell access from Cpanel / Plesk / Kloxo Panel to customers often customers are messing up permissions leaving important security credential files such as wp-config.php (which is storing user / pass credentials about connection to MySQL / PostgreSQL to have improper permissions and be world readable e.g. have permissions such as 666 or 777 while in reality the WordPress recommended permissions for wp-config.php is 600. I will skip here to explain in details difference between file permissions on Linux as this is already well described in any Linux book, however I just will recommend for any Share hosting Admin where Wordperss is hosted on Lighttpd / Apache Webserver + Some kind of backend database to be extra cautious.
Hence it is very useful to list all your WordPress sites on server wp-config.php permissions with find like this:
find / -iname 'wp-config.php' -print1;
I find it a generally good practice to also automatically set all wp-config.php permissions to 600 (6= Read / Write permissions only for File Owner user 0 = No permissions for All groups, 0 = No Permissions for all non-owner users)
If find command output gives you some file permissions such as:
ls -al /var/www/wordpress-bak/wp-config.php
-rw-rw-rw- 1 www-data www-data 2654 jul 28 2009 wp-config.php
E.g. file permission has 666 permissions (Readable for all users), then it is wise to fix this with:
chmod 600 /var/www/wordpress-bak/wp-config.php
It is generally a very good practice to run also a chmod 600 to each and every found wp-config.php file on server:
find / -iname 'wp-config.php' -print1 -exec chmod 600 '{}' \;
Above command will also print each file to whcih permission is set to Read / Write for Owner (this si done with -print1 option).
It is a good practice for shared hosting server to always configure a root cronjob to run above find chmod command at least once daily (whenever server hosts 50 – 100 wordpress+ more sites).
crontab -u root -l | { cat; echo “05 03 * * * find / -iname 'wp-config.php' -print1 -exec chmod 600 '{}' \; } | crontab –
If you don't have the 600 permissions set for all wp-config.php files this security "backdoor" can be used by any existing non-root user to be read and to break up (crack) in your database and even when there are Deface bot-nets involved to deface all your hosted server wordpress sites.
One of my servers with wordpress has just recently suffered with this little but very important security hole due to a WordPress site directory backup with improper permissions which allowed anyone to enter MySQL database, so I guess there are plenty of servers with this hidden vulnerability silently living.
Many thanks to my dear friend (Dimitar Paskalev) Nomen for sharing with me about this vulnerability! Very important note to make here is admins who are using some security enhancement modules such as SuPHP (which makes Apache webserver to run Separate Website instances with different user), should be careful with his set all wp-config.php modules to Owner, as it is possible the wp-config.php owner change to make customer WP based websites inaccessible.
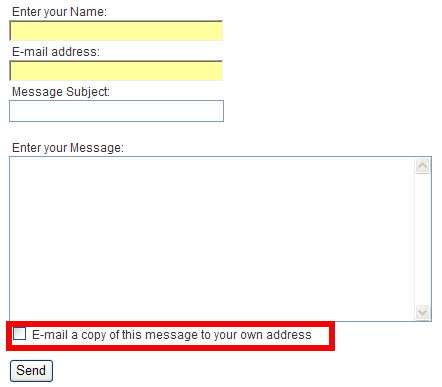
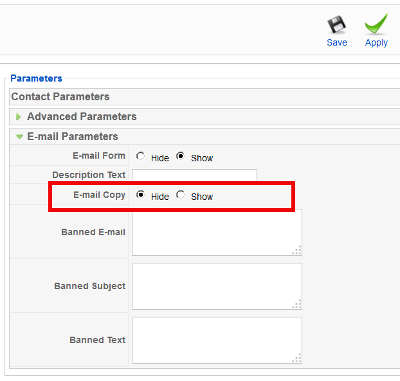
Another good security measure to protect your server WordPress based sites from malicious theme template injections (for both personal own hosted wordpress based blog / sites or a WordPress hosting company) is to install and activate WordPress Antivirus plugin.






How to turn off telnetd on FreeBSD
Sunday, December 25th, 2011There is a brand new remote FreeBSD vulnerability in telnetd in all its versions starting from version 7 to 9. It is therefore advisable that the telnet daemon be completely disabled.
To disable telnetd on FreeBSD:
1. Open /etc/inetd.conf
freebsd# vi /etc/inetd.conf
2. Comment out the line
telnet stream tcp nowait root /usr/libexec/telnetd telnetd
e.g.:
#telnet stream tcp nowait root /usr/libexec/telnetd telnetd
3. Restart inetd
freebsd# /etc/rc.d/inetd restart
The whole remote root telnetd FreeBSD security advisory (SA), can be read here
Tags: brand, Comment, conf, daemon, freebsd, freebsd security, inetd, libexec, line, line telnet, nowait, Restart, root, security, security advisory, stream, tcp, Telnet, telnetd, usr, version, vulnerability
Posted in Computer Security, FreeBSD, System Administration | 1 Comment »