If just installed Ubuntu or Xubuntu and choose as a default language English by mistake and you happen to live in Bulgaria, Russia, Ukraine, Belarus or any other cyrillic speaking / writting country and you want to make the desktop graphical environment to display menus in mother language Cyrillic. Here is how;
To add cyrillic localization, native support in GUI environment for major Dsektop Graphic Environments (XFCE, GNOME, KDE …) run in terminal:
For Bulgarian Cyrillic language Desktop support:
linux:~# apt-get install language-pack-bg
Четене на ÑпиÑъците Ñ Ð¿Ð°ÐºÐµÑ‚Ð¸… Готово
Изграждане на дървото ÑÑŠÑ Ð·Ð°Ð²Ð¸ÑимоÑти
Четене на информациÑта за ÑÑŠÑтоÑнието… Готово
Следните допълнителни пакети ще бъдат инÑталирани:
firefox-locale-bg language-pack-bg-base
Следните ÐОВИ пакети ще бъдат инÑталирани:
firefox-locale-bg language-pack-bg language-pack-bg-base
0 актуализирани, 3 нови инÑталирани, 0 за премахване и 2 без промÑна.
Ðеобходимо е да Ñе изтеглÑÑ‚ 0 B/1048 kB архиви.
След тази Ð¾Ð¿ÐµÑ€Ð°Ñ†Ð¸Ñ Ñ‰Ðµ бъде използвано 3533 kB допълнително диÑково проÑтранÑтво.
ИÑкате ли да продължите [Y/n]? Y
Selecting previously unselected package language-pack-bg-base.
(Reading database … 287291 files and directories currently installed.)
Unpacking language-pack-bg-base (from …/language-pack-bg-base_1%3a12.04+20130128_all.deb) …
Selecting previously unselected package language-pack-bg.
Unpacking language-pack-bg (from …/language-pack-bg_1%3a12.04+20130128_all.deb) …
Selecting previously unselected package firefox-locale-bg.
Unpacking firefox-locale-bg (from …/firefox-locale-bg_19.0.2+build1-0ubuntu0.12.04.1_i386.deb) …
Processing triggers for software-center …
Updating software catalog…this may take a moment.
INFO:softwarecenter.db.pkginfo_impl.aptcache:aptcache.open()
Software catalog update was successful.
ИнÑталиране на firefox-locale-bg (19.0.2+build1-0ubuntu0.12.04.1) …
ИнÑталиране на language-pack-bg (1:12.04+20130128) …
ИнÑталиране на language-pack-bg-base (1:12.04+20130128) …
Generating locales…
bg_BG.UTF-8… up-to-date
Generation complete.
Two packages language-pack-bg and language-pack-bg-base packages add to system localization files which in Linux are in the format of .mo files. Here is list of 2 packs file content:
linux:~# dpkg -L language-pack-bg
/.
/usr
/usr/share
/usr/share/doc
/usr/share/doc/language-pack-bg
/usr/share/doc/language-pack-bg/copyright
/usr/share/doc/language-pack-bg/changelog.gz
/usr/share/locale-langpack
linux:~# dpkg -L language-pack-bg-base
/.
/usr
/usr/share
/usr/share/doc
/usr/share/doc/language-pack-bg-base
/usr/share/doc/language-pack-bg-base/copyright
/usr/share/doc/language-pack-bg-base/changelog.gz
/usr/share/locale-langpack
/usr/share/locale-langpack/bg
/usr/share/locale-langpack/bg/LC_MESSAGES
/usr/share/locale-langpack/bg/LC_MESSAGES/Linux-PAM.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/pidgin.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/findutils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/mutt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/help2man.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/pppconfig.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/jade.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/recode.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/wdiff-gnulib.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/software-properties.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/grub.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/cracklib.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ggzcore.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libapt-inst1.4.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/system-service.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gwibber-service-sohu.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/mlocate.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/lynx.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/dnsmasq.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/apparmorapplet.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gettext-tools.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/binutils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/hello.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/quota.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ld.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libvisual-0.4.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/friendly-recovery.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gnupg2.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/git-gui.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/bash.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/apturl.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/sharutils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ubuntuone-control-panel.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/pulseaudio.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/hello-debhelper.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/hunspell.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/dctrl-tools.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gwibber-service-sina.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/popt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/powertop.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/xdiagnose.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ubuntuone-client.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gettext-runtime.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/debian-tasks.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/nano.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/lvm2.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ecryptfs-utils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/duplicity.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ubuntu-wallpapers.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/dselect.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/debconf.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/mountall.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/JabberBot.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/net-tools.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/apport.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libidn.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/newt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/tar.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gnupg.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/coreutils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/make.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libapt-pkg4.12.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/kerneloops.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ldm.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ufw.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/pidgin-libnotify.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/pppoeconf.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/acl.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/python-apt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gutenprint.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/MoinMoin.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/usbcreator.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/launchpad-integration.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/example-content.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/avahi.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/transmission-gtk.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/xkeyboard-config.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/dpkg-dev.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libgpg-error.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/human-theme.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/grep.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/sane-backends.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/NetworkManager.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libvirt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ubuntu-sso-client.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/app-install-data.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/dpkg.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/whois.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/system-config-kickstart.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gprof.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/zeitgeist.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/shared-mime-info.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/virt-manager.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/bison-runtime.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/wget.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/quilt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/command-not-found.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/jockey.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/attr.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ltsp-login.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/kcm_gtk.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/alsa-utils.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/aspell.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/fetchmail.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/man-db-gnulib.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/devscripts.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/xscreensaver.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/unity-2d.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/compiz.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/apt.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/gODBCConfig.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/libc.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/plasma_applet_menubarapplet.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/update-manager.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/psmisc.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/screen-resolution-extra.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/unattended-upgrades.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/adduser.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/sysstat.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/checkbox.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/apt-listchanges.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/ubuntuone-installer.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/upstart.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/upower.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/tasksel.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/byobu.mo
/usr/share/locale-langpack/bg/LC_MESSAGES/language-selector.mo
/var
/var/lib
/var/lib/locales
/var/lib/locales/supported.d
/var/lib/locales/supported.d/bg
Above .mo files are binary files, generated from plain text .po / .pod files. In free software OS .po files are the most common language translation files, where for each different language a set of .po files exist. Translators usually translate from English to respective language using a GUI text editor called poedit. Once translation is made from those .po files .mo binaries are generated and shipped as localizations for program or group of programs. Below is edit of one of Polish translation of lang file belonging to CUPS Printing service.
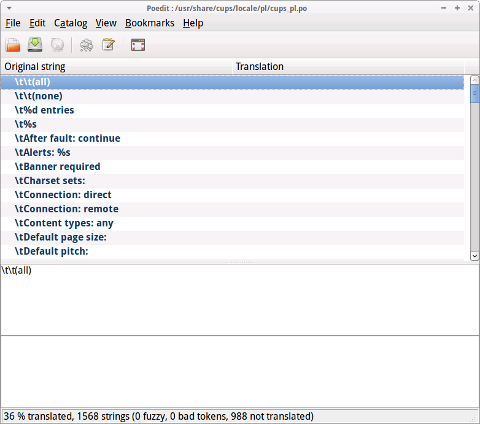
Once .po files are created, generation of .mo files can be done in various way, however usually Linux system uses msgfmt – (compile message catalog to binary format). In order to generate .mo file out of lets say cups_pl.po;
hipo@linux:~$ msgfmt cups_pl.so
hipo@linux:~$ ls -al *.mo
-rw-rw-r-- 1 hipo hipo 31988 Mar 18 12:38 messages.mo
Anyways, here is how to add Cyrillic support for rest of Major cyrillic speaking countries, issue;
For Russian Cyrillic language Linux Desktop env support;
linux:~# apt-get install --yes language-pack-ru
...
For Belarusian Cyrillic Linux Desktop;
linux:~# apt-get install --yes language-pack-be
For Linux Desktop in Ukrainian;
linux:~# apt-get install --yes language-pack-uk
…
For Linux Desktop in Serbian language;
linux:~# apt-get install --yes language-pack-sr
...
For Graphic Environment in Macedonian;
linux:~# apt-get install --yes llanguage-pack-mk
...
For Linux GUI in Bosnian;
linux:~# apt-get install --yes language-pack-bs
...
For Kyrgyz language Linux localization;
linux:~# apt-get install --yes language-pack-ky
Whether, you are using Linux Desktop internationalization on some other Cyrillic related language, which I'm missing here please feel free to drop me a comment how you install it? I