Posts Tagged ‘most linux distributions’
Wednesday, June 12th, 2013 
Here in my job, there is one internet (TV) around which can only read video formats in Mp4. Henceforth I needed a way to convert a number of JPEG / PNG format Picture files to Mp4. In my situation I needed to make video out of pictures and script it as this was required to be later pushed via FTP protocol to the Internet TV. Ater doing some research I figured out this is possible to build video out of pictures by using together ImageMagick and avconv.
First thing is to send pictures in certain resolution. There is a tool from imagemagick package called mogrify (which can do that). To convert a number of different dimension pictures to lets say 1024×768, used:
noah:~# mogrify -resize 1024×768 *.png
In earlier Linux distributions to create a movie from pictures ffmpeg was used like so:
# ffmpeg -qscale 5 -r 20 -b 9600 -i SDC%04d.png movie.mp4
However in newer version of ffmpeg support for this is removed, and to make video from images, there is other tool avconv. On most Linux distributions avconv is part of libav-tools package.
To install on avconv Debian and Ubuntu;
noah:~# apt-get install –yes libav-tools
…
Once installed to create single mp4 video from JPEG or PNG pictures:
noah:~# avconv -i SDC106001.JPG SDC10595.JPG SDC13611.JPG SDC13612.JPG SDC13614.JPG movie-from-pictures.mp4
I found there is also a nice GUI,software Open Movie Editor, which can create video out of number of pictuers stored in a directory.
Open Movie Editor is available in most Linux distributions (unfortunately as of time of writting on Debian Wheeze there is no install candidate of openmovieeditor), there is however substitute package doing the same job called openshot);
On latest Debian stable to install Openshot:
noah:~# apt-get install –yes openshot
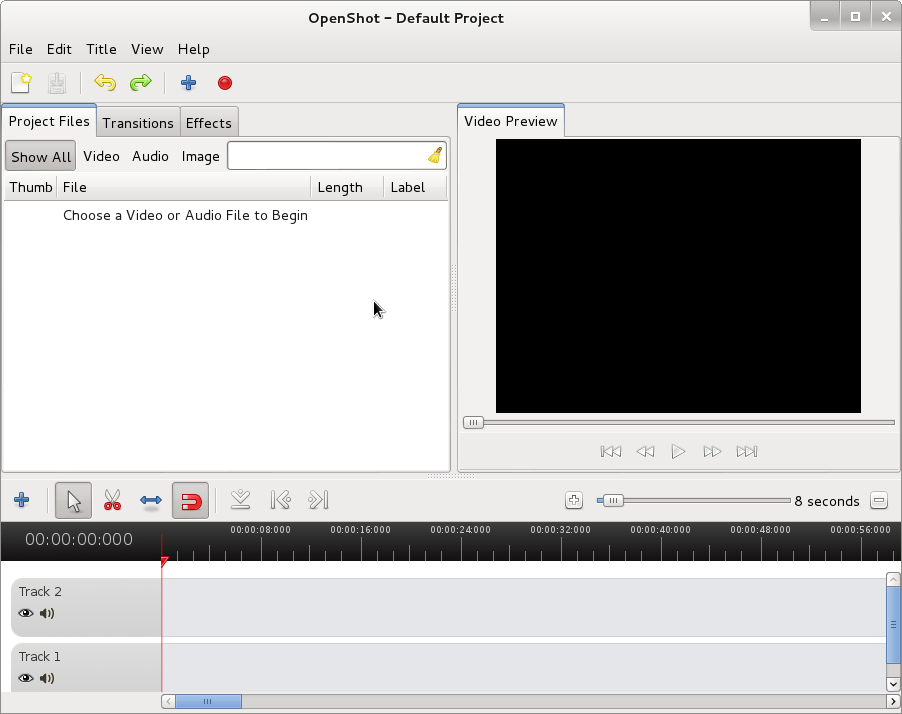
Openshot has an option (Import Image Sequence) from File -> Import Image Sequence. Using this option you can select a directory with fles with common prefix name lets say IMG*.png and create Video based on the photos inside.
On Ubuntu Linux or other distro where openmovieeditor is avialable install it with:
ubuntu:~# apt-get install –yes openmovieeditor
…
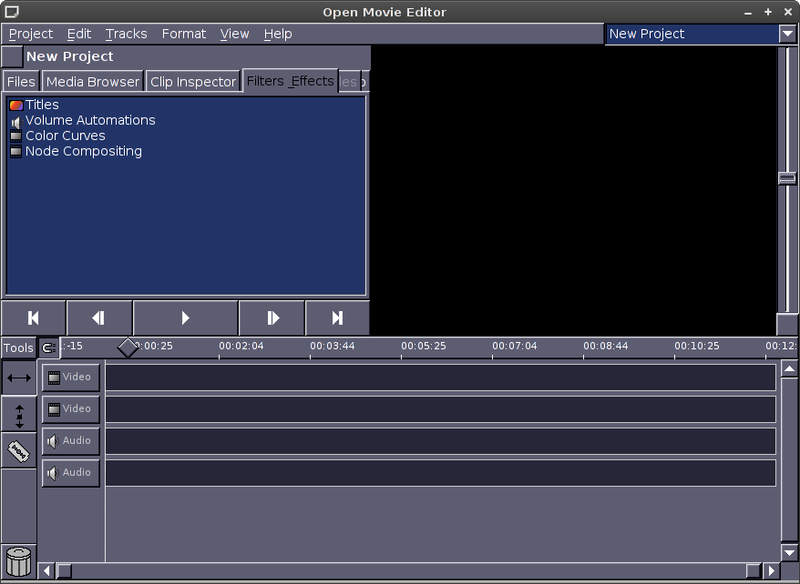
To create a video out of pictures click on Media Browser tab. Choose the Folder with pictures from which video will be generated and drag them to the Video bar
(window).
To save produced video navigate to menus:
Project -> Render
and select format to save it as. One good codec to save output is Quicktime's. To convert later Quicktime MOV Video to MP4 video,
there is the Pytube Media Converter script.
Well that's all enjoy your new videos from pictures 🙂
Tags: ffmpeg, images, internet tv, jpeg images, Linux, mogrify, most linux distributions, pictuers, png format, Protocol, ubuntu linux, video formats, wheeze, writting
Posted in Everyday Life, Linux, Linux and FreeBSD Desktop, Various | No Comments »
Saturday, May 11th, 2013 
Creating user with access only through FTP is vital in daily routine system administration job. The reason why it is good to disable SSH access to users which don't need it is of course better security. Disabling access to ssh shell for users which don't need it prevents you for user to run malicious code usually exploits or some DDoS Fork bombs – like the infamous Linux shell Denial of Service string;
:(){ :|:&};:
Better not try above string on productive server 😉
So back to the topic here how to add Linux FTP only user;
1. Create a regular user with adduser or useradd (depending) on GNU / Linux distribution
adduser is available across most Linux distributions nowadays, however I remember in past there was some distros which had useradd instead. Anyways for most adduser should be ok. As of time of writting both 3 main stream Linux distributions Slackware, Debian and Fedora has adduser.
linux:~# adduser new-user-for-ftp-only
Adding user `new-user-for-ftp-only' …
Adding new group `new-user-for-ftp-only' (1006) …
Adding new user `new-user-for-ftp-only' (1005) with group `new-user-for-ftp-only' …
Creating home directory `/home/new-user-for-ftp-only' …
Copying files from `/etc/skel' …
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for new-user-for-ftp-only
Enter the new value, or press ENTER for the default
Full Name []: New Linux User Only for FTP access
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] Y
linux:~#
2. Change user shell /bin/bash to /bin/false
Again depending on Linux distribution by default /bin/bash /bin/sh or /bin/whatever shell will get added. To make just created user access to SSH disabled. Change shell to /bin/false – a tiny program which just returns a FALSE value and quits immediately.
There are two ways to do so;
a) Edit directly /etc/passwd with vim / joe
linux:~# vim /etc/passwd
Go to end of file and find the record for user, should be smth like:
new-user-for-ftp-only:x:1005:1006:New Linux User Only for FTP access,,,:/home/new-user-for-ftp-only:/bin/bash
Change to;
new-user-for-ftp-only:x:1005:1006:New Linux User Only for FTP access,,,:/home/new-user-for-ftp-only:/bin/false
b) Use chsh cmd
linux:~# chsh new-user-for-ftp-only
Changing the login shell for new-user-for-ftp-only
Enter the new value, or press ENTER for the default
Login Shell [/bin/bash]: /bin/false
linux:~# grep -i new-user-for-ftp-only /etc/passwd
new-user-for-ftp-only:x:1005:1006:New Linux User Only for FTP access,,,:/home/new-user-for-ftp-only:/bin/false
3. Testing if ssh access to new user is disabled
linux:~# ssh new-user-for-ftp-only@localhost
new-user-for-ftp-only@localhost's password:
Linux noah 2.6.32-5-amd64 #1 SMP Mon Feb 25 00:26:11 UTC 2013 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Connection to localhost closed.
Tags: adduser, change user, distros, fedora, ftp access, home directory, linux distribution, linux shell, linux user, main stream, most linux distributions, routine system administration, unix password, user information, useradd
Posted in Computer Security, System Administration, Various | 2 Comments »
Saturday, March 16th, 2013 It is a common thing for me as a Linux and FreeBSD sysadmin to know what process assignes to which port number? I'm sure many novice system administrators will end up sooner or later with same question. Knowing what kind of processes has listening to TCP and UDP protocol / ports is a must to have a proper configured Linux / BSD system. In Linux there are two commands ( lsof and fuser) with which you can get various extra PID information on running processes (i.e. get information which cannot otherwise be obtained via the usual ps and netstat To use them on most Linux distributions, you will have to have them installed.
1. Install fuser / lsof on Linux / BSD
a) On RPM based Linux distros – Fedora, CentOS, RHEL, SuSE /sbin/fuser is usually part of base install psmisc rpm package, however /usr/sbin/lsof is not among standard installed rpms, so you have to manually install via yum:
[root@centos ~]# yum install -y lsof
….
b) On Deb based Linuxes (Debian, Ubuntu, Mint, ArchLinux etc.). both lsof and fuser has to be installed via a separate packages non-part of Debian base install packs.
server:~# apt-get --yes install lsof fuser
....
On Debian full path location of both is in /bin/fuser and /usr/bin/lsof.
Two tools are precious swiss army knife outfit to use, whether you doubt someone cracked into a server or in doubt you might have "hidden" cracker processes on server.
c) Install fuser on Free/Net/Open/ BSD
bsd# cd /usr/ports/sysutils/fuser
bsd# make install clean
....
bsd# cd /usr/ports/sysutils/lsof
bsd# make install clean
....
2. Using fuser and lsof to look up process PIDs assigned to port numbers
lsof name is derived from List Open Files, as we know in UNIX, GNU / Linux, *BSD everything on the system is a file, thus to get all kind of information concerning all active files (i.e. ports, PIDs, procotols and process names;
server:~# lsof +M -i4 | less
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
portmap 1317 daemon 4u IPv4 3930 0t0 UDP *:sunrpc[portmapper]
portmap 1317 daemon 5u IPv4 3939 0t0 TCP *:sunrpc[portmapper] (LISTEN)
rpc.statd 1329 statd 4u IPv4 3974 0t0 UDP *:657
rpc.statd 1329 statd 6u IPv4 3983 0t0 UDP *:28530[status]
rpc.statd 1329 statd 7u IPv4 3986 0t0 TCP *:58515[status] (LISTEN)
apache2 1625 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 1625 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
sshd 1918 root 3u IPv4 4945 0t0 TCP *:ssh (LISTEN)
miniserv. 2155 root 5u IPv4 5299 0t0 TCP *:20000 (LISTEN)
miniserv. 2155 root 6u IPv4 5300 0t0 UDP *:20000
miniserv. 2161 root 6u IPv4 5367 0t0 TCP *:webmin (LISTEN)
miniserv. 2161 root 7u IPv4 5368 0t0 UDP *:10000
ntpd 2172 ntp 16u IPv4 5395 0t0 UDP *:ntp
ntpd 2172 ntp 18u IPv4 5402 0t0 UDP localhost:ntp
ntpd 2172 ntp 19u IPv4 5403 0t0 UDP iqtest.soccerfame.com:ntp
ntpd 2172 ntp 20u IPv4 16028 0t0 UDP secure.broomlake.com:ntp
apache2 4505 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4505 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 4539 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4539 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 4780 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4780 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 4900 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4900 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 4907 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4907 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 4915 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 4915 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5067 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5067 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5133 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5133 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5134 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5134 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5148 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5148 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5152 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5152 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5259 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5259 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5265 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5265 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5266 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5266 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5346 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5346 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5356 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5356 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5467 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5467 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5523 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5523 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5568 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5568 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5715 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5715 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5716 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5716 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5758 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5758 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 5789 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 5789 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 6106 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 6106 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 16608 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 16608 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 16904 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 16904 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 17124 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 17124 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 17280 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 17280 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 20855 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 20855 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 20920 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 20920 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 21023 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 21023 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 22182 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 22182 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23307 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23307 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23366 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23366 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23408 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23408 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23419 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23419 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23428 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23428 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23452 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23452 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23561 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23561 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23579 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23579 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 23851 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 23851 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 24103 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 24103 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 24659 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 24659 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
sshd 25073 root 3u IPv4 29855891 0t0 TCP iqtest.soccerfame.com:ssh->www.pc-freak.net:50176 (ESTABLISHED)
sshd 25084 hipo 3u IPv4 29855891 0t0 TCP iqtest.soccerfame.com:ssh->www.pc-freak.net:50176 (ESTABLISHED)
apache2 25089 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 25089 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 26737 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 26737 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 27243 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 27243 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 27282 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 27282 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 27633 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 27633 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 28205 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 28205 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 29244 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 29244 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 29372 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 29372 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 29411 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 29411 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 29462 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 29462 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 29548 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 29548 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 30161 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 30161 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 31876 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 31876 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 31958 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 31958 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32052 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32052 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32061 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32061 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32143 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32143 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32149 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32149 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32440 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32440 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32635 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32635 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 32790 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 32790 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 40211 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 40211 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 40309 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 40309 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 40432 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 40432 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 40476 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 40476 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46319 root 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46319 root 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46438 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46438 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46439 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46439 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46440 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46440 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46441 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46441 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46442 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46442 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46443 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46443 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46509 root 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46509 root 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46510 root 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46510 root 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 46515 root 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 46515 root 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 51287 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 51287 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 51485 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 51485 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 51804 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 51804 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
named 54418 bind 20u IPv4 31298857 0t0 TCP localhost:domain (LISTEN)
named 54418 bind 21u IPv4 31298859 0t0 TCP iqtest.soccerfame.com:domain (LISTEN)
named 54418 bind 22u IPv4 31298861 0t0 TCP secure.broomlake.com:domain (LISTEN)
named 54418 bind 23u IPv4 31298865 0t0 TCP localhost:953 (LISTEN)
named 54418 bind 512u IPv4 31298856 0t0 UDP localhost:domain
named 54418 bind 513u IPv4 31298858 0t0 UDP iqtest.soccerfame.com:domain
named 54418 bind 514u IPv4 31298860 0t0 UDP secure.broomlake.com:domain
named 54418 bind 515u IPv4 31298864 0t0 UDP *:domain
proftpd 62010 proftpd 1u IPv4 31306260 0t0 TCP *:ftp (LISTEN)
mysqld 62420 mysql 11u IPv4 31306903 0t0 TCP *:mysql (LISTEN)
apache2 62582 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 62582 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 62845 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 62845 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
apache2 64748 www-data 3u IPv4 5456 0t0 TCP *:www (LISTEN)
apache2 64748 www-data 4u IPv4 5458 0t0 TCP *:https (LISTEN)
Above lsof command lists all active listening processes port number on UDP and TCP/IP 4 proto with the assigned process PID number (in second column). This is very useful if you find out to have listening service on port number and you cannot figure out what process name exactly is listening.
A classic example, where this is very helpful is if you have a listening process on SMTP port 25 and you cannot identify what kind of mail server is taking up the port? This has happened me many times on Debian Linux based hosts, which by default had priorly installed sendmail and I later removed sendmail to install Postfix or Exim SMTP.
To find out what is assigning port 25, you had to grep the protocol name from all binded host processes, like so:
server:~# lsof +M -i4 | grep -i smtp
exim4 17550 root 3u IPv4 31577966 0t0 TCP localhost:smtp (LISTEN)
Whether you want to get information on Process ID, binding other random port lets say port 10000, following same logic you can grep it:
server:~# lsof +M -i4 |grep -i 10000
miniserv. 2161 root 7u IPv4 5368 0t0 UDP *:10000
To get rid of a process for which you're unsure what kind of (/etc/init.d/service-name) init script is starting it, you can then use kill cmd to stop it;
server:~# kill -9 2161
Second approach to find out what kind of process is listening on a random port or socket, lets say port num 58515 is by using fuser.
server:~# netstat -ltn4
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:58515 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN
tcp 0 0 77.92.85.71:53 0.0.0.0:* LISTEN
tcp 0 0 109.123.106.44:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:20000 0.0.0.0:* LISTEN
Below netstat cmmand, lists all active listening processes on respective IP address and port for protocol TCPIP v.4.
Hence on to get more information on what process is listening on port 58515?
server:~# fuser -v 58515/tcp
USER PID ACCESS COMMAND
58515/tcp: statd 1329 F…. rpc.statd
Once you know what is listening, whether you want to kill it this is also possible directly through fuser;
server:~# fuser -vk 58515/tcp
As a close-up, I will say fuser and lsof are two must have software tools on any productive server. It is among the critical applications admin has to install during initial server set-up. fuser and lsof helps me often in my sysadmin work, it was more than once I've used them to identify script-kiddies exploit scanners running as a standard process names, as well secretly listening on weird port number cracker back-doors.
Hopefully this little article, helps someone learn something new. Plenty is written and will be written and if one takes the time to research he can learn much, much more. I'm sure my tiny article is nothing new under the sun for old-school admins, I still hope it will be of use to novice. I'm looking forward to hear if I'm missing some neat use or some interesting case, when lsof or fuser "saved your ass" 🙂
Tags: bsd system, configured linux, fedora, ipv4, Linux, lsof, most linux distributions, running processes, statd, swiss army knife, tcp and udp, Ubuntu, udp protocol, www data
Posted in FreeBSD, System Administration, Web and CMS | No Comments »
Saturday, January 14th, 2012 Mounting ISO files in Linux is easy with mount cmd, however remembering the exact command one has to issue is a hard task because mounting ISO files is not a common task.
Mounting ISO files directly by clicking on the ISO file is very nice, especially for lazy people uninitiated with the command line 😉
Besides that I'm sure many Windows users are curious if there is an equivallent program to DaemonTools for Linux / BSD*?
The answer to this question is YES!
There are two major programs which can be used as a DaemonTools substitute on Linux:
These are FuriousISOMount and AcetoneISO
AcetoneISO is more known and I've used it some long time ago and if I'm correct it used to be one of the first ISO Mount GUI programs for Linux. There is a project called GMount-ISO / (GMountISO) which of the time of writting this article seems to be dead (at least I couldn't find the source code).
Luckily FuriousISOMount and AcetoneISO are pretty easy to install and either one of the two is nowdays existing in most Linux distributions.
Probably the programs can also be easily run on BSD platform also quite easily using bsd linux emulation.
If someone has tried something to mount GUIs in Free/Net/OpenBSD, I'll be interesting to hear how?
1. Mount ISO files GUI in GNOME with Furius ISO Mount
FuriousISOMount is a simple Gtk+ interface to mount -t iso9660 -o loop command.
To start using the program on Debian / Ubuntu install with apt;
debian:~# apt-get install furiusisomount
The following extra packages will be installed:
fuseiso fuseiso9660 libumlib0
The following NEW packages will be installed:
furiusisomount fuseiso fuseiso9660 libumlib0
…
To access the program in GNOME after install use;
Applications -> Accessories -> Furious ISO Mount
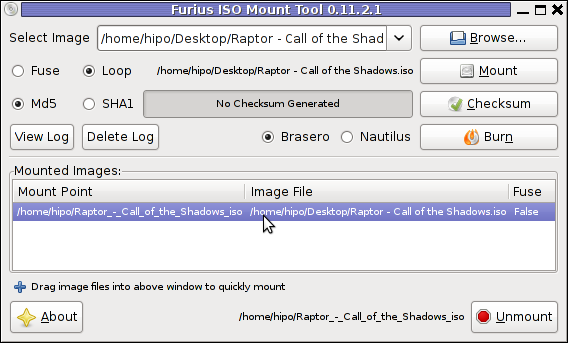
When mounting it is important to choose Loop option to mount the iso instead of Fuse
After the program is installed to associate the (.iso) ISO files, to permanently be opened with furiusisomount roll over the .iso file and choose Open With -> Other Application -> (Use a custom command) -> furiusisomount
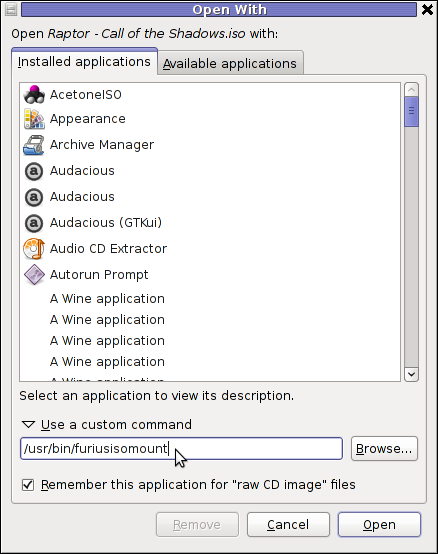
2. Mount ISO Files in KDE Graphical Environment with AcetoneISO
AcetoneISO is build on top of KDE's QT library and isway more feature rich than furiousisomount.
Installing AcetoneISO Ubuntu and Debian is done with:
debian:~# apt-get install acetoneiso
The following NEW packages will be installed:
acetoneiso gnupg-agent gnupg2 libksba8 pinentry-gtk2 pinentry-qt4
0 upgraded, 6 newly installed, 0 to remove and 35 not upgraded.
Need to get 3,963 kB of archives.
After this operation, 8,974 kB of additional disk space will be used.
...
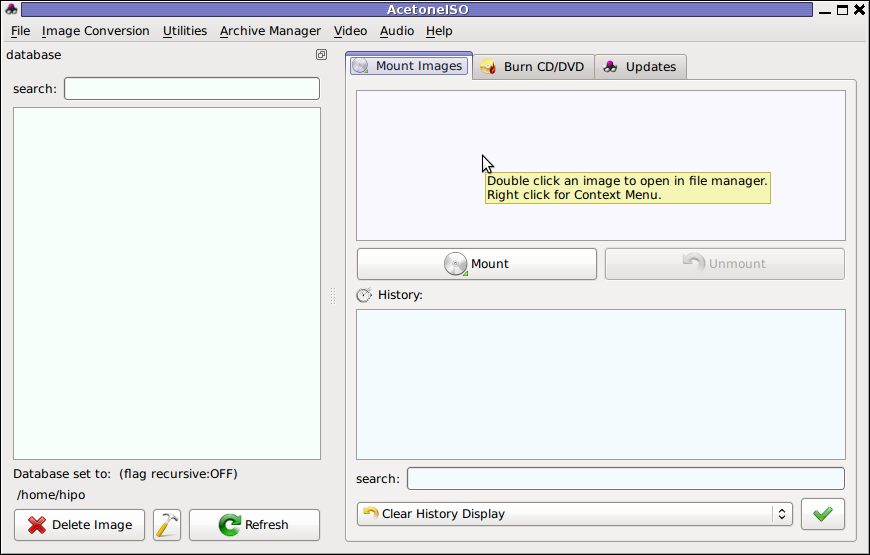
AcetoneISO supports:
- conversion between different ISO formats
- burn images to disc
- split ISO image volumes
- encrypt images
- extract password protected files
Complete list of the rich functionality AcetoneISO offers is to be found on http://www.acetoneteam.org/viewpage.php?page_id=6
To start the program via the GNOME menus use;
Applications -> Accessories -> Sound & Video -> AcetoneISO
I personally don't like AcetoneISO as I'm not a KDE user and I see the functionality this program offers as to rich and mostly unnecessery for the simple purpose of mounting an ISO.
3. Mount ISO image files using the mount command
If you're a console guy and still prefer mounting ISO with the mount command instead of using fancy gui stuff use:
# mount -t iso9660 -o loop /home/binary/someiso.iso /home/username/Iso_Directory_Name
Tags: AcetoneISO, Auto, BSD, cmd, custom, debian gnu, Draft, emulation, exact command, file, Files, Free, GMount-ISO, Gnome, graphical environment, gtk interface, guis, image files, ISO, iso file, iso files, iso9660, libumlib, long time, loop command, most linux distributions, nbsp, Open, OpenBSD, option, platform, roll, someone, something, source code, substitute, time, Ubuntu, windows users, YES
Posted in Gnome, Linux, Linux and FreeBSD Desktop, Linux Audio & Video | No Comments »
Thursday, January 19th, 2012 Since its early days dosbox has elolved a lot. For all those who haven't heard of dosbox, it is x86 Free Software Linux / FreeBSD DOS emulator
DosBox supports, almost all the game classics we used top lay in oldschool times when DOS (Disk Operating System ) version was running on top of most personal computer.
The most spread versions of DOS people used to use on their PCs were Novell (DR-DOS) more rarely used, and MS-DOS (The Microsoft DOS ver.).
I'm sometimes being sentimental about the past so I remembered for Raptor – Call of the Shadows !
Having a bit of experience with DOSBox to run few DOS games I've decided to give a try with dosbox.
First I have to dig for this shareware, since this game is part of the sharewares, nowdays a binary version of it is freely distributed on the net.
Finding the game however took me about 10 minutes, as most of the download links for Raptor, were either dead or required some kind of registration. After a bit of look I found it on an old torrent with few seeders and succeded downloading.
For the convenience of people who would like to download run the Raptor arcade classic game check here
Nicely Raptor works out of the box directly launched with dosbox emulator.
Dosbox has packages for most Linux distributions.
I personally used it on my Debian Linux so installed via apt:
debian:~# apt-get install dosbox
...
The game works without any dosbox hacks, just download, unarchive and launch with dosbox:
hipo@debian:~$ wget https://www.pc-freak.net/files/Raptor_Call_of_The_Shadows_Apogee_arcade.tar.gz
...
hipo@debian:~$ tar -zxvf Raptor_Call_of_The_Shadows_Apogee_arcade.tar.gz
...
hipo@debian:~$ cd Raptor/
hipo@debian:/home/hipo/Raptor$ dosbox rap.exe
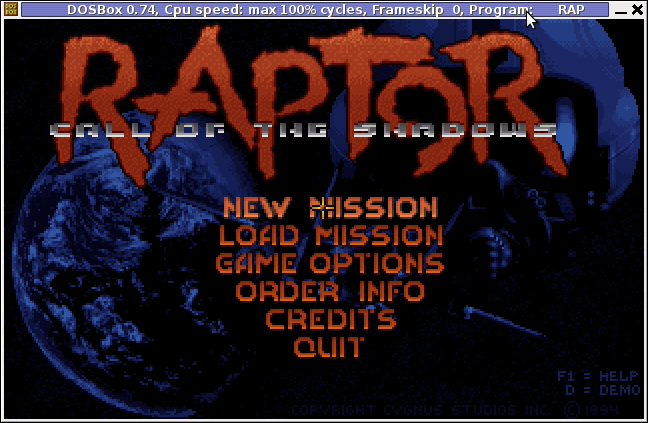
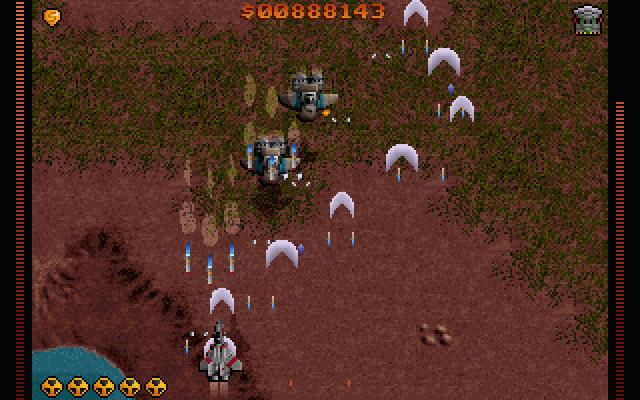
People like me 😉 who lived in that glorious times when DOS was a standard for a desktop operating system pretty much like MS Windows is today, certainly remember the awesome games produced by Apogee Software a company later known as 3D Realms
Apogee until this very day remain one of the greatest game creation companies in history of games. 3D Realms played a crucial role in development of PC game industry as well as has a great santimental value to probably million of old school arcade game addicts.
They can be ben undoubtedly can be praised for having created some of the most awesome arcade games for all times.
Some of the early hit games they created you probably know, few of the titles are:
- Duke Nukem I, II
- Arctic Adventure
- Monster Bash
- Stargunner
- Commander Keen series
- Wolfenstein 3D
- Blake Stone
- Terminal Velocity (Terminal Reality)
- Shadow Warrior
- Death Rally
- Blood
Apogee was also notable for being a company to had established the so spread mostly during the late 80s up to the early years of the second millenium.
ShareWare model of distribution is an interesting phenomenon, that co-relates more or less with the ideas of Free Software.
The idea of ShareWare games was games are distributed for Free and the end customer (gamer) is asked to pay for a game only if he likes it.
Some of the shareware published games was available for free download and play, however the game was only bundled with only a number of game levels to unlock the rest of the game levels you had to play some money.
The shareware games produced were then freely published and shared via dial up access BBS nodes (A text based Bulletin Board System similar to nowdays Forums).
BBS has historically been the major way of sharing knowledge and exchanging ideas and opinions preceding the massive rise of the WEB.
Today most computer users would probably even haven't heard about BBS, if you like to have a general idea on how BBSes seemed to look dahmer.vistech.net .
ShareWare started to loose speed with the decline of BBS and the emergence of Free Software.
Some of the conceptual ideas of ShareWare found its way in "Open Source & Free Software", and commercial companies like RedHat and SuSE.
If you have tried some other Apogee games with Dosbox on Linux and FreeBSD and you can positively confirm they work it will be great. In theory all of the DOS games of apogee should work fine with dosbox. Any feedback or game recommendations of your favourite games of the DOS years are mostly welcome in comments. I'm curious to hear what was your favourite DOS game. Maybe when I have time I'll prepare a list of my favourite games put them here 😉
Tags: apogee, arcade game, Auto, BBS, binary version, bit, BSD, Call, classic game, convenience, debian cd, Desktop, desktop operating system, Disk, dos disk, dos emulator, dos games, dosbox, dr dos, Draft, exePeople, favourite, Free, game check, game classics, glorious times, GNU, gnu linux, hipo, Linux, Microsoft, microsoft dos, most linux distributions, MS-DOS, Nicely, Play, quot, raptor call of the shadows, seeders, Shareware, sharewares, software, software linux, tar gz, terminal, wget, zxvf
Posted in FreeBSD, Games Linux, Linux, Linux and FreeBSD Desktop | 1 Comment »
Monday, January 16th, 2012 My sister, experience some programs running with wine (Windows Emulator) to crash on her Ubuntu 11.10.
As she is quite new with Linux, she has no idea about the existence of CTRL ALT BACKSPACE key combination to restart a hanged GNOME, KDE by directly killing the Xorg server.
I felt obliged to explain her it is better to use CTRL ALT BACKSPACE X kill switch instead of restarting the whole Linux kernel (which basiclly is working) and that it is just the display keeping blacnk.
Pressing the would kill Xorg and therefore all applicatins previously running on top of it will die. In Ubuntu Xorg is configured to run via gdm, so once killed it will automatically reload the GDM (Gnome Display Manager).
I was about to explain her that its better she use CTRL+ALT+BACKSPACE instead of restarting the whole system but suddenly I realized this is not working.
In UBUNTU 11.10 and I guess in all UBUNTU's after 9.04 CTRL ALT BACKSPACE is substituted with the key switch combination ALT PRINTSCREEN K, I've explained her about that.
This change is actually a change implied by most Linux distributions nowdas and is some kind of change in Xorg newer versions…
To enable back the CTRL + ALT + BACKSPACE , I've issued cmd:
stanimira@ubuntu~:$ echo' setxkbmap -option terminate:ctrl_alt_bksp' >> ~/.xinitrc
An alternative way to set setxkbmap -option terminate:ctrl_alt_bksp to run on Ubuntu user login is by setting it as a startup application using;
stanimira@ubuntu:~$ gnome-session-properties
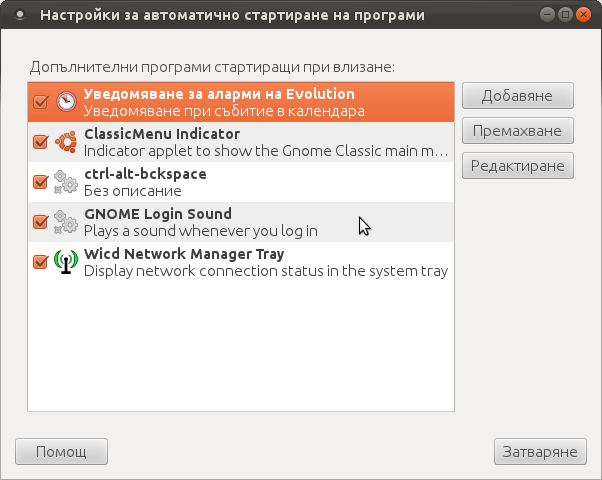
Press the Add button and type in the box to appear;
Name: setxkbmap
Command: setxkbmap -option terminate:ctrl_alt_bksp
Comment: setxkbmap
Reverting the Xserver kill switch back to the classical Ctrl+Alt+Backspace should also be running fine on older Ubuntu Linuces – 11.04, 10.10, 10.04 etc.
Tags: add button, Alt, Auto, backspace, Button, change, Comment, Ctrl, Display, Draft, existence, GDM, Gnome, kde, key switch, kill, kill switch, Linux, linux kernel, login, most linux distributions, ocelot, option, Press, printscreen, Reverting, session properties, setxkbmapCommand, startup, startup application, switch combination, type, Ubuntu, wine, wine windows, xinitrcAn, Xorg, xserver
Posted in Linux, Linux and FreeBSD Desktop | No Comments »
Thursday, December 22nd, 2011 Do you remember the old arcade spaceship shooter Xenon 2 Megablast? I do 😉 For all those who are too young to remember, here are two screenshots:

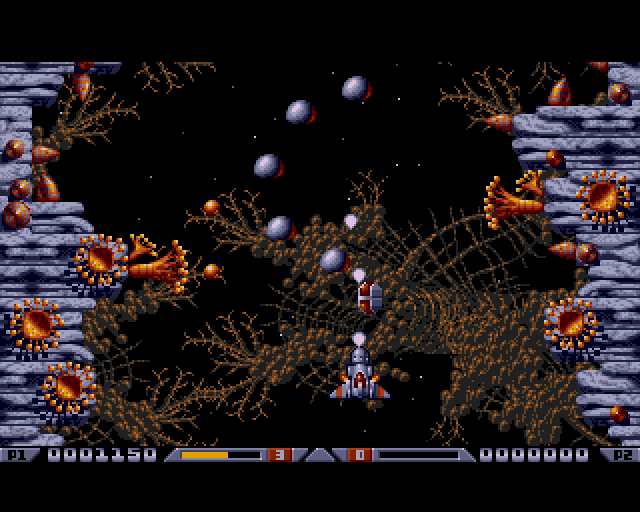
Even though Xenon 2 Megablast original can now be played using dosbox DOS emulator. Its interesting to mention I've found two Linux games that more or less can be qualitified to resemble Xenon 2.
The games are Native Free Software games and existing in package repositories of most Linux distributions and *BSD port trees.
Geki 2 and Geki 3 are of a less quality to Xenon but still, the game experience is nice and is among the Arcade shooter games to bring you fun in the boring days if you're on GNU / Linux or FreeBSD Free OS platforms.
Installing Geki2 and Geki3 on Debian and Ubuntu Linux is standard with apt:
debian:~# apt-get install geki2 geki3
...
On Debian GNU / Linux , after installed the games would not create GNOME Applications -> Games -> game startup shortcuts, however the game startups will get added in GNOME Applications Menu under:
Applications -> Debian -> Games -> Action -> Geki 2
and
Applications -> Debian -> Games -> Action -> Geki 3
The games can be launched also manually with commands:
geki2
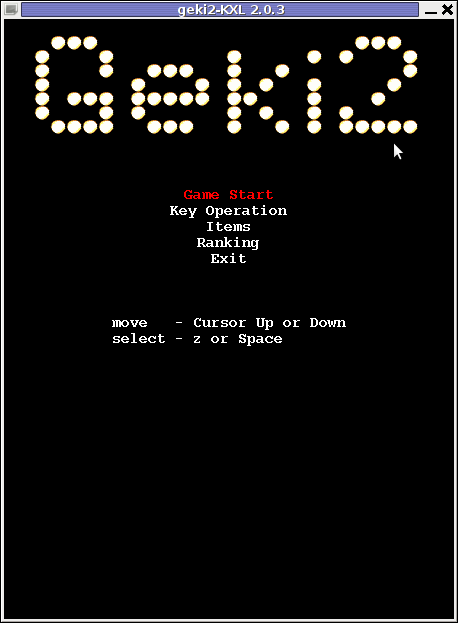
or
geki3
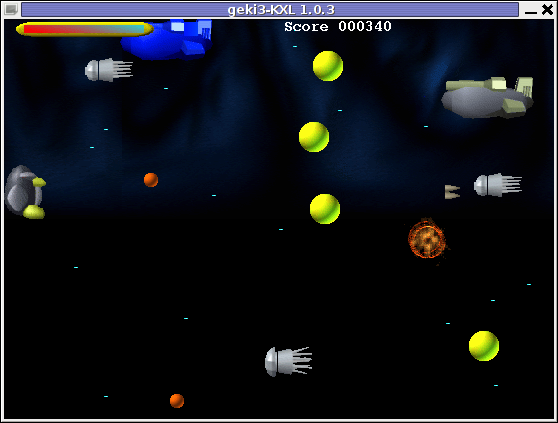
Geki 2 is a way closer to Xenon 2 as it has similar look and feel and the same vertical direction the spaceship is navigated.
In Geki 3 still the shoot 'em' up spaceship like arcade is present, however instead of penguin you have to fly a flying penguin, as well as the spaceship move direction is horizontal.
Both the games have the same sound and music effects. The game music and effects are not of top quality but are not bad. In general the games surely gives some of the arcade atmosphere.
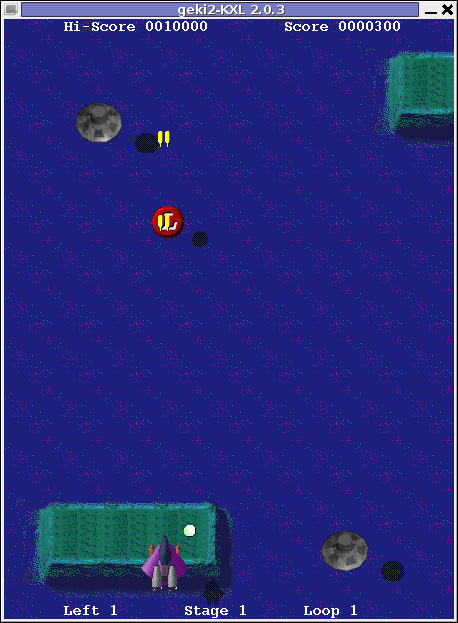
Geki 2 Xenon 2 Megablast like on Debian Linux
In the tradition of the arcade games at the end of each level in both games you face the Level Boss Enemy, you should destroy.
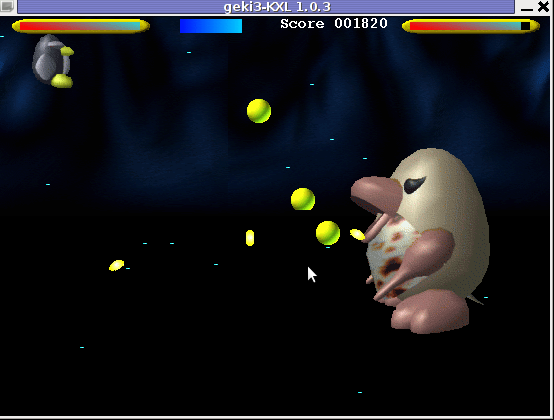
As you can see in below's screenshot the overall graphics of GEKI 3 is poorer while compared to GEKI 2
still GEKI 2 gampley is fun and addictive and I would say not less enjoyable than GEKI 2.
At times I even think that Geki 3 is more fun because it is more dynamic.
Maybe other reason, why I enjoyed more Geki 3 is also the fact that Geki 2 is a way harder to play. Dying only 3 times in the game you get GAME OVER and the next game you're started from the beginning of the same level you died in …

Something really annoying that affects both the games; there is no option to play them in Fullscreen mode! ARGH!
Game controls for Geki2 and Geki3 are identical as follows:
Up - Arrow up key
Down - Down arrow key
Right - Right arrow key
left - Left arrow key
Shoot - z or Space
Pause - s
Geki2 and Geki3 are fun and can kill some time, but definitely aren't that (professional) as other spaceship shoot'em'up arcades for Linux and BSD. Games like Starfighter , Critical Mass or powermanga .
Lest that they are two worthy to install and play on your Free Software OS.
Tags: action gt, arcade shooter, atmosphere, boring days, BSD, debian gnu, Dying, Free, free software games, fun, game experience, game music, game startup, Geki, Gnome, gnome applications, gnu linux, gt games, key, level, linux games, megablast, menu, most linux distributions, move, music effects, nbsp, option, os platforms, package, penguin, reason, screenshot, shooter, shooter games, software, something, Space, spaceship, startup, time, Ubuntu, ubuntu linux, vertical direction, xenon 2
Posted in Entertainment, Games Linux, Linux, Linux and FreeBSD Desktop | 1 Comment »
Friday, October 7th, 2011 
RarCrack is able to crack rar and 7z archive files protected by password on Linux.
The program is currently at release version 0.2, so its far from perfection, but at least it can break rars.
RarCrack is currently installable on most Linux distributions only from source, to install on a random Linux distro, download and make && make install . RarCrack’s official site is here, I’ve mirrored the current version of RarCrack for download here . To install rarcrack from source using the mirrored version:
linux:~# wget https://www.pc-freak.net/files/rarcrack-0.2.tar.bz2
...
linux:~# tar -jxvvf rarcrack-0.2.tar.bz2
linux:~# cd rarcrack-0.2
linux:~/rarcrack-0.2# make
...
linux:~/rarcrack-0.2# make install
...
On FreeBSD, rarcrack is available and installable via the ports tree, to install on FreeBSD:
freebsd# cd /usr/ports/security/rarcrack
freebsd# make && make install
...
To use RarCrack to crack rar, zip or 7z archive file:
freebsd% rarcrack rar_file_protected_with_password.rar --type rar
The argument –type rar is optional, in most archives RarCrack should detect the archive automatically. The –type option could also take the arguments of rar and 7z .
I’ve created a sample rar file protected with password linux_then_and_now.png.rar . The archive linux_then_and_now.png contains a graphic file illustrating the linux growth in use in computers, mobiles and servers. linux_then_and_now.png.rar is protected with the sample password parola
RarCrack also supports threads (a simultaneous instance spawned copies of the program). Using threads speeds up the process of cracking and thus using the –threads is generally a good idea. Hence a good way to use rarcrack with the –threads option is:
freebsd% rarcrack linux_then_and_now.png.rar --threads 8 --type rar
RarCrack! 0.2 by David Zoltan Kedves (kedazo@gmail.com)
INFO: the specified archive type: rar
INFO: cracking linux_then_and_now.png.rar, status file: linux_then_and_now.png.rar.xml
Probing: '0i' [24 pwds/sec]
Probing: '1v' [25 pwds/sec]
RarCrack‘s source archive also comes with three sample archive files (rar, 7z and zip) protected with passwords for the sake of testing the tool.
One downside of RarCrack is its extremely slow in breaking the passwords on my Lenovo notebook – dual core 1.8ghz with 2g ram it was able to brute force only 20-25 passwords per second.
This means cracking a normal password of 6 symbols will take at least 5 hours.
RarCrack is also said to support cracking zip passwords, but my tests to crack password protected zip file did not bring good results and even one of the tests ended with a segmentation fault.
To test how rarcrack performs with password protected zip files and hence compare if it is superior or inferior to fcrackzip, I used the fcrackzip’s sample pass protected zip noradi.zip
hipo@noah:~$ rarcrack --threads 8 noradi.zip --type zip
2 by David Zoltan Kedves (kedazo@gmail.com)
INFO: the specified archive type: zip
INFO: cracking noradi.zip, status file: noradi.zip.xml
Probing: 'hP' [386 pwds/sec]
Probing: 'At' [385 pwds/sec]
Probing: 'ST' [380 pwds/sec]
As you can see in above’s command output, the zip password cracking rate of approximately 380 passwords per second is a bit quicker, but still slower than fcrackzip.
RarCrack seg faults if cracking a pass protected zip is passed on without specifying the –type zip command arguments:
linux:~$ rarcrack --threads 8 noradi.zip
RarCrack! 0.2 by David Zoltan Kedves (kedazo@gmail.com)
Segmentation fault
While talking about cracking protected rar and zip archives with password, its worthy to mention creating a password protected archive with Gnome Desktop on Linux and FreeBSD is very easy.
To create the password protected archive in Gnome graphic environment:
a. Point the cursor to the file you want to archive with password
b. Press on Other Options and fill in the password in the pwd dialog
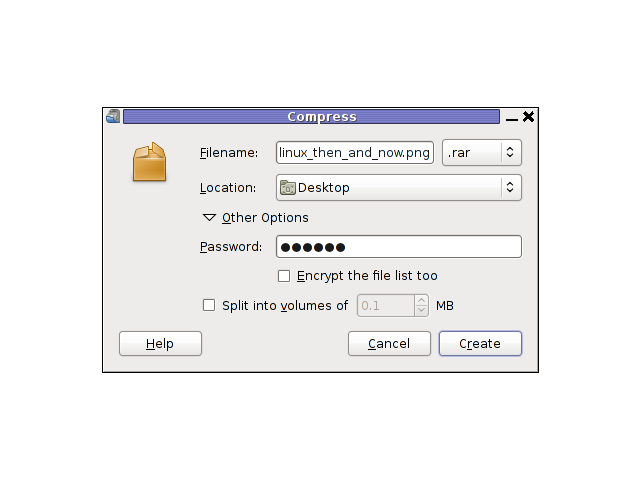
I think as of time of writting, no GUI frontend interface for neither RarCrack or FcrackZip is available. Lets hope some good guy from the community will take the time to write extension for Gnome to allow us to crack rar and zip from a nice GUI interface.
Tags: amp, archive type, argument, argument type, bz2 linux, com, current version, download, fcrackzip, file, freak, Gmail, Gnome, gnu linux, instance, Linux, linux cd, linux growth, linux tar, most linux distributions, option, password, png, ports, random linux, rar, rarcrackfreebsd, rarINFO, second, segmentation, status, tar bz2, time, tool, tree, type, type option, usr, version linux, wget, xml, zoltan
Posted in Computer Security, System Administration, Various | 3 Comments »
Wednesday, September 28th, 2011 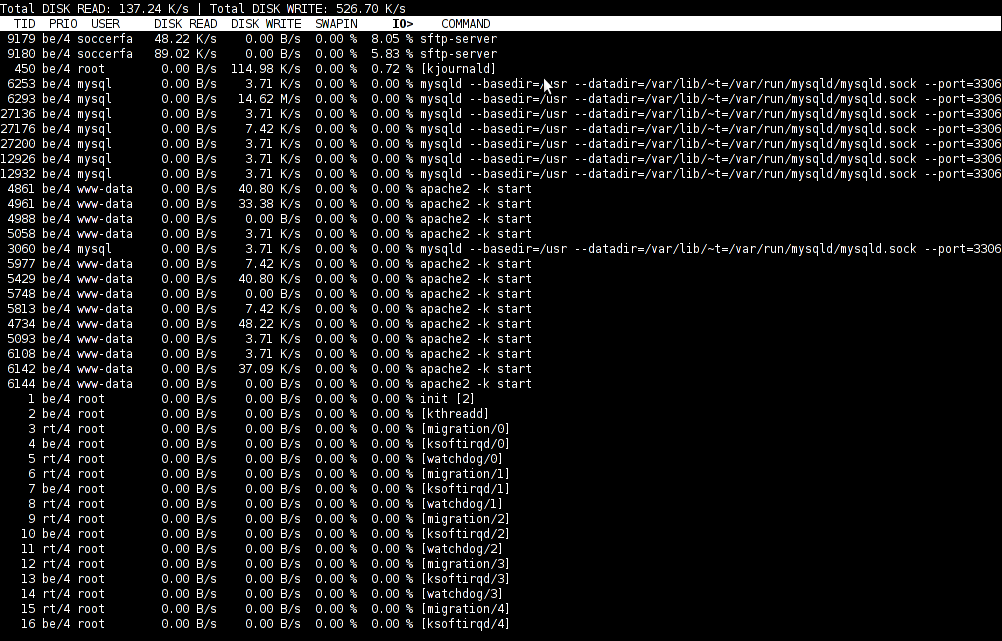
To find out which programs are causing the most read/write overhead on a Linux server one can use iotop
Here is the description of iotop – simple top-like I/O monitor, taken from its manpage.
iotop does precisely the same as the classic linux top but for hard disk IN/OUT operations.
To check the overhead caused by some daemon on the system or some random processes launching iotop without any arguments is enough;
debian:~# iotop
The main overview of iostat statistics, are the:
Total DISK READ: xx.xx MB/s | Total DISK WRITE: xx.xx K/s
If launching iotop, shows a huge numbers and the server is facing performance drop downs, its a symptom for hdd i/o overheads.
iotop is available for Debian and Ubuntu as a standard package part of the distros repositories. On RHEL based Linuxes unfortunately, its not available as RPM.
While talking about keeping an eye on hard disk utilization and disk i/o’s as bottleneck and a possible pitfall to cause a server performance down, it’s worthy to mention about another really great tool, which I use on every single server I administrate. For all those unfamiliar I’m talking about dstat
dstat is a – versatile tool for generating system resource statistics as the description on top of the manual states. dstat is great for people who want to have iostat, vmstat and ifstat in one single program.
dstat is nowdays available on most Linux distributions ready to be installed from the respective distro package manager. I’ve used it and I can confirm tt is installable via a deb/rpm package on Fedora, CentOS, Debian and Ubuntu linuces.
Here is how the tool in action looks like:
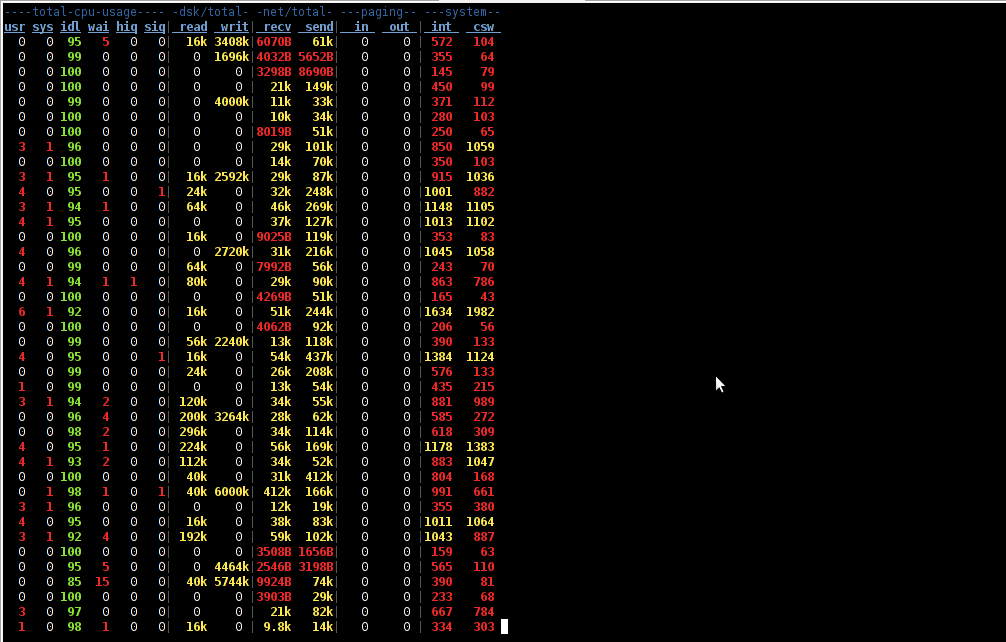
The most interesting things from all the dstat cmd output are read, writ and recv, send , they give a good general overview on hard drive performance and if tracked can reveal if the hdd disk/writes are a bottleneck to create server performance issues.
Another handy tool in tracking hdd i/o problems is iostat its a tool however more suitable for the hard core admins as the tool statistics output is not easily readable.
In case if you need to periodically grasp data about disks read/write operations you will definitely want to look at collectl i/o benchmarking tool .Unfortunately collect is not included as a packaget for most linux distributions except in Fedora. Besides its capabilities to report on servers disk usage, collect is also capable to show brief stats on cpu, network.
Collectl looks really promosing and even seems to be in active development the latest tool release is from May 2011. It even supports NVidia’s GPU monitoring 😉 In short what collectl does is very similar to sysstat which by the way also has some possibilities to track disk reads in time. collectl’s website praises the tool, much and says that in most machines the extra load the tool would add to a system to generate reports on cpu, disk and disk io is < 0.1%. I couldn’t find any data online on how much sysstat (sar) extra loads a system. It will be interesting if some of someone concluded some testing and can tell which of the two puts less load on a system.
Tags: action, bottleneck, CentOS, cmd, description, Disk, disk utilization, drive, drive performance, drop, eye, generating system, GNU, gnu linux, handy tool, interesting things, Linux, linux server, linux top, linuxes, manager, manual states, most linux distributions, overhead, package, performance drop, performance issues, pitfall, program, random processes, recv, repositories, resource statistics, server performance, sIf, system, system resource, tool, Ubuntu, versatile, versatile tool, vmstat
Posted in Linux, System Administration, Various | 5 Comments »




























How to enable Ctrl+Alt+Backspace in Ubuntu 11.10 (Oneiric Ocelot) Linux
Monday, January 16th, 2012My sister, experience some programs running with wine (Windows Emulator) to crash on her Ubuntu 11.10.
As she is quite new with Linux, she has no idea about the existence of CTRL ALT BACKSPACE key combination to restart a hanged GNOME, KDE by directly killing the Xorg server.
I felt obliged to explain her it is better to use CTRL ALT BACKSPACE X kill switch instead of restarting the whole Linux kernel (which basiclly is working) and that it is just the display keeping blacnk.
Pressing the would kill Xorg and therefore all applicatins previously running on top of it will die. In Ubuntu Xorg is configured to run via gdm, so once killed it will automatically reload the GDM (Gnome Display Manager).
I was about to explain her that its better she use CTRL+ALT+BACKSPACE instead of restarting the whole system but suddenly I realized this is not working.
In UBUNTU 11.10 and I guess in all UBUNTU's after 9.04 CTRL ALT BACKSPACE is substituted with the key switch combination ALT PRINTSCREEN K, I've explained her about that.
This change is actually a change implied by most Linux distributions nowdas and is some kind of change in Xorg newer versions…
To enable back the CTRL + ALT + BACKSPACE , I've issued cmd:
stanimira@ubuntu~:$ echo' setxkbmap -option terminate:ctrl_alt_bksp' >> ~/.xinitrc
An alternative way to set setxkbmap -option terminate:ctrl_alt_bksp to run on Ubuntu user login is by setting it as a startup application using;
stanimira@ubuntu:~$ gnome-session-properties
Press the Add button and type in the box to appear;
Name: setxkbmap
Command: setxkbmap -option terminate:ctrl_alt_bksp
Comment: setxkbmap
Reverting the Xserver kill switch back to the classical Ctrl+Alt+Backspace should also be running fine on older Ubuntu Linuces – 11.04, 10.10, 10.04 etc.
Tags: add button, Alt, Auto, backspace, Button, change, Comment, Ctrl, Display, Draft, existence, GDM, Gnome, kde, key switch, kill, kill switch, Linux, linux kernel, login, most linux distributions, ocelot, option, Press, printscreen, Reverting, session properties, setxkbmapCommand, startup, startup application, switch combination, type, Ubuntu, wine, wine windows, xinitrcAn, Xorg, xserver
Posted in Linux, Linux and FreeBSD Desktop | No Comments »