Color mind influence has been longly researched. It is researched and there are some findingings on how we people react on colors. This researches are not much known and most of them are not put on the internet (??) One model claiming to have explained how colors influence is called HBDI – Herrmann Brain Dominance Instruments.
In the picture beginning of this post, I have presented a quick "Personal Profile" of HBDI on how one think in order to determine in "which colors" one tends to think more ___
In short HBDI model claims to explain how people think in another model.
My personal view of it is it is like most science nowdays more based on faith than on a clearly conducted scientific research and facts. We know pretty well many people tried to explain how brain operates and many people give models to explain it however none of the models could grasp in completeness the complexity of human brain. Hence Businessman people who use this model in their daily life and they push it to us has put the model in action not that they know it is working but rather they believe it does .., Saying this few words as introduction I will contninue onwards to explain you about HBDI as in the business world it is considered as a "Strategic Asset" for a company success. Hence the use of richest companies of the model has a serious impact on us the common people and unknowing (uninformed) computer users.
Some of the companies who integrated the HBDI to their models we all know are of course not strangely Microsoft and Google
;;;
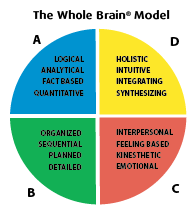
Below I present you a picture showing the HBDI The Whole Brain Model |||
Next I show you Microsoft Windows OS worldly "infamous" flag |||

You can see for yourself the basic color from HBDI WHOLE brain model are integrated in the Microsoft flag, only the order of colors present and the color gamma is different;;;;
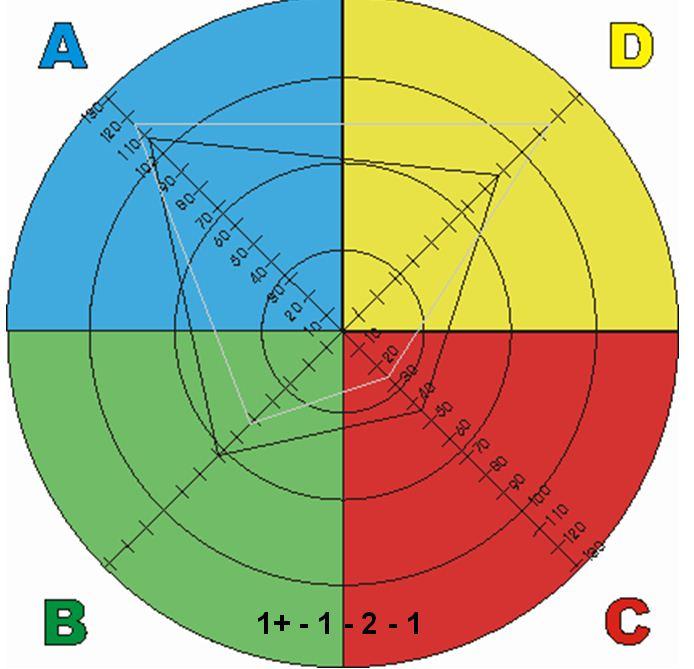
The basic colors in HBDI model to explain how human brain works is separated in 4 segments as you can see from above screenshot. There are a number of tests one can do to determine what is his exact HBDI profile, and in abstract terms in which kind of colors he prefers to think.
There are a whole "army" of people involved into this sect like philosophy (I call it philosophy as surely every model that tries to explain everything is doomed to fail it is the nature in which God created the universe so complex and he put us be part of it and not controllers of it that any Universal model trying to explain it has never succeeded so far. The HBDI has some fruits for the only reason it is believed to work well by the people with money.
As you see in the colors HBDI claims there are 4 segments corresponding to four basic colors
Each of the colors is an indicator on how the person tends to think the BLUE people as HBDI practicioners (believers) calls them are —
Analytical, Fact Based, Logal, Quantitative
The YELLOW oriented people are claimed to be —
Holistic, Intuitive, Integrating, Synthesizing
The GREEN ones in model terms are interested in —
Organizing, Sequentiality, Planning, Detailizing facts
Finally the RED Ones are said to be —
Interpersonal, Feeling based, Kinesthetic, Emotional
Now as you can understand this model though it looks like promising is based on a philosophy which rejects the existing of spirit realm God Angels or good or evil. It claims everything we're are or we want to be can be achieved following the HBDI to develop your own brain.
This model as every human made model however does reject the fact that besides internal factors and brains we're put into external environment most of which we cannot control and therefore even if we try our best to have certain goals and complete them the external uncontrolled facts can be a reason to stop us to complete our goals.
Now back to my point, that Google, Microsoft and probably many other products and physical goods are heavily using the HBDI color scheme ;;;
Here is the Google Inc. Logo the color trait of HBDI is there:

For those doubting that Google Inc. and Microsoft Inc. are along the false believers of HBDI color scheme brain ideology I present below the Logo of Google Web Browser =- Google Chrome

It is evident 4 colors used as a main ones in the HBDI tool are present in Google Chrome just like in Microsoft Windows logo flag, the only difference is in the order of colors.
Also it is interesting the name Chrome that Google Chrome took is most likely taken from Aldous Huxley's – Brave New World (A book depicting a short future highly conditioned society) , the book story line goes around a society programmed to do the things they do.
I assume it is very likely that Google's founders Sergey Brin or some of their subordinate working for Google are very much into the idea of conditioning people just like in the book and this is most likely the reason they choose the Chrome as a title for Google's browser ,,,
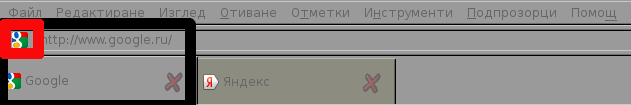
The 4 Colors from HBDI yellow, green, blue, red are embedded also in the google .ico file (the little icon showing in browser URL bar), below is a screenshot of a tab where google is opened showing the .ico image:
Do you remember the good old Windows XP start button, have you noticed the Windows flag embedded in it, if not let me show you;;;

But wait the Windows flag placed on the left bottom of Ms Windows-es is not only on XP it is also on Windows 3.11 cover, Winblows 98, Vista, Windows 2003, Windows 2007 and actually all the M$ operating systems ever produced since the very early days M$ become a top OS producer :::


Here is also the 4 colored (a bit like Nazi like looking) flag on M$ Win-doze 7 |||
Also the Microsoft Flag is positioned on the bottom left screen on purpose. It is well known fact that most of the world (except Arabic) are used to read the text from Left to Right
, therefore it is natural for our eyesight to look for the text on the left side. I just wonder why they placed the START on the bottom and not on top. It is natural we read text and books from the most top to the most bottom ,,,.,
Even Apple Computers nowdays Macs has most likely used the HBDI as the main 4 colors and some gamma from rainbow colors are present on their Classical Apple Computer logo

Makes me wonder if Jobs employed the HBDI model in his company. Well what is the reason for people loving so much this rainbow colors combination. If we think for a second outside of HBDI's brainwashing ideology for what each color would stand for. Well it is simple is comes from our young years most of the people between age 2 and 50 years has been more or less exposed to the so colorful Kids Cartoons, which are all so colorfully painted. Since our very early age we've placed in us a love for colorfulness outlook (well again not all of us for example I prefer less colors, I'm sure there are plenty of people who don't like the heavy colors we see in almost everywhere around us).
The problem with this 4 colors use on purpose and all this unnatural color placing everywhere is that it is unnatural and not in good synergy with our surrounding natural environment. Therefore I personally think using a colorful color paintings on everywhere in both computer programs and the physical world plays us a bad joke and is one of the reasons so many people are on the virge to get crazy nowdays and many have already had already cracked out.
It is my firm believe more and more people should be educated on the harm of HBDI and the fact that, we're forced to 'live it' unwilfully every day by using even as "simple things" as computers and daily technology or buying food in the super market ,,,