Yesterday I drinked 200 gr. of Vodka yesterday Night, it was pretty refreshing for me but I got drunk a little.I'm smoking again … Things are going bad in my life recently. I have health issues. And I intend to go to doctor today.Yesterday I went to the polyclinic but my personal Dr. Nikolay was not there (I was angry, I went to doctor once in years and he is not there) so I'll try again today. I had pains somewhere around the stomach. At least at work things are going smoothly at least God hears my prayers about this. I'm very confused and I have completely no idea what to do with my life. Yesterday I was out with Lily and Kiril on the fountain. The previous day Nomen, I, Yavor, Kiro and Bino went to the "Kobaklyka" (a woody place which is close to Dobrich.) Well that's most of what's happening lately with my life. I wrote a little script to make that nautilus to get restarted if it starts burning the cpu. It's a dumb script (the bad thing is that I'm loosing form scripting, Well I don't script much lately). Here is the script http://pcfreak.d-bg.net/bshscr/restart_nautilus.sh https://www.pc-freak.net/bshscr/restart_nautilus.sh. The days before the 4 days weekend, I hat to spend a lot of time on one of the servers fighting with Spammers. Hate spammers really! I ended removing bounce messages at all for one of the domains, which fixed the bounce spam method spammers use (btw qmail's chkuser seems to not work properly for some reason) … Also I started watching Stargate – SG1. First I thought it's a stupid sci-fi serial. But after the first serie I now think it has it's good moments :]. Also I had something like a Mortification Day going on during Monday. The whole day I listened to Mortification (The first Christian Death Metal Band). I Liked much the "Hammer of God" album. In the evening Sabin (Bino) came home and we watched some Mortification videos at Youtube. Right now I listen again to "Ever – Idyll" a pretty great song. And yeah I keep listening to ChristianIndustrial.net a lot, a great radio. Try it if you haven't!END—–
Posts Tagged ‘Qmail’
Vodka! :)
Wednesday, September 12th, 2007Tags: album, bg, bounce, christian, christian death metal, CPU, death metal band, form, gr, Hammer, hammer of god, hat, health, health issues, kiril, lily, Monday, mortification, nautilus, place, polyclinic, prayers, Qmail, quot, reason, Sabin, sci fi, script, servers, something, Spammers, stomach, time, vodka, weekend, what to do with my life, woody, work, yeah
Posted in Everyday Life, Various | No Comments »
Linux Send Monitoring Alert Emails without Mail Server via relay SMTP with ssmtp / msmtp
Friday, July 10th, 2020 
If you have to setup a new Linux server where you need to do a certain local running daemons monitoring with a custom scripts on the local machine Nagios / Zabbix / Graphana etc. that should notify about local running custom programs or services in case of a certain criteria is matched or you simply want your local existing UNIX accounts to be able to send outbound Emails to the Internet.
Then usually you need to install a fully functional SMTP Email server that was Sendmail or QMAIL in old times in early 21st century andusually postfix or Exim in recent days and configure it to use as as a Relay mail server some Kind of SMTP.
The common Relay smtp setting would be such as Google's smtp.gmail.com, Yahoo!'s smtp.mail.yahoo.com relay host, mail.com or External configured MTA Physical server with proper PTR / MX records or a SMTP hosted on a virtual machine living in Amazon's AWS or m$ Azure that is capable to delivere EMails to the Internet.
Configuring the local installed Mail Transport Agent (MTA) as a relay server is a relatively easy task to do but of course why should you have a fully stacked MTA service with a number of unnecessery services such as Email Queue, Local created mailboxes, Firewall rules, DNS records, SMTP Auth, DKIM keys etc. and even the ability to acccept any emails back in case if you just want to simply careless send and forget with a confirmation that remote email was send successfully?
This is often the case for some machines and especially with the inclusion of technologies such as Kubernettes / Clustered environments / VirtualMachines small proggies such as ssmtp / msmtp that could send mail without a Fully functional mail server installed on localhost ( 127.0.0.1 ) is true jams.
ssmtp program is Simple Send-only sendMail emulator has been around in Debian GNU / Linux, Ubuntu, CentOS and mostly all Linuxes for quite some a time but recently the Debian package has been orphaned so to install it on a deb based server host you need to use instead msmtp.
1. Install ssmtp on CentOS / Fedora / RHEL Linux
In RPM distributions you can't install until epel-release repository is enabled.
[root@centos:~]# yum –enablerepo=extras install epel-release
[root@centos:~]# yum install ssmtp
2. Install ssmp / msmtp Debian / Ubuntu Linux
If you run older version of Debian based distribution the package to install is ssmtp, e.g.:
root@debian:~# apt-get install –yes ssmtp
On Newer Debians as of Debian 10.0 Buster onwards install instead
root@debian:~# apt install –yes msmtp-mta
can save you a lot of effort to keep an eye on a separately MTA hanging around and running as a local service eating up resources that could be spared.
3. Configure Relay host for ssmtp
A simple configuration to make ssmtp use gmail.com SMTP servers as a relay host below:
linux:~# cat << EOF > /etc/ssmtp/ssmtp.conf
# /etc/ssmtp/ssmtp.conf
# The user that gets all the mails (UID < 1000, usually the admin)
root=user@host.name
# The full hostname. Must be correctly formed, fully qualified domain name or GMail will reject connection.
hostname=host.name
# The mail server (where the mail is sent to), both port 465 or 587 should be acceptable
# See also https://support.google.com/mail/answer/78799
mailhub=smtp.gmail.com:587
#mailhub=smtp.host.name:465# The address where the mail appears to come from for user authentication.
rewriteDomain=gmail.com
# Email 'From header's can override the default domain?FromLineOverride=YES
# Username/Password
AuthUser=username@gmail.com
AuthPass=password
AuthMethod=LOGIN
# Use SSL/TLS before starting negotiation
UseTLS=YES
UseTLS=Yes
UseSTARTTLS=Yes
logfile ~/.msmtp.logEOF
This configuration is very basic and it is useful only if you don't want to get delivered mails back as this functionality is also supported even though rarely used by most.
One downside of ssmtp is mail password will be plain text, so make sure you set proper permissions to /etc/ssmtp/ssmtp.conf
– If your Gmail account is secured with two-factor authentication, you need to generate a unique App Password to use in ssmtp.conf. You can do so on your App Passwords page. Use Gmail username (not the App Name) in the AuthUser line and use the generated 16-character password in the AuthPass line, spaces in the password can be omitted.
– If you do not use two-factor authentication, you need to allow access to unsecure apps.
4. Configuring different msmtp for separate user profiles
SSMTP is capable of respecting multiple relays for different local UNIX users assuming each of whom has a separate home under /home/your-username
To set a certain user lets say georgi to relay smtp sent emails with mail or mailx command create ~/.msmtprc
linux:~# vim ~/.msmtprc
Append configuration like:
# Set default values for all following accounts.
defaults
port 587
tls on
tls_trust_file /etc/ssl/certs/ca-certificates.crt
account gmail
host smtp.gmail.com
from <user>@gmail.com
auth on
user <user>
passwordeval gpg –no-tty -q -d ~/.msmtp-gmail.gpg
# Set a default account
account default : gmail
To add it for any different user modify the respective fields and set the different Mail hostname etc.
5. Using mail address aliases
msmtp also supports mail aliases, to make them work you will need to have file /etc/msmptrc with
aliases /etc/aliases
Standard aliasses them should work
linux:~# cat /etc/aliases
# Example aliases file
# Send root to Joe and Jane
root: georgi_georgiev@example.com, georgi@example.com
# Send everything else to admin
default: admin@domain.example
6. Get updated when your Debian servers have new packages to update
msmpt can be used for multiple stuff one example use would be to use it together with cron to get daily updates if there are new debian issued security or errata update pending packages, to do so you can use the apticron shell script.
To use it on debian install the apticron pack:
root@debian:~# apt-get install –yes apticron
apticron has the capability to:
* send daily emails about pending upgrades in your system;
* give you the choice of receiving only those upgrades not previously notified;
* automatically integrate to apt-listchanges in order to give you by email the
new changes of the pending upgrade packages;
* handle and warn you about packages put on hold via aptitude/dselect,
avoiding unexpected package upgrades (see #137771);
* give you all these stuff in a simple default installation;
To configure it you have to place a config copy the one from /usr/lib/apticron/apticron.conf to /etc/apticron/apticron.conf
The only important value to modify in the config is the email address to which an apt-listchanges info for new installable debs from the apt-get dist-upgrade command. Output from them will be be send to the configured EMAIL field in apticron.conf.
EMAIL="<your-user@email-addr-domain.com>"
The timing at which the offered new pending package update reminder will be sent is controlled by /etc/cron.d/apticron
debian:~# cat /etc/cron.d/apticron
# cron entry for apticron48 * * * * root if test -x /usr/sbin/apticron; then /usr/sbin/apticron –cron; else true; fi
apticron will use the local previous ssmtp / msmpt program to deliver to configured mailbox.
To manually trigger apticron run:
root@debian:~# if test -x /usr/sbin/apticron; then /usr/sbin/apticron –cron; else true; fi
7. Test whether local mail send works to the Internet
To test mail sent we can use either mail / mailx or sendmail command or some more advanced mailer as alpine or mutt.
Below is few examples.
linux:~$ echo -e "Subject: this is the subject\n\nthis is the body" | mail user@your-recipient-domain.com
To test attachments to mail also works run:
linux:~$ mail -s "Subject" recipient-email@domain.com < mail-content-to-attach.txt
or
Prepare the mail you want to send and send it with sendmail
linux:~$ vim test-mail.txt
To:username@example.com
From:youraccount@gmail.com
Subject: Test Email
This is a test mail.
linux:~$ sendmail -t < test-mail.txt
Sending encoded atacchments with uuencode is also possible but you will need sharutils Deb / RPM package installed.
To attach lets say 2 simple text files uuencoded:
linux:~$ uuencode file.txt myfile.txt | sendmail user@example.com
echo "
To: username@domain.com From: username@gmail.com Subject: A test Hello there." > test.mail
linux:~$ cat test.mail | msmtp -a default <username>@domain.com
That's all folks, hope you learned something, if you know of some better stuff like ssmtp please shar e it.
Tags: aline, delivery, exim, linux?, mail, mailx, msmpt, msmtp, mutt, no mail server, postfix, Qmail, recipient, send email, sendmail, server, SSMTP, test email
Posted in Email clients, Linux, Linux and FreeBSD Desktop, Sendmail | 1 Comment »
How to solve qmail-inject: fatal: qq temporary problem (#4.3.0) Qmail and Qmail Scanner problems on Debian Linux Wheezy
Monday, October 16th, 2017 
Below QMAIL error
qmail-inject: fatal: qq temporary problem (#4.3.0)
occured to me right after upgraded from Debian Linux Squeeze 6 to Debian 7 Wheezy,
qmail-inject: fatal: qq temporary problem (#4.3.0) is really terrible error and I only experienced that error in my Thunderbird during sending mails, mail receiving doesn't work either, so as normally when there are problems with Qmail its a lot of puzzling until you get it.
There is no even trace in logs on what might be causing it, strangely enough nothing in qmail-smtpd, qmail-send logs, the mail server and all components seemed to work perfectly fine I checked whether there are libraries that are missing with a small loop line as follows:
root@pcfreak:/var/log/qmail/qmail-smtpd# for i in $(ls -1 /var/qmail/bin/*); do ldd $i |grep -i "not found"; done
root@pcfreak:/var/log/qmail/qmail-smtpd#
The absence of result indicates, all binaries are properly linked and no found mmissing libraries.
After investigating closely what might be wrong and reading comments on Thibs QmailRocks Install Qmail-Scanner page, I realied
the error might be caused, because of problems with suid perl, as I already checked my earlier post in which I seemed to have faced the same qmail-inject: fatal: qq temporary problem (#4.3.0) error on Debian Wheezy and explained the possible reasons what might be causing the qq qmail error here as well
and a related issue I experienced earlier with qmail scanner unable to create files in previous article here Suid Perl no longer available as a package and therefore because of the inability of perl to run as root anymore in Debian Wheezy, qmail-scanner-queue.pl script did not work either.
root@pcfreak:/downloads/simscan-1.4.0# 320 echo "hi, testing." > /tmp/mailtest.txt
root@pcfreak:/downloads/simscan-1.4.0# env QMAILQUEUE=/var/qmail/bin/qmail-scanner-queue /var/qmail/bin/qmail-inject you@yourdomain.com < /tmp/mailtest.txt
YOU HAVEN'T DISABLED SET-ID SCRIPTS IN THE KERNEL YET!
FIX YOUR KERNEL, PUT A C WRAPPER AROUND THIS SCRIPT, OR USE -u AND UNDUMP!
qmail-inject: fatal: qq permanent problem (#5.3.0)
root@pcfreak:/downloads/simscan-1.4.0# /var/qmail/bin/qmail-scanner-queue
YOU HAVEN'T DISABLED SET-ID SCRIPTS IN THE KERNEL YET!
FIX YOUR KERNEL, PUT A C WRAPPER AROUND THIS SCRIPT, OR USE -u AND UNDUMP!
A short note to make here is qmail-scanner-queue and qmail-scanner-queue.pl are set with suid bit set as follows:
root@pcfreak:/home/hipo/info# ls -al /var/qmail/bin/{qmail-scanner-queue,qmail-scanner-queue.pl}
-rwsr-sr-x 1 qscand qscand 6814 окт 14 17:22 /var/qmail/bin/qmail-scanner-queue*
-rwsr-sr-x 1 qscand qscand 158880 окт 14 23:52 /var/qmail/bin/qmail-scanner-queue.pl*
Good to say here is qmail-scanner-queue is a suid wrapper binary that actually invokes qmail-scanner-queue.pl
root@pcfreak:/downloads/simscan-1.4.0# su hipo
hipo@pcfreak:/downloads/simscan-1.4.0$ /var/qmail/bin/qmail-scanner-queue.pl -g
perlscanner: generate new DB file from /var/spool/qscan/quarantine-events.txt
hipo@pcfreak:/downloads/simscan-1.4.0$ exitroot@pcfreak:/downloads/simscan-1.4.0# cp /downloads/qmail-scanner-2.11st/contrib/logrotate.qmail-scanner /etc/logrotate.d/qmail-scanner
root@pcfreak:/downloads/simscan-1.4.0# chmod 644 /etc/logrotate.d/qmail-scanner
root@pcfreak:/downloads/simscan-1.4.0# cd /downloads/qmail-scanner-2.11st/contrib
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# chmod 755 test_installation.sh
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# ./test_installation.sh -doit
Sending standard test message – no viruses… 1/4
qmail-inject: fatal: qq temporary problem (#4.3.0)
Bad error. qmail-inject died
This are the other things, I've done to fix possible permission issues
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# sudo -u qscand /var/qmail/bin/qmail-scanner-queue.pl -z
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# chown qscand:qscand /var/spool/qscan/qmail-scanner-queue-version.txt
In /etc/sudoers add following lines:
root@pcfreak:~# vim /etc/sudoers
ALL ALL=(qscand) NOPASSWD: /var/qmail/bin/qmail-scanner-queue.pl
##necroleak ALL=(ALL) ALL
Defaults env_keep +="TCPREMOTEIP TCPREMOTEHOST TCPREMOTEINFO REMOTE_OS REMOTE_COUNTRY QS_SPAMASSASSIN SA_ONLYDELETE_HOST SA_WHITELIST"
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# cat /etc/sudoers# /etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# See the man page for details on how to write a sudoers file.
#Defaults env_reset
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL) ALL
hipo ALL=(ALL) ALL
ALL ALL=(qscand) NOPASSWD: /var/qmail/bin/qmail-scanner-queue.pl
##necroleak ALL=(ALL) ALL
Defaults env_keep +="TCPREMOTEIP TCPREMOTEHOST TCPREMOTEINFO REMOTE_OS REMOTE_COUNTRY QS_SPAMASSASSIN SA_ONLYDELETE_HOST SA_WHITELIST"
# Allow members of group sudo to execute any command
# (Note that later entries override this, so you might need to move
# it further down)
%sudo ALL=(ALL) ALL
#
#includedir /etc/sudoers.d
In case you wonder why we put the line in /etc/sudoers:
Defaults env_keep +="TCPREMOTEIP TCPREMOTEHOST TCPREMOTEINFO REMOTE_OS REMOTE_COUNTRY QS_SPAMASSASSIN SA_ONLYDELETE_HOST SA_WHITELIST"
The reason behind this is that by default sudo resets the environment variables when executing the command. Thus qmail-scanner cannot recognize the important info regarding the incoming mail and treats everything as coming from localhost, which leads to passing everything without scanning. The above line preserves the important ENV variables for qmail-scanner.
In /etc/sudoers add following lines:
root@pcfreak:/downloads/qmail-scanner-2.11st/contrib# vim /var/qmail/bin/qmail-scanner-queue.pl
Right after comments or in Line 1 ADD
my $real_uid="qscand";
my $effective_uid="qscand";
Also somewhere in the beginning of scripts lets say after above two variable declarations add:
$ENV{'PATH'}='/bin:/usr/bin';
$whoami = getpwuid($<) || "unknown";
if($whoami ne "qscand") {
exec("/usr/bin/sudo -u qscand /var/qmail/bin/qmail-scanner-queue.pl") || die;
}
To prevent your users logged in on physical console and via SSH it is necessery to disable emergency logs for users in syslog / rsyslog, otherwise due to bug, users will logged in will get flooded with messages such as:
Message from syslogd@pcfreak at Oct 15 16:43:04 …
qmail-scanner-queue.pl: qmail-scanner[6834]: Clear:RC:0(95.142.194.223):SA:0(-2.0/2.0): 2.959242 10574 admin@notify.vk.com hipo@www.pc-freak.net Светлана_Георгиева_оставила_Вам_личное_соо� <36b63ec9a0ce7ecc570de2fcbba6ed73@localhost.localdomain> 1508074981.6836-1.pcfreak:6219 1508074981.6836-0.pcfreak:545
open /etc/rsyslog.conf and find the line starting with:
root@pcfreak:~# vim /etc/rsyslog.conf
*.emerg
add
;user.noneright after it so it reads like:
*.emerg;user.none
Tags: Fatal, problem, Qmail, qmail-inject:, Solve, Temporary
Posted in Qmail, System Administration | 1 Comment »
How to work around STARTTLS Qmail Thunderbird / Outlook mail sending (error) issues
Wednesday, October 26th, 2011 
After configuring a new Qmail+POP3+IMAP with vpopmail install based on Thibs QmailRocks I faced some issues with configuring mail accounts in Mozilla Thunderbird. The problem is also present in Microsoft Outlook Express as some colleagues working on Windows reported they can't configure there email accounts in Outlook either.
The issue was like this, the mail server is running fine, and I can send without issues directly from the server shell with mail command, however in Thunderbird I could only fetch the messages via POP3 or IMAP, whever I give a try to send one I got the error:
Sending of Message Failed
The message could not be sent using SMTP server for an
unknown reason. Please verify that SMTP server settings are correct and try
again, or contact your network administrator
Here is a screenshot preseting the issue, taken from my Thunderbird:
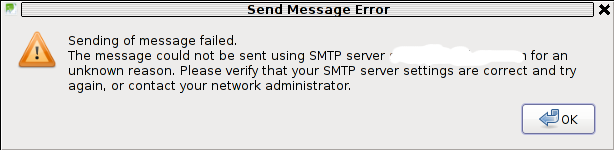
The reason for this error is an automatic setting that is being configured in Thunderbird in New Account Creation time:
Thunderbird queries the mail server and asks for the type of encryptions available for both POP3 and SMTP MX primary host.
Seeing that it supports STARTTLS data transfer encryption mail protocol for both POP3 / IMAP, Thunderbirds auto configuration does place STARTTLS to be used with SMTP and POP3
The incorrect setting which is being automatically filled in can be checked in following these Thunderbird menus:
Edit -> Account Settings -> Outgoing Server (SMTP)
If the configured mail account MX server is let's say mail.exampledomain.com one needs to Edit the settings for this SMTP auto configured domains and he will see some example settings like the one shown in the below screenshot:
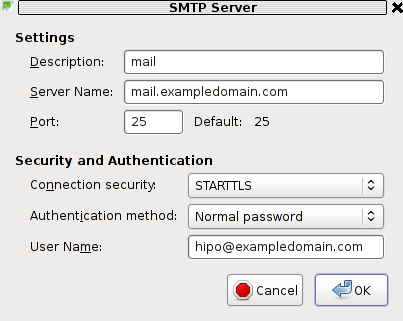
You can see from above's screenshot that the auto configured Connection Security setting is improperly set to: STARTTLS. Usually STARTTLS should be working on SMTP port 25, however it seems the problem consists in the fact that the MAIL FROM and RCPT TO is sent in incorrec time (ain't sure if its before or after the encryption).
Therefore the consequence of this failure to use STARTTLS being detected as the correct encryption type for SMTP lead that the new configured mail server clients were unable tot properly connect and send emails via the SMTP listening server on port 25.
I give a try and changing the Connection Security:STARTTLS to Connection SecuritySSL/TLS immediately resolved the SMTP sending issues. Therefore as I found out the SMTP server is working just fine configured to use my QMAIL on port 465 with Connection Security: SSL/TLS and hence to work around the SMTP sending issues, decided to completely disable the STARTTLS encryption to be reported as a supported encryption by qmail-smtpd
On Thibs QmailRocks and some other Qmail installstions based more or less on qmail.jms1.net service damemontools scripts, this can be done by simply changing a line:
DENY_TLS=0
to
DENY_TLS=1
The qmail start up scripts which these change has to be done if one has configured a mail server based on QmailRocks Thibs updated tutorial are:
1. /service/qmail-smtpd
2. /service/qmail-smtpdssl
A quick way to do the DENY_TLS=0 to DENY_TLS=1 changes via sed is like this:
qmail# sed -e 's#DENY_TLS=0#DENY_TLS=1#g' /service/qmail-smtpd/run >> /tmp/qmail-smtpd-run;qmail# sed -e 's#DENY_TLS=0#DENY_TLS=1#g' /service/qmail-smtpdssl/run >> /tmp/qmail-smtpdssl-run;qmail# mv /tmp/qmail-smtpd-run /service/qmail-smtpd/run
qmail# mv /tmp/qmail-smtpdssl-run /service/qmail-smtpdssl/run
After the correct modifications, of course as usual a qmail restart is required, e.g.:
qmail# qmailctl restart
...
Making this changes, irradicated the sending issues. It's best practice that the account which had issues with sending before is deleted and recreated from scratch.
Hope this helps somebody out there who encounters the same issue. Cheers 😉
Tags: account creation, account settings, administratorHere, anunknown, auto configuration, com, configure, configured, connection security, creation time, email accounts, encryption, Express, host, How to, inco, issue, mail account, mail accounts, mail command, mail protocol, mail server, Microsoft, microsoft outlook express, Mozilla, mozilla thunderbird, mx server, network administrator, Outgoing, outgoing server, outlook, outlook mail, place, pop, Qmail, QmailRocks, reason, screenshot, Sending, server settings, server smtp, Shell, smtp, smtp port 25, starttls, thunderbirds, time, TLS, tmp, type, working
Posted in FreeBSD, Linux, Qmail, System Administration, Various, Web and CMS | 5 Comments »
How to harden Linux Security and imprpove network efficiency on Kernel sysctl Level to Stop SYN flood
Friday, July 8th, 2011
Some long time ago I’ve written an article Optimizing Linux tcp/ip networking
In the article I’ve examined a number of Linux kernel sysctl variables, which significantly improve the way TCP/IP networking is handled by a non router Linux based servers.
As the time progresses I’ve been continuing to read materials on blogs and internet sites on various tips and anti Denial of Service rules which one could apply on newly installed hosting (Apache/MySql/Qmail/Proxy) server to improve webserver responce times and tighten the overall security level.
In my quest for sysctl 😉 I found a few more handy sysctl variables apart from the old ones I incorporate on every Linux server I adminstrate.
The sysctl variables improves the overall network handling efficiency and protects about common SYN/ACK Denial of service attacks.
Here are the extra sysctl variables I started incorporating just recently:
############ IPv4 Sysctl Settings ################
#Enable ExecShield protection (randomize virtual assigned space to protect against many exploits)
kernel.randomize_va_space = 1
#Increase the number of PIDs processes could assign this is very needed especially on more powerful servers
kernel.pid_max = 65536
# Prevent against the common 'syn flood attack'
net.ipv4.tcp_syncookies = 1
# Controls the use of TCP syncookies two is generally a better idea, though you might experiment
#net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
##################################################
#
############## IPv6 Sysctl Settings ################
# Number of Router Solicitations to send until assuming no routers are present.
net.ipv6.conf.default.router_solicitations = 0
# Accept Router Preference in RA? Again not necessery if the server is not a router
net.ipv6.conf.default.accept_ra_rtr_pref = 0
# Learn Prefix Information in Router Advertisement (Unnecessery) for non-routers
net.ipv6.conf.default.accept_ra_pinfo = 0
# disable accept of hop limit settings from other routers (could be used for DoS)
net.ipv6.conf.default.accept_ra_defrtr = 0
# disable ipv6 global unicasts server assignments
net.ipv6.conf.default.autoconf = 0
# neighbor solicitations to send out per address (better if disabled)
net.ipv6.conf.default.dad_transmits = 0
# disable assigning more than 1 address per network interface
net.ipv6.conf.default.max_addresses = 1
#####################################################
To use this settings paste the above sysctl variables in /etc/sysctl.conf and ask sysctl command to read and apply the newly added conf settings:
server:~# sysctl -p
...
Hopefully you should not get errors while applying the sysctl settings, if you get some errors, it’s possible some of the variable is differently named (depending on the Linux kernel version) or the Linux distribution on which sysctl’s are implemented.
For some convenience I’ve created unified sysctl variables /etc/sysct.conf containing the newly variables I started implementing to servers with the ones I already exlpained in my previous post Optimizing Linux TCP/IP Networking
Here is the optimized / hardened sysctl.conf file for download
I use this exact sysctl.conf these days on both Linux hosting / VPS / Mail servers etc. as well as on my personal notebook 😉
Here is also the the complete content of above’s sysctl.conf file, just in case if somebody wants to directly copy/paste it in his /etc/sysctl.conf
# Sysctl kernel variables to improve network performance and protect against common Denial of Service attacks
# It's possible that not all of the variables are working on all Linux distributions, test to make sure
# Some of the variables might need a slight modification to match server hardware, however in most cases it should be fine
# variables list compiled by hip0
### https://www.pc-freak.net
#### date 08.07.2011
############ IPv4 Sysctl Kernel Settings ################
net.ipv4.ip_forward = 0
# ( Turn off IP Forwarding )
net.ipv4.conf.default.rp_filter = 1
# ( Control Source route verification )
net.ipv4.conf.default.accept_redirects = 0
# ( Disable ICMP redirects )
net.ipv4.conf.all.accept_redirects = 0
# ( same as above )
net.ipv4.conf.default.accept_source_route = 0
# ( Disable IP source routing )
net.ipv4.conf.all.accept_source_route = 0
# ( - || - )net.ipv4.tcp_fin_timeout = 40
# ( Decrease FIN timeout ) - Useful on busy/high load server
net.ipv4.tcp_keepalive_time = 4000
# ( keepalive tcp timeout )
net.core.rmem_default = 786426
# Receive memory stack size ( a good idea to increase it if your server receives big files )
##net.ipv4.tcp_rmem = "4096 87380 4194304"
net.core.wmem_default = 8388608
#( Reserved Memory per connection )
net.core.wmem_max = 8388608
net.core.optmem_max = 40960
# ( maximum amount of option memory buffers )
# tcp reordering, increase max buckets, increase the amount of backlost
net.ipv4.tcp_max_tw_buckets = 360000
net.ipv4.tcp_reordering = 5
##net.core.hot_list_length = 256
net.core.netdev_max_backlog = 1024
#Enable ExecShield protection (randomize virtual assigned space to protect against many exploits)
kernel.randomize_va_space = 1
#Increase the number of PIDs processes could assign this is very needed especially on more powerful servers
kernel.pid_max = 65536
# Prevent against the common 'syn flood attack'net.ipv4.tcp_syncookies = 1
# Controls the use of TCP syncookies two is generally a better idea, though you might experiment
#net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
###################################################
############## IPv6 Sysctl Settings ################
# Number of Router Solicitations to send until assuming no routers are present.
net.ipv6.conf.default.router_solicitations = 0
# Accept Router Preference in RA? Again not necessery if the server is not a router
net.ipv6.conf.default.accept_ra_rtr_pref = 0
# Learn Prefix Information in Router Advertisement (Unnecessery) for non-routersnet.
ipv6.conf.default.accept_ra_pinfo = 0
# disable accept of hop limit settings from other routers (could be used for DoS)
net.ipv6.conf.default.accept_ra_defrtr = 0
# disable ipv6 global unicasts server assignmentsnet.
ipv6.conf.default.autoconf = 0
# neighbor solicitations to send out per address (better if disabled)
net.ipv6.conf.default.dad_transmits = 0
# disable assigning more than 1 address per network interfacenet.
ipv6.conf.default.max_addresses = 1
#####################################################
# Reboot if kernel panic
kernel.panic = 20
These sysctl settings will tweaken the Linux kernel default network settings performance and you will notice the improvements in website responsiveness immediately in some cases implementing this kernel level goodies will make the server perform better and the system load might decrease even 😉
This optimizations on a kernel level are not only handy for servers, their implementation on Linux Desktop should also have a positive influence on the way the network behaves and could improve significantly the responce times of opening pages in Firefox/Opera/Epiphany Torrent downloads etc.
Hope this kernel tweakenings are helpful to someone.
Cheers 😉
Tags: adminstrate, amount, anti, apache mysql, autoconf, default, default network, default router, Denial, denial of service, denial of service attacks, exploits, file, harden, How to, imprpove, internet sites, ip networking, ipv, ipv4, ipv6, kernel, kernel level, level, Linux, Linux Security, linux server, memory, network efficiency, non, number, protection, proxy server, Qmail, quot, ra, randomize, reordering, responce, responce times, router linux, routers, rtr, security, security level, serverskernel, Service, solicitations, Source, SYN, syn flood attack, sysctl, time, variables, wmem
Posted in Computer Security, Linux, Linux and FreeBSD Desktop, System Administration | 4 Comments »
Tracking graphically MySQL, Apache and Network performance in web with Munin on Debian Linux
Saturday, March 19th, 2011 
Munin is great software for surveillance software for your MySQL, Apache, Qmail, Postfix and many other of the classical daemon services which most of the Linux, BSD servers online are running on.
1. Munin on Debian Linux is really easy to be installed and comes to executing:
debian:~# apt-get install munin munin-node munin-plugins-extra
2. Link /var/www/munin/ to some VirtualHost or ServerHost
For instance if your munin is to be placed on the domain www.pc-freak.net.net which has the DocumentRoot of /var/www
debian:~# cd /var/www
debian:/var/www# ln -sf /var/www/munin munin
3. Add some extra MySQL related plugins
To check whole list of pmunin plugins you can enable check in /etc/munin/plugins directory
Lets say our Munin will be providing statistics mainly for MySQL, enable this bunch of plugins:
cd /etc/munin/plugins
ln -s /usr/share/munin/plugins/mysql_ mysql_
ln -s /usr/share/munin/plugins/mysql_bytes mysql_bytes
ln -s /usr/share/munin/plugins/mysql_innodb mysql_innodb
ln -s /usr/share/munin/plugins/mysql_isam_space_ mysql_isam_space_
ln -s /usr/share/munin/plugins/mysql_queries mysql_queries
ln -s /usr/share/munin/plugins/mysql_slowqueries mysql_slowqueries
ln -s /usr/share/munin/plugins/mysql_threads mysql_threads
Though above command would enable mysql monitoring it will be not working out of the box. You will find in munin logs error like:
To fix this install libcache-perl and libcache-cache-perl
apt-get install --yes libcache-perl libcache-cache-perl
Then regenerate munin plugin configuration issue cmd:
munin-node-configure --suggest --shell | sh
and restart Munin-node server
service munin-node restart
Munin Node should be able login to the MySQL server using the Debian System Maintenance user however if you should need to create a custom user you can add the following configuration to:
/etc/munin/plugin-conf.d/munin-node
[mysql*]
user root
env.mysqluser muninmonitor
env.mysqlpassword Your-Secret-Password
4. Edit Munin config
Make sure you have at least the following variables enabled in /etc/munin/munin.conf
dbdir /var/lib/munin
htmldir /var/cache/munin/www
logdir /var/log/munin
rundir /var/run/munintmpldir /etc/munin/templates
includedir /etc/munin/munin-conf.d
[localhost.localdomain]
address 127.0.0.1
use_node_name yes
5. Add Munin Alias or Virtualhost
To make Munin Accessible from Webserver you need to at least add an alias create a file
/etc/apache2/conf.d/munin with following content:
vim /etc/apache2/conf.d/munin
Alias /munin /var/cache/munin/www
<Directory /var/cache/munin/www>
Order allow,deny
#Allow from localhost 127.0.0.0/8 ::1
Allow from all
Options None
php_value engine off<IfModule mod_expires.c>
ExpiresActive On
ExpiresDefault M310
</IfModule></Directory>
If you want to access Munin from Apache subdomain create it lets say you want to access it via stats.www.pc-freak.net, use following config file:
vi /etc/apache2/sites-enabled/stats.www.pc-freak.net
<VirtualHost *>
ServerAdmin hipo@www.pc-freak.net
ServerName stats.www.pc-freak.net
DocumentRoot /var/cache/munin/www
<Directory />
Options FollowSymLinks
#AllowOverride All
php_value engine off
</Directory>
LogLevel debug
CustomLog /var/log/apache2/munin/access.log combined
ErrorLog /var/log/apache2/munin/error.log
ServerSignature On
<Directory /var/cache/munin/www>
Order allow,deny
#Allow from localhost 127.0.0.0/8 ::1
Allow from all
Options FollowSymlinks
#AllowOverride All
php_value engine off</Directory>
</VirtualHost>
6. Restart Apache;
debian:~# /etc/init.d/apache2 restart
Now to access the newly installed munin point your favorite browser to (either the subdirectory configured for access or the Virtualhost subdomain):
https://www.pc-freak.net/munin/
or
http://munin.www.pc-freak.net
7. Protecting Munin with a password
As it could be a security leak to expose statistics regarding your server (Disk I/O, Memory, Load Avarage, Apache, MySQL Postfix) operations it is good security practice to protect munin with a password.
I've earlied blogged on how to protect your server munin web-statistics wtih an htaccess password (read it here)
Happy Monitoring
Tags: apache performance, apache2, bsd servers, configuration issue, CustomLog, documentroot, domain pc, freak, great software, Linux, munin, net, node, password, postfix, Qmail, restart apache, security practice, share, surveillance software, Tracking graphically MySQL and Apache performance in web with Munin on Debian, Virtualhost, web, www
Posted in Monitoring, MySQL, System Administration, Web and CMS | 1 Comment »
Installation and Configuration of Clamav antivirus on Debian GNU / Linux
Monday, September 9th, 2013
Clamav Antivirus is one of must have packages installed on a new Debian Linux server. It is not only necessary whether configuring a new Mail server be it Qmail or Postfix but is good to have to always check files on a Webserver. Until few years infecting of Sites with Viruses / Installing WebShells or Backdooring for further access using Perl or PHP vulnerable PHP code was not so common, However nowadays with increase of complexity of languages and increase of not security minded programmers this possibility dramatically increaed. Thus nowadays, whether I configure a new Apache + PHP + CGI support server I always install Clamav AV. Some might argue that Clamav Virus definitions are still too little compared to proprietary solutions like BitDefender / AVG or Avast but since my experience with this under Linux is not so bright as well as Clamav captures essential Viruses and Backdoors I still prefer to keep on with Clamav. Even on home Desktops with Linux clamav is of use as there are plenty of free-ware software for Linux which come only distributed only in a binary form and hence its good to check them with clamav before use whether they don't contain some well known Rootkit or Virus. Over the years Clamav has done great job for me whether I had to clean up "hacked" hosts containing script kiddie exploit scanners or Virus infected ELF binaries
.
1. Installing ClamAV in Debian Wheezy Linux
Before time there was a separate Debian repository called Volatille providing latest version release of Clamav, since Debian Squeeze Volatille project is discontinued, thus installing on Wheezy as a deb package is only available via standard Debian repositories.
apt-get update && apt-get --yes upgrade
...
apt-get install --yes clamav clamav-daemon
As package dependencies you get installed:
clamav clamav-base clamav-freshclam libbz2-1.0 libclamav1 libcurl3 libidn11 ucf
Clamav-Daemon will launch immediately after packages are installed and is available as process name /usr/sbin/clamd
# ps ax |grep -i clam
2641 ? Ssl 6:39 /usr/sbin/clamd
2791 ? Ss 12:04 /usr/bin/freshclam -d --quiet
12300 pts/0 S+ 0:00 grep -i clam
2. Updating Clamav Antivirus Definitions
Its worthy say few words on clamav-freshclam as it is part of ClamAV which is used to update Clamav Virus definitions. Update of ClamAV vir definitions are updating automatically through /usr/bin/freshclam daemon which is started automatically by Debian postconfiguration scripts right after Clamav install.
Manual update of AV definitions can be done also with freshclam.
# freshclam
ClamAV update process started at Sun Sep 8 17:48:36 2013
main.cvd is up to date (version: 54, sigs: 1044387, f-level: 60, builder: sven)
daily.cvd is up to date (version: 17830, sigs: 1696886, f-level: 63, builder: neo)
bytecode.cld is up to date (version: 225, sigs: 42, f-level: 63, builder: dgoddard)
To keep an eye on definition auto-updates (useful to check where something fails), check out in /var/log/clamav/freshclam.log
A sure indication that Anvirus updates are conducting fine should be log records like:
Sun Sep 8 16:27:44 2013 -> ————————————–
Sun Sep 8 17:27:44 2013 -> Received signal: wake up
Sun Sep 8 17:27:44 2013 -> ClamAV update process started at Sun Sep 8 17:27:44 2013
Sun Sep 8 17:27:44 2013 -> main.cvd is up to date (version: 54, sigs: 1044387, f-level: 60, builder: sven)
Sun Sep 8 17:27:44 2013 -> daily.cld is up to date (version: 17830, sigs: 1696886, f-level: 63, builder: neo)
Sun Sep 8 17:27:44 2013 -> bytecode.cld is up to date (version: 225, sigs: 42, f-level: 63, builder: dgoddard)
Sun Sep 8 17:27:47 2013 -> ————————————–
3. Configuring ClamAV
For Desktop use clamav default config is pretty good. However for servers its good to raise 2 up MaxThreads:
By default MaxThreads is 12
MaxThreads 12
Change to from 30 to 80 depending on how powerful machine ClamAV runs, even on some servers more Clamav threads might be necessary
MaxThreads 30
Other value I like changing is SelfCheck 3600 is too long time for clamav Virus definitions integrity I prefer to set it to 600, i.e.
SelfCheck 600
By default ClamAV is also configured to scan archive files as well. However for this to work you will have to have previously installed unzip and unrar on system. If still you don't have them installed run:
# apt-get install --yes unrar unzip
...
Note that you will need to have non-free part of Debian deb repositories to /etc/apt/sources.list
Here is one of my sources.list
deb http://ftp.uk.debian.org/debian squeeze main contrib non-free
deb http://security.debian.org/ squeeze/updates main contrib non-free
deb-src http://security.debian.org/ squeeze/updates main contrib non-freedeb http://ftp.debian.skynet.be/ftp/debian/ squeeze main contrib non-free
deb-src http://ftp.debian.skynet.be/ftp/debian/ stable main contrib non-freedeb http://security.debian.org squeeze/updates main contrib non-free
deb-src http://security.debian.org/ squeeze/updates main contrib non-free
3. Scanning with ClamAV
# clamscan -r /tmp/
./dos-58.160.208.43: OK
./dos-108.18.38.140: OK
./dos-188.194.80.100: OK
./dos-91.224.160.135: OK
./dos-128.253.117.70: OK
./dos-128.172.143.110: OK
./dos-77.92.102.34: OK
./dos-195.230.5.12: OK
...
....
----------- SCAN SUMMARY -----------
Known viruses: 2735887
Engine version: 0.97.8
Scanned directories: 1
Scanned files: 129
Infected files: 0
Data scanned: 0.00 MB
Data read: 0.00 MB (ratio 0.00:1)
Time: 4.769 sec (0 m 4 s)
-r flag stands for recursive scan – e.g. scan all sub-directories in directory and its content
To not flood your console / ssh connection one very useful option is -i (print only whetherinfected files are matched). Here is one more sample case:
# clamscan -r -i /var/tmp/
Whether you're on a physical server console and it has pc speaker or sound blaster use –bell option to ring a bell every time a Virus infection is found, for exmpl.
----------- SCAN SUMMARY -----------
Known viruses: 2735887
Engine version: 0.97.8
Scanned directories: 1
Scanned files: 2
Infected files: 0
Data scanned: 0.26 MB
Data read: 0.13 MB (ratio 1.97:1)
Time: 4.824 sec (0 m 4 s)
# clamscan -r -i --bell /var/www/
…
4. Scanning periodically and reporting with ClamAV directories with websites
A very common use of ClamAV is to just setup a scheduled cronjob once a month to scan, whether server folder containing a bunch of websites in separate Virtualhosts contain some viruses or malicious stuff. Then as administrator check those logs once a month to make sure server site or group of sites does not become banned in search engine (blocked by Google Chrome and Firefox as Virus hotbed) …
# crontab -u root -e
00 02 01 * * clamscan -r /var/www -l /var/log/websites-scan.log
Then once a month check out /var/log/websites-scan.log
Tags: avast, cgi support, clamav antivirus, complexity, deb package, debian gnu, debian linux, debian repositories, elf binaries, home desktops, mail server, new mail, Perl, php code, postfix, programmers, proprietary solutions, Qmail, rootkit, squeeze, support server, virus definitions
Posted in Computer Security, Linux, System Administration | No Comments »
Is it possible mail server to work on alternative port to 25?
Thursday, February 28th, 2013If you're running a small home based Linux or BSD server with Qmail, Exim or Postfix and it happens your ISP has filtered incoming connections to TCP/IP port 25 and you wonder if it is possible to use other alternative port to 25 for example the (Secure SMTP) SMTPS 465 supported by all major SMTP servers, the answer unfortunately is it is not possible.
The only accepted and working mail transmission port works on TCP/IP Port 25, thus the only option to make the mail server working fine is contact your ISP and convince them to remove filtering for port 25 to your custom IP. Many ISPs set a Firewall filter for 25, because nowadays many Windows XP / Vista / 7 PCs get infected with Viruses and Trojans running a tiny SMTP server on the host and trying to send million of SPAM messages via the poor unknowing victim. This congests the network and often even creates ISP network overloads, thus ISPs prefer to filter Port 25 to get rid of such eventual problems.
Once again, alternative port to 25 for Mail is impossible !
Tags: eventual problems, exim, incoming connections, Linux, mail server, mail transmission, postfix, Qmail, smtp server, smtp servers, spam messages, trojans, Viruses, windows xp
Posted in Entertainment, Various | No Comments »
Testing Qmail installation for problems: Common reasons for unworking qmail / How to debug Qmail mail server failing to delivery or send emails
Friday, November 9th, 2012
Through my 10 years of experience in managing and "life with qmail", I've at many times had to deal with suddenly broken or misconducting, qmail installs. With some of them the problems started during new Qmail install configuration time, with others QMAIL worked perfectly for years and then suddenly it stopped working. Nomatter what the situation was, there was a kind of "scenario" and common things to check to debug and find out what is causing the respective qmail installation to not work. In this little, article I will try to share my knowledge in hope that others which configure new QMAIL based mail servers or are in situation to need to recover – "resurrect" a one that suddenly stopped working qmail to its normal operations.
Here are few cases , there are many more, probably hundreds of reasons which might be causing Qmail + Vpopmail to stop properly delivering e-amails but as this ones ones are really most likely ones just checking them gives a good clue What is going wrong with Qmail?.:
- Something broke up with scheduled daemontools processes;
- There is no hard disk (the disk is full) and Qmai is unable to writeinside its mail Queue directories (/var/qmail/queue) or Spamassassin or AntiVirus programs fails to write on disk
- qmail-scanner-queue.pl ( /var/qmail/bin/qmail-scanner-queue.pl ) perl script is messed up or if using simscan to do antivirus check-ups instead simscan is failing somewhere
- something messed up with /var/qmail/control/rcpthosts
- something messed up with /var/qmail/control/validrcptto.txt or /var/qmail/control/validrcptto.cdb
- incorrect main server host in /var/qmail/control/me or /var/qmail/control/plusdomain
- Messed up vpopmail (virtual domain) records in /var/qmail/control/virtualdomains file
- problems with insufficient memory (whether there is a softlimit memory limit for /service/qmail-smtpd/run (qmail daemontools start up and monitoring script) – /usr/local/bin/softlimit is no longer proposed used by newer qmail guides but in older ones it was common to appear in /../qmail-smtpd/run
- Something is wrong with clamd (/usr/sbin/clamd – for example crashed due to bug) or something is wrong with clamav database ( /var/lib/clamav or wherever set to be stored; on some installs /usr/local/lib/clamav) – there most commonly main.cvd and daily.cld break up during freshclam clamav database update.
- As freshclam takes care for AntiVirus database updates it is good to check it is properly running, either as a service or via a cronjob
- Assure there are no mistakes or wrong (unexistent) variables in /etc/tcp.smtp file or / and /etc/tcp.smtp.cdb is not broken
- Permission issues with; qmail main binaries in /var/qmail/bin/ , queue files – /var/qmail/queue or qmail log files /var/log/qmail/…
As I said there are plenty of other possible, reasons but I listed this here, since they're the most common reasons for problems with sent or receive of messages with Qmail mail server.
Checking all of the above and making sure they're okay, I've checked daemontools readprodctitle process as it often signalize for problems with any part of qmail install, there all seemed normal no warnings and errors, e.g.:
qmail:~# ps ax|grep -i -E 'clam|freshclam|spam|vpopmail'
2241 ? Ssl 3:49 /usr/sbin/clamd
2408 ? Ss 11:54 /usr/bin/freshclam -d --quiet
2853 ? S 0:00 tcpserver -H -R -v -c100 0 110 qmail-popup mail.www.pc-freak.net /home/vpopmail/bin/vchkpw qmail-pop3d Maildir
2856 ? S 0:01 tcpserver -vR -l /var/qmail/control/me -c 30 -u 89 -g 89 -x /etc/tcp.smtp.cdb 0 25 rblsmtpd -t0 -r zen.spamhaus.org -r dnsbl.njabl.org -r dnsbl.sorbs.net -r bl.spamcop.net qmail-smtpd /var/qmail/control/me /home/vpopmail/bin/vchkpw /bin/true
2857 ? S 0:00 sslserver -e -vR -l mail.www.pc-freak.net -c 30 -u 89 -g 89 -x /etc/tcp.smtp.cdb 0 465 qmail-smtpd mail.www.pc-freak.net /home/vpopmail/bin/vchkpw /bin/true
qmail:~# ps ax|grep -i qmail
2840 ? S 0:00 supervise qmail-send
2844 ? S 0:00 supervise qmail-smtpd
2846 ? S 0:00 supervise qmail-pop3d
2848 ? S 0:00 supervise qmail-smtpdssl
2850 ? S 0:05 qmail-send
2852 ? S 0:00 multilog t n1024 s1048576 n20 /var/log/qmail/qmail-smtpdssl
2853 ? S 0:00 tcpserver -H -R -v -c100 0 110 qmail-popup mail.www.pc-freak.net /home/vpopmail/bin/vchkpw qmail-pop3d Maildir
2854 ? S 0:00 multilog t s100000 n20 /var/log/qmail/qmail-pop3d
2855 ? S 0:01 multilog t n1024 s1048576 n20 /var/log/qmail/qmail-smtpd
2856 ? S 0:01 tcpserver -vR -l /var/qmail/control/me -c 30 -u 89 -g 89 -x /etc/tcp.smtp.cdb 0 25 rblsmtpd -t0 -r zen.spamhaus.org -r dnsbl.njabl.org -r dnsbl.sorbs.net -r bl.spamcop.net qmail-smtpd /var/qmail/control/me /home/vpopmail/bin/vchkpw /bin/true
2857 ? S 0:00 sslserver -e -vR -l mail.www.pc-freak.net -c 30 -u 89 -g 89 -x /etc/tcp.smtp.cdb 0 465 qmail-smtpd mail.www.pc-freak.net /home/vpopmail/bin/vchkpw /bin/true
2858 ? S 0:01 multilog t n1024 s1048576 n20 /var/log/qmail/qmail-send
2868 ? S 0:01 qmail-lspawn ./Maildir
2869 ? S 0:00 qmail-rspawn
2870 ? S 0:00 qmail-clean
2871 ? S 0:04 qmail-todo
2872 ? S 0:01 qmail-clean
27742 pts/6 S+ 0:00 grep -i qmail
qmail:~# ps ax |grep -i readproc|grep -v grep
48060 ? S 0:00 readproctitle service errors: ................................................................................................................................................................................................................................................................................................................................................................................................................
As you see "….." signalize, all is fine with processes scheduled to run over daemontools process. If you instead get warnings or error messages usually the error will point you what is wrong with the qmail install. Common error, I've got over the years here especially on long time functionining qmail installs is insufficient disk space to write in qmail queue and log files.
Also above
ps ax|grep -i -E 'clam|freshclam|spam|vpopmail'
shows all 3 clamd, freshclam and vpopmail are up and running so this most likely means all is good with them. Of course sometimes some of those 3 is working and there are problems with the services properly processing emails so it is always a good idea to read qmail log files, in most qmail installations qmail logs are located in /var/log/qmail .
Quickest way is to check all of the qmail related logs
in a loop with something like:
qmail:~# for i in $(ls -d /var/log/qmail/*qmail*/); do tail -n 10 $i/current|tai64nlocal; sleep 5; done
Also it is always a good idea to check last 10 lines of clamav, freshclam, qmail-scanner and spamd logs:
qmail:~# tail -n 10 /var/log/qmail/clamav/clamav.log;
Fri Nov 9 06:52:28 2012 -> SelfCheck: Database status OK.
Fri Nov 9 07:52:28 2012 -> SelfCheck: Database status OK.
Fri Nov 9 08:52:28 2012 -> SelfCheck: Database status OK.
Fri Nov 9 09:52:28 2012 -> SelfCheck: Database status OK.
Fri Nov 9 10:52:29 2012 -> SelfCheck: Database status OK.
Fri Nov 9 11:57:29 2012 -> SelfCheck: Database status OK.
Fri Nov 9 12:57:29 2012 -> SelfCheck: Database status OK.
Fri Nov 9 14:14:35 2012 -> SelfCheck: Database status OK.
Fri Nov 9 15:33:46 2012 -> SelfCheck: Database status OK.
Fri Nov 9 16:33:46 2012 -> SelfCheck: Database status OK.
qmail:~# tail -n 10 /var/log/qmail/clamav/freshclam.log
Fri Nov 9 16:20:44 2012 -> --------------------------------------
Fri Nov 9 17:20:44 2012 -> Received signal: wake up
Fri Nov 9 17:20:44 2012 -> ClamAV update process started at Fri Nov 9 17:20:44 2012
Fri Nov 9 17:20:44 2012 -> WARNING: Your ClamAV installation is OUTDATED!
Fri Nov 9 17:20:44 2012 -> WARNING: Local version: 0.97.5 Recommended version: 0.97.6
Fri Nov 9 17:20:44 2012 -> DON'T PANIC! Read http://www.clamav.net/support/faq
Fri Nov 9 17:20:44 2012 -> main.cvd is up to date (version: 54, sigs: 1044387, f-level: 60, builder: sven)
Fri Nov 9 17:20:44 2012 -> daily.cld is up to date (version: 15557, sigs: 284869, f-level: 63, builder: jesler)
Fri Nov 9 17:20:44 2012 -> bytecode.cld is up to date (version: 191, sigs: 37, f-level: 63, builder: neo)
Fri Nov 9 17:20:46 2012 ->
--------------------------------------
qmail:~# tail -n 10 /var/log/qmail/qscan/qmail-queue.log
Fri, 09 Nov 2012 13:14:35 EET:14705:
from='noreply@theitjobboard.eu', subj='Network Developer', via SMTP from oy-ip-034.smwebhost.com
Fri, 09 Nov 2012 13:14:44 EET:14705: ------ Process 14705 finished. Total of 8.846395 secs
Fri, 09 Nov 2012 15:04:27 EET:21979: +++ starting debugging for process 21979 (ppid=21969) by uid=89
Fri, 09 Nov 2012 15:04:27 EET:21979: g_e_h: return-path='hipo@www.pc-freak.net', recips='sandy.richardson@hyperionrecruitment.com'
Fri, 09 Nov 2012 15:04:27 EET:21979: from='"G. Georgiev"
Fri, 09 Nov 2012 15:04:34 EET:21979: ------ Process 21979 finished. Total of 6.626484 secs
Fri, 09 Nov 2012 15:33:46 EET:23891: +++ starting debugging for process 23891 (ppid=23884) by uid=89
Fri, 09 Nov 2012 15:33:46 EET:23891: g_e_h: return-path='sdy.richardson@hyperionrecruitment.com', recips='hipo@www.pc-freak.net'
Fri, 09 Nov 2012 15:33:46 EET:23891: from='"Sandy Richardson"
ostrich.dnsmaster.net
qmail:~# tail -n 10 /var/log/spamd/current |tai64nlocal 2012-11-09 16:25:43.091680500 Nov 9 15:04:27.858 [22049] info: spamd: connection from localhost [127.0.0.1] at port 54494
2012-11-09 16:25:43.091683500 Nov 9 15:04:27.948 [22049] info: spamd: checking message <509CFF4F.9030601@www.pc-freak.net> for qscand:89
2012-11-09 16:25:43.091684500 Nov 9 15:04:33.837 [22049] info: spamd: clean message (0.0/5.0) for qscand:89 in 6.0 seconds, 1104 bytes.
2012-11-09 16:25:43.091690500 Nov 9 15:04:33.838 [22049] info: spamd: result: . 0 - scantime=6.0,size=1104,user=qscand,uid=89,required_score=5.0,rhost=localhost,raddr=127.0.0.1,rport=54494,mid=<509CFF4F.9030601@www.pc-freak.net>,autolearn=ham
2012-11-09 16:25:43.091692500 Nov 9 15:04:34.077 [22043] info: prefork: child states: II
2012-11-09 16:25:43.091692500 Nov 9 15:33:53.626 [22049] info: spamd: connection from localhost [127.0.0.1] at port 54681
2012-11-09 16:25:43.091696500 Nov 9 15:33:53.656 [22049] info: spamd: checking message <05e201cdbe7e$d1c83c90$7558b5b0$@hyperionrecruitment.com> for qscand:89
2012-11-09 16:25:43.091697500 Nov 9 15:33:59.467 [22049] info: spamd: clean message (0.0/5.0) for qscand:89 in 5.8 seconds, 33845 bytes.
2012-11-09 16:25:43.091698500 Nov 9 15:33:59.467 [22049] info: spamd: result: . 0 - scantime=5.8,size=33845,user=qscand,uid=89,required_score=5.0,rhost=localhost,raddr=127.0.0.1,rport=54681,mid=<05e201cdbe7e$d1c83c90$7558b5b0$@hyperionrecruitment.com>,autolearn=ham
2012-11-09 16:25:43.091702500 Nov 9 15:33:59.506 [22043] info: prefork: child states: II
Whether observing, some of above logs reveals problems to delivery e-mail messages because e-mail boxes are not existing in /var/qmail/control/validrcptto.cdb – this often happens whether new e-mail boxes are created and the new mail somehow did not enter validrcptto.txt / validrcptto.cdb , you will have to re-build validrcptto.cdb. Rebuilding validrcptto.cdb manually is done with cmd:
br />
qmail:~# /usr/local/bin/mkvalidrcptto > /var/qmail/control/validrcptto.txt qmail:~# cdbmake-12 /var/qmail/control/validrcptto.cdb /var/qmail/control/validrcptto.tmp < /var/qmail/control/validrcptto.txt
Of course, if the qmail was already properly installed with validrcptto support, this should be done automatically with some cron job set to invoke above commands every 5 minutes or so. In Thibs QmailRocks followed install the script is called /usr/sbin/update-validrcptto and is set to exec every 5 mins.
If spamassassin is configured to automatically update its set of anti-spam rules, via some cron job or smth. it is always a good idea to check if spamassassin, properly loads up does not fail due to some antispam rule:
qmail:~# spamassassin --lint -D ...
....
You will have to examine carefully, the long returned content for "warning" and "error" keywords. If you don't won't to bother with details you can do, spamassassin –lint
Another good idea whether problems with qmail is of course to rebuild tcpserver cdb file for smtp – this usually solves problems caused by broken /etc/tcp.smtp.cdb.cdb files.
Re-building manually tcp.smtp.cdb is done with:
qmail:~# tcprules /etc/tcp.smtp.cdb /etc/tcp.smtp.tmp < /etc/tcp.smtp
qmail:~# chmod 644 /etc/tcp.smtp.cdb
However, most qmail installation guides recommend or set a qmailctl bash script file, to start / stop / reload / flush qmail queue or simply get status of the qmail installation, so it much easier to rebuild tcp.smtp.cdb through it:
qmail:~# qmailctl cdb
Reloaded /etc/tcp.smtp.
To check the basic qmail compontents (qmail-send, qmail-smtpd , qmail-smtpdssl)do:
qmail:~# qmailctl stat
/service/qmail-send: up (pid 2850) 1886193 seconds
/service/qmail-send/log: up (pid 2858) 1886193 seconds
/service/qmail-smtpd: up (pid 2856) 1886193 seconds
/service/qmail-smtpd/log: up (pid 2855) 1886193 seconds
/service/qmail-smtpdssl: up (pid 2857) 1886193 seconds
/service/qmail-smtpdssl/log: up (pid 2852) 1886193 seconds
messages in queue: 2
messages in queue but not yet preprocessed: 0
Another good practice if you have doubts that something is messed with qmail-queue is to check what is waiting to be send in queue:
qmail:~# qmail-qstat
messages in queue: 2
messages in queue but not yet preprocessed: 0
In above paste, from my mail server I have just 2 mails, if you however notice here some large numbers like 5000 or 10000, this might be the cause for asetbacks. If you have plenty of undelivered mails waiting in mail server queue, examine the queue:
qmail:~# qmail-qread ....
.....
Of course it is sometimes, possible to be in situation, where more than one components are creating mail server's sent / receive delivery issues. Anyhow doing a close examination of all possible components usually should (if not reveal what causes the issue) at least give you some pointer to where to search for the problem.
Also for qmail installations based on QmailRocks or Thibs QmailRocks guide, there is a tiny shell script provided, that does evaluation on standard qmail files permissions and binary locations and reports, whether it finds problems with some of them. You can fetch a copy of the qmr_inst_check from here . Although the script is created to check a newly install qmail for problems, it also often helps in determining issues with qmails who mysteriously stopped working.
If you suspect, there are::
- permission problems with vpopmail installation ( /home/vpopmail ) – use vpfixpermissions shell script to restore proper permissions
- permission problems with /var/qmail/ and its subdirectories run JMS's qfixpermissions shell script
- On qmail queue, messed up permissions (something I hope you will never end up with), you will have to run JMS QFIXQ bash script.
Messed up queue permissions issue happened to me just few times and it is one of the most terrible ones to get with qmail – I hope and wish you never experience it.
Well that's it. Hope this little walk through give you idea where to check on troublesome Qmail install. Please leave a comment if it help you (somehow) solve your issue. Also will be glad to hear if I'm missing something – i'm sure I am.
Tags: common, installation, Problems, Qmail, reasons, testing
Posted in Qmail, System Administration, Various | 2 Comments »
How to speed up qmail qmail-smtpd response time on QmailRocks Thibs based install
Saturday, October 6th, 2012I have recently installed Qmail following the Updated Debian QmailRocks Thibs Install
The qmail is configured just like Thibs points out the server was configured to a run qmail-smtpd script together with DJB’s Daemontools
I’ve figured out today connecting to the newly install Qmail host with telnet, using:
qmail:~# telnet mail.qmailhost.com 25
Trying 83.228.93.76...
Connected to mail.qmailhost.com.
Escape character is '^]'.
220 This is Mail mail.qmailhost.com ESMTP
Does a few seconds delay until my configured qmail greeting shows up. This is not a a deadly problem, but the delay itself might have a negative influence and make the host look like a spammer host to someone, hence I took few seconds to find a way to reduce this SMTP port connection delay.
The mail server responds on port 25, using qmail-smtpd so it was logical delay is caused somewhere by /service/qmail-smtpd/run (which actually links to /var/qmail/supervise/qmail-smtpd/run).
I did a quick review of /var/qmail/supervise/qmail-smtpd/run and found two lines that possibly create unnecessery delay, cause on each and every Port 25 connection request from repote SMTP server /usr/bin/head and /usr/bin/which are executed.
Here are two lines in /service/qmail-smtpd/run, I refer to:
LOCAL=`head -1 $VQ/control/me
(located on line 34)
and
TRUE=`which true`
located on line 116
The script was smartly written as planned to run on multiple Linux distributions. However since QmailRocks Thibs guide and my particular case needs to run on Debian Linux I think this is totally waste of system CPU time.
Therefore I substituted above two lines with:
LOCAL="/var/qmail/control/me"
TRUE="/bin/true"
I checked in /var/qmail/control/me I have only my primary mail server host defined, cause otherwise this changed could pose random mail server errors:
qmail:~# wc -l /var/qmail/control/me
1 /var/qmail/control/me
qmail:~# cat /var/qmail/control/me
mail.qmailhost.com
An updated version of /service/qmail-smtpd/run script you can download from here
If you don’t want to temper manually edit the script the quickest way is to overwrite old script with changed one, i.e.:
qmail:~# cd /var/qmail/supervise/qmail-smtpd
qmail:/var/qmail/supervise/qmail-smtpd# wget -q https://www.pc-freak.net/files/qmail-smtpd-daemontools-run
qmail:/var/qmail/supervise/qmail-smtpd# mv qmail-smtpd-daemontools-run run
To test connection time delay afterwards, you can use:
# time (echo HELO localhost | telnet mail.qmailhost.com 25)
Trying 83.228.93.76...
Connected to mail.qmailhost.com.
Escape character is '^]'.
Connection closed by foreign host.
real 0m0.070s
user 0m0.004s
sys 0m0.000s
Well still there is a connection delay – it is not so quick as smtp.gmail.com, but now connection response delay is better. For sake of comparison here is same test with Google’s SMTP:
$ time (echo HELO localhost | telnet smtp.gmail.com 25)
Trying 173.194.70.108...
Connected to gmail-smtp-msa.l.google.com.
Escape character is '^]'.
Connection closed by foreign host.
real 0m0.017s
user 0m0.004s
sys 0m0.000s
BTW a bit of time delay sometimes, can have a positive impact against spammers, as it can reduce a bit the amount of spammer mail servers connecting to the host. So i’m not sure if being 4 times slower in connection than Gmail is necessery bad 🙂
Tags: Qmail, QmailRocks, response, SMTPD, speed
Posted in Qmail, System Administration | 1 Comment »




