If you have installed recent version of CentOS, you have noticed by default the Installator did setup Xserver and GNOME as Graphical Environment as well the surrounding GUI Administration tools. That's really not needed on "headless" monitorless Linux servers as this wastes up for nothing a very tiny amount of the machine CPU and RAM and Disk resource on keeping services up and running. Even worse a Graphical Environment on a Production server poses a security breach as their are much more services running on the OS that could be potentially hacked.
Removal of GUI across CentOS is similar but slightly differs. Hence in this article, I'll show how it can be removed on CentOS Linux 7 / 8 and 9. Removal of Graphics is usual operation for sysadmins thus there is plenty of info on the net,how this is done on CentOS 7 and COS 8 but unfortunately as of time of writting this article, couldn't find anything on the net on how to Remove GUI environment on CentOS 9.
The reason for this article is mostly for documentation purposes for myself
First list the available meta-package groups installed on the OS:
1. List machine installed package groups
[root@centos ~]# yum grouplist
Last metadata expiration check: 3:55:48 ago on Mon 11 Apr 2022 03:26:06 AM EDT.
Available Environment Groups:
Server
Minimal Install
Workstation
KDE Plasma Workspaces
Custom Operating System
Virtualization Host
Installed Environment Groups:
Server with GUI
Installed Groups:
Container Management
Headless Management
Available Groups:
Legacy UNIX Compatibility
Console Internet Tools
Development Tools
.NET Development
Graphical Administration Tools
Network Servers
RPM Development Tools
Scientific Support
Security Tools
Smart Card Support
System Tools
Fedora Packager
On CentOS 8 and CentOS 9 to list the installed package groups, you can use also:
[root@centos ~]# dnf grouplist
…
Installed Environment Groups:
Server with GUI
2. Remove GNOME and Xorg GUIs on CentOS 7
[root@centos ~]# yum groupremove "Server with GUI" –skip-broken
[root@centos ~]# yum groupremove "GNOME Desktop" -y
…
3. Remove GNOME and X on CentOS 8
[root@centos ~]# dnf groupremove 'X Window System' 'GNOME' -y
…
4. Remove Graphical Environment on CentOS 9
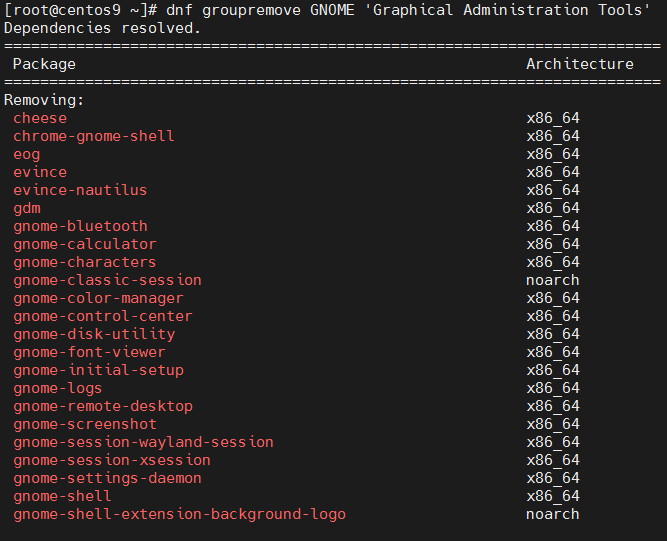
[root@centos ~]# yum groupremove GNOME 'Graphical Administration Tools' -y
Removing Groups:
GNOMETransaction Summary
====================================================
Remove 123 PackagesFreed space: 416 M
Is this ok [y/N]: y
Is this ok [y/N]: y
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
…
xorg-x11-drv-libinput-1.0.1-3.el9.x86_64
xorg-x11-server-Xorg-1.20.11-10.el9.x86_64
xorg-x11-server-Xwayland-21.1.3-2.el9.x86_64
xorg-x11-server-common-1.20.11-10.el9.x86_64
xorg-x11-server-utils-7.7-44.el9.x86_64
xorg-x11-xauth-1:1.1-10.el9.x86_64
xorg-x11-xinit-1.4.0-11.el9.x86_64Complete!
Graphical Administration Tools – is a group of tools that
Or alternatively you can do
[root@centos ~]# yum remove gnome* xorg* -y
5. Change the Graphical boot to text multiuser
[root@centos ~]# systemctl set-default multi-user.target
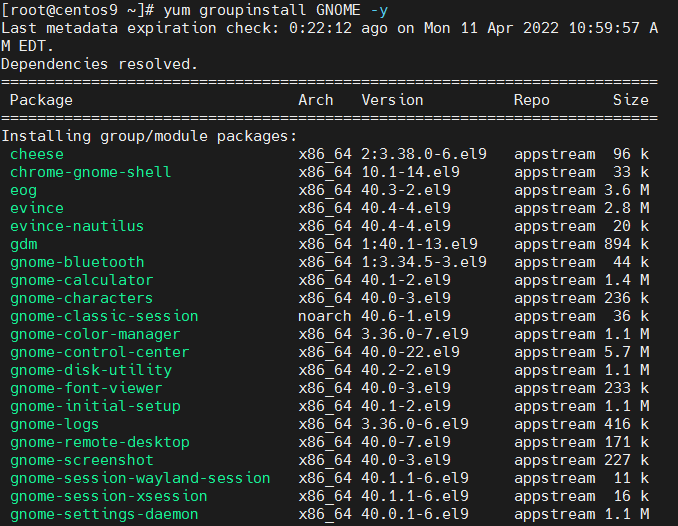
6. Install GNOME / X GUI on the CentOS 7 / 8 / 9
Sometimes GNOME Desktop environment and Xorg are missing on previously delpoyed installs but you need it back for some reason.For example it was earlier removed a year ago on the server as it was not needed, but the machine use type changes and now you need to have installed an Oracle Server / Oracle Client which usually depends on having at least a minimal working version of X environment ont the Linux.
To install back the GNOME and X back on the machine:
[root@centos ~]# yum groupistall "Server with GUI" –skip-broken
[root@centos9 network-scripts]# yum groupinstall "Server with GUI" –skip-broken
Last metadata expiration check: 0:09:26 ago on Mon 11 Apr 2022 07:43:11 AM EDT.
No match for group package "insights-client"
No match for group package "redhat-release"
No match for group package "redhat-release-eula"
Dependencies resolved.
===================================================
Package Arch Version Repository Size
===================================================
Installing group/module packages:
NetworkManager-wifi x86_64 1:1.37.2-1.el9 baseos 75 k
cheese x86_64 2:3.38.0-6.el9 appstream 96 k
chrome-gnome-shell x86_64 10.1-14.el9 appstream 33 k
eog x86_64 40.3-2.el9 appstream 3.6 M
evince x86_64 40.4-4.el9 appstream 2.8 M
evince-nautilus x86_64 40.4-4.el9 appstream 20 k
gdm x86_64 1:40.1-13.el9 appstream 894 k
gnome-bluetooth x86_64 1:3.34.5-3.el9 appstream 44 k
gnome-calculator x86_64 40.1-2.el9 appstream 1.4 M
gnome-characters x86_64 40.0-3.el9 appstream 236 k
gnome-classic-session noarch 40.6-1.el9 appstream 36 k
gnome-color-manager x86_64 3.36.0-7.el9 appstream 1.1 M
gnome-control-center x86_64 40.0-22.el9 appstream 5.7 M
gnome-disk-utility x86_64 40.2-2.el9 appstream 1.1 M
gnome-font-viewer x86_64 40.0-3.el9 appstream 233 k
gnome-initial-setup x86_64 40.1-2.el9 appstream 1.1 M
gnome-logs x86_64 3.36.0-6.el9 appstream 416 k
…
Installing dependencies:
cheese-libs x86_64 2:3.38.0-6.el9 appstream 941 k
clutter x86_64 1.26.4-7.el9 appstream 1.1 M
clutter-gst3 x86_64 3.0.27-7.el9 appstream 85 k
clutter-gtk x86_64 1.8.4-13.el9 appstream 47 k
cogl x86_64 1.22.8-5.el9 appstream 505 k
colord-gtk x86_64 0.2.0-7.el9 appstream 33 k
dbus-daemon x86_64 1:1.12.20-5.el9 appstream 202 k
dbus-tools x86_64 1:1.12.20-5.el9 baseos 52 k
evince-previewer x86_64 40.4-4.el9 appstream 29 kInstalling weak dependencies:
gnome-tour x86_64 40.1-1.el9 appstream 722 k
nm-connection-editor x86_64 1.26.0-1.el9 appstream 838 k
p11-kit-server x86_64 0.24.1-2.el9 appstream 199 k
pinentry-gnome3 x86_64 1.1.1-8.el9 appstream 41 k
Installing Environment Groups:
Server with GUI
Installing Groups:
base-x
Container Management
core
fonts
GNOME
guest-desktop-agents
Hardware Monitoring Utilities
hardware-support
Headless Management
Internet Browser
multimedia
networkmanager-submodules
print-client
Server product core
standardTransaction Summary
=======================================================
Install 114 PackagesTotal download size: 96 M
Installed size: 429 M
Is this ok [y/N]: y
…
or yum groupinstall GNOME
[root@centos9 ~]# yum grouplist
Last metadata expiration check: 3:55:48 ago on Mon 11 Apr 2022 03:26:06 AM EDT.
Available Environment Groups:
…
Installed Environment Groups:
Server with GUI
…
Next you should change the OS default run level to 5 to make CentOS automatically start the Xserver and gdm.
To see the list of available default Login targets do:
[root@centos ~]# find / -name "runlevel*.target"
/usr/lib/systemd/system/runlevel0.target
/usr/lib/systemd/system/runlevel1.target
/usr/lib/systemd/system/runlevel2.target
/usr/lib/systemd/system/runlevel3.target
/usr/lib/systemd/system/runlevel4.target
/usr/lib/systemd/system/runlevel5.target
/usr/lib/systemd/system/runlevel6.target
The meaning of each runlevel is as follows:
| Run Level | Target Units | Description |
|---|---|---|
| 0 | runlevel0.target, poweroff.target | Shut down and power off |
| 1 | runlevel1.target, rescue.target | Set up a rescue shell |
| 2,3,4 | runlevel[234].target, multi- user.target | Set up a nongraphical multi-user shell |
| 5 | runlevel5.target, graphical.target | Set up a graphical multi-user shell |
| 6 | runlevel6.target, reboot.target | Shut down and reboot the system |
If this does not work you can try:

[root@centos ~]# yum -y groups install "GNOME Desktop"
…
7. To check the OS configured boot target
[root@centos ~]# systemctl get-default
multi-user.target
multi-user.target is a mode of operation that is text mode only with multiple logins supported on tty and remotely.
To change it to graphical
[root@centos ~]# systemctl set-default graphical.target
or simply link it yourself
[root@centos ~]# ln -sf /lib/systemd/system/runlevel5.target /etc/systemd/system/default.target
[root@centos ~]# reboot
If the X was not used so far ever, you will get a few graphial screens to accept the License Information and Finish the configuration,i .e.
1. Accept the license by clicking on the “LICENSE INFORMATION“.
2. Tick mark the “I accept the license agreement” and click on “Done“.
3. Click on “FINISH CONFIGURATION” to complete the setup.
And voila GDM (Graphical Login) Greater should shine up.
You could also go the manual route by adding an .xinitrc file in your home directory (instead of making the graphical login screen the default, as done above with the sudo systemctl set-default graphical.target command). To do this, issue the command:
[root@centos ~]# echo "exec gnome-session" >> ~/.xinitrc