Posts Tagged ‘Service’
Friday, August 19th, 2011 I'm tuning a Windows 2003 for better performance and securing it against DoS of service attacks. After applying all the changes I needed to restart the WebServer for the new configurations to take effect.
As I'm not a GUI kind of guy I found it handy there is a fast command to restart the Microsoft Internet Information Server. The command to restart IIS is:
c:> iisreset
Tags: command, DoS, effect, GUI, guy, IIS, iisreset, information, Internet, internet information server, kind, line, Microsoft, microsoft iis, microsoft internet information server, performance, server, Service, webserver, Windows, windows command
Posted in IIS, System Administration, Windows | 1 Comment »
Saturday, December 8th, 2012 Business or not a business entity, in the mostly globalized world it is almost inevitable to go on at least monthly basis without a need for some kind of currency convertion. Of course there are plenty of websites allowing Free Money Convertion services out there. However as I'm not a big fan of the Software as a Service (SAS). I don't like other people to be able to sniff what kind of money, amounts I'm intending to convert as well as I don't like google or other search engine to profile me how frequently I'm converting or intending to convert money. Thus today I did a quick research what kind of Free and Open Source Software FOSS is available to do the money convertion operation custom on my own webserver or my desktop PC. Though It was not exactly what I was looking for I found a Windows Desktop Software -CConverter which is capable of convertions between mostly if not all Currencies around the world. I'm not a m$ Windows user myself, but I was glad to know a Free Software exists for the task. CConverter is definitely a piece of soft useful for Businesses and People. In future if I do my own business it would be nice to know of this little handy soft existence and I will put it in action (to save costs) and add confidentiality to my business money transaction / convertions. Below is the two screenshots of CConverter I found on the project's sourceforge website:


Tags: action, convertions, currency convertion, existence, free software, kind, microsoft windows, Pc, plenty, SAS, Service, task, Though It, Windows
Posted in Business Management, Curious Facts | No Comments »
Tuesday, May 24th, 2011 
I have installed TightVNC to a Windows host just a few weeks ago in order to be able to manage remotely a Windows host and forgot to write down the administrator password 🙂 (stoopid!)
I had to explain to a friend remotely how to change the TightVNC admin password and it was a complete nightmare!
Shortly here is the exact menus one who wants to reset the password of a TigthVNC server after forgotten:
Start -> All Programs -> TightVNC
-> TightVNC Server (Service Mode) ->
TightVNC Service - Offline Configuration.
In the configuration dialog to popup there are the Server and Administration tabs through which a new password can be set.
After the password is change either a restart of the TightVNC server is necessery or a restart of the Windows PC.
Tags: admin, Administration, administrator, administrator password, change, dialog, friend, host, How to, menus, Mode, necessery, nightmare, Offline, order, password, popup, Programs, reset, server, server service, Service, service mode, service offline, Start, stoopid, tabs, TightVNC, TigthVNC, Windows, windows pc
Posted in System Administration, Various, VNC, Windows | 25 Comments »
Thursday, June 23rd, 2011 
Holy Mount Athos st. Georgi the Glory Bringer – Zographus Monastic main Church
I start this post with the St. George Zographus Monastery’s main Church as the Zographus Monastery on Holy Mount Athos was our brother Georgi last eartly place he wanted to spend the remaining of his eartly life.
Today it’s the 40th day since our brother in Christ (ipodeacon) Georgi Nedev has presented his humble soul to our Saviour Jesus.

This is the only picture I have of our brother Georgi
His living was as humble as his departure from this life and his passing I believe in the eternal life with God.
Georgi had the severe desire to become a monk in Holy Mount Athos and has multiple friends in there which loved him and often prayed for him.
Now on this 40 day in our Bulgarian monastery in Holy Mount Athos, Saint George – The GloryBringer (Zographus) monks will be serving a requiem service (Panihida – as we say in Slavonic)
His departure was striking and sudden for of us in the Church community here in Dobrich’s Holy Trinity Church, as well as not less shocking for the Holy Mount Athos Zographus monks Christian community who loved our brother sincerely.
Some short biographic facts about our brother ipodeacon Georgi Nedev are here
Unfortunately the bio-facts I know about Georgi are very little, as I only knew him for a couple of years. Even though the short time I used to know him, I can say I was blessed through him and I’m exteremely grateful to him, it was through him I’ve learned a bit more about Holy Mount Athos and our Bulgarian monk community that is in Zographus, as well as some very minor details concerning the spiritual Church life that I’ve never thought about.
It was thanks to him I was being encouraged on numerous times in terrible times of desparation and loss of faith and track in life.
Thanks to him I was being explained for a first time, how one can go for a pilgrimage journey to Holy Mount Athos and how one can get the pilgrim’s permit documentation related to going there called in greek diamontirium
He also told me about numerous miracles about Holy Mount Athos, and explained me one needs to pray to the Holy Theotokos Virgin Mary and ask her that is being allowed to enter this holy place.
This last lent, even though his sickness Georgi was regularly visiting the evening services in the Church and was dilegent in his spiritual life.
I remember him expressing his enormous joy the last time I saw him on a Holy Liturgy for he took the Holy Communion.
After the Church service, I asked him how is he, his answer was; I’m not feeling well, but praise be to God! for I was able to take the Holy Communion
Many times when I asked him what are his future plans, he used to answer I don’t know anything, it’s all in the God’s will (hands) for me.
You can see yourself how great his dedicated for God was by his own words.
As our priest, who used to be his confessor said, “Georgi was a righteous man and God took him early on”.
Let eternal be your Memory beloved brother Georgi now and Forver and Ever! Amen!
Tags: answer, beloved brother, bishop, bit, brother in christ, Bulgarian, Communion, CommunionMany, desparation, diamontirium, dilegent, eternal life, Forver, George Zographus Monastery, georgi, Holy, Holy Mount Athos Zographus, holy theotokos, holy trinity church, humble soul, ipodeacon, journey, last, life thanks, life today, memory, minor details, Monastery, monk, Monks, mount athos, permit, picture, pilgrim, pilgrimage journey, place, pray, priest, requiem, requiem service, saviour jesus, Service, soul, spiritual, spiritual church, spiritual life, st george, terrible times, time, today, Trinity, trinity church, virgin mary, Vladishka, Zographus
Posted in Christianity, Everyday Life | 1 Comment »
Friday, July 8th, 2011 
Some long time ago I’ve written an article Optimizing Linux tcp/ip networking
In the article I’ve examined a number of Linux kernel sysctl variables, which significantly improve the way TCP/IP networking is handled by a non router Linux based servers.
As the time progresses I’ve been continuing to read materials on blogs and internet sites on various tips and anti Denial of Service rules which one could apply on newly installed hosting (Apache/MySql/Qmail/Proxy) server to improve webserver responce times and tighten the overall security level.
In my quest for sysctl 😉 I found a few more handy sysctl variables apart from the old ones I incorporate on every Linux server I adminstrate.
The sysctl variables improves the overall network handling efficiency and protects about common SYN/ACK Denial of service attacks.
Here are the extra sysctl variables I started incorporating just recently:
############ IPv4 Sysctl Settings ################
#Enable ExecShield protection (randomize virtual assigned space to protect against many exploits)
kernel.randomize_va_space = 1
#Increase the number of PIDs processes could assign this is very needed especially on more powerful servers
kernel.pid_max = 65536
# Prevent against the common 'syn flood attack'
net.ipv4.tcp_syncookies = 1
# Controls the use of TCP syncookies two is generally a better idea, though you might experiment
#net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
##################################################
#
############## IPv6 Sysctl Settings ################
# Number of Router Solicitations to send until assuming no routers are present.
net.ipv6.conf.default.router_solicitations = 0
# Accept Router Preference in RA? Again not necessery if the server is not a router
net.ipv6.conf.default.accept_ra_rtr_pref = 0
# Learn Prefix Information in Router Advertisement (Unnecessery) for non-routers
net.ipv6.conf.default.accept_ra_pinfo = 0
# disable accept of hop limit settings from other routers (could be used for DoS)
net.ipv6.conf.default.accept_ra_defrtr = 0
# disable ipv6 global unicasts server assignments
net.ipv6.conf.default.autoconf = 0
# neighbor solicitations to send out per address (better if disabled)
net.ipv6.conf.default.dad_transmits = 0
# disable assigning more than 1 address per network interface
net.ipv6.conf.default.max_addresses = 1
#####################################################
To use this settings paste the above sysctl variables in /etc/sysctl.conf and ask sysctl command to read and apply the newly added conf settings:
server:~# sysctl -p
...
Hopefully you should not get errors while applying the sysctl settings, if you get some errors, it’s possible some of the variable is differently named (depending on the Linux kernel version) or the Linux distribution on which sysctl’s are implemented.
For some convenience I’ve created unified sysctl variables /etc/sysct.conf containing the newly variables I started implementing to servers with the ones I already exlpained in my previous post Optimizing Linux TCP/IP Networking
Here is the optimized / hardened sysctl.conf file for download
I use this exact sysctl.conf these days on both Linux hosting / VPS / Mail servers etc. as well as on my personal notebook 😉
Here is also the the complete content of above’s sysctl.conf file, just in case if somebody wants to directly copy/paste it in his /etc/sysctl.conf
# Sysctl kernel variables to improve network performance and protect against common Denial of Service attacks
# It's possible that not all of the variables are working on all Linux distributions, test to make sure
# Some of the variables might need a slight modification to match server hardware, however in most cases it should be fine
# variables list compiled by hip0
### https://www.pc-freak.net
#### date 08.07.2011
############ IPv4 Sysctl Kernel Settings ################
net.ipv4.ip_forward = 0
# ( Turn off IP Forwarding )
net.ipv4.conf.default.rp_filter = 1
# ( Control Source route verification )
net.ipv4.conf.default.accept_redirects = 0
# ( Disable ICMP redirects )
net.ipv4.conf.all.accept_redirects = 0
# ( same as above )
net.ipv4.conf.default.accept_source_route = 0
# ( Disable IP source routing )
net.ipv4.conf.all.accept_source_route = 0
# ( - || - )net.ipv4.tcp_fin_timeout = 40
# ( Decrease FIN timeout ) - Useful on busy/high load server
net.ipv4.tcp_keepalive_time = 4000
# ( keepalive tcp timeout )
net.core.rmem_default = 786426
# Receive memory stack size ( a good idea to increase it if your server receives big files )
##net.ipv4.tcp_rmem = "4096 87380 4194304"
net.core.wmem_default = 8388608
#( Reserved Memory per connection )
net.core.wmem_max = 8388608
net.core.optmem_max = 40960
# ( maximum amount of option memory buffers )
# tcp reordering, increase max buckets, increase the amount of backlost
net.ipv4.tcp_max_tw_buckets = 360000
net.ipv4.tcp_reordering = 5
##net.core.hot_list_length = 256
net.core.netdev_max_backlog = 1024
#Enable ExecShield protection (randomize virtual assigned space to protect against many exploits)
kernel.randomize_va_space = 1
#Increase the number of PIDs processes could assign this is very needed especially on more powerful servers
kernel.pid_max = 65536
# Prevent against the common 'syn flood attack'net.ipv4.tcp_syncookies = 1
# Controls the use of TCP syncookies two is generally a better idea, though you might experiment
#net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
###################################################
############## IPv6 Sysctl Settings ################
# Number of Router Solicitations to send until assuming no routers are present.
net.ipv6.conf.default.router_solicitations = 0
# Accept Router Preference in RA? Again not necessery if the server is not a router
net.ipv6.conf.default.accept_ra_rtr_pref = 0
# Learn Prefix Information in Router Advertisement (Unnecessery) for non-routersnet.
ipv6.conf.default.accept_ra_pinfo = 0
# disable accept of hop limit settings from other routers (could be used for DoS)
net.ipv6.conf.default.accept_ra_defrtr = 0
# disable ipv6 global unicasts server assignmentsnet.
ipv6.conf.default.autoconf = 0
# neighbor solicitations to send out per address (better if disabled)
net.ipv6.conf.default.dad_transmits = 0
# disable assigning more than 1 address per network interfacenet.
ipv6.conf.default.max_addresses = 1
#####################################################
# Reboot if kernel panic
kernel.panic = 20
These sysctl settings will tweaken the Linux kernel default network settings performance and you will notice the improvements in website responsiveness immediately in some cases implementing this kernel level goodies will make the server perform better and the system load might decrease even 😉
This optimizations on a kernel level are not only handy for servers, their implementation on Linux Desktop should also have a positive influence on the way the network behaves and could improve significantly the responce times of opening pages in Firefox/Opera/Epiphany Torrent downloads etc.
Hope this kernel tweakenings are helpful to someone.
Cheers 😉
Tags: adminstrate, amount, anti, apache mysql, autoconf, default, default network, default router, Denial, denial of service, denial of service attacks, exploits, file, harden, How to, imprpove, internet sites, ip networking, ipv, ipv4, ipv6, kernel, kernel level, level, Linux, Linux Security, linux server, memory, network efficiency, non, number, protection, proxy server, Qmail, quot, ra, randomize, reordering, responce, responce times, router linux, routers, rtr, security, security level, serverskernel, Service, solicitations, Source, SYN, syn flood attack, sysctl, time, variables, wmem
Posted in Computer Security, Linux, Linux and FreeBSD Desktop, System Administration | 4 Comments »
Wednesday, September 7th, 2011 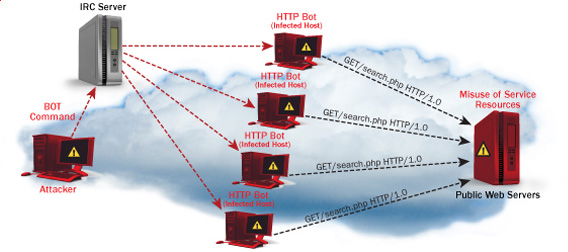
One good module that helps in mitigating, very basic Denial of Service attacks against Apache 1.3.x 2.0.x and 2.2.x webserver is mod_evasive
I’ve noticed however many Apache administrators out there does forget to install it on new Apache installations or even some of them haven’t heard about of it.
Therefore I wrote this small article to create some more awareness of the existence of the anti DoS module and hopefully thorugh it help some of my readers to strengthen their server security.
Here is a description on what exactly mod-evasive module does:
debian:~# apt-cache show libapache2-mod-evasive | grep -i description -A 7
Description: evasive module to minimize HTTP DoS or brute force attacks
mod_evasive is an evasive maneuvers module for Apache to provide some
protection in the event of an HTTP DoS or DDoS attack or brute force attack.
.
It is also designed to be a detection tool, and can be easily configured to
talk to ipchains, firewalls, routers, and etcetera.
.
This module only works on Apache 2.x servers
How does mod-evasive anti DoS module works?
Detection is performed by creating an internal dynamic hash table of IP Addresses and URIs, and denying any single IP address which matches the criterias:
- Requesting the same page more than number of times per second
- Making more than N (number) of concurrent requests on the same child per second
- Making requests to Apache during the IP is temporarily blacklisted (in a blocking list – IP blacklist is removed after a time period))
These anti DDoS and DoS attack protection decreases the possibility that Apache gets DoSed by ana amateur DoS attack, however it still opens doors for attacks who has a large bot-nets of zoombie hosts (let’s say 10000) which will simultaneously request a page from the Apache server. The result in a scenario with a infected botnet running a DoS tool in most of the cases will be a quick exhaustion of system resources available (bandwidth, server memory and processor consumption).
Thus mod-evasive just grants a DoS and DDoS security only on a basic, level where someone tries to DoS a webserver with only possessing access to few hosts.
mod-evasive however in many cases mesaure to protect against DoS and does a great job if combined with Apache mod-security module discussed in one of my previous blog posts – Tightening PHP Security on Debian with Apache 2.2 with ModSecurity2
1. Install mod-evasive
Installing mod-evasive on Debian Lenny, Squeeze and even Wheezy is done in identical way straight using apt-get:
deiban:~# apt-get install libapache2-mod-evasive
...
2. Enable mod-evasive in Apache
debian:~# ln -sf /etc/apache2/mods-available/mod-evasive.load /etc/apache2/mods-enabled/mod-evasive.load
3. Configure the way mod-evasive deals with potential DoS attacks
Open /etc/apache2/apache2.conf, go down to the end of the file and paste inside, below three mod-evasive configuration directives:
<IfModule mod_evasive20.c>
DOSHashTableSize 3097DOS
PageCount 30
DOSSiteCount 40
DOSPageInterval 2
DOSSiteInterval 1
DOSBlockingPeriod 120
#DOSEmailNotify hipo@mymailserver.com
</IfModule>
In case of the above configuration criterias are matched, mod-evasive instructs Apache to return a 403 (Forbidden by default) error page which will conserve bandwidth and system resources in case of DoS attack attempt, especially if the DoS attack targets multiple requests to let’s say a large downloadable file or a PHP,Perl,Python script which does a lot of computation and thus consumes large portion of server CPU time.
The meaning of the above three mod-evasive config vars are as follows:
DOSHashTableSize 3097 – Increasing the DoSHashTableSize will increase performance of mod-evasive but will consume more server memory, on a busy webserver this value however should be increased
DOSPageCount 30 – Add IP in evasive temporary blacklist if a request for any IP that hits the same page 30 consequential times.
DOSSiteCount 40 – Add IP to be be blacklisted if 40 requests are made to a one and the same URL location in 1 second time
DOSBlockingPeriod 120 – Instructs the time in seconds for which an IP will get blacklisted (e.g. will get returned the 403 foribden page), this settings instructs mod-evasive to block every intruder which matches DOSPageCount 30 or DOSSiteCount 40 for 2 minutes time.
DOSPageInterval 2 – Interval of 2 seconds for which DOSPageCount can be reached.
DOSSiteInterval 1 – Interval of 1 second in which if DOSSiteCount of 40 is matched the matched IP will be blacklisted for configured period of time.
mod-evasive also supports IP whitelisting with its option DOSWhitelist , handy in cases if for example, you should allow access to a single webpage from office env consisting of hundred computers behind a NAT.
Another handy configuration option is the module capability to notify, if a DoS is originating from a number of IP addresses using the option DOSEmailNotify
Using the DOSSystemCommand in relation with iptables, could be configured to filter out any IP addresses which are found to be matching the configured mod-evasive rules.
The module also supports custom logging, if you want to keep track on IPs which are found to be trying a DoS attack against the server place in above shown configuration DOSLogDir “/var/log/apache2/evasive” and create the /var/log/apache2/evasive directory, with:
debian:~# mkdir /var/log/apache2/evasive
I decided not to log mod-evasive DoS IP matches as this will just add some extra load on the server, however in debugging some mistakenly blacklisted IPs logging is sure a must.
4. Restart Apache to load up mod-evasive
debian:~# /etc/init.d/apache2 restart
...
Finally a very good reading which sheds more light on how exactly mod-evasive works and some extra module configuration options are located in the documentation bundled with the deb package to read it, issue:
debian:~# zless /usr/share/doc/libapache2-mod-evasive/README.gz
Tags: ana amateur, anti, apache 2, apache server, apache2, awareness, bandwidth server, botnet, brute force attack, concurrent requests, configured, criterias, DDoS, debian linux, Denial, denial of service, denial of service attacks, description, dos attack, dos tool, DOSHashTableSize, evasive maneuvers, event, exhaustion, existence, file, grep, hash, hash table, HTTP, IfModule, Installing, libapache, mod, number, option, page, period of time, protection, Secure Apache, server security, Service, show, small article, system resources, time, tool, uris, webpage
Posted in Computer Security, Linux, System Administration, Web and CMS | 1 Comment »
Friday, July 22nd, 2011 There are few commands I usually use to track if my server is possibly under a Denial of Service attack or under Distributed Denial of Service
Sys Admins who still have not experienced the terrible times of being under a DoS attack are happy people for sure …
1. How to Detect a TCP/IP Denial of Service Attack This are the commands I use to find out if a loaded Linux server is under a heavy DoS attack, one of the most essential one is of course netstat.
To check if a server is under a DoS attack with netstat, it’s common to use:
linux:~# netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n|wc -l
If the output of below command returns a result like 2000 or 3000 connections!, then obviously it’s very likely the server is under a DoS attack.
To check all the IPS currently connected to the Apache Webserver and get a very brief statistics on the number of times each of the IPs connected to my server, I use the cmd:
linux:~# netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
221 80.143.207.107 233 145.53.103.70 540 82.176.164.36
As you could see from the above command output the IP 80.143.207.107 is either connected 221 times to the server or is in state of connecting or disconnecting to the node.
Another possible way to check, if a Linux or BSD server is under a Distributed DoS is with the list open files command lsof
Here is how lsof can be used to list the approximate number of ESTABLISHED connections to port 80.
linux:~# lsof -i TCP:80
litespeed 241931 nobody 17u IPv4 18372655 TCP server.www.pc-freak.net:http (LISTEN)
litespeed 241931 nobody 25u IPv4 18372659 TCP 85.17.159.89:http (LISTEN)
litespeed 241931 nobody 30u IPv4 29149647 TCP server.www.pc-freak.net:http->83.101.6.41:54565 (ESTABLISHED)
litespeed 241931 nobody 33u IPv4 18372647 TCP 85.17.159.93:http (LISTEN)
litespeed 241931 nobody 34u IPv4 29137514 TCP server.www.pc-freak.net:http->83.101.6.41:50885 (ESTABLISHED)
litespeed 241931 nobody 35u IPv4 29137831 TCP server.www.pc-freak.net:http->83.101.6.41:52312 (ESTABLISHED)
litespeed 241931 nobody 37w IPv4 29132085 TCP server.www.pc-freak.net:http->83.101.6.41:50000 (ESTABLISHED)
Another way to get an approximate number of established connections to let’s say Apache or LiteSpeed webserver with lsof can be achieved like so:
linux:~# lsof -i TCP:80 |wc -l
2100
I find it handy to keep track of above lsof command output every few secs with gnu watch , like so:
linux:~# watch "lsof -i TCP:80"
2. How to Detect if a Linux server is under an ICMP SMURF attack
ICMP attack is still heavily used, even though it’s already old fashioned and there are plenty of other Denial of Service attack types, one of the quickest way to find out if a server is under an ICMP attack is through the command:
server:~# while :; do netstat -s| grep -i icmp | egrep 'received|sent' ; sleep 1; done
120026 ICMP messages received
1769507 ICMP messages sent
120026 ICMP messages received
1769507 ICMP messages sent
As you can see the above one liner in a loop would check for sent and recieved ICMP packets every few seconds, if there are big difference between in the output returned every few secs by above command, then obviously the server is under an ICMP attack and needs to hardened.
3. How to detect a SYN flood with netstat
linux:~# netstat -nap | grep SYN | wc -l
1032
1032 SYNs per second is quite a high number and except if the server is not serving let’s say 5000 user requests per second, therefore as the above output reveals it’s very likely the server is under attack, if however I get results like 100/200 SYNs, then obviously there is no SYN flood targetting the machine 😉
Another two netstat command application, which helps determining if a server is under a Denial of Service attacks are:
server:~# netstat -tuna |wc -l
10012
and
server:~# netstat -tun |wc -l
9606
Of course there also some other ways to check the count the IPs who sent SYN to the webserver, for example:
server:~# netstat -n | grep :80 | grep SYN |wc -l
In many cases of course the top or htop can be useful to find, if many processes of a certain type are hanging around.
4. Checking if UDP Denial of Service is targetting the server
server:~# netstat -nap | grep 'udp' | awk '{print $5}' | cut -d: -f1 | sort |uniq -c |sort -n
The above command will list information concerning possible UDP DoS.
The command can easily be accustomed also to check for both possible TCP and UDP denial of service, like so:
server:~# netstat -nap | grep 'tcp|udp' | awk '{print $5}' | cut -d: -f1 | sort |uniq -c |sort -n
104 109.161.198.86
115 112.197.147.216
129 212.10.160.148
227 201.13.27.137
3148 91.121.85.220
If after getting an IP that has too many connections to the server and is almost certainly a DoS host you would like to filter this IP.
You can use the /sbin/route command to filter it out, using route will probably be a better choice instead of iptables, as iptables would load up the CPU more than simply cutting the route to the server.
Here is how I remove hosts to not be able to route packets to my server:
route add 110.92.0.55 reject
The above command would null route the access of IP 110.92.0.55 to my server.
Later on to look up for a null routed IP to my host, I use:
route -n |grep -i 110.92.0.55
Well hopefully this should be enough to give a brief overview on how, one can dig in his server and find if he is under a Distributed Denial of Service, hope it’s helpful to somebody out there.
Cheers 😉
Tags: apache webserver, approximate number, awk print, BSD, checking, cmd, command, course, Denial, denial of service, denial of service attack, Detect, difference, dos attack, ESTABLISHED, freak, How to, HTTP, ICMP, ips, Linux, linux server, linux webserver, LISTEN, litespeed, netstat, nobody, node, ntu, number, server pc, Service, sleep, statistics, SYN, SYNs, sys admins, tcp, terrible times, Watch
Posted in Linux, System Administration | 5 Comments »
Monday, November 12th, 2012 
On my home router configured qmail install, I have recently noticed I receive e-mails only sent via contact forms on the few websites hosted there. I'm subscribed to Debian newsletter, as well as usually receive about 10 emails and few spam mails every day, so after a few days of reduced emails on my email (receiving only e-mail notification about blog issued comments), I logically suspected something is not properly working with the qmail installation.
My first logical guesses was the usual Qmail problems I've previously experienced through the years, earlier I blogged about most common problems / causes and solutions with qmail mail here
First thing I did as usual is to send a test e-mail from Gmail to my Mailboxes on the mail server, the test mail was not received and in Gmail a failure to delivery notice was returned, I paste the TXT content of it as taken from Gmail's webmail -> Show Original menu:
Delivered-To: hipodilski@gmail.com
Received: by 10.112.27.135 with SMTP id t7csp91961lbg;
Mon, 29 Oct 2012 11:08:28 -0700 (PDT)
Received-SPF: pass (google.com: domain of designates 10.60.171.72 as permitted sender) client-ip=10.60.171.72
Authentication-Results: mr.google.com; spf=pass (google.com: domain of designates 10.60.171.72 as permitted sender) smtp.mail=; dkim=pass header.i=
Received: from mr.google.com ([10.60.171.72])
by 10.60.171.72 with SMTP id as8mr17839903oec.140.1351534106946 (num_hops = 1);
Mon, 29 Oct 2012 11:08:26 -0700 (PDT)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=20120113;
h=mime-version:from:to:x-failed-recipients:subject:message-id:date
:content-type:content-transfer-encoding;
bh=GOkrGPurYWG9obiJDBWq6v3JHXdHlUebhVco7rIE73E=;
b=mQemNDUu1Wl7d/VoIseXgXFbL0SdwMIY4MZH9GOm8TuRSVaU8oz80wdWt93zJTt/DR
TEYTT6VRxUaDRAE2igBRLqjiSXdpZAJuBhoNA+bOTPwU53v+eaAUaV/7uHVHG0SYvF6u
rkpc1Rbf41VYIDLthm+e7X8vFdaxqiYFiiHcih2stsAzgI9jAQy62SLlBytYRZeDc3po
BXsb4SLm3+4kF4PuBlmhnCL+ba0hR3vQE5yC8/et0lPaxdSaJk0bHFkrjtmvg00fkyXo
Pv+0dPJHvAInzHlPGtL+XHuvjZCq5XD5ZJjsajyAlG6J64z9dmziz8YM+qqA0KpNaF8+
CVrA==
Received: by 10.60.171.72 with SMTP id as8mr17839903oec.140.1351534106944;
Mon, 29 Oct 2012 11:08:26 -0700 (PDT)
MIME-Version: 1.0
Return-Path: <>
Received: by 10.60.171.72 with SMTP id as8mr20755231oec.140; Mon, 29 Oct 2012
11:08:26 -0700 (PDT)
From: Mail Delivery Subsystem <mailer-daemon@googlemail.com>
To: hipodilski@gmail.com
X-Failed-Recipients: hipo@www.pc-freak.net
Subject: Delivery Status Notification (Failure)
Message-ID: <bcaec54edff658a23d04cd368e01@google.com>
Date: Mon, 29 Oct 2012 18:08:26 +0000
Content-Type: text/plain; charset=ISO-8859-1
Content-Transfer-Encoding: quoted-printable
Delivery to the following recipient failed permanently:
hipo@www.pc-freak.net
Technical details of permanent failure:=20
Google tried to deliver your message, but it was rejected by the recipient =
domain. We recommend contacting the other email provider for further inform=
ation about the cause of this error. The error that the other server return=
ed was: 451 451 qq temporary problem (#4.3.0) (state 17).
----- Original message -----
DKIM-Signature: v=3D1; a=3Drsa-sha256; c=3Drelaxed/relaxed;
d=3Dgmail.com; s=3D20120113;
h=3Dmime-version:date:message-id:subject:from:to:content-type;
bh=3DoaO9B2OZ1YJ19nwzUGkqXFVmVnakcfMdp7uW1TTA/u4=3D;
b=3DQGaaKOgrnXxSa7X0ZjdmbG2/CWDPK10czq4n0YxHLRfX8N+pzJLHWXBFWmVWUNt=
yte
rs8VrYu0BkdAE18MXS3x61cklvi/gk/eCUTzTm+L8fRu/Iiy6pZCr8S3Y6BWBN+5F1=
dm
1LkL0mTpSHqVIoMB/fZwHIzz6q5tTqYSSNHX+hapu30eI5liyK5rbf2/4T9BhJ1VM0=
v+
6NwupzAJK12jniKD8q9b4qJEhEoEqKKZrLKbTYiflHkAVMsg/C3v5zzwH+KZqsHP4W=
Us
Tl/sHUcErXWOry1OrQXLNYR2K9vgqVdBUS5aoU2Jy1FgxbL/t5+XzB3tUK2mv43ttX=
0k
wWbw=3D=3D
MIME-Version: 1.0
Received: by 10.60.171.72 with SMTP id as8mr10945566oec.140.1351262651282;
Fri, 26 Oct 2012 07:44:11 -0700 (PDT)
Received: by 10.182.41.232 with HTTP; Fri, 26 Oct 2012 07:44:11 -0700 (PDT)
Date: Fri, 26 Oct 2012 16:44:11 +0200
Message-ID: <CAPk3ZemH=3D6U0oCihDqDwb9DT8EbE8mTjZou6zzw2LUHHO4ObbA@mail.gma=
il.com>
Subject:=20
From: Georgi Georgiev <hipodilski@gmail.com>
To: hipo@www.pc-freak.net
Content-Type: multipart/alternative; boundary=3Dbcaec54edff653f66804ccf75ab=
9
http://www.nybooks.com/blogs/nyrblog/2012/sep/04/jesus-vs-mao-interview-yua=
n-zhiming/
--=20
Georgi Georgiev
Mobile: +31644943358
After evaluating on qmail logs and various qmail components and basic qmail configurations, noticed the spamassassin spamd process is not running on the host. I've figured it out from qscanner-scanner.pl in /var/log/qscan/qmail-queue.log, there were records saying, qmail-scanner can't pass incoming scanned mail to spand and thus failing
I onwards check in proclist to make sure qmail-queue.log suggestion is right, i.e.:
qmail:~# ps axu|grep -i spamd|grep -v grep
qmail:~#
As you see from my paste qmail scanner logs were right,spamd process died due to some memory leak bug or whatever. To temporary solve the problem I first launched spamd, via its init script:
qmail:~# /etc/init.d/spamassassn start
....
However it was clear, that in future spamd might unexpectedly terminate and this might ruin whole email receive processing again.
I've encountered on few qmail servers issues like this, so I knew of 3 work-arounds.
- One is to use a tiny script set to run via cron job with superuser which checks every few minutes if spamd is running and if not re-launch it via the init script.
In some qmail installations, I've solved issues by using a tiny shell script – here you can download the script restart_spamd_if_crashed.sh
To use it download it to any directory lets say in /usr/local/bin and set cron job like:
qmail:~# crontab -u root -e
*/5 * * * * /usr/local/bin/restart_spamd_if_crashed.sh >/dev/null 2>&1
- Third and in my view best spamd crashes work-around is to configure spamd to be constantly monitored and respawned whether found missing via daemontools.
To do so download those spamd_daemontools_supervise_script.tar.gz archive and place it in /var/qmail/supervise (or wherever qmail/supervise dir is located) and create directory for spamd daemontools monitoring logs
qmail:~# cd /var/supervise
qmail:/var/supservice:# wget -q https://www.pc-freak.net/files/spamd_daemontools_supervise_script.tar.gz
qmail:/var/supervise:# tar -zxvvf spamd_daemontools_supervise_script.tar.gz
....
qmail:/var/supervise:# chmod +t spamd/
qmail:/var/supervise:# mkdir /var/log/spamd
qmail:/var/supervise:# chown -R qmaill:root /var/log/spamd
qmail:/var/supervise:# touch /var/log/spamd/current qmail:/var/supervise:# chown qmaill:nofiles /var/log/spamd/current
It is also generally good idea to check the content of scripts spamd/run and spamd/log/run, a common problem with those scripts is spamassassin might be custom installed in /usr/local/bin/spamd and not in the usual /usr/bin/spamd – spamd location is defined in spamd/run; as well as location of daemontools logging tool multilog might be not /usr/bin/multilog but in /usr/local/bin/multilog – depending on what kind of Qmail guide was used on qmail install time.
Finally, to make daemontools schedule for monitoring spamd service link it in /service dir:
qmail:~# ln -sf /var/supervise/qmail/ /service/qmail
qmail:~# ls -al /service/spamd lrwxrwxrwx 1 root root 27 Nov 8 14:38 spamd -> /var/qmail/supervise/spamd//
To check whether daemontools, started and watch over spamd check what is in /var/log/spamd/current and check the status of daemontools:
qmail:~# tail -n 5
qmail:~# ps ax|grep -i readproc|grep -v grep 27916 ? S 0:00 readproctitle service errors: .............................
qmail:~# tail -n 5 /var/log/spamd/current |tai64nlocal 2012-11-12
Whether, you're sure daemontools, now handles spamd, startup it is also recommended, you stop the on boot time /etc/init.d/spamassassin start-up.
qmail:~# mv /etc/rc2.d/S18spamassassin /etc/rc2.d/K81spamassassin
Of course if spamd is crashing due to some newly included anti-spam rule, which prevents spamassassin from starting, suggested fixes and even daemontools will be unable to "respawn" spamd. In most cases however, implementing any of above "fixes" will assure you a peaceful sleep.
Tags: crashing, preventing, Service, Solve, spamassassin, spamd
Posted in Qmail, System Administration, Various | 3 Comments »
Tuesday, July 3rd, 2012 
I'm currently once again on a pilgrimage in Pomorie Monastery St. George (Bulgaria) – EU as you should read in my previous day post. The brotherhood here is very hospital, since our coming (with Kliment), we were treated like being a part of the monks community. We're given food and allowed to eat together with the monks on one table and even we can enter into some of the interesting discussions after food :).
The life in a monastery is actually quite fascinating, though on the outside it seems boring.
As a general rule monks eat a meal twice a day. On Monday, Wednesday and Friday, the meals are cooked and served usually without oil (except if the Abbot didn't bless differently). The abbot in the Monastery is like a King. The order in the whole monastery resides very much a Kingdom, where the abbot is king some of the monks are his (left and right hand and counselors) etc.
Just like in kingdoms, there are workers who help the kingdom to flourish. With the case with the monastery workers are (mostly believing people) hired (with a wage) to help with the monastery works.
The kitchen "district" has a (chef) cook lady, person/s (usually believing Christians) who help with cooking cutting and vegetables and various meal preparations etc. and serving the brotherhood and workers dinner and lunch. Oh yes I almost forgot, monks didn't eat breakfast. Their usual first meal is like 12 or 12:30 as a straight dinner.
As in Other Orthodox monasteries, here in Pomorie Monastery the monastery is named after the heavenly protector of the place Saint Martyr George.
The brotherhood life here is not as tough as the monasteries located in desert destinations, though just like in other mountain situated Orthodox Christian monasteries the monks has an established everyday Morning and Evening Church Service.
The morning Church service usually starts around 06:00 or 06:30, while on a feast days like Sunday (The Day of Resurrection of Jesus Christ) the service starts a bit later in 07:00 or at very special occasions in 07:30 …
The Evening Services usually start around 04:30 or 05:00 o'clock and continue (depending on Church calendar feast day (saint)) from 30 to 40 minutes up to 2, 3 hours (in biggest feasts or fasting periods).
All the monks should be present on Morning and Evening service, where a bell is rang whether the monks has to gather together for a Church service prayer.
As of time of writting officially Pomorie monastery has 4 monk brothers. One is the Abbot, the abbot's left hand, one other hiero-monk who sometimes is serving the Holy Liturgy church services and another monk who is in his 70s and is mostly doing Church book readings.
Occasionally the brotherhood accepts a novice pupils who want to enter the monastic life, but as long as my observations goes (during the few years I came as a pilgrim here) many of the novices find the monastic life for them and quit after a few months or a year time.
Just a year earlier the brotherhood, here had 6 monks. Unfortunately the oldest monk Father Tikhon who lived inside the monastery more than half of his life (40 years in the monastery W0W!) passed away after a short sickness and hospitalization.
Another one of the monks (Father Joanikius) was transferred by the Sliven's Metropolitan (named also father Joanikius) to serve his monkship (obedience) in our Bulgarian Monastery situation in Holy Mount Athos (Greece) , e.g. to Zographus monastery.
The Abbot of the monastery (Father Yierotej) is a young and energetic person (35 years old) with a good sense of humour and a great God given wisdom grace and joyful temper.
Besides the core monks brothrehood currently the monastery has 5 workers and about 5 to 10 persons (people who are in hardships and have no place to stay) and were accepted to get a healing and a life stabilization while living for a while in the monastery. Some of those people are almost full time living inside the monsatic walls helping with their knowledge and talents to the brotherhood
The overall number of people who inhibit the monastery is about rawly 15 people.
All this people are given free meals 2 times daily and eat together often either in the monastic kitchen or the dining-room (which is also serving as a guest room).
Before and after each meal intake the people gathered together in the dinner-room pray together asking Jesus Christ to bless their food and drink. Usually the Abbot whenever on the table is the one to ask God for a food blessing. After the meal is complete the Abbot or some of the monks says a thanksful prayer thanking Jesus for giving the daily bread and asking God to give us also the heavenly spiritual food.
The most common food eaten here is vegetables and fruits and in non-fasting days they eat some youghurt, cheese or fish. Eating meat however is un-common and most of the food consumed is fasting food (meat is considered inappropriate food for Orth Christian Monks).
The monastery is surrounded by a around a meter monastic walls. In the middle of the monastery is located the Monastic Church Saint Martyr George whichs basic walls dates back to the distant XIX century.

Facing the church about 40 meters from the Chuch are located the monks dwelling rooms also in monastic language called (cells). The monk's cell is full of icon and holy water, crucific crosses and all kind of faith related books so in a sense the monks room looks like a tiny Church.
Right in the middle of Pomorie Monsatery there is a holy spring – disease healing water which by God's providence healed the first Abbot and beneficient of the monastery (ironically the Turkish Abbot Salim Bey who converted from Islam to Christianity and donated all his land to the Bulgarian Orthodox Church in the 18 century when still Bulgaria was enslaved by Turkish).
The monastic yard is filled with green beautiful Peach and Plumb Trees. In the monastery yard they have sew of; potatoes, tomatoes, corn and few other "basic" self-grown. vegetables.

Along with the plants in one of the corners near the monastic wall there is a henhouse where some chickens and few turkeys are grown for getting fresh (natural) eggs.
In the old days the brotherhood was growing all their food by themselves as it was a tradition in the Monasteries, however with the changing times and the huge decrease of monks, growing all the monastic food on their-own became an impossible task ….
The monastery is mainly living on pilgrim or local believing people donations and the monastic land, as well as to sales of Orthodox icons and tiny faith related objects (crosses, holy bibles, church related books and literature) etc.
As I hear from some of the monks the harsh economic situation and severe world crisis that is plaguing the world also has a negative influence on the financial balance of the holy cloister too.
A monk shared with me the financial expenses of the monastery tend to be "dangerously" growing lately as the amount of people whose the brotherhood is feeding and taking care (healing) daily along with the money for restoration works are raising and the monastery experiences a shortage of money.
Still they're not discouraged but as I was told praying and hoping on God's grace to send them kind heart donators to help the monastery.
On Pomorie Monastery's website there is an e-PayPal donation form through which willing donators can help financially the monastic community
Most of the people who are in the monsatery not for a theraupetic reason (with a severe disease) work all day long. Though the work seems to be never ending here, one feels calm, relaxed and gracious.
Even staying for few hours here, makes you filled-up with God's grace and gives you new energy and hope to continue the harsh daily stress filled life.
Besides the Monastery the town of Pomorie is also very beuatiful and have all the facilities and entertainment a tourist might like to have from a modern beach resort. Yesterday I went and had my first beach time here in Pomorie.
Something interesting I noticed on the beach is the sand color which here in Pomorie is a bit blackish. The sea coast here near the beach is not big but feels cozy and there are bars near the beach shore, so anyone wanting to enjoy some of the world goods too can have a fanastic time here 🙂
Tags: Auto, brotherhood, chef, chef cook, christian monasteries, christians, cook, counselors, desert, Draft, evening church service, Father, feast, feast days, King, Kingdom, kingdoms, lunch, martyr george, meal preparations, Monastery, Monday, monk, Monks, morning, morning and evening, Mountain, orthodox christian, orthodox monasteries, Other, person, pilgrimage, place, pomorie, quot, saint, Service, st george, time, vegetables, Wednesday, year
Posted in Christianity, Everyday Life | 1 Comment »
Saturday, May 28th, 2011 One of the mail server clients is running into issues with secured SSL IMAP connections ( he has to use a multiple email accounts on the same computer).
I was informed that part of the email addresses are working correctly, however the newly created ones were failing to authenticate even though all the Outlook Express email configuration was correct as well as the username and password typed in were a real existing credentials on the vpopmail server.
Initially I thought, something is wrong with his newly configured emails but it seems all the settings were perfectly correct!
After a lot of wondering what might be wrong I was dumb enough not to check my imap log files.
After checking in my /var/log/mail.log which is the default log file I’ve configured for vpopmail and some of my qmail server services, I found the following error repeating again and again:
imapd-ssl: Maximum connection limit reached for ::ffff:xxx.xxx.xxx.xxx" imapd-ssl error
where xxx.xxx.xxx.xxx was the email user computer IP address.
This issues was caused by one of my configuration settings in the imapd-ssl and imap config file:
/usr/lib/courier-imap/etc/imapd
In /usr/lib/courier-imap/etc/imapd there is a config segment called
Maximum number of connections to accept from the same IP address
Right below this commented text is the variable:
MAXPERIP=4
As you can see it seems I used some very low value for the maximum number of connections from one and the same IP address.
I suppose my logic to set such a low value was my desire to protect the IMAP server from Denial of Service attacks, however 4 is really too low and causes problem, thus to solve the mail connection issues for the user I raised the MAXPERIP value to 50:
MAXPERIP=50
Now to force the new imapd and imapd-ssl services to reload it’s config I did a restart of the courier-imap, like so:
debian:~# /etc/init.d/courier-imap restart
That’s all now the error is gone and the client could easily configure up to 50 mailbox accounts on his PC 🙂
Tags: address right, client, config, configuration settings, configure, connection, courier imap, credentials, default log, Denial, denial of service, denial of service attacks, email accounts, email addresses, errorwhere, Express, ffff, file, imap connections, imap server, init, lib, limit, mail connection, mail log, mail server, Maximum, maximum connection, maximum number, outlook, outlook express, password, quot, segment, server clients, server services, Service, something, ssl services, text, username, value
Posted in Linux, Qmail, System Administration | 2 Comments »














