Posts Tagged ‘apache webserver’
Wednesday, July 1st, 2020 
Did you happen to administer Apache Webservers or NGINX webservers whose logs start to grow so rapidly that are flooding the disk too quickly?
Well this happens sometimes and it also happens that sometimes you just want to stop logging especially, to offload disk writting.
There is an easy way to disable logging for requests and errors (access_log and error_log usually residing under /var/log/httpd or /var/log/nginx ) for all configured Virtual Domains with a short one liner, here is how.
Before you start Create backup of /etc/apache2/sites-enabled / or /etc/nginx to be able to revert back to original config.
# cp -rpf /etc/apache2/sites-enabled/ ~/
# cp -rpf /etc/nginx/ ~/
1. Disable Logging for All Virtual Domains configured for Apache Webserver
First lets print what the command will do to make sure we don't mess something
# find /home/hipo/sites-enabled/* -exec echo sed -i 's/#*[Cc]ustom[Ll]og/#CustomLog/g' {} \;
You will get some output like
find /home/hipo//sites-enabled/* -exec echo sed -i 's/#*[Cc]ustom[Ll]og/#CustomLog/g' {} \;
find /etc/apache2/sites-enabled/* -exec sed -i 's/#*[Cc]ustom[Ll]og/#CustomLog/g' {} \;
find /etc/apache2/sites-enabled/* -exec sed -i 's/#*[Ee]rror[Ll]og/#ErrorLog/g' {} \;
2. Disable Logging for All configured Virtual Domains for NGINX Webserver
find /etc/nginx/sites-enabled/* -exec sed -i 's/#*access_log/#access_log/g' {} \;
find /etc/nginx/sites-enabled/* -exec sed -i 's/#*error_log/#error_log/g' {} \;
f course above substituations that will comment out with '#' occurances from file configs of only default set access_log and error_log / access.log, error.log
for machines where there is no certain convention on file naming and there are multiple domains in custom produced named log files this won't work.
This one liner was inspired from a friend's daily Martin Petrov. Martin blogged initially about this nice tip for those reading Cyrillic check out mpetrov.net, so. Thanks Marto ! 🙂
Tags: about, access, ALL, and, apache, apache webserver, apache webservers, apache2, are, BACK, blogged, check, command, Comment, config, configured, convention, course, create, custom
Posted in Everyday Life, Nginx, Web and CMS | No Comments »
Tuesday, April 7th, 2015 
There are plenty of security schemes and strategies you can implement if you're a Shared Web Hosting company sysadmin however probably the most vital one is to install on Apache + PHP Webserver SuPHP module.
# apt-cache show suphp-common|grep -i descrip -A 4
Description: Common files for mod suphp Suphp consists of an Apache module (mod_suphp for either Apache 1.3.x or Apache 2.x) and a setuid root binary (suphp) that is called by the Apache module to change the uid of the process executing the PHP interpreter to the owner of the php script.
So what SuPHP actuall does is to run separate CPanel / Kloxo etc. Users with separate username and groupid permissions coinciding with the user present in /etc/passwd , /etc/shadow files existing users, thus in case if someone hacks some of the many customer sites he would be able to only write files and directories under the user with which the security breach occured.
On servers where SuPHP is not installed, all systemusers are using the same UserID / GuID to run PHP executable scripts under separate domains Virtualhost which are coinciding with Apache (on Debian / Ubuntu uid, gid – www-data) or on (CentOS / RHEL / Fedora etc. – user apache) so once one site is defaced exploited by a worm all or most server websites might end up infected with a Web Virus / Worm which will be trying to exploit even more sites of a type running silently in the background. This is very common scenarios as currently there are donezs of PHP / CSS / Javasripts / XSS vulnerability exploited on VPS and Shared hosting servers due to failure of a customer to update his own CMS scripts / Website (Joomla, Wordpress, Drupal etc.) and the lack of resource to regularly monitor all customer activities / websites.
Therefore installing SuPHP Apache module is essential one to install on new serverslarge hosting providers as it saves the admin a lot of headache from spreading malware across all hosted servers sites ..
Some VPS admins that are security freaks tend to also install SuPHP module together with many chrooted Apache / LiteSpeed / Nginx webservers each of which running in a separate Jailed environment.
Of course using SuPHP besides giving a improved security layer to the webserver has its downsides such as increased load for the server and making Apache PHP scripts being interpretted a little bit slower than with plain Apache + PHP but performance difference while running a site on top of SuPHP is often not so drastic so you can live it up ..
Installing SuPHP on a Debian / Ubuntu servers is a piece of cake, just run the as root superuser, usual:
# apt-get install libapache2-mod-suphp
Once installed only thing to make is to turn off default installed Apache PHP module (without SuPHP compiled support and restart Apache webserver):
# a2dismod php5 …
# /etc/init.d/apache2 restart
…
To test the SuPHP is properly working on the Apache Webserver go into some of many hosted server websites DocumentRoot
And create new file called test_suphp.php with below content:
# vim test_suphp.php
<?php
system('id');
?>
Then open in browser http://whatever-website/test_suphp.php assuming that system(); function is not disabled for security reasons in php.ini you should get an User ID, GroupID bigger than reserved system IDs on GNU / Linux e.g. ID > UID / GID 99
Its also a good idea to take a look into SuPHP configuration file /etc/suphp/suphp.conf and tailor options according to your liking
If different hosted client users home directories are into /home directory, set in suphp.conf
;Path all scripts have to be in
docroot=/home/
Also usually it is a good idea to set
umask=0022
Tags: apache webserver, customer, debian linux, file, good, home directory, hosting servers, how to install suphp apache better security, improve apache user security suphp, install suphp debian, level, Linux, piece of cake, plenty, read, root, running, scripts, security, security breach, server, servers, setup, Shared Web Hosting, sysadmin, website, Website Joomla
Posted in Computer Security, Linux, System Administration, Various, Web and CMS | No Comments »
Monday, March 30th, 2015 
If you're a Webhosting company sysadmin like me and you already have configured directory listing for certain websites / Vhosts and those files are mirrored from other development webserver location but some of the uploaded developer files extensions which are allowed to be interptered such as php include files .inc / .htaccess mod_rewrite rules / .phps / .html / .txt need to be working on the dev / test server but needs to be disabled (excluded) from delivery or interpretting for some directory on the prod server.
Open Separate host VirtualHost file or Apache config (httpd.conf / apache2.conf) if all Vhosts for which you want to disable certain file extensions and add inside:
<Directory "/var/www/sploits">
AllowOverride All
…
</Directory>
Extension Deny Rules such as:
For disabling .inc files from inclusion from other PHP sources:
<Files ~ "\.inc$">
Order allow,deny
Deny from all
</Files>
To Disable access to .htaccess single file only
<Files ~ "^\.htaccess">
Order allow,deny
Deny from all
</Files>
To Disable .txt from being served by Apache and delivered to requestor browser:
<Files ~ "\.txt$">
Order allow,deny
Deny from all
</Files>
To Disable any left intact .html from being delivered to client:
<Files ~ "\.html$">
Order allow,deny
Deny from all
</Files>
Do it for as many extensions as you need.
Finally to make changes affect restart Apache as usual:
If on Deb based Linux issue:
/etc/init.d/apach2 restart
On CentOS / RHEL and other Redhats / RedHacks 🙂
/etc/init.d/httpd restart
Tags: apache webserver, client, development, httpd, init, left, Linux, make, need, php, Virtualhost, www
Posted in System Administration, Various, Web and CMS | 1 Comment »
Tuesday, March 10th, 2015 
Something very useful that most Apache LAMP (Linux Apache MySQL PHP) admins should know is how to check Apache Webserver uptime and MySQL server running (uptime).
Checking Apache / MySQL uptime is primary useful for scripting purposes – creating auto Apache / MySQL service restart scripts, or just as a quick console way to check what is the status and uptime of Webserver / SQL.
My experience as a sysadmin shows that lack of Periodic Apache and MySQL restart every week or every month often creates sys-admin a lot of a headaches cause (Apache / NGINX / SQL server) starts eating too much memory or under some circumstances leads to service or system crashes. Periodic system main services restart is especially helpful in case if Website's backend programming code is writetn in a bad and buggy uneffient way by unprofessional (novice) programmers.
While I was still working as Senior SysAdmin in Design.BG, I've encountered many such Crappy Web applications developed by dozen of different programmers (because company's programmers changed too frequently and many of the hired Web Developers ,were still learning to program, I guess same is true also for other Start-UP Web / IT Company where crappy programming code is developed you will certainly need to keep an eye on Apache / MYSQL uptime. If that's the case below 2 quick one liners with PS command will help you keep an eye on Apache / MYSQL uptime
ps -eo "%U %c %t"| grep apache2 | grep -v grep|grep root
root apache2 02:30:05
Note that above example is Debian specific on RPM based distributions you will have to grep for httpd instead of apache2
ps -eo "%U %c %t"| grep http| grep -v grep|grep root
root apache2 10:30:05
To check MySQL uptine:
ps -eo "%U %c %t"| grep mysqld
root mysqld_safe 20:42:53
mysql mysqld 20:42:53
Though example is for mysql and Apache you can easily use ps cmd in same way to check any other Linux service uptime such as Java / Qmail / PostgreSQL / Postfix etc.
ps -eo "%U %c %t"|grep qmail
qmails qmail-send 19-01:10:48
qmaill multilog 19-01:10:48
qmaill multilog 19-01:10:48
qmaill multilog 19-01:10:48
root qmail-lspawn 19-01:10:48
qmailr qmail-rspawn 19-01:10:48
qmailq qmail-clean 19-01:10:48
qmails qmail-todo 19-01:10:48
qmailq qmail-clean 19-01:10:48
qmaill multilog 40-18:02:53
ps -eo "%U %c %t"|grep -i nginx|grep -v root|uniq
nobody nginx 55-01:22:44
ps -eo "%U %c %t"|grep -i java|grep -v root |uniq
hipo java 27-22:02:07
Tags: apache webserver, apache2, case, cms, command, Crappy Web, crashes, daemon, doesn, example, eye, grep, headaches, How to, lot, multilog, mysqld, primary, programmers, programming code, root, running, scripting, scripts, week
Posted in Everyday Life, Linux, Monitoring, Programming, System Administration | No Comments »
Saturday, March 24th, 2012 
I've written a tiny script to check and restart, Apache if the server encounters, extremely high load avarage like for instance more than (>25). Below is an example of a server reaching a very high load avarage:;
server~:# uptime
13:46:59 up 2 days, 18:54, 1 user, load average: 58.09, 59.08, 60.05
load average: 0.09, 0.08, 0.08
Sometimes high load avarage is not a problem, as the server might have a very powerful hardware. A high load numbers is not always an indicator for a serious problems. Some 16 CPU dual core (2.18 Ghz) machine with 16GB of ram could probably work normally with a high load avarage like in the example. Anyhow as most servers are not so powerful having such a high load avarage, makes the machine hardly do its job routine.
In my specific, case one of our Debian Linux servers is periodically reaching to a very high load level numbers. When this happens the Apache webserver is often incapable to serve its incoming requests and starts lagging for clients. The only work-around is to stop the Apache server for a couple of seconds (10 or 20 seconds) and then start it again once the load avarage has dropped to less than "3".
If this temporary fix is not applied on time, the server load gets increased exponentially until all the server services (ssh, ftp … whatever) stop responding normally to requests and the server completely hangs …
Often this server overloads, are occuring at night time so I'm not logged in on the server and one such unexpected overload makes the server unreachable for hours.
To get around the sudden high periodic load avarage server increase, I've written a tiny bash script to monitor, the server load avarage and initiate an Apache server stop and start with a few seconds delay in between.
#!/bin/sh
# script to check server for extremely high load and restart Apache if the condition is matched
check=`cat /proc/loadavg | sed 's/\./ /' | awk '{print $1}'`
# define max load avarage when script is triggered
max_load='25'
# log file
high_load_log='/var/log/apache_high_load_restart.log';
# location of inidex.php to overwrite with temporary message
index_php_loc='/home/site/www/index.php';
# location to Apache init script
apache_init='/etc/init.d/apache2';
#
site_maintenance_msg="Site Maintenance in progress - We will be back online in a minute";
if [ $check -gt "$max_load" ]; then>
#25 is load average on 5 minutes
cp -rpf $index_php_loc $index_php_loc.bak_ap
echo "$site_maintenance_msg" > $index_php_loc
sleep 15;
if [ $check -gt "$max_load" ]; then
$apache_init stop
sleep 5;
$apache_init restart
echo "$(date) : Apache Restart due to excessive load | $check |" >> $high_load_log;
cp -rpf $index_php_loc.bak_ap $index_php_loc
fi
fi
The idea of the script is partially based on a forum thread – Auto Restart Apache on High Load – http://www.webhostingtalk.com/showthread.php?t=971304Here is a link to my restart_apache_on_high_load.sh script
The script is written in a way that it makes two "if" condition check ups, to assure 100% there is a constant high load avarage and not just a temporal 5 seconds load avarage jump. Once the first if is matched, the script first tries to reduce the server load by overwritting a the index.php, index.html script of the website with a one stating the server is ongoing a maintenance operations.
Temporary stopping the index page, often reduces the load in 10 seconds of time, so the second if case is not necessery at all. Sometimes, however this first "if" condition cannot decrease enough the load and the server load continues to stay too high, then the script second if comes to play and makes apache to be completely stopped via Apache init script do 2 secs delay and launch the apache server again.
The script also logs about, the load avarage encountered, while the server was overloaded and Apache webserver was restarted, so later I can check what time the server overload occured.
To make the script periodically run, I've scheduled the script to launch every 5 minutes as a cron job with the following cron:
# restart Apache if load is higher than 25
*/5 * * * * /usr/sbin/restart_apache_on_high_load.sh >/dev/null 2>&1
I have also another system which is running FreeBSD 7_2, which is having the same overload server problems as with the Linux host.
Copying the auto restart apache on high load script on FreeBSD didn't work out of the box. So I rewrote a little chunk of the script to make it running on the FreeBSD host. Hence, if you would like to auto restart Apache or any other service on FreeBSD server – get /usr/sbin/restart_apache_on_high_load_freebsd.sh my script and set it on cron on your BSD.
This script is just a temporary work around, however as its obvious that the frequency of the high overload will be rising with time and we will need to buy new server hardware to solve permanently the issues, anyways, until this happens the script does a great job 🙂
I'm aware there is also alternative way to auto restart Apache webserver on high server loads through using monit – utility for monitoring services on a Unix system. However as I didn't wanted to bother to run extra services in the background I decided to rather use the up presented script.
Interesting info to know is Apache module mod_overload exists – which can be used for checking load average. Using this module once load avarage is over a certain number apache can stop in its preforked processes current serving request, I've never tested it myself so I don't know how usable it is. As of time of writting it is in early stage version 0.2.2
If someone, have tried it and is happy with it on a busy hosting servers, please share with me if it is stable enough?
Tags: Anyhow, apache server, apache webserver, Auto, avarage, awk print, bak, bash script, bash shell, bash shell script, condition, cron, cron job, Draft, dual core, host, incoming requests, index, index page, init, instance, job, level, level numbers, Linux, linux servers, loc, location, night time, php, quot, Restart, restart apache, rpf, script, server load, server overloads, server services, server uptime, Shell, ssh, ssh ftp, time, unexpected overload, unreachable, utility
Posted in FreeBSD, Programming, System Administration | 5 Comments »
Tuesday, September 18th, 2012 Almost evertime whether install a new Debian Linux server to host some websites, use the popular small and mid-sized hosting solution combination:
- Apache webserver
- PHP module to interpret the PHP programming code
- MySQL to store the DB Backend
Installing the basis for on Debian is easy:
# apt-get install --yes apache2 apache2-mpm-prefork libapache2-mod-php \
mysql-server php5 php5-mysql mysql-client mysql-common phpmyadmin
....
This of course is in case, if necessery to run websites which are written to usephp code which is not thread safety (Use Apache child prefork technology to manage processes); For websites writen to be thread safety (not use some forking php functions like: php – exec(); fork(); etc. – I install apache2-mpm-prefork for better Webserver performance and speed.
This minimum collection of packages is good only for basic, websites and most Joomla, WordPress, Drupal or whatever custom PHP websites has to be hosted usually require much more PHP functions which are not part of this basic bundle. Hence as I said prior on almost all new Linux debian / ubuntu deb package based servers need to install following list of extra PHP deb packages:
# apt-get install --yes php-apc php-auth-ssl php-mail \
php-http php-net-smtp php-net-socket php-pear php5-cli php5-curl \
php5-gd php5-imagick php5-mapscript php5-mcrypt php5-odbc php5-sybase \
php5-xsl
...,
After installing this standard bundle of modules PHP is extended to support somenice functionalities like Image editting / convertion / resizing … various graphic editting functions as supported by infamous ImageMagick and GDlib, PEAR support (PHP Extension and Application Repository) bundle providing number of useful PHP classes.
php5-xInstalling Usual PHP Apache needed modules for new Debian GNU / Linux serverssl is usually necessery for websites which pass data in XSL format (a specific formatted XML data). php5-xsl is usually necessery for websites containing flash animations – Presentation, videos, games etc.
That is mostly it, hope this helps some sys admin like me who need configure new Debian based hosting server 🙂
Tags: apache webserver, combination, debian linux, hosting server, necessery, need, php, sys admin, thread, Use Apache
Posted in Joomla, Various, Web and CMS, Wordpress | No Comments »
Friday, July 22nd, 2011 There are few commands I usually use to track if my server is possibly under a Denial of Service attack or under Distributed Denial of Service
Sys Admins who still have not experienced the terrible times of being under a DoS attack are happy people for sure …
1. How to Detect a TCP/IP Denial of Service Attack This are the commands I use to find out if a loaded Linux server is under a heavy DoS attack, one of the most essential one is of course netstat.
To check if a server is under a DoS attack with netstat, it’s common to use:
linux:~# netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n|wc -l
If the output of below command returns a result like 2000 or 3000 connections!, then obviously it’s very likely the server is under a DoS attack.
To check all the IPS currently connected to the Apache Webserver and get a very brief statistics on the number of times each of the IPs connected to my server, I use the cmd:
linux:~# netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
221 80.143.207.107 233 145.53.103.70 540 82.176.164.36
As you could see from the above command output the IP 80.143.207.107 is either connected 221 times to the server or is in state of connecting or disconnecting to the node.
Another possible way to check, if a Linux or BSD server is under a Distributed DoS is with the list open files command lsof
Here is how lsof can be used to list the approximate number of ESTABLISHED connections to port 80.
linux:~# lsof -i TCP:80
litespeed 241931 nobody 17u IPv4 18372655 TCP server.www.pc-freak.net:http (LISTEN)
litespeed 241931 nobody 25u IPv4 18372659 TCP 85.17.159.89:http (LISTEN)
litespeed 241931 nobody 30u IPv4 29149647 TCP server.www.pc-freak.net:http->83.101.6.41:54565 (ESTABLISHED)
litespeed 241931 nobody 33u IPv4 18372647 TCP 85.17.159.93:http (LISTEN)
litespeed 241931 nobody 34u IPv4 29137514 TCP server.www.pc-freak.net:http->83.101.6.41:50885 (ESTABLISHED)
litespeed 241931 nobody 35u IPv4 29137831 TCP server.www.pc-freak.net:http->83.101.6.41:52312 (ESTABLISHED)
litespeed 241931 nobody 37w IPv4 29132085 TCP server.www.pc-freak.net:http->83.101.6.41:50000 (ESTABLISHED)
Another way to get an approximate number of established connections to let’s say Apache or LiteSpeed webserver with lsof can be achieved like so:
linux:~# lsof -i TCP:80 |wc -l
2100
I find it handy to keep track of above lsof command output every few secs with gnu watch , like so:
linux:~# watch "lsof -i TCP:80"
2. How to Detect if a Linux server is under an ICMP SMURF attack
ICMP attack is still heavily used, even though it’s already old fashioned and there are plenty of other Denial of Service attack types, one of the quickest way to find out if a server is under an ICMP attack is through the command:
server:~# while :; do netstat -s| grep -i icmp | egrep 'received|sent' ; sleep 1; done
120026 ICMP messages received
1769507 ICMP messages sent
120026 ICMP messages received
1769507 ICMP messages sent
As you can see the above one liner in a loop would check for sent and recieved ICMP packets every few seconds, if there are big difference between in the output returned every few secs by above command, then obviously the server is under an ICMP attack and needs to hardened.
3. How to detect a SYN flood with netstat
linux:~# netstat -nap | grep SYN | wc -l
1032
1032 SYNs per second is quite a high number and except if the server is not serving let’s say 5000 user requests per second, therefore as the above output reveals it’s very likely the server is under attack, if however I get results like 100/200 SYNs, then obviously there is no SYN flood targetting the machine 😉
Another two netstat command application, which helps determining if a server is under a Denial of Service attacks are:
server:~# netstat -tuna |wc -l
10012
and
server:~# netstat -tun |wc -l
9606
Of course there also some other ways to check the count the IPs who sent SYN to the webserver, for example:
server:~# netstat -n | grep :80 | grep SYN |wc -l
In many cases of course the top or htop can be useful to find, if many processes of a certain type are hanging around.
4. Checking if UDP Denial of Service is targetting the server
server:~# netstat -nap | grep 'udp' | awk '{print $5}' | cut -d: -f1 | sort |uniq -c |sort -n
The above command will list information concerning possible UDP DoS.
The command can easily be accustomed also to check for both possible TCP and UDP denial of service, like so:
server:~# netstat -nap | grep 'tcp|udp' | awk '{print $5}' | cut -d: -f1 | sort |uniq -c |sort -n
104 109.161.198.86
115 112.197.147.216
129 212.10.160.148
227 201.13.27.137
3148 91.121.85.220
If after getting an IP that has too many connections to the server and is almost certainly a DoS host you would like to filter this IP.
You can use the /sbin/route command to filter it out, using route will probably be a better choice instead of iptables, as iptables would load up the CPU more than simply cutting the route to the server.
Here is how I remove hosts to not be able to route packets to my server:
route add 110.92.0.55 reject
The above command would null route the access of IP 110.92.0.55 to my server.
Later on to look up for a null routed IP to my host, I use:
route -n |grep -i 110.92.0.55
Well hopefully this should be enough to give a brief overview on how, one can dig in his server and find if he is under a Distributed Denial of Service, hope it’s helpful to somebody out there.
Cheers 😉
Tags: apache webserver, approximate number, awk print, BSD, checking, cmd, command, course, Denial, denial of service, denial of service attack, Detect, difference, dos attack, ESTABLISHED, freak, How to, HTTP, ICMP, ips, Linux, linux server, linux webserver, LISTEN, litespeed, netstat, nobody, node, ntu, number, server pc, Service, sleep, statistics, SYN, SYNs, sys admins, tcp, terrible times, Watch
Posted in Linux, System Administration | 5 Comments »
Wednesday, February 26th, 2014 
Having a combination of Apache webservice Reverse Proxy to redirect invisibly traffic to a number of Tomcat server positioned in a DMZ is a classic task in big companies Corporate world.
Hence if you work for company like IBM or HP sooner or later you will need to configure Apache Webserver cluster with few running Jakarta Tomcat Application servers behind. Scenario with necessity to access a java based application via Tomcat which requires logging (authentication) relaying on establishing and keeping a session ID is probably one of the most common ones and if you do it for first time you will probably end up with Session ID issues. Session ID issues are hard to capture at first as on first glimpse application will seem to be working but users will have to re-login all the time even though the programmers might have coded for a session to expiry in 30 minutes or so.
… I mean not having configured Session ID prevention to Tomcats will cause random authentication session expiries and users using the Tomcat app will be unable to normally access below application with authenticated credentials. The solution to these is known under term "Sticky sessions"
To configure Sticky sessions you need to already have configured Apache/s with following minimum configuration:
- enabled mod_proxy, proxy_balancer_module, proxy_http_module and or mod_proxy_ajp (in Apache config)
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_balancer_module modules/mod_proxy_balancer.so
LoadModule proxy_http_module modules/mod_proxy_http.so
- And configured and tested Tomcats running an Application reachable via AJP protocol
Below example assumes there is Reverse Proxy Load Balancer Apache which has to forward all traffic to 2 tomcats. The config can easily be extended for as many as necessary by adding more BalancerMembers.
In Apache webserver (apache2.conf / httpd.conf) you need to have JSESSIONID configured. These JSESSIONID is going to be appended to each client request from Reverse Proxy to each of Tomcat servers with value opened once on authentication to first Tomcat node to each of the other ones.
<Proxy balancer://mycluster>
BalancerMember ajp://10.16.166.53:11010/ route=delivery1
BalancerMember ajp://10.16.166.66:11010/ route=delivery2
</Proxy>
ProxyRequests Off
ProxyPass / balancer://mycluster/ stickysession=JSESSIONID
ProxyPassReverse / balancer://mycluster/
The two variables route=delivery1 and route=delivery2 are routed to hosts identificators that also has to be present in Tomcat server configurations
In Tomcat App server First Node (server.xml)
<Engine name="Catalina" defaultHost="localhost" jvmRoute="delivery1">
In Tomcat App server Second Node (server.xml)
<Engine name="Catalina" defaultHost="localhost" jvmRoute="delivery2">
Once Sticky Sessions are configured it is useful to be able to track they work fine this is possible through logging each of established JESSSIONIDs, to do so add in httpd.conf
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"\"%{JSESSIONID}C\"" combined
After modifications restart Apache and Tomcat to load new configs. In Apache access.log the proof should be the proof that sessions are preserved via JSESSIONID, there should be logs like:
127.0.0.1 - - [18/Sep/2013:10:02:02 +0800] "POST /examples/servlets/servlet/RequestParamExample HTTP/1.1" 200 662 "http://localhost/examples/servlets/servlet/RequestParamExample" "Mozilla/5.0 (X11; Linux x86_64; rv:17.0) Gecko/20130807 Firefox/17.0""B80557A1D9B48EC1D73CF8C7482B7D46.server2"
127.0.0.1 - - [18/Sep/2013:10:02:06 +0800] "GET /examples/servlets/servlet/RequestInfoExample HTTP/1.1" 200 693 "http://localhost/examples/servlets/" "Mozilla/5.0 (X11; Linux x86_64; rv:17.0) Gecko/20130807 Firefox/17.0""B80557A1D9B48EC1D73CF8C7482B7D46.server2"
That should solve problems with mysterious session expiries 🙂
Tags: AJP, apache webserver, apache2, application, authentication, combination, conf, configured, DMZ, Engine, First Node, hp, httpd, ID, Jakarta Tomcat Application, JESSIONID, JSESSIONID, localhost, need, number, proof, proxy, request, Reverse Proxy, Reverse Proxy Load Balancer Apache, run, Second Node, server, session, working, xml
Posted in Linux, System Administration, Various | 2 Comments »
Monday, March 19th, 2012 
One of the company Debian Lenny 5.0 Webservers, where I'm working as sys admin sometimes stops to properly server HTTP requests.
Whenever this oddity happens, the Apache server seems to be running okay but it is not failing to return requested content
I can see the webserver listens on port 80 and establishing connections to remote hosts – the apache processes show normally as I can see in netstat …:
apache:~# netstat -enp 80
Active Internet connections (w/o servers)
Proto Recv-Q Send-Q Local Address Foreign Address State User Inode PID/Program name
tcp 0 0 xxx.xxx.xxx.xx:80 46.253.9.36:5665 SYN_RECV 0 0 -
tcp 0 0 xxx.xxx.xxx.xx:80 78.157.26.24:5933 SYN_RECV 0 0 -
...
Also the apache forked child processes show normally in process list:
apache:~# ps axuwwf|grep -i apache
root 46748 0.0 0.0 112300 872 pts/1 S+ 18:07 0:00 \_ grep -i apache
root 42530 0.0 0.1 217392 6636 ? Ss Mar14 0:39 /usr/sbin/apache2 -k start
www-data 42535 0.0 0.0 147876 1488 ? S Mar14 0:01 \_ /usr/sbin/apache2 -k start
root 28747 0.0 0.1 218180 4792 ? Sl Mar14 0:00 \_ /usr/sbin/apache2 -k start
www-data 31787 0.0 0.1 219156 5832 ? S Mar14 0:00 | \_ /usr/sbin/apache2 -k start
In spite of that, in any client browser to any of the Apache (Virtual hosts) websites, there is no HTML content returned…
This weird problem continues until the Apache webserver is retarted.
Once webserver is restarted everything is back to normal.
I use Apache Check Apache shell script set on few remote hosts to regularly check with nmap if port 80 (www) of my server is open and responding, anyways this script just checks if the open and reachable and thus using it was unable to detect Apache wasn't able to return back HTML content.
To work around the malfunctions I wrote tiny script – retart_apache_if_empty_content_is_returned.sh
The scripts idea is very simple;
A request is made a remote defined host with lynx text browser, then the output of lines is counted, if the output returned by lynx -dump http://someurl.com is less than the number returned whether normally invoked, then the script triggers an apache init script restart.
I've set the script to periodically run in a cron job, every 5 minutes each hour.
# check if apache returns empty content with lynx and if yes restart and log it
*/5 * * * * /usr/sbin/restart_apache_if_empty_content.sh >/dev/null 2>&1
This is not perfect as sometimes still, there will be few minutes downtime, but at least the downside will not be few hours until I am informed ssh to the server and restart Apache manually …
A quick way to download and set from cron execution my script every 5 minutes use:
apache:~# cd /usr/sbin
apache:/usr/sbin# wget -q https://www.pc-freak.net/bscscr/restart_apache_if_empty_content.sh
apache:/usr/sbin# chmod +x restart_apache_if_empty_content.sh
apache:/usr/sbin# crontab -l > /tmp/file; echo '*/5 * * * *' /usr/sbin/restart_apache_if_empty_content.sh 2>&1 >/dev/null
Tags: address state, apache processes, apache server, apache webserver, apache2, apacheroot, Auto, checks, child processes, client, client browser, content, cron, Draft, enp, everything, grep, HTML, HTTP, internet connections, lenny, Lynx, nmap, oddity, program, proto, Restart, restart apache, root, script, scripts, Shell, shell script, show, spite, ss, SYN, User, Virtual, virtual hosts, webservers, weird problem
Posted in System Administration, Web and CMS | 7 Comments »
Wednesday, March 7th, 2012 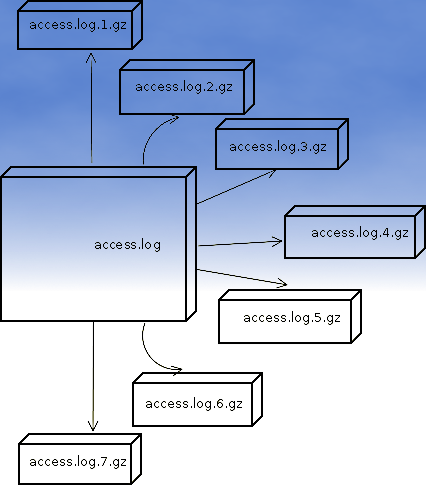
If you are sys admin of Apache Webserver running on Debian Linux relying on logrorate to rorate logs, you might want to change the default way logroration is done.
Little changes in the way Apache log files are served on busy servers can have positive outcomes on the overall way the server CPU units burden. A good logrotation strategy can also prevent your server from occasional extra overheads or downtimes.
The way Debian GNU / Linux process logs is well planned for small servers, however the default logroration Apache routine doesn't fit well for servers which process millions of client requests each day.
I happen to administrate, few servers which are constantly under a heavy load and have occasionally overload troubles because of Debian's logrorate default mechanism.
To cope with the situation I have made few modifications to /etc/logrorate.d/apache2 and decided to share it here hoping, this might help you too.
1. Rotate Apache acccess.log log file daily instead of weekly
On Debian Apache's logrorate script is in /etc/logrotate.d/apache2
The default file content will be like so like so:
debian:~# cat /etc/logrotate.d/apache2
/var/log/apache2/*.log {
weekly
missingok
rotate 52
size 1G
compress
delaycompress
notifempty
create 640 root adm
sharedscripts
postrotate
if [ -f "`. /etc/apache2/envvars ; echo ${APACHE_PID_FILE:-/var/run/apache2.pid}`" ]; then
/etc/init.d/apache2 reload > /dev/null
fi
endscript
}
To change the rotation from weekly to daily change:
weekly
to
#weekly
2. Disable access.log log file gzip compression
By default apache2 logrotate script is tuned ot make compression of rotated file (exmpl: copy access.log to access.log.1 and gzip it, copy access.log to access.log.2 and gzip it etc.). On servers where logs are many gigabytes, once logrotate initiates its scheduled work it will have to compress an enormous log record of apache requests. On very busy Apache servers from my experience, just for a day the log could grow up to approximately 8 / 10 Gigabytes.
I'm sure there are more busy servers out there, which log files are growing to over 100GB for just a single day.
Gzipping a 100GB file piece takes an enormous load on the CPU, as well as often takes long time. When this logrotation gzipping occurs at a moment where the servers CPU cores are already heavy loaded from Apache serving HTTP requests, Apache server becomes inaccessible to most of the clients.
Then for end clients various oddities are experienced, for example Apache dropped connection errors, webserver returning empty pages, or simply inability to respond to the client browser.
Sometimes as a result of the overload, even secure shell connection to SSHD to the server is impossible …
To prevent your server from this roration overloads remove logrorate's default access.log gzipping by commenting:
compress
to
#comment
3. Change maximum log roration by logrorate to be up to 30
By default logrorate is configured to create and keep up to 52 rotated and gzipped access.log files, changing this to a lower number is a good practice (in my view), in cases where log files grow daily to 10 or more GBs. Doing so will save a lot of disk space and reduce the chance the hard disk gets filled in because of the multiple rorated ungzipped enormous access.log files.
To tune the default keep max rorated logs to 30, change:
rotate 52
to
rotate 30
The way logrorate's apache log processing on RHEL / CentOS Linux is working better on high load servers, by default on CentOS logrorate is not configured to do log gzipping at all.
Here is the default /etc/logrorate.d/httpd script for
CentOS release 5.6 (Final)
[hipo@centos httpd]$ cat /etc/logrotate.d/httpd /var/log/httpd/*log {
missingok
notifempty
sharedscripts
postrotate
/bin/kill -HUP `cat /var/run/httpd.pid 2>/dev/null` 2> /dev/null || true
endscript
}
Tags: adm, apache linux, apache log files, apache webserver, apache2, Auto, burden, CentOS, change, client, client requests, compression, connection, copy, cpu units, default mechanism, Disk, doesn, Draft, enormous log, fi, file, gnu linux, gzip, heavy load, init, Linux, linux servers, logrorate, logrotation, logs, mechanism, notifempty, overheads, PID, postrotate, quot, root, rotation, script, server cpu, weeklyto
Posted in Linux, System Administration | No Comments »











Linux: Howto Disable logging for all VirtualHosts on Apache and NGINX Webservers one liner
Wednesday, July 1st, 2020Did you happen to administer Apache Webservers or NGINX webservers whose logs start to grow so rapidly that are flooding the disk too quickly?
Well this happens sometimes and it also happens that sometimes you just want to stop logging especially, to offload disk writting.
There is an easy way to disable logging for requests and errors (access_log and error_log usually residing under /var/log/httpd or /var/log/nginx ) for all configured Virtual Domains with a short one liner, here is how.
Before you start Create backup of /etc/apache2/sites-enabled / or /etc/nginx to be able to revert back to original config.
1. Disable Logging for All Virtual Domains configured for Apache Webserver
First lets print what the command will do to make sure we don't mess something
You will get some output like
2. Disable Logging for All configured Virtual Domains for NGINX Webserver
f course above substituations that will comment out with '#' occurances from file configs of only default set access_log and error_log / access.log, error.log
for machines where there is no certain convention on file naming and there are multiple domains in custom produced named log files this won't work.
This one liner was inspired from a friend's daily Martin Petrov. Martin blogged initially about this nice tip for those reading Cyrillic check out mpetrov.net, so. Thanks Marto ! 🙂
Tags: about, access, ALL, and, apache, apache webserver, apache webservers, apache2, are, BACK, blogged, check, command, Comment, config, configured, convention, course, create, custom
Posted in Everyday Life, Nginx, Web and CMS | No Comments »